| Oracle® Fusion Middleware System Administrator's Guide for Content Server 11g Release 1 (11.1.1) Part Number E10792-01 |
|
|
View PDF |
| Oracle® Fusion Middleware System Administrator's Guide for Content Server 11g Release 1 (11.1.1) Part Number E10792-01 |
|
|
View PDF |
After the Need to Know component has been installed, the NTK Configuration Information link is available through the Administration tray or menu. This link provides access to the NTK Configuration Information page, which provides security configuration status information and the capability to edit the security configuration.
The Need to Know component provides the following configuration pages:
The NTK Configuration Information page provides information about Need to Know content security configuration, search results configuration, and hit list roles configuration. This page also enables you to edit the security configuration, edit the search results configuration, edit the hit list roles configuration, view Idoc Script and hidden fields for the configuration, and test Idoc Script. To access this page, select Administration, then NTK Configuration Information from the main menu.
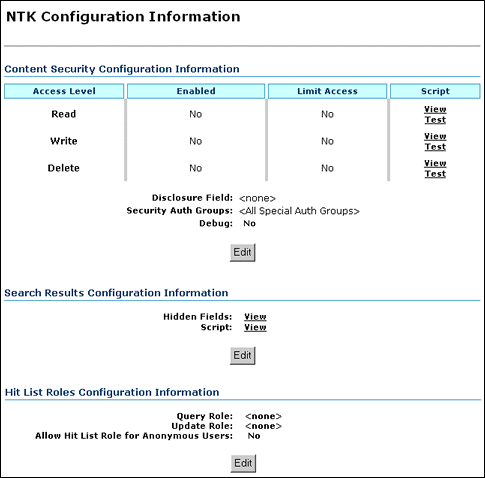
| Element | Description |
|---|---|
| Access Level column | Displays the permission levels (Read, Write, Delete) for access to content items. |
| Enabled column | Indicates whether Need to Know security is enabled for Read, Write, or Delete access.
No: Need to Know security is disabled for the access level. This is the default. Yes: Need to Know security is enabled for the access level. |
| Limit Access column | Specifies whether Read, Write, and Delete access is limited by Need to Know security. If Need to Know security is used to limit user access, it does so regardless of whether the user has standard Read, Write, or Delete access to a content item. If Need to Know security is not used to limit user access, the user has standard access to a content item. This feature enables you to create a security model more restrictive than the standard security model.
No: Access is not limited by Need to Know security. This is the default Yes: Access is limited by Need to Know security. |
| Script column | Provides links to view or test Idoc Script that is evaluated to determine if a user has Read, Write, or Delete access to a content item. The Need to Know component uses one of three parameters as a flag to determine if access is given:
Read access: isNTKReadAccess Write access: isNTKWriteAccess Delete access: isNTKDeleteAccess Click View in the row for the access level for which you want to view the Idoc Script that the Need to Know component evaluates to determine if a user has Read, Write, or Delete access. Click Test in the row for the access level for which you want to test the Need to Know security configuration. The NTK Test Content Security page is displayed. You can use this page to create and run a test of Idoc Script for security configuration. For more information, see "Test NTK Content Security Page". |
| Disclosure Field option | Displays the custom metadata field that is evaluated for the Idoc Script function isDisclosureQuery. The disclosure field can be used to create a content-specific query. The default value is <none>.
Use the Configuration Manager to create this field, and make it a memo field type. For more information, see "Installing the NTK Component" and "Configuring the NTK Component". When the disclosure field exists, an Update button is displayed next to the field where it appears on the Content Check In Form page. Click the button to access the Disclosure Query Security Applet (see "Disclosure Query Security Applet"). The applet helps you create queries based on the user metadata. |
| Security Auth Groups option | Displays a list of security groups for which Need to Know security is used. The groups must be a subset of the SpecialAuthGroups configuration variable. If no groups are selected, all SpecialAuthGroups are used. The default value for SpecialAuthGroups is <All Special Auth Groups>.
Use the Configuration Manager to specify a SpecialAuthGroups value in the config.cfg file. For more information, see "Installing the NTK Component" and "Configuring the NTK Component". |
| Debug option | Displays the status of the debugging option.
Yes: Debugging information is written to a log file for any security check that occurs for a content item. Users with the administrator role are not logged because they always receive access to the content item. No: Debugging information is not written to a log file. |
| Edit button | Displays the Content Security Configuration Information page, where the content security configuration can be changed |
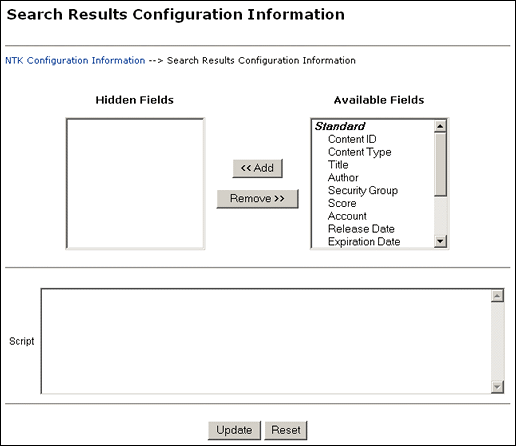
| Hidden Fields field | Click View to display a list of fields that can be hidden on the Search Results page. |
| Script field | Click View to display the Idoc Script that controls the presentation of the Search Results page. |
| Edit button | Displays the Search Results Configuration Information page, where the search results security configuration can be changed. |
| Query Role field | Displays the name of the query role, or <none>. This role is applied on the Search query page. |
| Update Role field | Displays the name of the update role, or <none>. This role is applied on a content check-in or update page. |
| Allow Hit List Role for Anonymous Users field | Applies the hit list role for anonymous users.
No: The hit list role is not applied for anonymous users. This is the default value. Yes: The hit list role is applied for anonymous users. |
| Edit button | Displays the Hit List Roles Configuration Information page, where the hit list roles security configuration can be changed. |
The Content Security Configuration Information page enables you to change security and access configuration for Read, Write, Delete, and other options for the Need to Know component. To access this page, click Edit in the Content Security Configuration Information area of the NTK Configuration Information page.
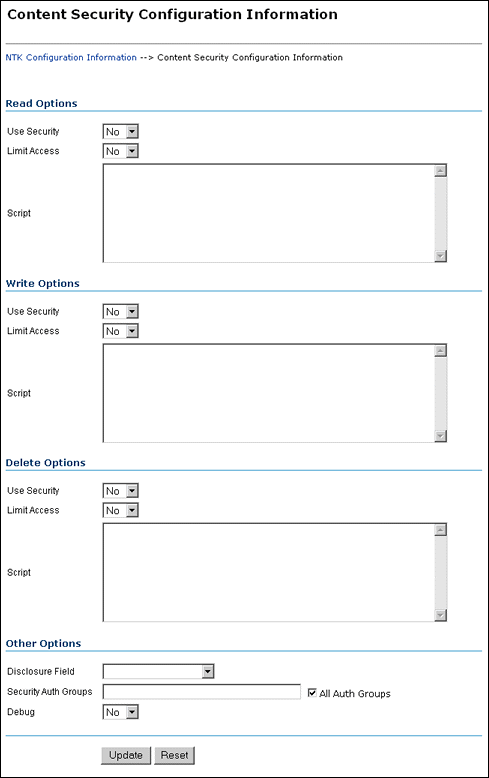
| Element | Description |
|---|---|
| Read Options: Use Security list | Use security as specified in the Script field.
No: Do not use Need to Know content security. This is the default value. Yes: Use Need to Know content security. |
| Read Options: Limit Access list | Limit access permissions as specified in the Script field.
No: Do not limit access permissions. This is the default value. Yes: Limit access permissions. |
| Read Options: Script field | Enter IdocScript in this field to specify the Need do Know security configuration for Read permission. |
| Write Options: Use Security list | Use security as specified in the Script field.
No: Do not use Need to Know content security. This is the default value. Yes: Use Need to Know content security. |
| Write Options: Limit Access list | Limit access permissions as specified in the Script field.
No: Do not limit access permissions. This is the default value. Yes: Limit access permissions. |
| Write Options: Script field | Enter IdocScript in this field to specify the Need to Know security configuration for Write permission. |
| Delete Options: Use Security list | Use security as specified in the Script field.
No: Do not use Need to Know content security. This is the default value. Yes: Use Need to Know content security. |
| Delete Options: Limit Access list | Limit access permissions as specified in the Script field.
No: Do not limit access permissions. This is the default value. Yes: Limit access permissions. |
| Delet Options: Script field | Enter IdocScript in this field to specify the Need to Know security configuration for Delete permission. |
| Other Options: Disclosure Field field | Select the name of a disclosure field from the list.This field is used to configure security in a content-specific query.
Note: If you create a metadata field for content item-level queries using the Configuration Manager, that field will appear as an option in the list. |
| Other Options: Security Auth Groups field | Enter the SpecialAuthGroups to be used in content-specific queries. If you use the General Configuration page to create a specific security group for the Need to Know component, you can specify the group here. If you need to add a security group, you can also edit the Additional Configuration Variables SpecialAuthGroups value in the config.cfg file. |
| Other Options: All Auth Groups check box | Specifies that the Need to Know component use all SpecialAuthGroups instead of a specific group listed in the Security Auth Groups field. This check box is selected by default.
Note: Other products such as Records Management can also use the SpecialAuthGroups variable. Be careful to specify only the security groups you want to use the Need to Know security configuration. |
| Other Options: Debug list | Select whether to use debugging to view security checking for a content item.
Yes: Debugging information is written to a log file for any security check that occurs for a content item. Users with the administrator role are not logged because they always receive access to the content item. When debugging is used, two additional options are visible: View and Clear. Click View to view the log file of debugging information. Click Clear to empty the log file of information. No: Debugging is not used and information is not written to a log file. This is the default value. |
| Update button | Updates the content security information to use the new settings, restarts the Content Server, and returns you to the NTK Configuration Information page. |
| Reset button | Returns the Content Security configuration settings to their last saved values. |
The Search Results Configuration Information page enables you to customize the search results that are returned from a search query. This does not affect what content items are returned, just how the results are displayed. To access this page, click Edit in the Search Results Configuration Information area of the NTK Configuration Information page.
The Hit List Roles Configuration Information page enables you to configure hit list roles for users. To access this page, click Edit in the Hit List Roles Configuration Information area of the NTK Configuration Information page.
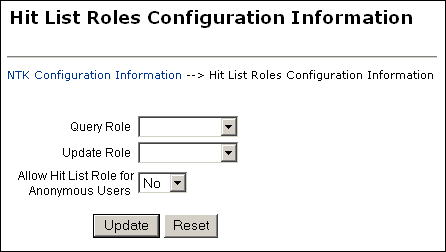
| Element | Description |
|---|---|
| Query Role field | Select the hit list role to be applied as the query role when the Search page is used. Security group roles with Read access are displayed in the list of selections, including any security group roles for which the user already has Read access.
This role is separate from content security. You could have a content item appear in Search results configured for content security, but the user would not be able to view the Content Information page for that item. |
| Update Role field | Select the hit list role to be applied as the update role when the Update page is used. Security group roles with Write access are displayed in the list of selections, including any security group roles for which the user already has Write access. When the content item is actually checked in or updated, this role is not applied.
This field is probably most useful in conjunction with content security. For examples of using this field,see "Security Customization Samples". |
| Allow Hit List Role for Anonymous Users field | Applies the hit list roles for anonymous users.
No: Do not apply the hit list roles for anonymous users. This is the default value. Yes: Apply the hit list roles for anonymous users. |
| Update button | Updates the hit list configuration, restarts the Content Server, and returns you to the NTK Configuration Information page. |
| Reset button | Returns the Hit List Roles configuration settings to their last saved values. |
The Test NTK Content Security page enables you to run a test security script for a user. To access this page, click Test in the Script column for one of the access permission levels displayed on the NTK Configuration Information page.
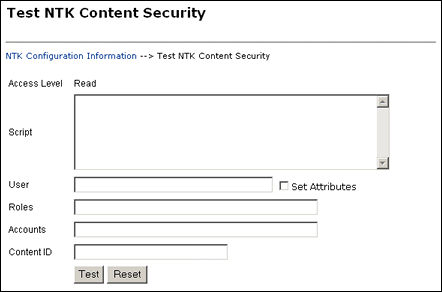
| Element | Description |
|---|---|
| Access Level field | Displays the access level for the permissions level you select to test: Read, Write, or Delete. |
| Script field | Enter Idoc Script for the content security configuration to be tested. |
| User field | Enter the user ID for the test. |
| Set Attributes check box | Select the check box to automatically set the user attributes to match the user's existing attributes. |
| Roles field | Enter the roles assigned to the user for the test. Use this field if you are testing with external users where attributes may not be accessible. |
| Accounts | Enter the accounts assigned to the user for the test. Use this field if you are testing with external users where attributes may not be accessible. |
| Content ID | Enter the content ID for the test. |
| Test button | Click Test to test the configuration specified on the Test NTK Content Security page. The Need to Know component test returns results on whether the user has the specified access, whether Need to Know security was used, and if Need to Know security was not used then the reason why. |
| Reset button | Returns the Test NTK Content Security configuration settings to their last saved values. |