| Oracle® Fusion Middleware Business Process Composer User's Guide for Oracle Business Process Management 11g Release 1 (11.1.1) Part Number E15177-02 |
|
|
View PDF |
| Oracle® Fusion Middleware Business Process Composer User's Guide for Oracle Business Process Management 11g Release 1 (11.1.1) Part Number E15177-02 |
|
|
View PDF |
This chapter describes how to perform administrative using Oracle Business Process Composer.
This chapter includes the following sections:
Oracle BPM uses the security realm functionality of Oracle WebLogic Server to determine what Business Process Composer features a user can access.
Security realm provide mechanisms for protecting Oracle BPM application resources. Each security realm consists of a set of configured security providers, users, groups, security roles, and security policies. A user must be defined in a security realm to access any Oracle BPM resources.
When a user attempts to access Business Process Composer or other Oracle BPM resource, WebLogic Server tries to authenticate and authorize the user by checking the security role assigned to the user in the relevant security realm and the security policy of the particular WebLogic resource.
Table 9-1 describes the basic components of security realms that are relevant to Business Process Composer administration.
Note:
The security roles managed and used in Business Process Composer are not global roles. They are used only within the context of Business Process Composer for managing access to application functionality.Table 9-1 Oracle WebLogic Server Security Realm
| Security Realm Component | Description |
|---|---|
|
Users |
A user can be a person, such as application end user, or a software entity, such as a client application, or other instances of WebLogic Server. As a result of authentication, a user is assigned an identity, or principal. Each user is given a unique identity within the security realm. Users may be placed into groups that are associated with security roles, or be directly associated with security roles. |
|
Groups |
Groups are logically ordered sets of users. Usually, group members have something in common. For example, a company may separate its sales staff into two groups, Sales Representatives and Sales Managers. Companies may do this because they want their sales personnel to have different levels of access to WebLogic resources, depending on their job functions. |
|
Security Roles |
A security role is a privilege granted to users or groups based on specific conditions (see Figure 4-1). Like groups, security roles allow you to restrict access to WebLogic resources for several users at simultaneously. |
Figure 9-1 shows how Business Process Composer fits within the overall Oracle WebLogic Server security architecture.
Figure 9-1 Oracle Business Process Composer Administration
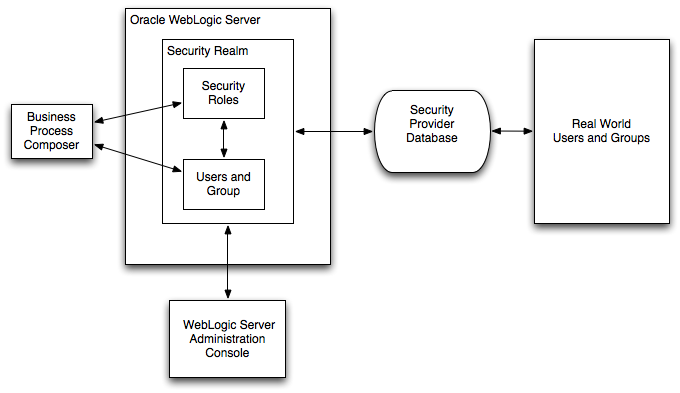
Oracle BPM provides additional default security roles that are creating during installation of the Oracle BPM Suite. These additional security roles define access to different functionality within Business Process Composer.
Note:
The set of security roles in Business Process Composer is fixed. You cannot create new security roles or delete any of the default security roles.You can use Oracle Enterprise Manager to map the default security roles to the application roles defined in your business application.
Table 9-2 describes the Oracle BPM default security roles.
Table 9-2 Default Security Roles in Oracle BPM
| Security Role | Description |
|---|---|
|
Project Administrator |
Enables users and groups to access the administration functionality of Business Process Composer. Users and groups assigned to this role can delete projects, lock and unlock projects. It also enables the assigned users and groups to perform all tasks within the Business Process Composer application, including creating projects. |
|
Developer |
Grants users and groups permission to implement any project stored in Oracle BPM MDS. |
|
Designer |
Grants users and groups permission to model any project stored in Oracle BPM MDS. It does not permit implementation. |
|
Deployer |
Grants users and groups permission to deploy any unlocked project to Oracle BPM run time. In addition to the Deployer security role, users and groups must also be assigned application roles within the SOA infrastructure. See Section 4.6.1, "Introduction to the Deployer Security Role" for more information. |
|
Project Creator from Template |
Enables users and groups to create projects based on project templates. |
|
Project Creator |
Enables assigned users and groups to create process blueprints or projects based on templates. |
|
Project Viewer |
Enables users and groups to view any project stored in Oracle BPM MDS. |
|
Project Documentor |
Grants users and groups permission to add documentation to any project. |
|
SOA Designer |
The SOA Designer role is a security role shared with the SOA infrastructure. Business Process Composer uses this role to enable users and groups to edit Oracle Business Rules at run time. See Section 8.4, "How to Edit the Oracle Business Rules at Run Time" for more information. |
Using the Business Process Composer administration tool, you can assign users and groups to security roles and remove security role assignments.
Note:
The configuration changes outlined in the following procedures are propagated immediately. However, any users who are currently signed on will not see these changes propagated until they sign off and sign on again.To assign users and groups to security roles
Click Administration.
Select Role Mapping.
Expand Add Mapping.
Select the security role where you want to add a user or group.
Click Choose, then click Search.
This returns a list of all users of groups. Optionally, you could search for a specific user or group.
Select the appropriate user or group from the Available column.
Click the Move.
Click OK.
Click Add Mapping.
To remove a security role assignment:
Click Administration
Select Role Mapping.
Expand Manage Mappings, then select the security role mapping you want to delete.
Click Delete.
When you remove a security role mapping, these changes are propagated immediately. However, if the user whose role has been revoked is currently signed in, the changes are not propagated until the next time the user signs-in again.
In contrast, when the administrator role is revoked and the user is currently signed in, a message is displayed when performing any administrative task. The user is then signed off automatically.
Business Process Composer enables you to perform the following project management tasks:
Release project locks
Delete projects from Oracle BPM MDS
To perform project related administrative tasks:
Sign-on to Business Process Composer.
Click Administration.
Select Project Management from the left-hand column
Select the appropriate project from the right-hand column, then select from the following:
Delete: Deletes the selected project from the Oracle BPM Metadata Service repository.
Release Lock: Releases the lock for the selected project. Other users with the appropriate permissions can lock and edit the project.
Refresh Repository: Refreshes the project list from the Oracle BPM Metadata Service repository.
When deleting or resetting locks on projects, it is important to consider how this effects other Business Process Composer Users. It is possible to delete a project or project lock while a user is actively making changes to a project. You must ensure that deleting a project or removing a lock does not adversely effect your users.
After deleting a project or project lock, process participants do not see the propagated changes until they refresh the Oracle BPM Metadata Service Repository or sign-on to Business Process Composer.