| Oracle® Fusion Middleware Administrator's Guide for Oracle Access Manager 11g Release 1 (11.1.1) Part Number E15478-02 |
|
|
View PDF |
| Oracle® Fusion Middleware Administrator's Guide for Oracle Access Manager 11g Release 1 (11.1.1) Part Number E15478-02 |
|
|
View PDF |
Only a registered policy enforcement agent can communicate with OAM 11g authentication and authorization services. OAM administrators must register the agent that resides on the computer hosting the partner application to be protected. A partner application is one that delegates the authentication function to the SSO provider (Oracle Access Manager 11g) to spare users from re-authenticating when accessing multiple resources.
This chapter focuses on using the OAM Administration Console to perform agent registration and management. This chapter includes the following topics:
Registering and Managing WebGate Agents Using the Administration Console
Registering and Managing OSSO Agents Using the Administration Console
Note:
To use the command-line to register a partner, see Chapter 6.Before you can perform tasks in this chapter ensure that the OAM Administration Console and a managed OAM Server are running.
Following are the knowledge-based requirements for tasks in this chapter.
Review Chapter 17, "Managing OAM 10g WebGates with OAM 11g" if you are registering OAM 10g WebGates
This section provides information about access clients, known as policy-enforcement agents, and the registration process that is required to set up the trust mechanism between the agent and Oracle Access Manager 11g SSO.
With Oracle Access Manager 11g, each policy enforcement Agent acts as a filter for HTTP requests. Your deployment can include the following agents in any combination:
OAM Agents:
OAM 11g WebGates
OAM 10g WebGates
OSSO Agents: mod_osso is part of the (still supported) OracleAS 10g single sign-on (OSSO) solution that authenticates users at a central OSSO Server.
After registering 10g mod_osso as an agent, OAM 11g gives mod_osso the redirect URL for the user based on the authentication scheme associated with the OAM policy defined for the resource.
Note:
The mod_osso module is an Oracle HTTP Server module that provides authentication to OracleAS applications.Unless explicitly stated, details about OAM Agents apply equally to WebGates and AccessGates:
WebGate is out of an box access client. This Web server access client intercepts HTTP requests for Web resources and forwards these to the OAM 11g Server. WebGates for various Web servers are shipped with Oracle Access Manager.
AccessGate is a custom access client created for use with non-Web applications. This custom access client must be specifically developed using the Software Developer Kit (SDK) and Oracle Access Manager APIs, either by you or by Oracle. An AccessGate is a form of access client that processes requests for Web and non-Web resources (non-HTTP) from users or applications.
Table 5-1 provides information about all agents for OAM 11g.
Table 5-1 Agents for OAM 11g
| Agents | Description |
|---|---|
|
OSSO Agent (mod_osso 10g) |
Following registration with OAM 11g, the mod_osso module:
|
|
11g WebGates |
After installation and registration with OAM 11g, 11g WebGates communicate with Oracle Access Manager 11g services using the OAM Proxy to "sanitize" the request and respond identically for all agents. |
|
10g WebGates |
After installation and registration, OAM 10g WebGates directly communicate with Oracle Access Manager 11g services through a JAVA-based OAM proxy that acts as a bridge. OAM 10g WebGates include:
See Also IDMDomainAgent in this table. |
|
AccessGates |
Only authentication and authorization is supported (not policy modification) for AccessGates. |
|
IDMDomainAgent |
The IDM Domain Agent provides single sign-on functionality for the IDM Administration Console. The IDM Domain Agent is installed and pre-configured as part of the Oracle Access Manager 11g Server installation and configuration. See Also: "About the Pre-Registered IDM Domain Agent". |
Table 5-2 provides a comparison of the agent types that are compatible with OAM 11g as well as the differences between OAM 11g and earlier agents (organized in columns).
Table 5-2 Comparing Agent Types and Differences
| OAM 11g | OAM 10g | OSSO 10g | |
|---|---|---|---|
|
Available agents |
OAM Agents
OSSO Agents
|
WebGate and AccessGate
With OAM 10g, WebGate installation included Web server configuration. |
|
|
Remote Registration Tool |
Available to register agents to operate with OAM 11g. |
Available to register agents operating with OAM 11g. Note: There was no remote registration equivalent for OAM 10g. |
Available for agents operating with OAM 11g Note: There was no remote registration equivalent before OAM 11g. |
|
Login Forms |
/oam/pages/css/login_page.css |
No login forms provided and used with a 10g WebGate are relevant for OAM 11g. |
unchanged |
|
logout.html |
See Chapter 11 for details about configuring logout for 10g and 11g Agents |
logout.html requires specific details when using a 10g WebGate with OAM 11g. See Chapter 11. |
There is no change required for OAM 11g with mod_osso (OSSO Agents). Applications that use dynamic directives require no entry in mod_osso.conf. Instead, protection is written into the application as one or more dynamic directives. |
|
Multiple network domain support |
OAM 11g supports cross-network-domain single sign-on out of the box. Oracle recommends you use Oracle Identity Federation for this situation. |
OAM provides a proprietary multiple network domain SSO capability that predates Oracle Identity Federation. If this is implemented in your OAM 10g deployment, you can register OAM 10g Agents with OAM 11g to continue this support. |
|
|
Cryptographic keys Notes: The protocols used to secure information exchange on the Internet. |
Note: One key is generated and used per registered mod_osso or 11g WebGate. However, one single key is generated for all 10g WebGates. |
There is just one global shared secret key per OAM deployment which is used by all the WebGates |
|
|
Keys storage |
|
Global shared secret stored in the directory server only (not accessible to WebGate) |
|
Administrators can use either the OAM Administration Console or the remote registration tool to:
Register a freshly installed OAM 11g Agent
Provision a legacy (or freshly installed) OAM 10 WebGate for use with OAM 11g, as described in Chapter 17.
Register an OSSO 10g Agent (mod_osso)
Note:
You can upgrade OracleAS 10g SSO, as described in the Oracle Fusion Middleware Upgrade Guide for Oracle Identity Management. During the upgrade, OSSO agents are registered with OAM 11g. See Appendix B, "Co-existence Overview: OAM 11g and OSSO 10g".The IDM Domain Agent provides single sign-on functionality for the IDM Administration Console. The IDM Domain Agent is installed and pre-configured as part of the Oracle Access Manager 11g Server installation and configuration.
The IDM Domain agent is a domain-wide agent:
Once deployed, the IDM Domain agent is installed on every server in the domain
Unless disabled, every request coming into the WebLogic Application Server is evaluated and processed by the IDM Domain Agent
Configuration details are located under the 10g Webgates node (Policy Configuration tab) in the OAM Administration Console.
Certain IDM Domain Agent configuration elements are available in the WebLogic Administration Console (in the Security Provider section) and others in the OAM Administration Console.
WebLogic Administration Console, Security Provider Settings
In the Security Provider section of the WebLogic Administration Console are five bootstrap configuration parameters.
While Oracle recommends that you retain these without making changes, there are circumstances where you might need to change one of the following parameters:
Primary Access Server: You can replace this value with information for your actual OAM Server. The default value (localhost:5575) can be replaced with information for your actual OAM Server if more than one host is part of the IDM Domain.Agent Password: By default there is no password. However, you can add one here if you want to establish a password for the IDMDomainAgent connection to the OAM Server through the NetPoint (now Oracle) Access Protocol (NAP or OAP).
Figure 5-2 illustrates the default Security Provider settings for the IDM Domain Agent.
OAM Administration Console, IDMDomainAgent Registration Page
The IDMDomainAgent registration page is like all other OAM agent registration pages.
Security Mode: Open is the only security mode available for the IDMDomainAgent. This cannot be changed.
Preferred Host: IDMDomain is the pre-configured host required by this agent
Note:
The Access Client Password here must match the Agent Password in the WebLogic Administration Console. If you changed the Agent Password, you must also change the Access Client Password.Figure 5-2 illustrates the default configuration characteristics for the IDM Domain Agent.
With few exceptions, all agent registration elements are the same. Table 5-3 outlines the differences. All elements are described in Table 5-6, "Expanded OAM 11g and 10g WebGate Agent Elements and Defaults".
Table 5-3
| Element | 11g Webgate | 10g WebGate | IDMDomainAgent |
|---|---|---|---|
|
Primary Cookie Domain |
N/A |
x |
x |
|
Token Validity Period |
x |
N/A |
N/A |
|
Preferred Host |
x |
x |
IDMDomain |
|
Logout Callback URL |
x |
N/A |
N/A |
|
Logout Redirect URL |
x |
N/A |
N/A |
|
Logout Target URL |
x |
N/A |
N/A |
Table 5-4 describes the resources protected by the IDM Domain Agent. Oracle recommends that you do not make any additions or changes. The WebLogic Administration Console (/console/.../*) and Fusion Middleware Enterprise Manager (/em/.../*) are not protected.
Table 5-4 Resources Protected by IDMDomainAgent
| Resource | Description |
|---|---|
|
OAM Console |
/oamconsole/.../* |
|
OINAV |
/oinav/.../* |
|
APM |
/apm/.../* |
|
OAAM Console |
/oaam_admin/.../* |
|
OIM Resources Using LDAPScheme |
/admin/faces/pages/Admin.jspx /oim/faces/pages/Self.jspx /oim/faces/pages/Admin.jspx /xlWebApp/.../* /Nexaweb/.../* |
|
OIM Resources Using OIMScheme |
/admin/faces/pages/pwdmgmt.jspx |
|
OIM Resources Using AnonymousScheme |
/oim/faces/pages/USelf.jspx /admin/faces/pages/forgotpwd.jspx /admin/faces/pages/accountlocked.jspx /admin/.../*.js /admin/.../*.css /admin/.../*.png /admin/.../*.gif /oim/.../*.js /oim/.../*.css /oim/.../*.png /oim/.../*.gif |
You can replace this agent with a 10g WebGate, as described in Chapter 17, "Managing OAM 10g WebGates with OAM 11g".
Only registered policy enforcement agents can communicate with an OAM Server, and process information when a user attempts to access a protected resource.
OAM administrators must register the OAM Agent or OSSO Agent that resides on the computer hosting the application to be protected. Agent registration can include partner registration by automatically creating an application domain and default policies.
Following registration, agent details appear in the OAM Administration Console and are propagated to all Managed Servers in the cluster. If you choose to automatically create policies during agent registration, you can also view and manage the application domain and policies that were registered with the partner application.
Note:
Registering an Agent is also known as "registering a partner application" or "registering a partner application with OAM".During registration, the Agent is presumed to be on the same Web server as the application it is protecting. However, the Agent can be on a proxy Web server and the application can be on a different host.
During Agent registration:
One key is generated per agent, accessible to the WebGate through a local wallet file on the client host, and to OAM Server through the Java Key Store on the server side.
The Agent specific key must be accessible to WebGates through a secure local storage on the client machine. See Table 5-2.
A key is generated for the partner (application) during registration. (except for 10g WebGate agents).
An OAM application domain is created, named after the Agent, and populated with default authentication and authorization policies. The new application domain uses the same host identifier that was specified for the Agent during registration. For more information on application domains, see Chapter 9.
After registration, the agent can monitor attempts to access a Web site and use OAM Servers to provide authentication and authorization services before completing the request. Administrators can view, modify, or remove a registered agent using either the Administration Console or custom WLST commands for OAM 11g.
For more information, see:
When you register an agent using the OAM Administration Console, a new file system directory is created for the Agent on the OAM Administration Console host:
<MW_HOME>/user_projects/domains/<domain_name>/output/<agent_name>
This new directory includes generated files for the registered agent that must be copied in to the agent's installation directory.
11g WebGate: Copy generated files to WebGate_instance_dir/webgate/config (for example, WebTier_Middleware_Home/Oracle_WT1/instances/instance1/config/OHS/ohs1/webgate/config)
10g WebGate: copy generated files to WebGate_install_dir/webgate/config
mod_osso: Copy generated files to OHS_webserver_dir/oracle/product /11.1.1/as_1/instances/instance1/config/OHS/ohs1/osso/
Generated files include the following:
ObAccessClient.xml (for WebGates)
The pre-registered IDM Domain Agent does not use ObAccessClient.xml for bootstrap or configuration.
With OAM 10g, ObAccessClient.xml was generated on the agent side when the configureWebGate tool was run. With OAM 11g, you can use the Administration Console or the remote registration tool to create ObAccessClient.xml.
cwallet.sso (for 11g WebGates, regardless of the transport security mode)
certificate and password files for secure communication, if needed. For example, password.xml file or aaa_cert.pem and aaa_key.pem files.
Note:
When editing an 11g WebGate registration, password.xml is updated only when the mode is changed from Open to Cert or Simple to Cert. In cert mode, once generated, password.xml cannot be updated. Editing the agent Key Password does not result in creation of a new password.xml.osso.conf file (for OSSO Agents)
Before WebGate startup, copy the ObAccessClient file from the generated location to the WebGate installation directory on the computer hosting the WebGate instance.
During WebGate run time, the ObAccessClient file is updated automatically when a change is discovered during periodic update checks.
Simple Mode Global passphrase stored in a nominally encrypted file: password.xml
Cert Mode:
PEM KeyStore Alias
PEM KeyStore Alias Password
This section describes how to manage OAM Agents using the Administration Console. Topics include:
See Also:
The following chapters as neededThis topic describes OAM Agent registration using the OAM Administration Console.
Figure 5-3 illustrates the Create OAM 11g Agent page, under the System Configuration tab in the Administration Console. The Create OAM 10g Agent page includes the same elements. The page requests minimal information to streamline registration. Required information is identified by the asterisk (*).
The page includes named text fields where you enter requested information. Table 5-5 describes each of elements on the Create OAM Agent page. This is the same information that is requested when you use the remote registration tool with the simplified OAM request template as described in Chapter 6.
Table 5-5 Create OAM Agent Pages for OAM 10g and 11g Agents
| OAM Agent Element | Description |
|---|---|
|
Agent Name |
The identifying name for this WebGate Agent. This is often the name of the computer that is hosting the Web server used by WebGate. Note: If the Agent Name exists, an error occurs and registration fails. If the host identifier exists, the unique Agent Base URL is added to the existing host identifier and registration proceeds. |
|
Agent Base URL Optional for OAM 10g and 11g agents. |
The host and port of the computer on which the Web server for the agent is installed. For example, http://my_host:port or https://my_host:port. The port number is optional. Note: A particular Agent Base URL can be registered once only. There is a one-to-one mapping from the Agent's Base URL to the Web server domain on which the WebGate is installed (as specified with the <hostidentifier> element). However, one domain can have multiple Agent's Base URLs. |
|
Access Client Password |
An optional, unique password for this WebGate, which was assigned during WebGate registration. When a registered WebGate connects to an OAM 11g Server, the password is used for authentication to prevent unauthorized WebGates from connecting to OAM 11g Servers and obtaining policy information. |
|
Level of communication transport security between the Agent and the OAM Server (this must match the level specified for the OAM Server):
Note: For more information on Simple and Cert modes, and encrypting the private key using the DES algorithm, see Appendix E. |
|
|
Host Identifier |
This identifier represents the Web server host. |
|
Auto Create Policies |
During agent registration, you can have authentication and authorization policies created automatically. This option is checked (enabled) by default. Default: Enabled Note: If you already have a domain and policies registered, you can simply add new resources to it. If you clear this option (no check), no application domain or policies are generated automatically. |
|
Protected Resource (URI) List |
URIs for the protected application: /myapp/login, for example. Each URI for the protected application should be specified in a new row of the table for the Protected Resource List. Default: 2 resources are protected by default. /.../* / The default matches any sequence of characters within zero or more intermediate levels spanning multiple directories. See Also: "About the Resource URL". |
|
Public Resource (URI) List |
Each public application should be specified in a new row of the table for the Public Resource List. Add a field and enter URI values for the public applications and resources. Each URI should be specified in a new row of the table for the Public Resource List. |
To help streamline Agent registration, additional elements are concealed and default values are applied. When you view or edit an Agent's page in the Administration Console, all elements and values are revealed, as shown in Figure 5-4. Most elements are the same as those you define when using the remote registration tool with the expanded OAM template, as described in Chapter 6.
Figure 5-4 OAM 11g Webgate Page with Defaults
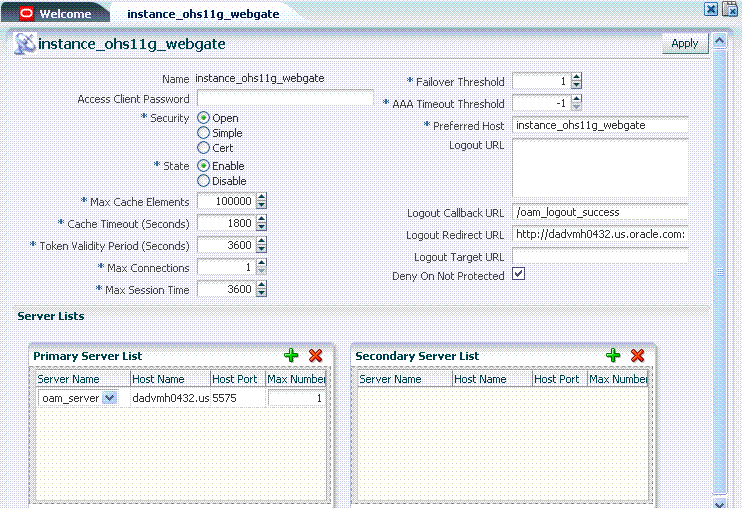
Table 5-6 summarizes elements on an expanded registration. Additional settings revealed here are used by the OAM Proxy. ObAccessClient.xml is populated with values after agent registration, whether you use the OAM Administration Console as described here or the remote registration tool as described in Chapter 6.
Table 5-6 Expanded OAM 11g and 10g WebGate Agent Elements and Defaults
| OAM Agent Element | Description |
|---|---|
|
Agent Name |
Name of the OAM Agent. |
|
Optional, unique password for the OAM Agent. When the agent connects to an OAM Server, it uses the password to authenticate itself to the server. This prevents unauthorized agents from connecting and obtaining policy information. |
|
|
10g WebGate only. |
This parameter describes the Web server domain on which the OAM Agent is deployed, for instance,.acompany.com. You must configure the cookie domain to enable single sign-on among Web servers. Specifically, the Web servers for which you configure single sign-on must have the same Primary Cookie Domain value. The OAM Agent uses this parameter to create the ObSSOCookie authentication cookie. This parameter defines which Web servers participate within the cookie domain and have the ability to receive and update the ObSSOCookie. This cookie domain is not used to populate the ObSSOCookie; rather it defines which domain the ObSSOCookie is valid for, and which Web servers have the ability to accept and change the ObSSOCookie contents. Default: If the client side domain can be determined during registration, the Primary Cookie Domain is populated with that value. However, if no domain is found, there is no value and WebGate uses the host-based cookie. Note: The more general the domain name, the more inclusive your single sign-on implementation will be. For example, if you specify b.com as your primary cookie domain, users will be able to perform single sign-on for resources on b.com and on a.b.com. However, if you specify a.b.com as your primary cookie domain, users will have to re-authenticate when they request resources on b.com. |
|
Set only in the OAM Administration Console. |
Specifies whether the OAM Agent is enabled or disabled. Default = Enabled |
|
Number of elements maintained in the cache. Cache elements are the following:
The value of this setting refers to the maximum consolidated count for elements in both of these caches. Default = 100000 |
|
|
Amount of time cached information remains in the OAM Agent cache when the information is neither used nor referenced. Default = 1800 (seconds) |
|
|
11g WebGate only |
Maximum valid time period for an agent token (the content of OAMAuthnCookie for 11g WebGate). The equivalent to tokenValidityPeriod field in 10g WebGates is called cookieSessionTime. Default = 3600 (seconds) Note: For OAM 10g WebGates, use Cookie Session Time to set the Token Validity Period. |
|
The maximum number of connections that this OAM Agent can establish with the OAM Server. This number must be the same as (or greater than) the number of connections that are actually associated with this agent. Default = 1 |
|
|
Maximum amount of time in seconds that a user's authentication session is valid, regardless of their activity. At the expiration of this session time, the user is re-challenged for authentication. This is a forced logout. Default = 24 (hours) A value of 0 disables this timeout setting. |
|
|
Number representing the point when this OAM Agent opens connections to a Secondary OAM Server. Default = 1 For example, if you type 30 in this field and the number of connections to primary OAM Server falls to 29, this OAM Agent opens connections to secondary OAM Server. |
|
|
Number (in seconds) to wait for a response from the OAM Server. If this parameter is set, it is used as an application TCP/IP timeout instead of the default TCP/IP timeout. Default = -1 (default network TCP/IP timeout is used) A typical value for this parameter is between 30 and 60 seconds. If set to a very low value, the socket connection can be closed before a reply from Access Server is received, resulting in an error. For example, suppose an OAM Agent is configured to talk to one primary OAM Server and one secondary OAM Server. If the network wire is pulled from the primary OAM Server, the OAM Agent waits for the TCP/IP timeout to learn that there is no connection to the primary OAM Server. The WebGate tries to reestablish the connections to available servers starting with the primary Access Server. Again, the OAM Agent waits for the TCP/IP timeout to determine if a connection can be established. If it cannot, the next server in the list is tried. If a connection can be established to another OAM Server (either a primary or secondary), the requests are re-routed. However this can take longer than desired. When finding new connections, OAM Agent checks the list of available servers in the order specified in its configuration. If there is only one primary OAM Server and one secondary OAM Server specified, and the connection to the primary OAM Server times out, the OAM Agent still tries the primary OAM Server first. As a result, the OAM Agent cannot send requests to an OAM Server for a period greater than twice the setting in the OAM Server Timeout Threshold. If the OAM Server takes longer to service a request than the value of the timeout threshold, the OAM Agent abandons the request and retries the request on a new connection. Note that the new connection that is returned from the connection pool can be to the same OAM Server, depending on your connection pool settings. Also, other OAM Server may also take longer to process the request than the time specified on the threshold. In these cases, the OAM Agent can continue to retry the request until the OAM Server is shut down. |
|
|
Idle Session Timeout 10g WebGates only |
Default: 3600 Release 7.0.4 WebGates enforced their own idle session timeout only. 10.1.4.0.1 WebGates enforced the most restrictive timeout value among all WebGates the token had visited. With 10g (10.1.4.3), the 7.0.4 behavior was reinstated as the default with this element. To set idleSessionTimeoutLogic:
|
|
Preferred Host |
Specifies how the hostname appears in all HTTP requests as users attempt to access the protected Web server. The hostname within the HTTP request is translated into the value entered into this field regardless of the way it was defined in a user's HTTP request. The Preferred Host function prevents security holes that can be inadvertently created if a host's identifier is not included in the Host Identifiers list. However, it cannot be used with virtual Web hosting. For virtual hosting, you must use the Host Identifiers feature. |
|
Deny on Not Protected |
Denies access to all resources to which access is not explicitly allowed by a rule or policy. Always enabled in 11g WebGate registration, and cannot be changed. On a 10g WebGate registration page, you can choose to disable this. |
|
Logout URL |
The Logout URL triggers the logout handler, which removes the cookie (ObSSOCookie for 10g WebGates; OAMAuthnCookie for 11g WebGates) and requires the user to re-authenticate the next time he accesses a resource protected by Oracle Access Manager.
Default = Note: This is the standard OAM 10g WebGate configuration parameter used to trigger initial logout. See Also: Chapter 11 for additional steps required for configuring logout for OAM 10g WebGates registered with OAM 11g. |
|
Additional Logout for 11g WebGate Only |
For OAM 11g WebGate single sign-off behavior, specific logout elements and values automate the redirect to a central logout URL, callback URL, and end_URL. This replaces 10g WebGate single sign-off only through a customized local logout page. |
|
Logout Callback URL 11g WebGate only |
The URL to oam_logout_success, which clears cookies during the call back. This can be a URI format without host:port (recommended), where the OAM Server calls back on the host:port of the original resource request. For example: Default = /oam_logout_success This can also be a full URL format with a host:port, where OAM 11g server calls back directly without reconstructing callback URL. When the request URL matches the Logout Callback URL, WebGate clear its cookies and streams an image gif in the response. This is similar to OSSO agent behavior. When WebGate redirects to the server logout page, it records an "end" URL as a query parameter ( Other OAM 11g services support the central logout page on the server. The end_url relies on the target URL query parameter passed from OPSS integrated applications. |
|
Logout Redirect URL 11g WebGate only |
This parameter is automatically populated after agent registration completes.By default, this is based on the OAM Server host name with a default port of 14200. For example: Default = http://OAMServer_host:14200/oam/server/logout The Logout URL triggers the logout handler, which removes the OAMAuthnCookie_<host:port>_<random number> and requires the user to re-authenticate the next time he accesses a resource protected by Oracle Access Manager. See Also: Chapter 11, "Configuring Centralized Logout for 11g WebGate with OAM 11g Server" |
|
Logout Target URL 11g WebGate only |
The value is the name for the query parameter that the OPSS applications passes to WebGate during logout; the query parameter specifies the target URL of the landing page after logout completes. Default: end_url See Also: Chapter 11, "Configuring Centralized Logout for 11g WebGate with OAM 11g Server" |
|
Primary Server List |
Identifies Primary Server details for this Agent. The default is based on the OAM Server:
|
|
Secondary Server List |
Identifies Secondary OAM Server details for this agent, which must be specified manually:
|
Users with valid OAM Administrator credentials can perform the following procedure to search for an OAM Agent using the Administration Console.
Prerequisites
The WebGate must be a registered agent of Oracle Access Manager 11g.
To search for an OAM Agent registration
Activate the System Configuration tab.
From the search type list, choose the relevant type (10g Webgates or 11g Webgates) to define your search.
In the text field, enter the exact name of the instance you want to find. For example:
my_OAM_Agent
Click the Search button to initiate the search.
Click the Search Results tab to display the results table, and then:
Edit: Click the Edit command button in the tool bar to display the configuration page.
Delete: Click the Delete button in the tool bar to remove the instance; confirm removal in the Confirmation window.
Detach: Click Detach in the tool bar to expand the table to a full page.
View: Select a View menu item to alter the appearance of the results table.
Click the Browse tab to return to the navigation tree when you finish with the Search results.
You can register a WebGate agent before you install it. Users with valid OAM Administrator credentials can perform the following task to register an OAM Agent using the Administration Console.
Note:
During agent registration, at least one OAM Server instance must be running in the same mode as the agent. Otherwise, agent registration fails.After agent registration, you can change the communication mode of the OAM Server if needed. Communication between the agent and server continues to work as long as the WebGate mode is at least at the same level as the OAM Server mode or higher. See Appendix E.
Prerequisites
Confirm that at least one OAM Server is running in the same mode as the agent to be registered.
To register a WebGate agent
Log in to the OAM Administration Console as usual.
From the OAM Administration Console Welcome page, Agent Configuration panel, click one of the following links to open a fresh page:
Add OAM 11g Agent
Add OAM 10g Agent (see also Chapter 17)
Alternatively: From the System Configuration tab, expand the Agents node, the OAM Agents node, and either the 11g Webgates or 10g Webgates node, then click the Create command button in the tool bar.
On the Create: OAM Agent page, enter required details (those with an *) to register this OAM Agent, as shown in Table 5-5:
Protected Resource List: In this table, enter individual resource URLs to be protected by this OAM Agent, as shown in Table 5-5.
Public Resource List: In this table, enter individual resource URLs to be public (not protected), as shown in Table 5-5.
Click Apply to submit the registration (or close the page without applying changes).
Check the Confirmation window for the location of generated artifacts and then close the window.
In the navigation tree, confirm the Agent name is listed.
Note:
If you are provisioning an OAM 10g WebGate, skip Step 9 for now and go to Chapter 17.Perform the following steps to copy the artifacts to the WebGate installation directory (or install WebGate and then copy these artifacts):
On the OAM Administration Console host, locate the updated OAM Agent ObAccessClient.xml configuration file (and any certificate artifacts). For example:
$DOMAIN_HOME/output/$Agent_Name/ObAccessClient.xml
On the OAM Agent host, copy artifacts (to the following WebGate directory path). For example:
Restart the OAM Server that is hosting the Agent and proceed to Part III, "Single Sign-on, Policies, and Testing".
Users with valid OAM Administrator credentials can change any setting for a registered OAM Agent using the Administration Console, as described in the following procedure. For example, you might want to revise the timeout threshold or other settings used by the OAM Proxy.
After changes, updated details are propagated through a runtime configuration update process. There is usually no need to copy the artifacts over to WebGate configuration area.
Note:
Artifacts need only be copied to the WebGate directory path if the agent name, access client password, or security mode is changed.Prerequisites
The agent must be registered and available in the Oracle Access Manager Administration Console.
To view or modify details for a registered WebGate Agent
From the System Configuration tab, navigation tree, expand the following nodes as needed:
Double-click the desired agent's name to display the registration page.
Modify Agent details, and Primary or Secondary Server details, as needed (see Table 5-5 and Table 5-6).
Click Apply to submit changes and dismiss the Confirmation window (or close the page without applying changes).
Perform the following steps to copy artifacts if needed:
Note:
Artifacts need only be copied to the WebGate directory path if the agent name, or agent client password, or security mode is changed. See Chapter 17 if you are provisioning an OAM 10g WebGate.On the OAM Administration Console host, locate the updated OAM Agent ObAccessClient.xml configuration file (and any certificate artifacts). For example:
$DOMAIN_HOME/output/$Agent_Name/ObAccessClient.xml
On the OAM Agent host, copy artifacts (to the following WebGate directory path). For example:
Restart the OAM Server that is hosting the Agent and proceed to Part III, "Single Sign-on, Policies, and Testing".
See Appendix E, "Securing Communication with OAM 11g", if needed.
Users with valid OAM Administrator credentials can perform the following procedure to delete a registered OAM Agent from the Administration Console.
Note:
Deleting an agent registration remove only the registration (not the associated host identifier, application domain, resources, or the agent itself).See Also:
Prerequisites
Evaluate the application domain, resources, and policies associated with this agent and ensure that these are configured to use another agent or that they can be removed.
To delete an OAM agent registration
From the System Configuration tab, navigation tree, expand the:
Optional: Double-click the desired agent's name to view the registration, then close the page.
Click the desired agent's name, click the Delete button in the tool bar, and confirm the removal in the Confirmation window.
Confirm the Agent name is no longer listed in the navigation tree.
Remove WebGate Instance: Perform the following steps and also refer to "Removing a 10g WebGate from the OAM 11g Deployment", if needed.
Shut down the Web server.
Remove WebGate software using the utility provided in the following directory path:
$WebGate_install_dir/oui/bin
Windows: setup.exe -d Unix: runInstaller -d
Revert to the httpd.conf version before updates for WebGate. For example:
Copy: httpd.conf.ORIG
To: httpd.conf
Restart the Web server.
On the agent host, manually remove the WebGate instance directory. For example:
This section describes how to manage OSSO Agent registrations (mod_osso) using the Administration Console. For details, see:
An OSSO Agent is any mod_osso module deployed on an Oracle HTTP Server that is acting as a partner application for the OSSO server and protecting resources.
The OSSO Proxy supports interoperability between OAM and OSSO agents (using an OSSO agent to access a valid SSO session created for an OAM Agent, and vice versa).
| OSSO Proxy Supports | Description |
|---|---|
| SSO login | From an OSSO Agent to the OAM Server (and OSSO-specific tokens) |
| SSO logout | From the OSSO Agent to the OAM Server |
| OSSO Agent requests and protocols | OSSO Proxy translates the OSSO protocol into a protocol for Oracle Access Manager 11g services. |
This topic describes OSSO Agent registration using the Administration Console.
Note:
Before you register an OSSO Agent, ensure that the Oracle HTTP Server is installed on the client computer and that the Web server is configured for mod_osso.Figure 5-5 shows a Create OSSO Agent page, under the System Configuration tab in the Administration Console.
On the Create OSSO Agent page, required information is identified by the asterisk (*). Table 5-7 describes the required and optional details that you can specify when you register a new agent.
Table 5-7 Create OSSO Agent Page Elements
| Element | Description |
|---|---|
|
Agent Name |
The identifying name for this mod_osso Agent. |
|
Agent Base URL Required for OSSO agents. |
The required protocol, host, and port of the computer on which the Web server for the agent is installed. For example, http://host:port or https://host:port. Note: The host and port are used as defaults for the expanded registration. See Table 5-8. |
|
Admin ID |
Optional administrator log in ID for this mod_osso instance. For example, SiteAdmin. |
|
Admin Info |
Optional administrator details for this mod_osso instance. For example, Application Administrator. |
|
Host Identifier |
The host identifier is filled in automatically based on the Agent name |
|
Auto Create Policies |
During agent registration, you can have authentication and authorization policies created automatically. This option is checked (enabled) by default. The OSSO Proxy requires an application domain that includes a resource with the generic url(/.../*) protected by a policy based on the LDAP scheme (default). This is why a generic URL is used at the server side. Default: Enabled Note: If you already have a domain and policies registered, you can simply add new resources to it. If you clear (uncheck) this option, no application domain or policies are generated automatically. |
To help streamline Agent registration, several elements are concealed and default values are used during registration with the console. When you view an agent's registration page in the Administration Console, all elements and values are revealed.
Figure 5-6 shows the full Agent page as viewed in the Administration Console. The Confirmation window is still visible. All details specified, and defaults, are shown.
Figure 5-6 OSSO Agent Page and Confirmation Window
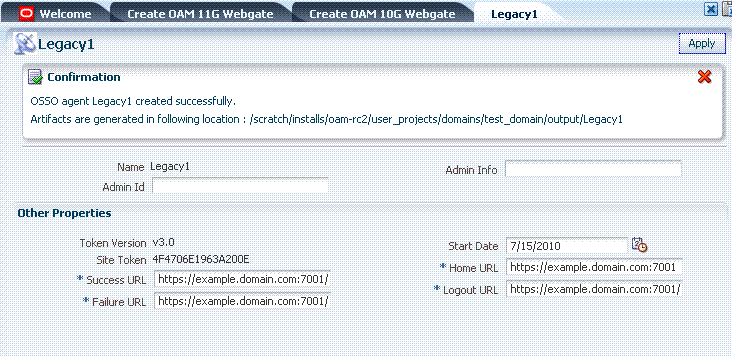
Table 5-8 summarizes the expanded elements and defaults that are used by the OSSO Agent.
Table 5-8 Expanded OSSO Agent Elements
| Element | Description |
|---|---|
|
Token Version |
The version of the token is 3.0. This cannot be edited. |
|
Site Token |
The Application Token used by the partner when requesting authentication. This cannot be edited. |
|
Success URL |
The redirect URL to be used upon successful authentication. By default, osso_login_success on the fully qualified host and port specified with the Agent Base URL are used. For example: Default: http://myhost:5678/osso_login_success |
|
Failure URL |
The redirect URL to be used if authentication fails.By default, osso_login_failure on the fully qualified host and port specified with the Agent Base URL are used: Default: http://myhost:5678/osso_login_failure |
|
Start Date |
First month, day, and year for which log in to the application is allowed by the server. Default: The date the Agent was registered. |
|
Home URL |
The redirect URL to be used for the Home page after authentication. By default, the fully qualified host and port specified with the Agent Base URL are used: Default: http://myhost:5678 |
|
Logout URL |
The redirect URL to be used when logging out. This redirects the user to the global logout page on the server: osso_logout_success. By default, the fully qualified host and port specified with the Agent Base URL are used: Default: http://myhost:5678/osso_logout_success See Also: "Introduction to OAM 11g Centralized Logout". |
Users with valid OAM Administrator credentials can perform the following procedure to search for an OSSO Agent using the Administration Console.
Prerequisites
The OSSO Agent must be registered and available in the Oracle Access Manager Administration Console.
To search for an OSSO Agent registration
Activate the System Configuration tab.
From the search type list, choose the OSSO agents type to define your search.
In the text field, enter the exact name of the instance you want to find. For example:
my_OSSO_Agent
Click the Search button to initiate the search.
Click the Search Results tab to display the results table, and then:
Edit: Click the Edit command button in the tool bar to display the configuration page.
Delete: Click the Delete button in the tool bar to remove the instance; confirm removal in the Confirmation window.
Detach: Click Detach in the tool bar to expand the table to a full page.
View: Select a View menu item to alter the appearance of the results table.
Click the Browse tab to return to the navigation tree when you finish with the Search results.
Users with valid OAM Administrator credentials can perform the following procedure to register an OSSO Agent using the Administration Console.
Prerequisites
Ensure that the Oracle HTTP Server is installed and running on the client computer, and is configured for mod_osso.
See Also:
Chapter 6 for details about using the remote command-line tool
To register an OSSO Agent
Log in to the OAM Administration Console as usual.
From the Welcome page, Agent Configuration panel, click the following link to open a fresh page:
Add OSSO Agent
Alternatively: From the System Configuration tab, expand the Agents node and the OSSO Agents node, then click the Create button in the tool bar.
Click the Create button in the tool bar.
On the Create: OSSO Agent page, enter required details, as shown in Table 5-7:
Agent Name
Agent Base URL
On the Create: OSSO Agent page, enter optional details as desired (Table 5-7):
Click Apply to submit the registration (or close the page without applying changes).
In the Confirmation window, check the path to generated artifacts and then close the window. For example:
Artifacts are generated in following location : /.../base_domain/output/OSSO1
Copy the updated osso.conf file to the OSSO Agent host:
On the OAM Administration Console host, locate the updated OSSO Agent osso.conf file. For example:
$DOMAIN_HOME/output/$Agent_Name/osso.conf
On the OSSO Agent host, copy osso.conf to the mod_osso directory path.
$OHS_dir/osso.conf
Restart the OAM Server that is hosting the OSSO Agent.
Proceed to Part III, "Single Sign-on, Policies, and Testing".
Users with valid OAM Administrator credentials can change any setting for a registered OSSO Agent using the Administration Console, as described in the following procedure. For example, you might want to revise the end date or add administrator information.
Prerequisites
Ensure that the Oracle HTTP Server is installed and running on the client computer, and is configured for mod_osso.
To view or modify an OSSO Agent registration
From the System Configuration tab, navigation tree, expand the Agents node.
Expand the OSSO Agents node, and double-click the desired agent's name to display the registration page.
On the registration page, view or modify details as needed based on details in Table 5-7 and Table 5-8.
Click Apply to submit the changes (or close the page without applying changes), and close the Confirmation window.
Copy the updated osso.conf file to the OSSO Agent host:
On the OAM Administration Console host, locate the updated OSSO Agent osso.conf file. For example:
$DOMAIN_HOME/output/$Agent_Name/osso.conf
On the OSSO Agent host, copy osso.conf to the mod_osso directory path.
$OHS_dir/osso.conf
Restart the OAM Server that is hosting the OSSO Agent and proceed to Part III, "Single Sign-on, Policies, and Testing":
Users with valid OAM Administrator credentials can perform the following procedure to delete a registered OSSO Agent from the Administration Console.
Note:
Deleting an agent registration removes only the registration (not the associated host identifier, application domain, resources, or the agent instance itself).Prerequisites
Evaluate the application domain, resources, and policies associated with this agent and ensure that these are configured to use another agent or that they can be removed.
To delete an OSSO Agent registration
From the System Configuration tab, navigation tree, expand the Agents node.
Expand the OSSO Agents node.
Optional: Double-click the desired agent's name to display the registration page; confirm this is the agent to remove, and close the page.
Click the Agent name, click the Delete button in the tool bar, and confirm removal in the Confirmation window.