| Prev | Next | J2EETM Developer's Guide
Security |
update method in the Employee enterprise bean.
Before Bob runs the client, the J2EE administrator sets up the security as follows:
update method of the Employee enterprise bean.1. When the J2EE application client starts running it opens a dialog that prompts for the J2EE user name and password, which Bob enters.
2. The authentication service verifies that Bob's user name and password exist in the default realm.
3. Bob clicks the update button in the client, which attempts to invoke theupdatemethod of theEmployeeenterprise bean.
4. The EJB container performs authorization. It verifies that the RegularEmployee role, to which Bob's group (FullEmployee) belongs, has permission to invoke the update method.
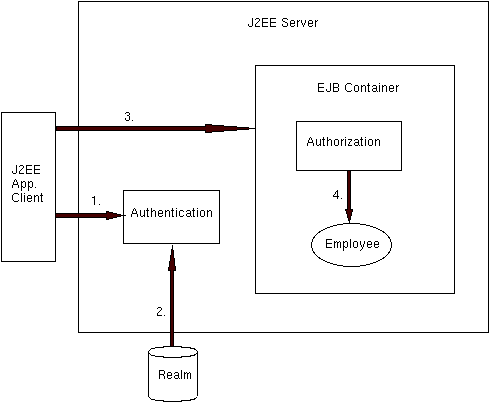
FIGURE 8-1 Authenticated Access to an Enteprise Bean
transfer method of the Account enterprise bean.
The J2EE administrator enforces security with these rules:
transfer method of the Account enterprise bean.1. Mary's browser attempts to access the JSP component.
2. Because the component is a protected resource, authentication is required. The Web service requests the Web browser to prompt for the J2EE user name and password.
3. Mary enters her J2EE user name and password, which are passed back to the J2EE server.
4. The authentication service verifies that the user name and password exist in the default realm.
5. The Web browser is allowed to access the JSP component.
6. Mary clicks the Transfer button on the form generated by the JSP component, which calls a JavaBeans component.
7. The JavaBeans component attempts to invoke thetransfermethod of theAccountenterprise bean.
8. Mary's J2EE group (CurrentCustomer) belongs to the Customer role, which is allowed to invoke the transfer method. Therefore, the EJB container authorizes the invocation.
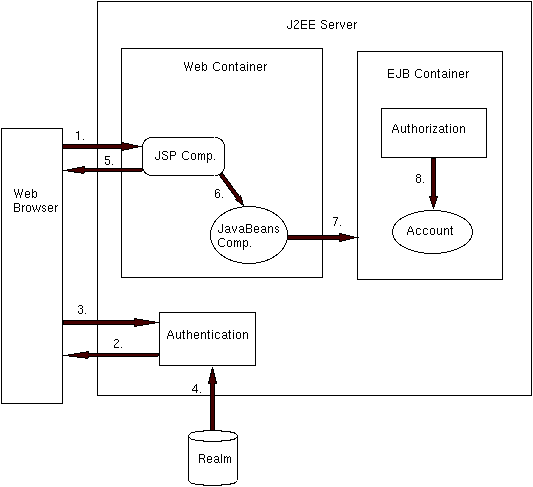
FIGURE 8-2 Authenticated Access to a JSP Component and an Enterprise Bean