|
Oracle® Identity Management Integration Guide
10g Release 2 (10.1.2) Part No. B14085-01 |
|
 Previous |
 Next |
|
Oracle® Identity Management Integration Guide
10g Release 2 (10.1.2) Part No. B14085-01 |
|
 Previous |
 Next |
The Oracle Provisioning Service enables applications to receive provisioning information from Oracle Internet Directory.
This chapter contains these topics:
About the Oracle Directory Integration and Provisioning Server
Security and the Oracle Provisioning Service
|
See Also:
|
Provisioning involves:
Applications subscribing to receive changes to particular data in the directory
The directory sending those changes to the subscribing applications
At times, you may want to synchronize all entities in an application-specific directory with those in the central directory, but provision the application to receive notification about only some of them. For example, the directory for Oracle Human Resources typically contains data for all employees in an enterprise, and you would probably want to synchronize all of that data with the central directory. However, you might want to provision a given application to be notified only when members join or leave a particular group.
When it is first installed, an application subscribes to provisioning by creating a provisioning profile in the directory.
In a directory-enabled environment, provisioning involves:
Creating the user in the central directory
Enrolling the user in the application—that is, creating application-specific user accounts and entitlements
Synchronizing those accounts and entitlements with the central directory
For example, provisioning a user to access an e-mail application involves:
Creating the user in the central directory
Enrolling the user in the e-mail application. This involves setting up an e-mail account, specifying the quota for that user, and creating the necessary public folders.
Synchronizing the user information in the e-mail application with that in the central directory
You can change information for users, groups, and user subscriptions from any of the following:
Oracle Delegated Administration Services
Oracle Human Resources or other applications integrated with Directory Integration and Provisioning
Oracle Directory Manager
Oracle Enterprise Manager tools—for example, Enterprise Security Manager
User enrollment in an application can happen either automatically or manually.
This method is sometimes called "on-demand enrollment." Instead of continuously synchronizing with the central directory, the application creates the user footprint when the user first accesses the application. Oracle Application Server Single Sign-On uses this method to enroll a user accessing an application.
In this method, an administrator provides application-specific information by using an application-specific administrative tool.
For example, you might want users to obtain their manager's approval before enrollment. In this case, rather than use on-demand enrollment, you might want the application administrator, after the necessary approvals are complete, to enroll the user manually.
Provisioning a user typically involves creating two kinds of information:
Shared user metadata in Oracle Internet Directory
This data includes the user's identity, credentials, profiles, and preferences. It is represented by standard directory user attributes—for example, mailing address or language preferences.
Application-specific user data in the application
This could include, for example, data in the user's e-mail message folder, or, for the calendaring application, the user's appointment data. It is typically represented by using application-specific conventions either in the directory or in application-specific repositories.
This section describes how the components of an Oracle Provisioning Service environment interact throughout the provisioning process. It contains these topics:
How the Oracle Provisioning Service Retrieves Changes from Oracle Internet Directory
How an Application Registers with the Oracle Provisioning Service
How an Application Receives Provisioning Information from Oracle Internet Directory
How Oracle Internet Directory Receives Provisioning Information from an Application
How an Application Unsubscribes from the Oracle Provisioning Service
In an Oracle Provisioning Service environment:
Oracle Internet Directory acts as the central repository for all information for users, groups, and user subscriptions.
Applications subscribe to receive the provisioning events by creating provisioning profiles in the directory.
The Oracle Provisioning Service monitors Oracle Internet Directory for any changes to relevant information, and conveys these changes to applications in the form of provisioning events.
To retrieve changes from Oracle Internet Directory, the Oracle Provisioning Service subscribes to the Oracle Internet Directory change log. The changes in the change log are filtered so that only the needed changes get passed to the applications. If an application is interested only in the events of a particular subtree, then the Oracle Provisioning Service notifies it of those changes only.
Figure 12-1 shows the relation between components in an Oracle Provisioning Service environment.
Figure 12-1 Typical Deployment of The Oracle Provisioning Service Environment
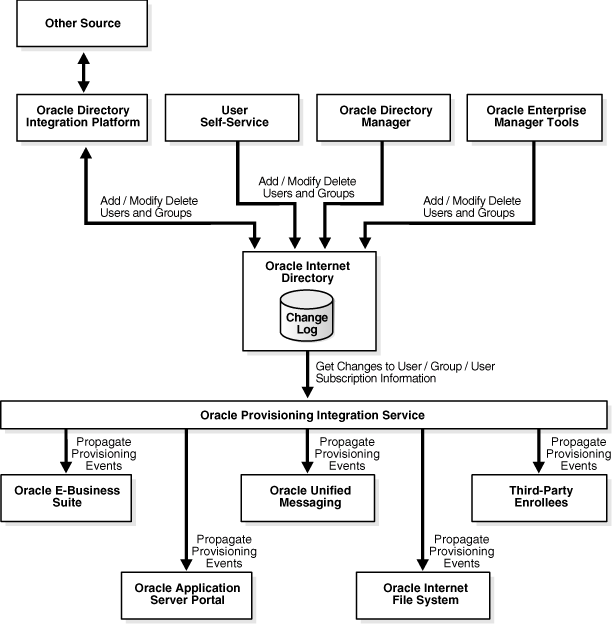
As Figure 12-1 shows:
Oracle Internet Directory acts as the central repository for all information for users, groups, and user subscriptions
Various components can add, modify, or delete user, group and user subscription entries in Oracle Internet Directory. These components are:
Directory Integration and Provisioning synchronizing with, for example, Oracle Human Resources or other repositories
The Oracle Delegated Administration Services
Oracle Directory Manager
Oracle Enterprise Manager tools—for example, the Enterprise Security Manager
The Oracle Internet Directory change log records these changes.
The Oracle Provisioning Service retrieves changes to information for users, groups, and user subscriptions from Oracle Internet Directory. It then sends those changes to subscribed applications. In this example, the applications are OracleAS Portal, Oracle Unified Messaging, Oracle Content Management Software Development Kit, and third-party enrollees.
After the application is installed and an application identity has been created in Oracle Internet Directory, application registration with the Oracle Provisioning Service can occur in one of two ways:
The application registers itself automatically during application installation by using the Provisioning Subscription Tool
The administrator manually registers it by using the Provisioning Subscription Tool.
This registration information includes:
The host name and port number of the Oracle directory server instance
The user name and password of the Oracle Internet Directory user
Information to register the application with Oracle Internet Directory
Information to register the database connect information with Oracle Internet Directory
Information for the Oracle Provisioning Service to service the application—for example, the kind of changes required, or scheduling properties
|
See Also: Appendix A, "Syntax for LDIF and Command-Line Tools" for instructions about how to use the Provisioning Subscription Tool |
The Oracle Provisioning Service monitors Oracle Internet Directory for any changes to user, group or user subscription information. It conveys these changes to applications in the form of provisioning events.
Figure 12-3 shows how an application receives the provisioning events from Oracle Internet Directory.
Figure 12-2 How an Application Receives Provisioning Information by Using the Oracle Provisioning Service
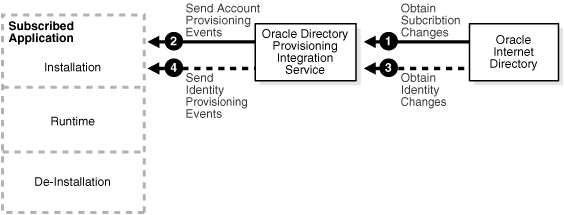
Provisioning information is sent from Oracle Internet Directory to an application by using the following process:
The Oracle Provisioning Service obtains from Oracle Internet Directory any changes to the subscription information for that application.
The Oracle Provisioning Service translates the subscription information to account provisioning events, which it periodically sends to the application. This information is based on application-specific database connect information.
The Oracle Provisioning Service obtains from Oracle Internet Directory any changes to the information about identities.
The Oracle Provisioning Service translates the changes to the information about identities to identity provisioning events, which it periodically sends to the application.
The way Oracle Internet Directory receives provisioning information from an application is the reverse of the way an application receives it from Oracle Internet Directory. That latter process was described in the previous section, "How an Application Receives Provisioning Information from Oracle Internet Directory".
Figure 12-3 shows how an application sends notifications of provisioning events to Oracle Internet Directory.
Figure 12-3 How Oracle Internet Directory Receives Provisioning Information from an Application
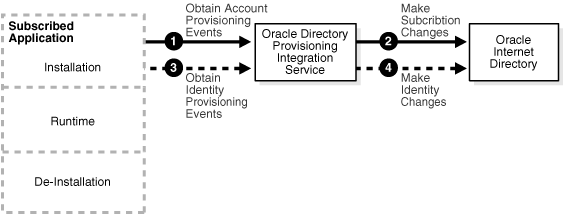
Provisioning information is sent from an application to Oracle Internet Directory by using the following process:
The Oracle Provisioning Service obtains from the application any account provisioning events for that application.
The Oracle Provisioning Service translates the account provisioning events to subscription changes, which it periodically sends to Oracle Internet Directory.
The Oracle Provisioning Service obtains from the application any identity provisioning events for that application.
The Oracle Provisioning Service translates the identity provisioning events to identity changes, which it periodically sends to Oracle Internet Directory.
You can unsubscribe an application from the Oracle Provisioning Service in one of two ways:
Let the application de-install itself automatically
Manually unsubscribe it by using the Provisioning Subscription Tool
|
See Also: "The Provisioning Subscription Tool (oidprovtool) Syntax" for instructions about how to use the Provisioning Subscription Tool |
The directory integration and provisioning server, the central component of Directory Integration and Provisioning, does the following:
Scheduling of connectors
The directory integration and provisioning server schedules connectors for synchronizing between Oracle Internet Directory and connected directories. If there is an agent, it also schedules the execution time of the agent.
Data import and export
The directory integration and provisioning server imports changes into and exports changes out of Oracle Internet Directory. DB, LDAP, LDIF, and tagged interfaces are supported.
Mapping
The Oracle directory integration and provisioning server includes a generic facility for filtering and mapping data to and from the connected directories. The directory integration and provisioning server maps attributes when exporting data to a connected directory and when interpreting data imported from a file or directory for input to Oracle Internet Directory.
The Oracle directory integration and provisioning server performs functions for both synchronization and provisioning. You can run multiple directory integration and provisioning server instances on any host.
This section describes the principal entities in the provisioning integration process and the privileges they need to complete various operations. It contains these topics:
There are important reasons to control access to the provisioning profiles of applications:
These profiles contain confidential information about the application—information that should not be viewable by unauthorized directory entities
Providing provisioning events to applications consumes system resources. You should therefore limit the number of those who can provision applications.
The access that you grant to entities to operate on profiles depends on the delegation needs of the applications. Entities that need controlled access to the provisioning profiles are:
The Oracle directory integration and provisioning server group—that is, cn=odisgroup,cn=odi,cn=oracle internet directory
Provisioning administrators—that is, cn=provisioning admins,cn=changelog subscriber,cn=oracle internet directory
Application Entities—that is, users for whom the value of the orclGUID attribute is orclODIPProvisioningAppGUID)
Provisioning profiles—that is, users identified by the DN of the provisioning profiles
All other users
Applications do not automatically have the rights to create provisioning profiles. Rather, only an LDAP identity with privileges to administer provisioning profiles can create them.
Provisioning administrators are modeled as a group and can perform any operation on the provisioning profiles. All other identities have lesser privileges.
Table 12-1 shows the entry-level privileges granted to each entity.
Table 12-1 Entry-Level Privileges
| User Category | Browse | Add | Delete | Explanation |
|---|---|---|---|---|
| Oracle directory integration and provisioning server
|
Yes | No | Yes | Oracle directory integration and provisioning servers need to:
However, Oracle directory integration and provisioning servers should not have access to add new provisioning profiles. |
| Provisioning administrators | Yes | Yes | Yes | The provisioning administrators group requires all privileges. |
| Application entities | Yes | No | Yes | Application entities themselves cannot create provisioning profiles, nor can they view another application's profiles. However, once a profile has been created, they can browse, modify, and delete their own profiles. |
| Provisioning profiles | Yes | No | No | Provisioning profiles also have an identity in the directory. For 10g Release 2 (10.1.2), this identity is not used, and hence it has the privilege only to perform a self-browse. |
| All other users | No | No | No | All other users should not be able to either browse, add, or delete provisioning profiles. |
Provisioning profiles contain security-sensitive attributes that need protection from unauthorized access. Table 12-2 describes them.
Table 12-2 Attribute Level Privileges Granted to Entities
| Attribute | Description |
|---|---|
userpassword
|
Stores the directory user password |
orclPasswordAttribute
|
Stores the clear text version of the directory user password |
orclODIPProfileInterfaceConnectInformation
|
Stores details of the connection information to the target application, including the password to the target system |
orclODIPProfileInterfaceAdditionalInformation
|
Stores any interface-specific information |
Table 12-3 describes the access control for the secure attributes for the main entities operating on the provisioning profiles.
Table 12-3 Access Control for Secure Attributes
| User Category | Read | Write | Search | Compare | Explanation |
|---|---|---|---|---|---|
| Oracle directory integration and provisioning servers | Yes | No | Yes | Yes | Oracle directory integration and provisioning servers need access to the secure attributes to complete their processing cycles. However, they do not need write access to them because these attributes should only be controlled by the Application Entities as well as Provisioning Admins. |
| Provisioning administrators | Yes | Yes | Yes | Yes | Provisioning administrators must be able to solve integration problems, and this requires full access to the secure attributes. |
| Application entities | Yes | Yes | Yes | Yes | Application entities are the real owners of the secure attributes, and this requires full access to the secure attributes. |
| Provisioning profiles | Yes | No | Yes | No | Provisioning profiles do not need to write or compare these attributes. As a result, they need only read and search privileges. |
| All other users | No | No | No | No | All other users receive no privileges. |
Table 12-4 shows the access control for all other attributes in the provisioning profiles.
Table 12-4 Access Control for All Other Attributes
| User Category | Read | Write | Search | Compare |
|---|---|---|---|---|
| Oracle directory integration and provisioning servers | Yes | Yes | Yes | Yes |
| Provisioning administrators | Yes | Yes | Yes | Yes |
| Application entities | Yes | Yes | Yes | Yes |
| Provisioning profiles | Yes | Yes | Yes | Yes |
| All other users | No | No | No | No |
Unlike secure attributes, the other attributes require a less strict access control. Full access is given to all entities involved in the provisioning process: Oracle directory integration and provisioning servers, provisioning administrators, application entities, and provisioning profiles. All other users receive no access to these attributes.