| Oracle® Fusion Middleware Integration Guide for Oracle Access Manager 11g Release 1 (11.1.1) Part Number E15740-02 |
|
|
View PDF |
| Oracle® Fusion Middleware Integration Guide for Oracle Access Manager 11g Release 1 (11.1.1) Part Number E15740-02 |
|
|
View PDF |
This chapter describes how to integrate Oracle Access Manager with Oracle Identity Federation to create an authenticated session.
Sections include:
This section provides background about the integration procedure. Topics include:
About Oracle Identity Federation
Oracle Identity Federation is a standalone, self-contained federation server that enables single sign-on and authentication in a multiple-domain identity network.
The SP integration Engine included with Oracle Identity Federation consists of a servlet that processes requests from the server to create a user authenticated session at the IAM server. The engine includes several internal plug-ins that allow it to interact with different IAM servers, including Oracle Access Manager.
About the Integration
The integration described in this chapter configures Oracle Identity Federation to propagate the authentication state to Oracle Access Manager in SP mode.
In this mode, Oracle Identity Federation uses the federation protocols to identify a user, and requests the authentication module to create an authenticated session at Oracle Access Manager so that the user can access the requested resource, which is protected by WebGate.
The basic steps required to integrate Oracle Access Manager with Oracle Identity Federation are as follows:
Ensure that the necessary components, including Oracle WebLogic Server and Identity Management (IdM) components, are installed.
Register Oracle HTTP Server as a partner with the Oracle Access Manager server to protect a resource.
Configure the Oracle Identity Federation server to function as a service provider (SP) with Oracle Access Manager.
Configure the Oracle Access Manager server to delegate the authentication to Oracle Identity Federation.
Test the integration.
The remaining sections provide details about each step.
You must install the following components prior to undertaking the integration tasks:
Oracle WebLogic Server
Oracle HTTP Server 11g
Oracle Access Manager 11g
Oracle Identity Federation 11g
Note:
Refer to the Certification Matrix for platform and version details.Oracle WebLogic Server
Ensure that the administration and managed servers are up and running.
Oracle HTTP Server
For testing purposes, identify or create a resource to be protected; for example, create an index.html file to serve as a test resource.
Oracle Identity Federation
Access the Fusion Middleware Control console for the Oracle Identity Federation server using a URL of the form:
http://oif_host:oif_em_port/em
Verify that all the servers are running.
Follow these steps to register Oracle HTTP Server with Oracle Access Manager for authentication:
Note:
MW_HOME represents the Oracle Fusion Middleware Home directory.Before registering Oracle HTTP Server with Oracle Access Manager, try accessing the protected resource. For example, if you have the test resource index.html, access it as:
http://OHS host:OHS port/private/index.html
Locate the OSSORequest.xml file in the directory:
MW_HOME/Oracle_IDM1/oam/server/rreg/input
Make the necessary changes to the file.
Locate the oamreg.sh script, which resides in:
MW_HOME/Oracle_IDM1/oam/server/rreg/bin
Execute the script using this command string:
./oamreg.sh inband input/OSSORequest.xml
The script executed in Step 3 generates an osso.conf file in the directory:
MW_HOME/Oracle_IDM1/oam/server/rreg/output/<AgentName>
Copy the file to the following location:
Oracle_WT1/instances/instance1/config/OHS/ohs1/moduleconf/osso/
Locate the mod_osso.conf file in the directory:
Oracle_WT1/instances/instance1/config/OHS/ohs1/moduleconf
Add these directives to the file:
OssoSecureCookies offOssoConfigFile path_to_osso.conf_file
Uncomment the Location tag and fill in the protected resource path:
<Location /private>require valid-userAuthType Osso</Location>
Restart Oracle HTTP Server.
Oracle_WT1/instances/instance1/bin/opmnctl restartproc process-type=OHS
Try accessing the protected resource again. You should be redirected to the Oracle Access Manager server for authentication.
Take these steps to generate and load the metadata for the IdP and SP:
Locate the Oracle Identity Federation instance in Fusion Middleware Control.
Navigate to Administration, then Security and Trust.
Click the Provider Metadata tab.
In the Generate Metadata section of the page, using the Provider Type drop-down, select Service Provider.
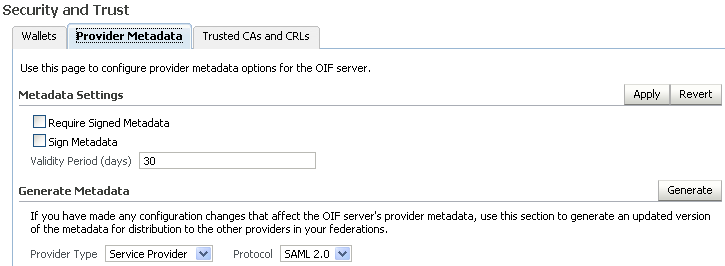
Click Generate. This creates metadata for the service provider.
Repeat Steps 4 and 5 to generate metadata for the identity provider.
Locate the Oracle Identity Federation instance in Fusion Middleware Control.
Navigate to Administration, then Federations.
Click Add. The Add Trusted Provider dialog appears.
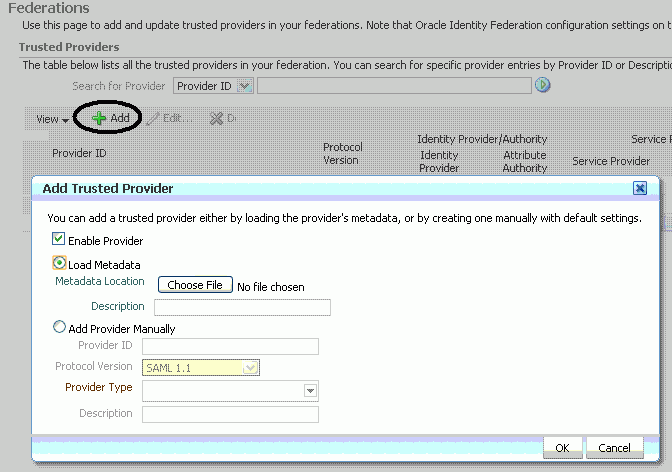
Check the Load Metadata box.
Click Choose File, and select the metadata file you generated for the IdP in Section 4.3.1, "Generated Provider Metadata".
Repeat the procedure to load metadata for the SP.
Both providers appear in the list of trusted providers:
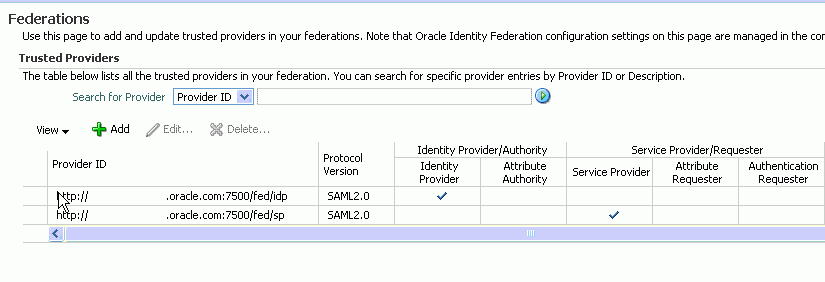
Locate the Oracle Identity Federation instance in Fusion Middleware Control.
Navigate to Administration, then Data Stores.
Specify the details of the user data store, as in this example:
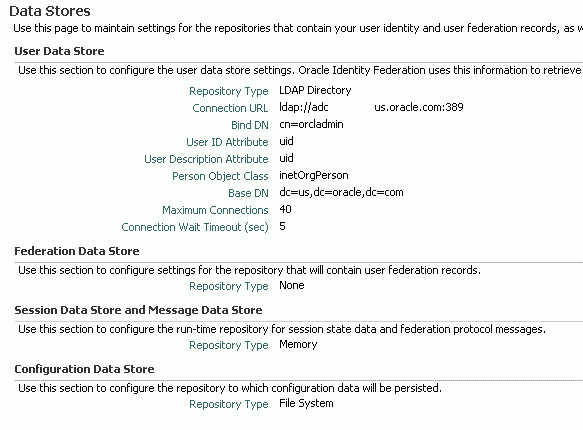
In this task, the authentication engine is configured to point to a user data store, enabling Oracle Identity Federation to validate users against that store.
Locate the Oracle Identity Federation instance in Fusion Middleware Control.
Navigate to Administration, then Authentication Engines.
in the Default Authentication Engine drop down, select LDAP Directory.
Enter the user data store that was configured in the previous task, Section 4.3.3, "Configure Data Store".
This task sets the IdP that was created in an earlier task as the default IdP.
Locate the Oracle Identity Federation instance in Fusion Middleware Control.
Navigate to Administration, then Service Provider.
Check the Enable Service Provider box.
For Default SSO Identity Provider, specify the IdP set up in Section 4.3.2, "Register the Providers".
Click Apply.
Having generated the IdP/SP metadata and registered those modules, the final task of configuring Oracle Identity Federation for the integration is to provide the Oracle Access Manager server details, so that Oracle Identity Federation can send assertion tokens and direct session management to Oracle Access Manager.
The steps to achieve this are as follows:
Locate the Oracle Identity Federation instance in Fusion Middleware Control.
Navigate to Administration, then Service Provider Integration Modules.
Select the Oracle Single Sign-On tab.
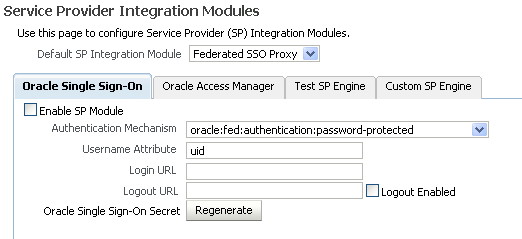
Configure the page as follows:
In the Default SP Integration Module drop-down, select Oracle Single Sign On.
Check the Enable SP Module box.
Configure these URLs:
Login URL : http://oam_host:oam_port/ngam/server/dap/cred_submit Logout URL : http://oam_host:oam_port/ngam/server/logout
where oam_host and oam_port are the host and port number of the Oracle Access Manager server respectively.
Click Regenerate.
This action generates a keystore file that contains the keys used to encrypt and decrypt the tokens that are exchanged between the Oracle Access Manager and Oracle Identity Federation servers.
Copy the keystore file to a location within the installation directory of Oracle Access Manager. Make a note of the location, since you will need to refer to it later.
As a result of performing the task in Section 4.2, "Register Oracle HTTP Server with Oracle Access Manager", clients seeking access to a protected resource are directed to Oracle Access Manager for authentication.
The final task in the integration procedure is to configure Oracle Access Manager to redirect the user to Oracle Identity Federation for authentication. The steps needed to achieve this are as follows:
Log in to the Oracle Access Manager Admin Console.
Select the Policy Configuration tab.
Protect the resource by selecting 'OIFScheme' in the Authentication Scheme drop-down.
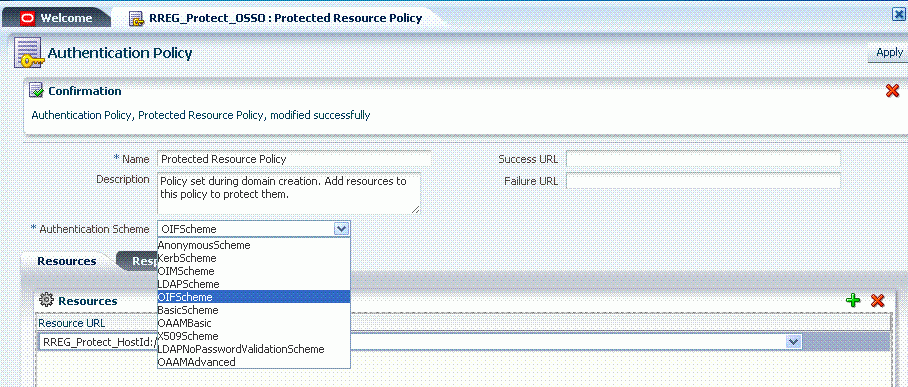
Click Apply.
Copy the keystore file to a directory under the middleware home in which the Oracle Access Manager server is installed.
Use a WLST command to update the OIFDAP partner block in the oam-config.xml configuration file. The syntax is as follows:
registerOIFDAPPartner(keystoreLocation=location of keystore file, logoutURL=logoutURL)
where logoutURL is the Oracle Identity Federation logout URL to invoke when the Oracle Access Manager server logs out the user.
For example:
registerOIFDAPPartner(keystoreLocation="/home/pjones/keystore", logoutURL="http://abcdef0123.in.mycorp.com:1200/fed/user/spsloosso?doneURL= http://abc1234567.in.mycorp.com:6001/ngam/pages/logout.jsp")
Verification
To verify the action you took in Step 6 above, examine the oam-config.xml file to confirm that the properties in the OIFDAPPartner block were updated as mandated in Step 6.
If the configuration is correct, a logout initiated from Oracle Access Manager should cause logout in Oracle Identity Federation.
You can test that the integration is correctly configured by taking these steps:
Try accessing the protected resource.
When set up correctly, you should be redirected to an Oracle Identity Federation login page.
Enter valid credentials on the login page.
Note:
The user should exist in both the Oracle Identity Federation Data Store and in the Oracle Access Manager Embedded LDAP store.Check that you are redirected to the protected page.
Verify that the following cookies are created:
OAM_ID ORA_OSFS_SESSION OHS Cookie