| Oracle® Fusion Middleware Administrator's Guide for Oracle Access Manager 11g Release 1 (11.1.1) Part Number E15478-02 |
|
|
View PDF |
| Oracle® Fusion Middleware Administrator's Guide for Oracle Access Manager 11g Release 1 (11.1.1) Part Number E15478-02 |
|
|
View PDF |
This chapter describes the initial steps needed to log in and navigate around the Oracle Access Manager 11g Administration Console. This chapter includes the following topics:
All tasks in this book presume that you have Oracle Access Manager 11g deployed as described in the Oracle Fusion Middleware Installation Guide for Oracle Identity Management.
Note:
You can access the Oracle Access Manager Administration Console when the WebLogic Administration Server is running. If the OAM Administration Console is protected by a WebGate, the OAM Server must be running.Before you begin tasks in this chapter:
Learn about the Administration Console as described in "Introduction to the OAM Administration Console and Controls".
Verify the administrative LDAP group defined in the primary user identity store.
Note:
The default LDAP group for both WebLogic and OAM administrators, "Administrator", is set during initial deployment using the Oracle Fusion Middleware Configuration Wizard, as described in "Introduction to OAM Administrators".Oracle Access Manager 11g provides a full range of Web perimeter security functions that include Web single sign-on; authentication and authorization; policy administration; auditing, and more.
This topic provides an overview of Oracle Access Manager 11g, which sits on Oracle WebLogic Servers and is part of the Oracle Fusion Middleware Access Management architecture.
While providing backward compatibility and co-existence with existing solutions, Oracle Access Manager 11g replaces and converges:
Oracle Access Manager 10g
Oracle Application Server SSO (OSSO) 10g
Oracle Sun OpenSSO
As illustrated in Figure 2-1, all user identities, policies, and audit records reside in centrally managed data stores. Oracle WebLogic Server provides domain management, deployment management, and post-installation configuration. Oracle Access Manager manages all agents and policies centrally.
Both Oracle WebLogic Server and Oracle Access Manager 11g rely on the Oracle Platform Security Services for authentication, authorization, secure communication (SSL), the common Audit Framework, as well as the credential store, and identity services.
Shared services for Access (SSA) include token processing, session management. Shared services for identity (SSI) include password reset, password policy, and delegated administration through Oracle Identity Manager.
Fraud prevention, security token service, identity federation, authentication and SSO, and authorization and Entitlements are integrated.
Figure 2-2 illustrates the primary Oracle Access Manager 11g components and services. The Protocol Compatibility Framework interfaces with OAM WebGates, mod_osso agents, and custom AccessGates created using the Access Manager Software Developer Kit (SDK).
Figure 2-3 illustrates the distribution of Oracle Access Manager components.
The Oracle Access Manager Administration Console (sometimes referred to as the Oracle Access Manager Admin Server) resides on the Oracle WebLogic Administration Server (known as AdminServer). WebLogic Managed Servers hosting OAM runtime instances are known as OAM Servers.
Shared information consists of:
Agent and server configuration data
Oracle Access Manager policies
User session data is shared among all OAM Servers
For more information, see "Comparing Oracle Access Manager 11g with OAM 10g and OSSO 10g".
This topic introduces Oracle Access Manager 11g architecture and provides a comparison against the 10g architecture for Oracle Access Manager and OSSO. Included are the following topics:
Oracle Access Manager 11g differs from Oracle Access Manager 10g in that the identity administration features have been transferred to Oracle Identity Manager 11g (including user self-service and self registration, workflow functionality, dynamic group management, and delegated identity administration).
Oracle Access Manager 10g supported Single Sign-on using a single session cookie (the ObSSOCookie) that contained the user identity and user session information required to access target resources that had the same or lower authentication level. The ObSSOCookie was encrypted and decrypted using a global shared secret key, the value of which was stored in the directory server. The ObSSOCookie was consumed by Access System components to verify the user identity and allow or disallow access to protected resources.
To close any possible security gaps, Oracle Access Manager 11g provides new server-side components that maintain backward compatibility with existing Oracle Access Manager 10g policy-enforcement agents (WebGates) and OSSO 10g agents (mod_osso). New Oracle Access Manager 11g WebGates are enhanced versions of 10g WebGates, that support a per-agent secret key for the Single Sign-on (SSO) solution. Thus, cookie-replay type of attack are prevented. The 11g WebGates are all trusted at the same level; a cookie specific for the WebGate is set and cannot be used to access any other WebGate-protected applications on a user's behalf.
Unless explicitly stated, the term "WebGate" refers to both an out of the box WebGate or a custom AccessGate.
Oracle Access Manager 11g uses technology from Oracle Coherence to provide centralized, distributed, and reliable session management.
For a list of names that have changed with Oracle Access Manager 11g, see "Product and Component Name Changes". Table 2-1 provides a comparison of Oracle Access Manager 11g, OAM 10g, and OracleAS SSO 10g.
Table 2-1 Comparison: OAM 11g versus OAM 10g versus OSSO 10g
| OAM 11g | OAM 10g | OSSO 10g | |
|---|---|---|---|
|
Architecture Components |
Note: Eight Administrator languages are supported. |
Note: Eight Administrator languages are supported. |
|
|
Cookies |
Host-based authentication cookie:
|
|
|
|
Cryptographic keys The protocols used to secure information exchange on the Internet. |
|
One global shared secret key for all WebGates |
|
|
Key storage |
|
Global shared secret stored in the directory server only (not accessible to WebGate) |
|
|
Encryption / Decryption (The process of converting encrypted data back into its original form) |
Introduces client-side cryptography and ensures that cryptography is performed at both the agent and server ends:
|
|
Cryptography is performed at both mod_osso and OSSO server:
|
|
Session Management |
|
|
|
|
Client IP |
|
|
|
|
Response token replay prevention |
|
N/A |
|
|
Centralized log-out |
For more information, see Chapter 11. |
|
The OSSO server cookie includes a list of partner IDs. When a user logs off from one partner application:
|
This section provides a brief overview of OAM deployments and installation:
Table 2-2 describes the types of deployments you might have within your enterprise, even though these might be named differently in your enterprise.
Table 2-2 Deployment Types
| Deployment Type | Description |
|---|---|
|
Development Deployment |
Ideally a sandbox-type setting where the dependency on the overall deployment is minimal |
|
QA Deployment |
Typically a smaller shared deployment used for testing |
|
Pre-production Deployment |
Typically a shared deployment used for testing with a wider audience |
|
Fully shared and available within the enterprise on a daily basis |
During initial installation and configuration you can create a new WebLogic Server domain (or extend an existing domain) and define information for OAM Servers, Database Schemas, optional WebLogic Managed Servers and clusters, and the embedded LDAP Server.
See Also:
The "Understanding Oracle WebLogic Server Domains" chapter in the Oracle Fusion Middleware Understanding Domain Configuration for Oracle WebLogic Server guide provides information about Oracle WebLogic Server administration domains.Regardless of the deployment size or type, in a new WebLogic Server domain the following OAM-related components are deployed using the Oracle Fusion Middleware Configuration Wizard:
WebLogic Administration Server
Oracle Access Manager Console deployed on the WebLogic Administration Server (sometimes referred to as the OAM Administration Server)
A WebLogic Managed Server for Oracle Access Manager
Application deployed on the Managed Server
Note:
In an existing WebLogic Server domain, the WebLogic Administration Server is already installed and operational.While using the Oracle Fusion Middleware Configuration Wizard, the with-DB config template was chosen to set up the database for application domain metadata. The database must be extended with the OAM-specific schema using the Repository Creation Utility (RCU). The policy store bootstrap occurs on the initial AdminServer startup after running the Configuration Wizard. For more information, see the Oracle Fusion Middleware Installation Guide for Oracle Identity Management.
The default Embedded LDAP is set as the primary user identity store for OAM 11g.
A Java key store is set up to be used for certificates for Simple or Certificate-based communication between OAM Servers and WebGates during authorization. The key store bootstrap also occurs on the initial AdminServer startup after running the Configuration Wizard.
During initial deployment, the WebLogic Administrator userID and password are set for use when signing in to both the OAM Administration Console and WebLogic Server Administration Console. A different administrator can be assigned for OAM, as described in "Introduction to OAM Administrators".
OAM administrators can log in and use the OAM Administration Console to manage:
User identity stores
OAM Server registration
Partner (agent and partner application) registration
Application domains and policies to protect resources
User sessions
Common Server Properties
Only users with sufficient privileges can log in to the Oracle Access Manager Administration Console or use OAM administrative command-line tools such as the remote registration tool or WLST. The WebLogic Scripting Tool (WLST) is a command-line scripting environment that can be used to manage, and monitor WebLogic Server domains. Administrators can also use customized OAM WLST commands to perform a number of tasks.
During initial deployment, the administrator userID and password are set. By default, access to the OAM Administration Console is provided using the WebLogic Server "Administrators" group. These credentials provide access to both the WebLogic Server Administration Console and the Oracle Access Manager Administration Console.
Note:
Initially, administrative users must log in to the OAM Administration Console using the WebLogic Administrator credentials set during initial OAM configuration.Table 2-3 describes the administrator Role that is recognized by Oracle Access Manager and WebLogic, and the default LDAP group to which the Role is mapped in the primary user identity store.
Table 2-3 Role Mapping from an LDAP Group to OAM Administrator
| OAM Administrator Role | Description and LDAP Group |
|---|---|
|
OAM Administrator's Role |
The LDAP group defined within the primary user identity store that grants users full OAM system and policy configuration privileges. Default Group = Administrators Note: Specifying a different LDAP group prohibits WebLogic administrators from logging in to OAM or from using OAM administrative command-line tools. |
Your enterprise might require independent sets of administrators: one set of users responsible for OAM administration and a different set for WebLogic administration. For more information, see "Defining a New OAM Administrator Role".
This section describes how to log in to and sign out of the Oracle Access Manager Administration Console directly.
This section provides the following topics:
Logging In to the Oracle Access Manager 11g Administration Console
Signing Out of Oracle Access Manager 11g Administration Console
Note:
If you have Oracle Identity Navigator installed to access multiple consoles from one URL, see the Oracle Fusion Middleware Administrator's Guide for Oracle Identity Navigator.The OAM log in page is shown in Figure 2-4.
Figure 2-4 Oracle Access Manager 11g Log In Page

Note:
Ensure that you use the correct administrative credential for log in. Initially, the LDAP group for the OAM Administrator is the same as the LDAP group defined for the WebLogic Server Administration Console ("Administrators") and the primary user identity store is the WebLogic Embedded LDAP.To log in to Oracle Access Manager 11g
In a browser window, enter the URL to the Oracle Access Manager 11g using the appropriate protocol (HTTP or HTTPS). For example:
https://hostname:port/oamconsole/
In the sample URL shown here:
HTTPS represents the Hypertext Transfer Protocol (HTTP) with the Secure Socket Layer (SSL) enabled to encrypt and decrypt user page requests and the pages returned by the Web server
hostname refers to fully-qualified domain name of the computer hosting the Oracle Access Manager 11g Administration Console
port refers to the designated bind port for the OAM Administration Console (this is the same as the bind port for the WebLogic Server Administration Console)
/oamconsole/refers to the OAM Administration Console Log In page
On the Log In page, enter the OAM Administrator credentials. For example:
Username: Admin_login_id
Password: Admin_password
Click the Log In button or press the Enter key.
Proceed as follows:
Successful: Policy Configuration, and System Configuration tabs appear on the left; Welcome page is on the right. Tour the console, as described in "Introduction to Policy Configuration and System Configuration Tabs" or start performing tasks on your own.
Not Successful: Log in again and ensure that you enter information exactly as specified for the OAM Administrator in the primary user identity store.
See Also:
"Introduction to OAM Administrators"The Sign Out link appears in the upper-right corner of the Administration Console, as shown in Figure 2-5. You select the Sign Out link to conclude your session. Oracle recommends that you also close the browser window after signing out.
Figure 2-5 Sign Out Link, Upper-right Corner
To sign out of Oracle Access Manager 11g Administration Console
Click the Sign Out link in the upper-right corner of the console.
Close your browser window.
The Oracle Access Manager Administration Console is a Web-based program that provides function-level tabs and controls, as well as page-level tabs and controls. This section introduces the Oracle Access Manager 11g Administration Console.
The Oracle Access Manager 11g Administration Console provides the system and policy configuration management functions required by administrators. You can enter the URL to the Oracle Access Manager 11g console in a browser window:
https://hostname:port/oamconsole
In the sample URL, hostname refers to computer that hosts the Oracle Access Manager 11g Administration Console; port refers to the HTTP port number on which the console host listens; /oamconsole refers to the Log In page.
This section provides a quick introduction to orient you to the Oracle Access Manager Administration Console.
Figure 2-6 provides a look at the Administration Console as it appears immediately after log in.
Figure 2-6 OAM Administration Console Welcome Page and Policy Configuration Tab
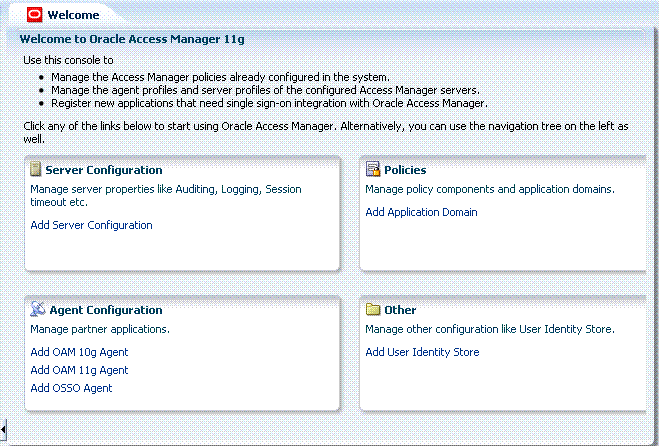
The OAM 11g Administration Console provides named function tabs on the left above the search controls and a menu and tool bar above the navigation tree. Open pages appear on the right. Currently the Welcome page is open.
Following topics provide more information:
Initially, the Welcome page is open and active on the right side of the console. Sections on the Welcome page include a brief description of a specific function and one or more "shortcuts" (links that you can select) to initiate certain tasks immediately as explained in Table 2-4.
Table 2-4 Welcome Page Quick Pick Sections
| Quick Pick Section | Description |
|---|---|
|
Server Configuration |
Click Add Server Configuration to launch a fresh Create: OAM Server page. See "About the System Configuration Tab" for more information. |
|
Policies |
Click Add Application Domain to launch a fresh Application Domains page. See "About the Policy Configuration Tab" for more information. |
|
Agent Configuration |
|
|
Other |
Click Add Identity Store to launch a fresh Create: User Identity Store page. |
Table 2-5 introduces the function-level tabs in the OAM 11g Administration Console.
Table 2-5 Function Tabs and Descriptions
| Function Tab Name | Description |
|---|---|
|
Policy Configuration |
Provides access to definitions for Shared Components and Application Domains. This tab is active and the related navigation tree is visible for browsing on the left side of the screen when you enter the console. See "About the Policy Configuration Tab" for more information. |
|
System Configuration |
Provides access to system-level definitions for Agents, Servers, and Data Sources. This is not the active tab when you enter the console, which is why it appears a different color. See "About the System Configuration Tab" for more information. |
|
Browse |
Provides the navigation tree from which you can access nodes and instances related to the active configuration tab (Policy or System). This tab is active when you enter the Administration Console. |
|
Search Results |
Provides access to the results of your latest search. Search controls appear above the Browse and Search Results tabs. For more information, see "Conducting Searches". |
The following topics provide more information about specific controls:
When the Browse tab is selected, the navigation tree for the active configuration tab (System Configuration or Policy Configuration tab) is visible. Named nodes identify groups under which you can choose individual instances on which to take action.
The nodes in the navigation tree for the Policy Configuration and System Configuration tabs are shown in Figure 2-7.
For more information, see the following topics:
A menu and tool bar appears above the navigation tree, as shown in Figure 2-8. Menus provide commands that you can use to take action on the selected item in the navigation tree. Many menu commands are also provided as command buttons in the tool bar for quick access.
Figure 2-8 Menu and Tool Bar Above the Navigation Tree
Table 2-6 provides a description of each command button in the tool bar. Buttons appear in color when they are available. When a command cannot be used, the command button (or menu item) appears in grey.
Table 2-6 Command Buttons in the Tool Bar
| Button | Definition | Description |
|---|---|---|
|
Refresh |
Revives the navigation tree, in the same way a Web browser refreshes a Web page. |
|
|
Create |
Opens a fresh page under the selected node in the navigation tree, which you can fill in to add a new configuration of the selected type. The new page opens as the active page on the right side of the navigation tree. This is available when you can add a new configuration, for instance, under Server Instances, or a specific Agent type, or a user identity store, or a non-HTTP Resource Type or Host Identifier or Application Domain. Alternatively, use the Create command on the Actions menu as described in Table 2-8. |
|
|
Duplicate |
Creates a copy of the selected configuration in the navigation tree, named "copy of original." The copy opens as the active page for immediate editing. Many fields are filled in. Exception: Fields that make up the unique identifier of the object (for example, Name of the policy or the URL pattern of a resource) are not automatically filled in. Note: You edit and save the duplicate as usual. |
|
|
Edit |
Opens the instance you have selected in the navigation tree, to view or modify. The configuration page opens as the active page on the right side of the navigation tree. Alternatively, double click the instance name to display a page for editing. |
|
|
Delete |
Removes the selected configuration. A deleted configuration is removed from the navigation tree and is no longer accessible to the system. For instance, if you delete an Agent configuration, the Agent is no longer registered and cannot be used. Alternatively, use the Delete command on the Actions menu as described in Table 2-8. |
|
|
Detach |
Separates the selected item (a results table on a configuration page, for instance) and displays it alone as a full page. Note: If you are viewing a detached table, you can click this button to re-attach it to the corresponding page and restore the standard page view. |
Figure 2-9 illustrates the View menu, which is available for use with both the Policy Configuration tab and the System Configuration tab.
Unavailable items (those that cannot be used on the selection in the navigation tree) appear in grey. View menu command descriptions are provided in Table 2-7.
Table 2-7 View Menu Command Descriptions
| Command | Description |
|---|---|
|
Expand |
Immediately reveal items within the selected node in the navigation tree. This does not open or activate a configuration page. Alternatively, click the icon beside the node in the navigation tree. |
|
Collapse |
Immediately conceal everything within the selected node in the navigation tree. This does not close an open page. Alternatively, click the icon beside the node in the navigation tree. |
|
Expand All Below |
Immediately reveal everything within the selected node. For example, click Application Domains and then click Expand All Below to see all application domains. |
|
Collapse All Below |
Immediately close the selected node and conceal its content. This does not close an open page. |
|
Expand All |
Immediately reveal all nodes and instances in the navigation tree. This has no impact on open pages. |
|
Collapse All |
Immediately conceal all nodes and instances in the navigation tree. This has no impact on open pages. |
|
Scroll to First Ctrl+Home |
Locates and displays the first item in the navigation tree or results table. |
|
Scroll to Last Ctrl+End |
Locates and displays the last item in the navigation tree or results table. |
This menu is available only when the System Configuration tab is active. Figure 2-9 illustrates the Actions menu, which provides appropriate commands for the selection in the navigation tree. For instance, if you have Server Instances selected in the navigation tree one of the commands on the Actions menu enables you to open the Server Common Properties page for viewing or editing.
Actions menu command descriptions are provided in Table 2-8. Certain commands on this menu mirror functions that are available by using command buttons in the tool bar. Unavailable items (those that cannot be used on the selection in the navigation tree) appear in grey.
Table 2-8 System Configuration, Action Menu, Command Descriptions
| Command | Description |
|---|---|
|
Open |
Opens the configuration page for the selected instance in the navigation tree. This is not available when you have a node selected in the navigation tree. Alternatively, double-click the instance name in the navigation tree to open a page. |
|
Create |
Activates a fresh page that you can fill in to define a new configuration. Alternatively, click the Create button in the tool bar as described in Table 2-6. |
|
Monitor |
Displays the monitoring page for the Agent selected in the navigation tree. For more information, see Chapter 15. |
|
Open common properties |
Opens the OAM Server Common Properties page, which provides various functional configurations shared among all OAM servers. This is available only when the Server Instances node is selected in the navigation tree. |
|
Delete |
Removes the selected instance registration. The deleted registration is removed from the navigation tree and is no longer accessible to the system. For instance, if you delete an agent registration, the Agent is no longer registered and cannot be used. Alternatively, click the Delete button in the tool bar as described in Table 2-6. |
Like the Welcome page, any open content pages appear on the right side of the console.
The active content page is visible and generally provides a work space where you can add, view, or modify related settings. A named tab identifies each open page, like the tabs on manila folders. The tab of the active page is white.
Up to ten pages can be open simultaneously per configuration tab: Policy Configuration tab or System Configuration tab. Only the named tabs of opened pages for the currently active configuration tab are shown.
Only the active page is visible, with as many named tabs of other open pages that can fit on one line. You can click a named tab to activate the corresponding page. When named tabs of open pages do not fit on one line, a pointer is provided that enables you to open and choose from a list of concealed pages. Figure 2-11 illustrates multiple pages open at the same time. You can see named tabs for each page and controls to access pages that are concealed (or to close the active page or close multiple pages).
Each page appears only once. No warning is issued if you attempt to open the same page multiple times. However, the page is only one time.
Note:
There is no warning if you open the page for the same item more than once.The controls that you can use with open pages are described in Table 2-9.
Table 2-9 Controls for Open Pages
| Page Control | Definition | Description |
|---|---|---|
 |
View a list of concealed pages |
Click the pointer to view the list of concealed pages when you cannot view all tabs simultaneously. |
|
Close Active Page |
Click this button to close the active page. Note: Closing a page before clicking Apply discards any changes or additions without warning. The changes are lost. You can use this to cancel changes you do not want to retain. |
|
|
Close Multiple Pages |
Note: Closing a page before clicking Apply discards any changes or additions without warning. The changes are lost. You can use this to cancel changes you do not want to retain. |
Pages in the Administration Console contain one or more graphical user interface elements as described in Table 2-10. For an example of each element n the Administration Console, see Figure 2-13 or log into the console and have a look.
Table 2-10 Page Elements and Descriptions
| Page Element | Description |
|---|---|
|
Named tab |
Identifies each open page on the right side of the console. Also, displays a page of related, lower-level settings. See Figure 2-14 for an example. |
|
Page controls |
Enables you to close one or more pages. See Table 2-9. |
|
Apply button |
Submits changes or additions made to the page. |
|
Named text box |
Enables you to enter relevant details in the named field using the keyboard. |
|
Option button |
Enables you to choose one of several options. For example, you can click an option button to define a state (Enabled vs. Disabled) or a security mode (Open vs. Simple vs. Cert). |
|
Tables |
Displays current specifications or space for new specifications. Tables have independent command buttons independent from page-level and option buttons. |
|
Command buttons for tables |
Enables you to: Add a fresh row. Remove the selected row. |
|
Drop down lists |
Provides a menu of choices on certain pages (and as part of the Search controls). You can choose one item from those listed. |
This section describes how to select the desired node or instance in the navigation tree, and selecting commands and page controls in the Administration Console. The usual selection guidelines apply.
Table 2-11 describes selections and controls.
Table 2-11 Selection Tasks and Controls
| Task | Control | Description |
|---|---|---|
|
Expand a node |
Click the Expand button beside the desired node in the navigation tree to reveal nodes or instances within it. |
|
|
Collapse a node |
Click the Collapse button beside the desired node in the navigation tree to conceal nodes or instances beneath it. |
|
|
Display View menu |
Right-click mouse button |
Right-click the desired node in the navigation tree to display a pop-up View menu. |
|
Select |
Click mouse button |
Click the desired item on which to operate. For example, click the desired:
|
|
Activate |
Click mouse button |
Click to activate the desired:
|
|
Open |
Double click mouse button |
Double-click an instance name to open the configuration page. For example, double-click a specific:
|
|
Highlight |
Drag cursor |
Drag the cursor across text in a box to highlight its content. |
This section provides a quick tour to orient you to major Oracle Access Manager functions:
Figure 2-12 shows the console. The Policy Configuration and System Configuration tabs appear on the left. Search controls appear directly beneath the Policy Configuration and System Configuration tabs. The navigation tree for the active (White) tab is identified by a Browse tab, which appears directly beneath the Search controls.
A tool bar separates the Browse and Search Results tabs from the navigation tree. The Actions menu is available only with the System Configuration tab; the View menu is always available. The active page appears on the right. The Welcome page is currently the active and open.
Figure 2-12 System Configuration Tab and navigation tree
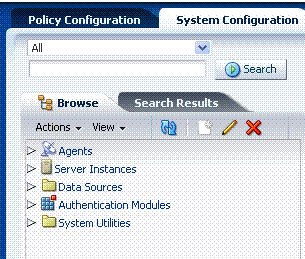
The System Configuration tab is currently active. It gives administrators access to Agent, Server, Data Source, and Authentication Module configuration details, and System Utilities. The navigation tree beneath the search controls and tool bar is related to the active tab.
See "Console Layout and Controls" for details on navigating and selecting command buttons, page controls, and menu items in the console.
You can also use commands on the View menu to expand the selected node in the navigation tree or to expand all nodes simultaneously. For instance, click Expand All from the View menu to see all nodes and related instances at one time.
Figure 2-13 provides an expanded view of nodes and instances on the System Configuration tab, navigation tree. A server instance is selected in the tree and the related configuration page appears on the right.
Figure 2-13 System Configuration: Expanded Tree (Left), Active Page (Right)
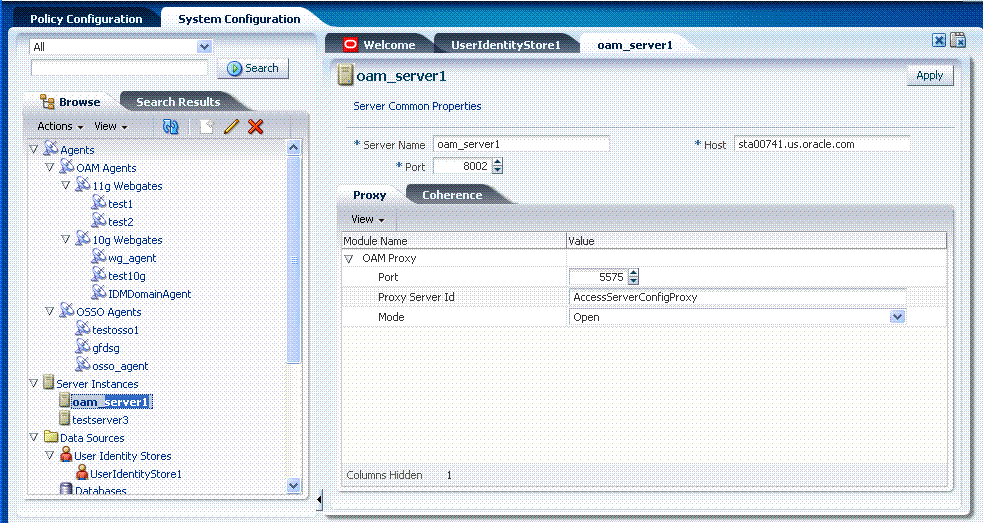
Figure 2-14 shows the OAM Server Common Properties page, which provides tabs for Auditing, SSO Engine, Session, Coherence, OAM Proxy, and Policy configuration details. This group of definitions is common to all Oracle Access Manager Servers. The Auditing Configuration tab is active and the relevant page is open on the right.
For more information about system configuration, see:
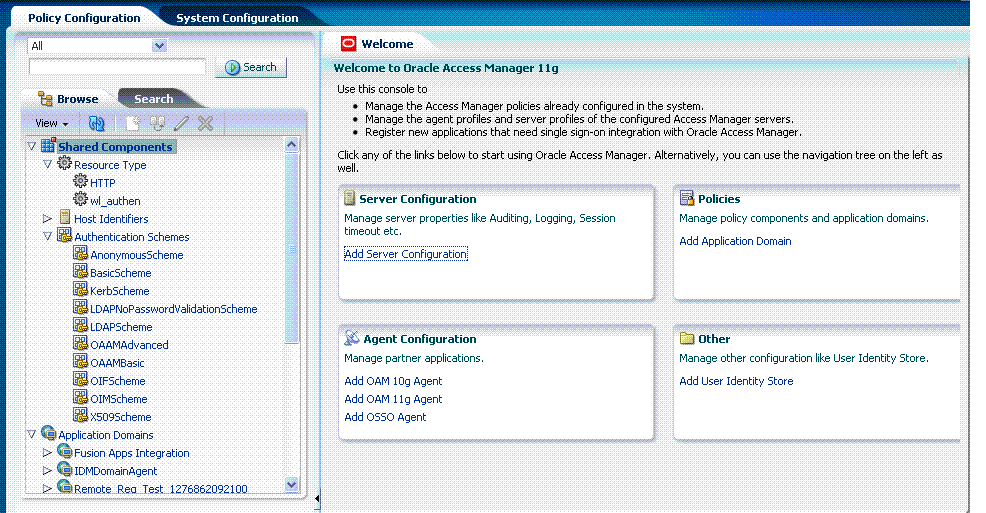
The Policy Configuration tab in the Oracle Access Manager Administration Console gives administrators access to application domain and shared component configurations. The view in Figure 2-15 lists first-level items beneath Shared Components and Authentication Schemes.
Figure 2-15 Policy Configuration Tab, Navigation Tree, and Active Page
See "Console Layout and Controls" for details on navigating and selecting command buttons, page controls, and menu items in the console.
You can also use commands on the View menu to expand the selected node in the navigation tree or to expand all nodes simultaneously. For instance, click Expand All from the View menu to see all nodes and related instances at one time.
See Also:
Part V, "Logging and Auditing"Administrators can view configuration details of individual agents, servers instances, data sources, shared components, and application domains from the OAM Administration Console.
In this example, you will view configuration details for an OAM Agent (WebGate). However, you can use similar steps to view configuration details for server instances, data sources, application domains, or shared components.
Alternatively, you can use custom WLST commands for OAM to view agent and server details.
To view configuration details using the Administration Console
Go to the Oracle Access Manager Administration console and log in as usual. For example:
https://hostname:port/oamconsole
In the sample URL, hostname refers to computer that hosts the Oracle Access Manager 11g Administration Console; port refers to the HTTP port number on which the console host listens; /oamconsole identifies the Administration Console.
Click the named tab that provides the configuration details you want to view. For example:
System Configuration
Either select Expand All from the View menu, or expand a node to view its content. For example:
Expand the Server Instances node, as described in Table 2-11, "Selection Tasks and Controls".
Double-click the instance name in the navigation tree to display the configuration page on the right.
View the page and note any specific details of interest.
Close the page by clicking the control in the upper-right corner.
This topic describes what you can search for and how to perform a search in the Administration Console.
Search controls are shown and described in Table 2-12.
Table 2-12 Search Control Definitions
| Search Control | Description |
|---|---|
 |
From the Policy Configuration Search menu, choose an item to define your search. |
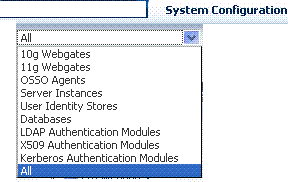 |
From the System Configuration Search menu, choose an item to define your search. |
 |
In the text field, enter the exact name of the instance you want to find. Click the Search button to initiate the search. Note: The name you enter in the field must be an exact match, including capitalization. No wild cards are allowed. |
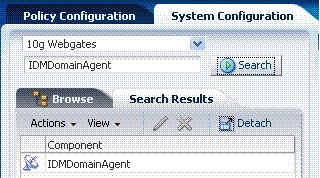 |
Click the Search Results tab to reveal the results of your search. Click a command button in the tool bar to remove the instance. The configuration page appears on the right side of the console. Click Detach in the tool bar to expand the table to a full page. Select a View menu item to alter the appearance of the results table. |
This topic describes how to perform a search using the capabilities in the Administration Console.
In the example in the following procedure, a search is conducted for an application domain. The procedure is generally the same, regardless of the type or instance you might choose.
To perform a search
Activate the Policy or System Configuration tab.
From the search type list, choose a type to define your search.
In the text field, enter the exact name of the instance you want to find. For example:
my_host_identifier
Click the Search button to initiate the search.
Click the Search Results tab to display the results table, and then:
Edit: Click the Edit command button in the tool bar to display the configuration page.
Delete: Click the Delete button in the tool bar to remove the instance; confirm removal when the Confirmation window appears.
Detach: Click Detach in the tool bar to expand the table to a full page.
View: Select a View menu item to alter the appearance of the results table.
Click the Browse tab to return to the navigation tree when you finish with the Search results.
At any time while using the Oracle Access Manager Administration Console, you can click the Help link at the top of the page to get more information. Online Help topics link to information in an online version of this book.
Online Help topics link to information in an online version of this book. Online Help procedures provide a brief introduction, followed by the procedure itself.
Generally speaking, topics that are displayed by selecting Help in the Administration Console appear in only English and Japanese languages. Online Help is not translated into the nine ADMIN languages.
You can click the Welcome tab to display a list of topics that describe actions you can take. For specific help topics, use the following procedure.
To locate a specific help topic
From the Administration Console, click a tab or named node in the navigation tree.
Click Help in the upper-right corner of the Administration Console.
Review the page that appears in a new window and select one of the following links to:
More—Click this link to view more information.
How?—Click this link to see steps to perform a task related to your help search.
Contents—In the left Help pane, expand Contents to see all help topics as well as all topics in the online manual.
Search—Displays a search window where you can enter your help search criteria.
Click the following buttons, as needed:
View—Displays a set of viewing options.
Arrows—Return to the previous page or go forward to the next page.
Printer Icon—Prints the page.
Envelope Icon—Emails the page.
Several command-line tools are available to perform various tasks using the keyboard rather than the Administration Console. After using these commands, configurations will be available in the Administration Console:
Remote registration tool, oamreg, enables remote registration of OAM Agents and OSSO Agents (mod_osso), and creation of default application domains.
Upgrade Assistant (UA) enables you to transfer OSSO 10g configuration to Oracle Access Manager 11g.
Oracle WebLogic Scripting Tool (WLST) provides a number of custom OAM command-line alternatives for tasks you can perform in the OAM Administration Console.
You can use the logging mechanism to capture critical Oracle Access Manager 11g component events. Logging is the mechanism by which Oracle Access Manager 11g components write messages to a file. These messages can be logged at different levels of granularity.
For more information, see Chapter 13, "Logging Component Event Messages".