10g (9.0.4)
Part Number B10851-01
Home |
Solution Area |
Contents |
Index |
| Oracle® Application Server Single Sign-On Administrator's Guide 10g (9.0.4) Part Number B10851-01 |
|
This chapter examines those aspects of OracleAS Single Sign-On that are dependent upon Oracle Internet Directory. The directory is the repository for all single sign-on user accounts and passwords--administrative and nonadministrative. All user and group management functions are handled by the directory.
The chapter contains the following topics:
Use the following tools to manage single sign-on users:
Oracle Delegated Administration Services is a self-service application that enables administrators to manage users and groups. For example, you can create and delete users and change passwords.
You can access Oracle Delegated Administration Services with a URL of this form:
http://host:port/oiddas/
where host is the name of the computer on which the Oracle Delegated Administration Services server is located, and port is the port number of the server. In a typical infrastructure installation, Oracle Delegated Administration Services and OracleAS Single Sign-On have the same host name.
Oracle Directory Manager is a Java-based tool for managing most functions in Oracle Internet Directory. Use it to configure password policies.
You can use command-line tools like ldapmodify in place of Oracle Delegated Administration Services and Oracle Directory Manager. These tools operate on text files. They take arguments that use the Lightweight Directory Interchange format.
The single sign-on user password is stored in Oracle Internet Directory as an attribute of the user's entry. Users can change their passwords either in the single sign-on UI or by going to Oracle Delegated Administration Services. Oracle Directory Manager enables the directory administrator to adjust password expiry behavior to suit enterprise needs.
This section covers the following topics:
Oracle Directory Manager has fields that enable you to specify the minimum number of characters that a password requires. To learn what the defaults are, see Oracle Internet Directory Administrator's Guide.
Using either Oracle Directory Manager or LDAP command-line tools, you can configure password life and can specify when users are prompted to change their passwords. You can also configure a grace login period for users. This is a period after which the user's password has expired. If the user neglects to change his password within this period, he must have an administrator reset it for him.
Users who try to log in when their passwords have expired or are about to expire experience the following server behavior:
The user is shown the password expiry screen. He or she must contact the directory administrator and have the password reset.
The user is shown the change password page. He has the option of cancelling the page or changing his password. In either case, authentication proceeds in the same manner as it does when the change password page is not thrown.
If a grace login period has been configured in the directory, the user is presented the change password page after her password has expired. She has the option of cancelling the page or changing her password. In either case, the authentication sequence is the same as it is for users with valid passwords.
OracleAS Single Sign-On does not support force change password. This feature prompts users to change their password after it has been reset by an administrator. On the directory side, you enable force change password by setting the pwdMustChange attribute.
An account lockout occurs when users are unable to access the single sign-on server from any number of workstations because they have submitted the incorrect user name and password combination more times than is permitted by Oracle Internet Directory. By default, this number is 10. Once the limit has been reached, even a valid user name and password combination fails to log the user in.
Because single sign-on user accounts are managed in the directory, the directory administrator determines account lockout policies. Oracle Directory Manager has fields for enabling and disabling lockout and for specifying lockout duration.
The default lockout duration is one day.
To learn how to unlock users, see Oracle Internet Directory Administrator's Guide.
To learn how to configure password policies, see Oracle Internet Directory Administrator's Guide.
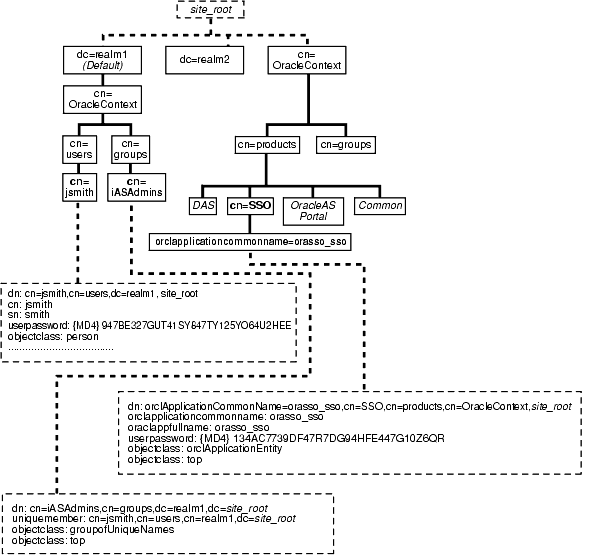
OracleAS Single Sign-On, like other components in the OracleAS complement, has its own "container" within the directory information tree (DIT). This container is found within the Oracle Context, an entry that serves as the root for all Oracle-specific data. In the simplified DIT shown in Figure 3-1, both the root Oracle Context and the realm-specific Oracle Context are expanded. The root Oracle Context is the repository for sitewide information--that is, information that applies to all identity management realms and products. Structurally, realm-specific Oracle Contexts are mirror images of the root context, but the information they contain pertains only to a particular realm. These realms store configuration information unique to specific users and other network entities. To learn more about realms, see Chapter 10, "Enabling Support for Application Service Providers".
In Figure 3-1, the single sign-on container is identified by the entry cn=SSO. It contains a single entry, orclApplicationCommonName=orasso_sso. This is the entry for the single sign-on server. In the illustration, the entry has been expanded to show the object classes and attributes that define the entry. For example, the orclapplicationcommonname attribute gives the default name for the single sign-on server, orasso. Note, too, that the single sign-on server has its own password, which, along with orclapplicationcommonname, the directory server uses to authenticate the single sign-on server when the latter performs user searches.
The container Common is a repository for information common to all OracleAS products. For instance, it contains attributes that enable products to identify the realm search base, or node, and the realm nickname. Realm-specific Common containers--not shown here--contain attributes that enable products to locate users within a realm subtree. In addition to expanding the SSO container, the illustration expands entries for an OracleAS user who is also an administrator.
The ssooconf.sql script enables you to change the following settings in the directory:
To change directory settings for the single sign-on server:
orasso. To obtain the schema password, see Appendix B.
SQL> @ssooconf.sql
The script displays updated settings for the single sign-on server.
If you run the script and then decide not to make changes, press Return or Enter to retain existing values.
The single sign-on server caches metadata about the Oracle Internet Directory DIT. This metadata includes the user search base, user nickname attribute, and realm-related metadata. In the event that the directory DIT changes, the cache for the single sign-on server must be refreshed. This is effected by running the ssoreoid.sql script.
SQL> connect orasso/orasso_password
See Appendix B to obtain the schema password.
SQL> @ssoreoid.sql
These are just a few of the DIT changes that require that the script be run:
To learn how realm information is changed in Oracle Internet Directory, see Oracle Internet Directory Administrator's Guide.
|
|
 Copyright © 1996, 2003 Oracle Corporation. All Rights Reserved. |
|