| Oracle® Fusion Middleware Administrator's Guide for Oracle Access Manager 11g Release 1 (11.1.1) Part Number E15478-02 |
|
|
View PDF |
| Oracle® Fusion Middleware Administrator's Guide for Oracle Access Manager 11g Release 1 (11.1.1) Part Number E15478-02 |
|
|
View PDF |
This chapter describes how to provision and manage OAM Server instance registrations using the Oracle Access Manager 11g Administration Console. The following topics are included:
Ensure that the following environmental considerations are met:
A new Managed Server has been added to the domain using either the Oracle WebLogic Server Administration Console or WLST commands.
The Oracle JRF Template was applied to the Managed Server (or cluster) if needed. For details, see Oracle Fusion Middleware Administrator's Guide.
Oracle recommends that you review the "Introduction to OAM Server Registration and Management".
This section introduces Oracle Access Manager server instance registration and management in the following topics:
Table 4-1 summarizes server-side differences between Oracle Access Manager 11g, OAM 10g, and OracleAS SSO 10g (extracted from the overall comparison in Table 2-1).
Table 4-1 Summary: Server-side Differences with OAM 11g versus OAM 1g versus OSSO 10g
| OAM 11g | OAM 10g | OSSO 10g | |
|---|---|---|---|
|
Server-side components |
|
|
|
|
Cryptographic keys The protocols used to secure information exchange on the Internet. |
|
One global shared secret key per WebGate |
|
|
Keys storage |
|
Global shared secret stored in the directory server only (not accessible to WebGate) |
|
Administrators can add one or more Managed Servers to the WebLogic Server domain for use with Oracle Access Manager 11g. When using the WebLogic Configuration Wizard, the OAM Server is automatically registered with OAM 11g. However, if the configuration wizard was not used, the OAM Server must be registered with the OAM 11g to open a communication channel.
Alternatively. You can use custom WLST commands for OAM to display, edit, or delete a server registration Any changes are automatically propagated to the OAM Administration Console and to every OAM Server in the cluster.
Only OAM Servers are registered with OAM 11g. The OAM Administration Console on the WebLogic Administration Server is not registered with itself.
Regardless of the method used to register an OAM Server, the details (also known as a registration) are organized under the System Configuration tab in the OAM Administration Console. OAM Server registration details within the OAM Administration Console include:
Server name, Host, Port
Proxy: Performs as the legacy Access Server and defines the communication security mode. For more information, see:
Oracle Coherence: Provides a distributed cache for various OAM services, including session data.
Administrators can search for a specific instance registration, register a newly installed OAM Server, view, modify, or delete server registrations using the Oracle Access Manager Administration Console. For more information, see "About the OAM Server Registration Page".
Oracle Access Manager 11g server-side components maintain backward compatibility with existing Oracle Access Manager 10g policy-enforcement agents (OAM 10G WebGates and AccessGates) and OracleAS SSO 10g mod_osso (known as OSSO Agents in 11g).
Legacy OAM 10g SSO: The OAM Proxy can accept requests from multiple Access clients concurrently and enables all WebGates and AccessGates to interact with Oracle Access Manager 11g services. For more information, see "OAM Proxy Page".
Legacy OracleAS 10g (OSSO): The integrated OSSO proxy handles token generation and validation in response to token requests during authentication using OSSO Agents with OAM 11g. The OSSO proxy needs no configuration. Simply register the OSSO agent with OAM 11g as described in Chapter 5 and Chapter 6.
You can upgrade OracleAS SSO to use OAM 11g SSO when you have a legacy deployment where OAM 10g is integrated and used in combination with OracleAS (OSSO) 10g.
After upgrading OSSO to use OAM 11g, you can have OAM 10g WebGates operating with OAM 11g SSO the same deployment. In this situation, the OAM Proxy forwards requests to either the OAM 10g Access Server or to OAM 11g services as needed.
The OAM 10g ObSSOCookie is an encrypted session-based single sign-on cookie that is generated when a user authenticates successfully. The OAM 10g ObSSOCookie stores user identity information, which you can cache if needed.
The integrated OAM Proxy supports the AES encryption algorithm of the 10g ObSSOCookie to enable backward compatibility with release 10g WebGates. The 10g Access Server can decrypt the cookie created by the OAM 11g Proxy (and vice versa). This allows OAM 11g to perform authentication and OAM 10g to perform authorization (and vice versa).
Note:
An OAM 11g ObSSOCookie created by OAM Proxy is compatible with the ObSSOCookie created by an Oracle Access Manager 10g Access Server.For more information, see "OAM Proxy Page".
Communication modes for the OAP channel include:
Open: Use this unencrypted mode if communication security is not an issue in your deployment.
Simple: Use this Oracle-signed certificate mode if you have some security concerns, such as not wanting to transmit passwords as plain text, but you do not manage your own Certificate Authority (CA).
Cert: Use if you want different certificates on OAM Servers and WebGates and you have access to a trusted third-party CA.
On each individual OAM Server registration, the security mode is defined on the Proxy tab, as described in "About the OAM Server Registration Page".
Simple and Cert modes also require:
Security passwords that are common to all OAM Servers and WebGates, as described in "Managing Common OAM Proxy Simple and Cert Mode Security".
Appropriately signed X.509 digital certificates, as described in Appendix E, "Securing Communication with OAM 11g".
At least one OAM Server instance must be running in the same mode as the agent during agent registration. Otherwise, agent registration fails. After agent registration, however, you can change the communication mode of the OAM Server. Communication between the agent and server would continue to work as long as the WebGate mode is at least at the same level as the OAM Server mode or higher. The agent mode can be higher but cannot be lower. For example, of OAM Server mode is Open, agents can communicate in any of the three modes. If OAM Server mode is Simple, agents can use Simple or Cert mode. If OAM Server mode is Cert, agents must use Cert mode.
Using the OAM 11g Administration Console, you can view and modify global settings that all OAM Servers share in common, including those for the SSO Engine, Policy Store, Session Management, Auditing, and Oracle Coherence.
For more information, see "Introduction to Managing OAM Server Common Properties".
This section describes how to register and manage OAM Server instances using the Oracle Access Manager Administration Console. Topics here include:
Users with valid OAM Administrator credentials can register a freshly installed Managed Server (OAM Server instance) or modify an existing OAM Server registration using the Oracle Access Manager Administration Console.
Alternatively: You can use custom WLST commands for OAM to register and manage OAM Server instances. Changes are reflected in the OAM Administration Console and are automatically propagated to every OAM Server in the cluster.
Figure 4-1 illustrates a typical OAM Server registration page when viewed within the Oracle Access Manager Administration Console.
Figure 4-1 OAM Server Registration Page with Proxy Tab
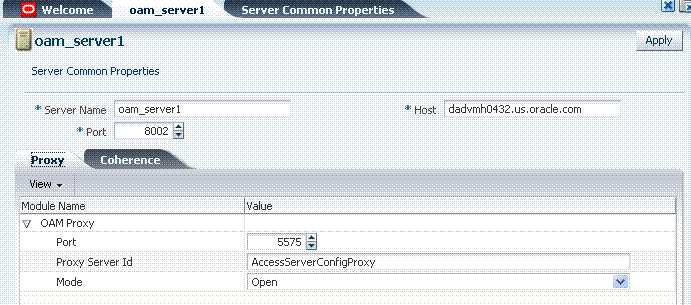
Individual server registration settings are described in Table 4-2.
Table 4-2 OAM Server Instance Settings
| Element | Definition |
|---|---|
|
Server Common Properties |
Links to the OAM Server Common Properties page. See Also: "Introduction to Managing OAM Server Common Properties". |
|
Server name |
The identifying name for this server instance, which was defined during initial deployment in the WebLogic Server domain. |
|
Host |
The full DNS name (or IP address) of the computer hosting the server instance. For example: host2.company.com. |
|
Port |
The port on which this server communicates (listens and responds). Default: 5575 Note: If both the SSL and Open ports of the Managed Server are enabled, then the Managed Server is set to the SSL port by default.If you must use the non-SSL port, the credential collector URL the authentication scheme must be set to the absolute URL which points to 'http' as the protocol and non-SSL port. |
|
Proxy |
See "OAM Proxy Page" |
|
Coherence |
An integrated proxy server (OAM Proxy) is installed with each Managed Server for Oracle Access Manager (OAM Server). The OAM Proxy is used as a legacy Access Server to provide backward compatibility for OAM 10g Agents that are registered with OAM 11g. The Agent can be freshly installed or currently operating within an OAM 10g SSO deployment.
Each OAM Proxy instance requires a different port. The proxy starts listening when the application starts. Registered access clients can immediately communicate with the proxy.
The OAM Proxy handles both configuration and run-time events. Each OAM Proxy can accept requests from multiple access clients concurrently. Each OAM Proxy enables OAM access clients to interact with Oracle Access Manager 11g services. This includes:
10g (10.1.4.3) WebGates
10g (10.1.4.2.0) WebGates
10g (10.1.4.0.1) WebGates
11g WebGates (needs no proxy)
Note:
For AccessGates, OAM 11g provides authentication and authorization functionality only. Policy modification through AccessGates is not supported.OAM Proxy settings consist of the details in Table 4-3.
Table 4-3 OAM Proxy Settings for an Individual OAM Server
| OAM Proxy Setting | Type | Value |
|---|---|---|
|
WebLogic Port |
int (integer) |
The port on which the Oracle WebLogic Server is listening, which is used by the proxy to redirect the user for credential collection. |
|
Port |
int (integer) |
The unique port on which this OAM Proxy instance is listening. |
|
Proxy Server ID |
The identifier of the computer on which the OAM Proxy (and this OAM Server instance) resides. DNS hostname is preferred; however, you can use any valid and relevant string. |
|
|
Mode |
OAM channel transport security for the OAM Proxy can be one of the following (the agent mode must match during registration and can be higher after registration):
Note: Simple and Cert transport security modes are governed by information defined on the OAM Server Common Properties OAM Proxy tab, as described in "Managing Common OAM Proxy Simple and Cert Mode Security". See Also: Appendix E if you are configuring Simple or Cert transport security modes. |
OAM Proxy Logging: Oracle Access Manager 11g components use the same logging infrastructure as any other Oracle Fusion Middleware 11g component, as described in Chapter 14. However, OAM Proxy uses Apache log4j for logging.
Coherence provides replicated and distributed (partitioned) data management and caching services on top of a reliable, highly scalable peer-to-peer clustering protocol. Coherence has no single points of failure; it automatically and transparently fails over and redistributes its clustered data management services when a server becomes inoperative or is disconnected from the network.
When a new server is added, or when a failed server is restarted, it automatically joins the cluster and Coherence fails back services to it, transparently redistributing the cluster load. Coherence includes network-level fault tolerance features and transparent soft re-start capability to enable servers to self-heal.
Coherence modules consist of the values, and types for the individual server instance, as shown in Figure 4-1.
WARNING:
Oracle recommends that you do not modify Oracle Coherence settings for an individual server unless you are requested to do so by an Oracle Support Representative.
Table 4-4 Default Coherence Settings for Individual OAM Servers
| Coherence Module | Type of Entry | Description and Default Values |
|---|---|---|
|
LogLevel |
String |
The Coherence log level (from 0 to 9) for OAM Server events. |
|
LogPort |
int (integer) |
The listening port for Coherence logging on the WebLogic Server. |
|
LogLimit |
String |
The Coherence log limit |
Coherence Logging: Appears only in the WebLogic Server log. There is no bridge from Oracle Coherence logging to Oracle Access Manager logging. For Oracle Fusion Middleware 11g logging infrastructure details, see Chapter 14.
Users with valid OAM Administrator credentials can perform the following procedure to search for an OAM Server registration using the Administration Console.
Prerequisites
The OAM Server must be registered in the Oracle Access Manager Administration Console.
To locate an individual server instance registration
Activate the System Configuration tab.
From the search type list, choose the Server Instances type to define your search.
In the text field, enter the exact name of the instance you want to find. For example:
my_OAM_Server
Click the Search button to initiate the search.
Click the Search Results tab to display the results table, and then:
Edit: Click the Edit command button in the tool bar to display the configuration page.
Delete: Click the Delete button in the tool bar to remove the instance; confirm removal in the Confirmation window.
Detach: Click Detach in the tool bar to expand the table to a full page.
View: Select a View menu item to alter the appearance of the results table.
Click the Browse tab to return to the navigation tree when you finish with the Search results.
Users with valid OAM Administrator credentials can perform the following task to register a new Managed Server (OAM Server) instance using the OAM Administration Console.
Note:
Each OAM Server must be registered to communicate with agents.Prerequisites
The new Managed Server instance must be configured in the Oracle WebLogic Server domain, but not yet started.
See Also:
To register an OAM Server instance
Install the new Managed Server instance and configure it in the Oracle WebLogic Server domain, but do not start this instance.
Log in to the OAM Administration Console as usual.
From the Welcome page, Server Configuration panel, click the Add Server Configuration link to open a fresh page.
Alternatively: From the System Configuration tab, click Server Instances then click the Create button in the tool bar to open a fresh page.
On the Create: OAM Server page, enter details for your instance, as described in Table 4-2:
Server name
Host
Port
Proxy: Enter or select details for this OAM Proxy instance, as described in Table 4-3:
WebLogic Port:
Port
Proxy Server ID
Mode (Open, Simple, or Cert)
See Also:
Appendix E if you are using Simple or Cert modeCoherence: Oracle recommends that you do not modify Oracle Coherence settings for an individual server instance unless you are requested to do so by an Oracle Support Representative.
Click Apply to submit the configuration, which should appear in the navigation tree (or close the page without applying changes).
Start the newly registered server.
Users with valid OAM Administrator credentials can perform the following task to view or modify settings for an individual server instance using the Administration Console. For instance, you might decide to change a listening port or the Proxy communication transport security mode.
Changes are immediately visible in the OAM Administration Console and propagated to all OAM Servers in the cluster.
See Also:
To view or modify a server instance registration
From the System Configuration tab, navigation tree, click to expand the Server Instances node.
Double-click the desired instance name to display its configuration, and then proceed as follows:
View Only: Close the page when you finish viewing details.
Modify: Perform remaining steps to edit the configuration.
On the Create: OAM Server page, enter details for your instance, as described in Table 4-2.
Proxy: Enter or select details for this OAM Proxy instance, as described in Table 4-3.
See Also:
Appendix E if you are using Simple or Cert modeCoherence: Oracle recommends that you do not modify Oracle Coherence settings for an individual server instance unless you are requested to do so by an Oracle Support Representative.
Click Apply to submit the changes (or close the page without applying change).
Users with valid OAM Administrator credentials can perform the following task to delete a server registration, which disables the OAM server.
To delete a server registration
From the System Configuration tab, navigation tree, click to expand the Server Instances node.
Double-click the desired instance name to confirm details, then close the page.
Click the desired instance name, click the Delete button in the tool bar, and confirm removal in the Confirmation window.
Confirm that the instance is removed from the navigation tree.
Finalize server instance removal by removing the instance from the WebLogic Server Administration Console.
The Node Manager on Managed Server host handles the rest automatically.
OAM Server Common Properties apply to all OAM Server instances. This section provides the following topics about common server and common single sign-on (SSO) Engine settings:
OAM Server Common Properties apply to all OAM Server instances. A number of common properties tabs appear on the OAM Server Common Properties page:
Figure 4-3 shows the OAM Server Common Properties page and named tabs.
Figure 4-3 OAM Server Common Properties Page
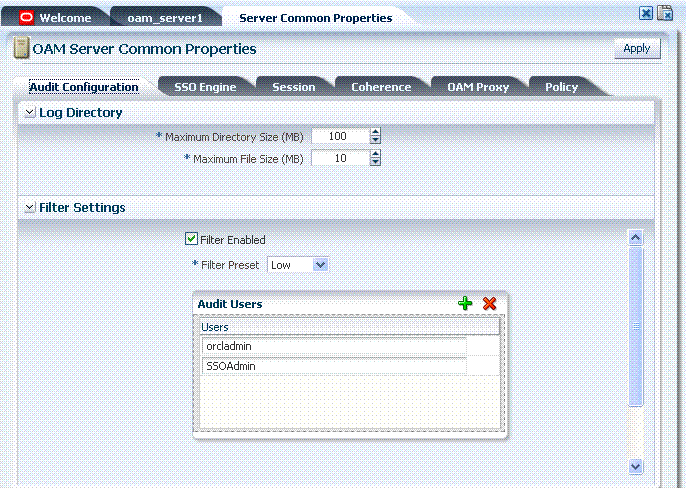
The Audit Configuration tab is open when you display OAM Server Common Properties. Common tabs and functionality are described in Table 4-5. Administrators can control and specify certain auditing parameters from this tab. Oracle Access Manager auditing configuration is recorded in the file oam-config.xml.
Table 4-5 OAM Server Common Properties Tabs
| Tab Name | Description |
|---|---|
|
Audit Configuration |
Oracle Access Manager supports auditing for a large number of administrative and run-time events, uniform logging and exception handling, and the diagnostics of all audit events. For details about configuring auditing, see Chapter 14, "Auditing OAM Administrative and Run-time Events". |
|
SSO Engine |
Single sign-on enables users, and groups of users, to access multiple applications after a single sign-on and successful authentication. SSO eliminates multiple log ins. For more information, see "Managing the Common SSO Engine". |
|
Session |
Session management refers to the process of managing the lifecycle requirements of a user session, and notification of session events to enable global logout. Global logout is required for OSSO Agents (mod_osso) to ensure that logging out of a session on any entity propagates the logout to all entities. For more information, see Chapter 12, "Managing Sessions". |
|
Coherence |
Common Oracle Coherence settings shared by all OAM Servers differ from those for individual OAM Servers. However, in both cases Oracle recommends that you make no adjustments to these settings unless instructed to do so by an Oracle Support Representative. See Also: "Using Oracle Coherence for Troubleshooting". |
|
OAM Proxy |
During initial deployment, the Simple mode global passphrase or the Cert (certificate) mode keystore alias and password are defined. For more information, see "Managing Common OAM Proxy Simple and Cert Mode Security". |
|
Policy |
During runtime policy evaluation, the Resource Matching Cache maps the requested URL to the policy. |
See Also:
Details for other operations common to all OAM components:Users with valid OAM Administrator credentials can perform the following task to display OAM Server Common Properties pages.
To display OAM Server Common Properties pages
From the System Configuration tab, navigation tree, double-click Server Instances to display the OAM Server Common Properties page and tabs.
Alternatively: Click the Server Common Properties link at the top of an individual server registration page.
Click the named tab that identifies the configuration details you want and refer to additional information as described in Table 4-5.
This section provides the following details:
Table 4-6 outlines the similarities between Simple and Cert modes.
Table 4-6 Summary: Simple and Cert Mode
| Artifact or Process | Simple Mode | Cert Mode | Open Mode |
|---|---|---|---|
|
X.509 digital certificates only. |
X |
X |
N/A |
|
Communication between OAM Agents and OAM Servers is encrypted using Transport Layer Security, RFC 2246 (TLS v1). |
X |
X |
N/A |
|
For each public key there is a corresponding private key that Oracle Access Manager stores in a file: |
aaa_key.pem generated by openSSL |
aaa_key.pem generated by your CA |
N/A |
|
Signed certificates in Privacy Enhanced Mail (PEM) format |
aaa_cert.pem generated by openSSL |
aaa_cert.pem generated by your CA |
N/A |
|
During OAM Server configuration, secure the private key with a Global passphrase or PEM format details, depending on which mode you are using. Before an OAM Server or WebGate can use a private key, it must have the correct passphrase. |
Global passphrase stored in a nominally encrypted file:
|
PEM format:
|
N/A |
|
During OAM Agent or OAM Server registration, the communication mode is propagated to the OAM 11g Administration Console. |
Same passphrase for each WebGate and OAM Server instance. |
Different passphrase for each WebGate and OAM Server instance. |
N/A |
|
The certificate request for the WebGate generates the certificate request file, which you must send to a root CA that is trusted by the OAM Sever. The root CA returns the WebGate certificates, which can then be installed either during or after WebGate installation. |
cacert.pem The certificate request, signed by the Oracle-provided openSSL Certificate Authority |
aaa_req.pem The certificate request, signed by the your Certificate Authority |
N/A |
|
Encrypt the private key using the DES Algorithm. For example: openssl rsa -in aaa_key.pem -passin pass: -out aaa_key.pem -passout pass: passphrase -des
|
N/A |
X |
N/A |
|
Agent Key Password |
N/A |
Enter a password during agent registration (see Table 5-5). |
N/A |
|
During Agent registration, ObAccessClient.xml is generated in: $DOMAIN_HOME/output/$Agent_Name/ |
ObAccessClient.xml Copy to: 11g WebGate: 11gWebGate_instance_dir/ 10g WebGate: $WebGate_install_dir/ |
ObAccessClient.xml Copy to: 11g WebGate: 11gWebGate_instance_dir/ 10g WebGate: $WebGate_install_dir/ |
ObAccessClient.xml Copy to: 11g WebGate: 11gWebGate_instance_dir/ 10g WebGate: $WebGate_install_dir/ |
|
During Agent registration, password.xml is generated in: $DOMAIN_HOME/output/$Agent_Name/ See Also: Appendix E |
password.xml Copy to: 11g WebGate: 11gWebGate_instance_dir/ 10g WebGate: $WebGate_install_dir/ |
password.xml Copy to: 11g WebGate: 11gWebGate_instance_dir/ 10g WebGate: $WebGate_install_dir/ |
N/A |
|
During Agent registration, aaa_key.pem is generated in: $DOMAIN_HOME/output/$Agent_Name/ See Also: Appendix E |
aaa_key.pem Copy to: 11g WebGate: 11gWebGate_instance_dir/ 10g WebGate: $WebGate_install_dir/ |
aaa_key.pem Copy to: 11g WebGate: 11gWebGate_instance_dir/ 10g WebGate: $WebGate_install_dir/ |
N/A |
The OAM Proxy tab on the OAM Server Common Properties page is where administrators can configure Simple or Cert communication security for use by all server instances and WebGates. Figure 4-4 illustrates the settings on this tab.
Table 4-7 describes the settings required for Simple or Cert mode configurations.
Table 4-7 Server Common OAM Proxy Secure Communication Settings
| Mode | Description |
|---|---|
|
Simple Mode Configuration |
The global passphrase for Simple mode communication using OAM-signed X.509 certificates. This is set during initial OAM Server installation. Administrators can edit this passphrase and then reconfigure all existing OAM Agents to use it, as described in"Viewing or Editing Simple or Cert Settings for OAM Proxy". |
|
Cert Mode Configuration |
Details required for the KeyStore where the Cert mode X.509 certificates signed by an outside Certificate Authority reside:
Note: These are set during initial OAM Server installation. The certificates can be imported using the import certificate utility or the keytool shipped with JDK. Administrators can edit the alias and password and then reconfigure all existing OAM Agents to use it, as described in"Viewing or Editing Simple or Cert Settings for OAM Proxy". |
OAM Administrators can use this procedure to confirm or alter settings for the common OAM Proxy.
See Also:
To view or edit Simple or Cert mode settings for the OAM Proxy
From the System Configuration tab, navigation tree, double-click Server Instances to display the Server Common Properties page.
Alternatively: From the server instance registration page, click the Server Common Properties link.
Click the OAM Proxy tab.
Simple Mode Configuration: Specify the Global Passphrase.
Cert Mode Configuration: Specify the following details.
PEM Keystore Alias
PEM Keystore Alias Password
Click Apply to submit the changes and dismiss the Confirmation window (or close the page without applying changes).
This section explains:
See Also:
"About Run Time Resource Evaluation"Figure 4-5 illustrates the OAM Server Common Properties Policy tab. This tab provides settings for the Resource Matching Cache and the Authorization Result Cache, which come into play during policy evaluation at run time.
Table 4-8 outlines these global settings that apply to all servers and requests.
Table 4-8 Policy Evaluation Caches
| Element | Description |
|---|---|
|
Resource Matching Cache |
Caches mappings between the requested URL and the policy holding the resource pattern that applies to the URL. Default Values:
|
|
Authorization Result Cache |
Caches policy decisions for the requested URL and user. Default Values:
|
OAM Administrators can use this procedure to manage the OAM Server common runtime policy evaluation caches.
To manage common runtime policy evaluation cache settings
From the System Configuration tab, navigation tree, double-click Server Instances.
Alternatively: From a server instance registration page, click the Server Common Properties link.
On the Server Common Properties page, click the Policy tab.
Resource Matching Cache: Specify details and click apply (Table 4-8).
Authorization Result Cache: Specify details and click apply (Table 4-8).
Click Apply to submit the changes and dismiss the Confirmation window (or close the page without applying changes).