10g (9.0.4)
Part Number B10851-01
Home |
Solution Area |
Contents |
Index |
| Oracle® Application Server Single Sign-On Administrator's Guide 10g (9.0.4) Part Number B10851-01 |
|
This chapter explains how to deploy OracleAS Single Sign-On for automatic sign-on, or Windows native authentication, from a Windows desktop. The terms automatic sign-on and Windows native authentication are interchangeable. For the remainder of the document, the latter term is used.
The chapter contains the following topics:
Windows native authentication is an authentication scheme for those who use Internet Explorer on Windows 2000. When this feature is enabled in OracleAS Single Sign-On, users log in to single sign-on partner applications automatically using Kerberos credentials obtained when the user logs in to a Windows 2000 computer.
Using the SPNEGO protocol, browsers that are Internet Explorer 5.0 and greater can automatically pass the user's Kerberos credentials to a Kerberos-enabled Web server when the server request these credentials. The Web server can then decrypt the credentials and authenticate the user.
Although SPNEGO supports both Kerberos version 5 and NTLM authentication schemes, OracleAS release 9.0.4 supports only Kerberos version 5 with SPNEGO.
The following steps, illustrated in Figure 8-1, describe what happens when a user tries to access a single-sign-on-protected application:
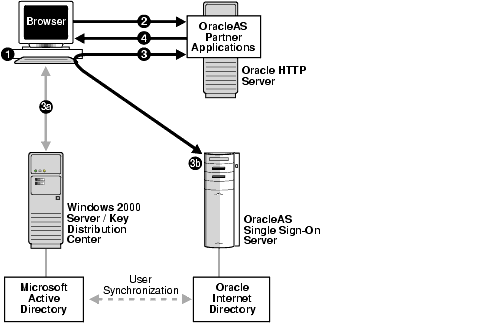
The user logs out of this application and single sign-on applications accessed subsequently by logging out of the Windows computer.
Windows native authentication is intended for intranet Web applications. Your intranet deployment must have the following:
Setting up Windows native authentication requires that Oracle Internet Directory, the single sign-on server, and the user's browser all be configured.
Perform these configuration tasks in the order listed:
Consult documentation for the Windows 2000 server to ensure that Microsoft Active Directory is set up and working.
Install Oracle Internet Directory and OracleAS Single Sign-On. To determine which deployment configuration suits your installation, see Chapter 9, "Advanced Configurations". For installation instructions, see Oracle Application Server 10g Installation Guide.
User entries in Oracle Internet Directory must be synchronized with user entries in Microsoft Active Directory. To learn how to synchronize Oracle Internet Directory with Microsoft Active Directory, see Oracle Internet Directory Administrator's Guide.
See Oracle Internet Directory Administrator's Guide.
Complete the following tasks to configure the single sign-on server.
Configure a kerberos realm on the single sign-on middle tier; then create a service account for the single sign-on server in Microsoft Active Directory. Finally, create a keytab file for the single sign-on server, mapping the service principal to the account name.
[libdefaults] default_realm = ADUSERS.ACME.COM [realms] ADUSERS.ACME.COM = { kdc = kdc.acme.com } [domain_realm] .acme.com = ADUSERS.ACME.COM
where ADUSERS.ACME.COM is the default realm of Microsoft Active Directory, kdc.acme.com is the host name of the KDC, and .acme.com is the DNS domain name of the UNIX computer. Be sure to replace the example values given with values suitable for your installation. These values appear in boldface in the example.
88/udp and 88/tcp on the Windows 2000 server. When added correctly to the /etc/services file, the entries for these port numbers look like this:
kerberos5 88/udp kdc # Kerberos key server kerberos5 88/tcp kdc # Kerberos key server
130.111.111.111 sso.acme.com sso loghost
Enter the name of the single sign-on host, omitting the domain name. If, for example, the host name is sso.acme.com, you enter only sso. This is the account name in Active Directory.
Note the password that you assigned to the account. You will need it later. Do not choose User must change password at next logon.
C:> Ktpass -princHTTP/sso.acme.com@ADUSERS.ACME.COM -passpassword-mapusersso-out sso.keytab
where -princ is the service principal. This value must be specified using the format HTTP/single_sign-on_host_name@KERBEROS_REALM_NAME. Note that HTTP and the Kerberos realm must be uppercase.
-pass is the account password that you obtained in step 4. -mapuser is the account name of the single sign-on middle tier. You created this account in step 4. -out is the output file that stores the service key.
Again, be sure to replace the example values given with values suitable for your installation. These values appear in boldface in the example.
Be sure to give the Web server uid on the single sign-on middle tier read permission for the file.
-Djavax.security.auth.useSubjectCredsOnly=false -Doracle.security.jazn.config=$ORACLE_HOME/j2ee/OC4J_ SECURITY/config/jazn.xml
These configurations should be added to the OC4J_SECURITY process configuration section of opmn.xml. Here is an example configuration for the OC4J_SECURITY process in the file.
<process-type id="OC4J_SECURITY" module-id="OC4J"> . . . <data id="java-options" value="-server -Djava.security.policy=$ORACLE_ HOME/j2ee/OC4J_SECURITY/config/java2.policy -Djava.awt.headless=true -Xmx512m -Djavax.security.auth.useSubjectCredsOnly=false -Doracle.security.jazn.config=$ORACLE_HOME/j2ee/OC4J_ SECURITY/config/jazn.xml"/> . . . </process-type>
<jazn provider="XML" location="./jazn-data.xml" />
In the XML entry, KeyTab designates the location of the keytab file. principal is the service principal name for the single sign-on server. For consistency, the example keytab file and principle have been retained in the entry. Be sure to replace the values that appear in boldface with actual values.
You can either cut and paste the entry provided here or copy and paste the sample file, $ORACLE_HOME/sso/conf/wna-jazn-data.xml.
<jazn_data> <jazn-loginconfig> . . . <application> <name>com.sun.security.jgss.accept</name> <login-modules> <login-module> <class>com.sun.security.auth.module.Krb5LoginModule</class> <control-flag>required</control-flag> <options> <option> <name>debug</name> <value>false</value> </option> <option> <name>addAllRoles</name> <value>true</value> </option> <option> <name>useKeyTab</name> <value>true</value> </option> <option> <name>keyTab</name> <value>Oracle_home/j2ee/OC4J_SECURITY/config/sso.keytab</value> </option> <option> <name>principal</name> <value>HTTP/sso.acme.com</value> </option> <option> <name>doNotPrompt</name> <value>true</value> </option> <option> <name>storeKey</name> <value>true</value> </option> </options> </login-module> </login-modules> </application> . . . </jazn-loginconfig> </jazn-data>
Cut and paste the entry provided here or copy and paste the sample file located at $ORACLE_HOME/sso/conf/wna-web.xml.
<web-app> . . . <security-role> <role-name>{{PUBLIC}}</role-name> </security-role> <security-constraint> <web-resource-collection> <web-resource-name>SSO</web-resource-name> <url-pattern>auth</url-pattern> </web-resource-collection> <!-- authorization --> <auth-constraint> <role-name>{{PUBLIC}}</role-name> </auth-constraint> </security-constraint> <!-- authentication --> <login-config> <auth-method>BASIC</auth-method> </login-config> . . . </web-app>
<orion-application> . . . <security-role-mapping name="{{PUBLIC}}"> <group name="{{PUBLIC}}" /> </security-role-mapping> <jazn provider="LDAP" location="ldap://directory_server.domain:port" default-realm="default_realm_in_Oracle_Internet_Directory"> <jazn-web-app auth-method="WINDOWS_KERBEROS_AUTH"/> <property name="kerberos-servicename" value="HTTP@sso.acme.com"/> </jazn> . . . </orion-application>
Edit the MediumSecurity_AuthPlugin parameter to look like this:
MediumSecurity_AuthPlugin = oracle.security.sso.server.auth.SSOKerbeAuth
Configure Internet Explorer to use Windows native authentication. Depending upon your browser, configuration is a three-part process:
http://sso.mydomain.com
If you are using Internet Explorer 6.0, perform steps 1 through 12 in "Internet Explorer 5.0 and Greater"; then add the following steps:
Only browsers that are Internet Explorer 5.0 or greater support SPNEGO-Kerberos authentication. OracleAS Single Sign-On provides fallback authentication support for unsupported browsers such as Netscape Communicator. Depending upon the type of browser and how it is configured, the user is presented with the single sign-on login form or the HTTP basic authentication dialog box. In either case, he or she must provide a user name and password. The user name consists of the Kerberos realm name and the user ID. It must be entered this way:
domain_name\user_id
For example:
acme\jdoe
Note that the user name and password are case sensitive. Note, too, that password policies for Microsoft Active Directory do not apply.
Fallback authentication is performed against Microsoft Active Directory, using an external authentication plugin for Oracle Internet Directory.
Users may encounter a number of different login behaviors within Internet Explorer depending upon which version they are using. Table 8-1 shows under what circumstances automatic sign-on and fallback authentication are invoked.
|
|
 Copyright © 1996, 2003 Oracle Corporation. All Rights Reserved. |
|