|
Oracle® Identity Management Guide to Delegated Administration
10g Release 2 (10.1.2) B14086-01 |
|
 Previous |
 Next |
|
Oracle® Identity Management Guide to Delegated Administration
10g Release 2 (10.1.2) B14086-01 |
|
 Previous |
 Next |
This chapter describes Oracle Delegated Administration Services, a framework consisting of pre-defined, Web-based units for building administrative and self-service consoles. These consoles can be used by delegated administrators and users to perform specified directory operations.
It contains these topics:
Installing and Configuring Oracle Delegated Administration Services
Starting and Stopping Oracle Delegated Administration Services
Creating Applications by Using Oracle Delegated Administration Services
Configuring Oracle Delegated Administration Services in an Existing Oracle Home
Configuring Oracle Delegated Administration Services in a New Oracle Home
Configuring Oracle Delegated Administration Services with Load Balancers in a Different DNS Domain
Configuring Load Balancers for Multiple Instances of Oracle Delegated Administration Services
Configuring Oracle Delegated Administration Services in a Replication Environment
Delegated administration is an important feature of the Oracle Identity Management infrastructure. It enables you to store all data for users, groups, and services in a central directory, while distributing the administration of that data to various administrators and end users. It does this in a way that respects the various security requirements in your environment.
Suppose, for example, that your enterprise stores all user, group, and services data in a central directory, and requires one administrator for user data, and another for the e-mail service. Or suppose that it requires the administrator of Oracle Financials to fully control user privileges, and the administrator of OracleAS Portal to fully control the Web pages for a specific user or group. Delegated administration as provided by the Oracle Identity Management infrastructure enables all of these administrators with their diverse security requirements to administer the centralized data in a way that is both secure and scalable. The following privileges can be delegated with Oracle Delegated Administration Services:
Creation, editing, and deletion of users and groups
Assignment of privileges to users and groups
Management of services and accounts
Configuration of Oracle Delegated Administration Services
Resource management of Oracle Reports and Oracle Application Server Forms Services
|
See Also: The chapter on delegation of privileges for an Oracle technology deployment in Oracle Internet Directory Administrator's Guide for more information about delegated administration |
Oracle Delegated Administration Services is a set of pre-defined, Web-based units for performing directory operations on behalf of a user. It frees directory administrators from the more routine directory management tasks by enabling them to delegate specific functions to other administrators and to end users. It provides most of the functionality that directory-enabled applications require, such as creating a user entry, creating a group entry, searching for entries, and changing user passwords.
You can use Oracle Delegated Administration Services to develop your own tools for administering application data in the directory. Alternatively, you can use the Oracle Internet Directory Self-Service Console, a tool based on Delegated Administration Services. This tool comes ready to use with Oracle Internet Directory.
This section contains these topics:
Applications built by using Oracle Delegated Administration Services enable you to grant a specific level of directory access to each type of user. For example, look at Figure 1-1, which shows the various administrative levels in a hosted environment.
Figure 1-1 Administrative Levels in a Hosted Environment
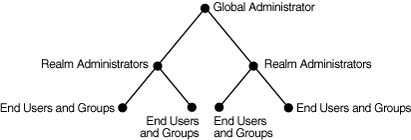
The global administrator, with full privileges for the entire directory, can delegate to realm administrators the privileges to create and manage the realms for hosted companies. These administrators can, in turn, delegate to end users and groups the privileges to change their application passwords, personal data, and preferences. Each type of user can thus be given the appropriate level of privileges.
Oracle Delegated Administration Services uses an Oracle Application Server Containers for J2EE (OC4J) that is enabled for small Java programs, called servlets. Together, the OC4J and the servlets:
Receive requests from clients
Process those requests—by either retrieving or updating data in Oracle Internet Directory—and compile the LDAP result into an HTML page
Send the HTML page back to the client Web browser
Figure 1-2 shows the flow of information between components in a Oracle Delegated Administration Services environment.
Figure 1-2 Flow of Information Between Components in a Oracle Delegated Administration Services Environment
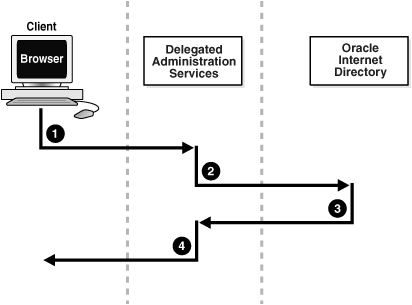
As Figure 1-2 shows:
The user, from a browser and using HTTP, sends to Oracle Delegated Administration Services a request containing a directory query.
Oracle Delegated Administration Services receives the request and launches the appropriate servlet. This servlet interprets the request, and sends it to Oracle Internet Directory by using LDAP.
Oracle Internet Directory sends the LDAP result to the Oracle Delegated Administration Services servlet.
The Oracle Delegated Administration Services servlet compiles the LDAP result into an HTML page, and sends it to the client Web browser.
When a user logs into an Oracle component, that component may need to obtain information from the directory on the end user's behalf—for example, the password verifier. To do this, the component typically logs into the directory as a proxy user, a feature that enables it to switch its identity to that of the end user.
A problem, however, is that the greater the number of components logging into the directory as proxy users, the greater the risk of a malicious user accessing the directory as a proxy user. To prevent this security problem, the Oracle Delegated Administration Services centralizes proxy user access.
In a Oracle Delegated Administration Services environment, each component, instead of logging into the directory as a proxy user, logs into the central Oracle Delegated Administration Services. Oracle Delegated Administration Services then logs into the directory as a proxy user, switches its identity to that of the end user, and performs operations on that user's behalf. Centralizing proxy user directory access in this way replaces the less secure strategy of granting proxy user access to every component accessing the directory.
Figure 1-3 shows the proxy user feature in an Oracle Delegated Administration Services environment. End users or delegated administrators log in to a central Oracle Delegated Administration Services. They do this by using the Oracle Internet Directory Self-Service Console, the consoles of other Oracle components such as OracleAS Portal, or those of third-party applications. The Oracle Delegated Administration Services then logs into Oracle Internet Directory as a proxy user.
This section tells you how to install and configure Oracle Delegated Administration Services. It contains these topics:
Task 2: Verify that Oracle Delegated Administration Services Is Running
Location of Log Files for Components in the Oracle Delegated Administration Services Environment
|
See Also: Appendix B, "Troubleshooting Oracle Delegated Administration Services" for information on how to troubleshoot Oracle Delegated Administration Services |
By default, Oracle Delegated Administration Services is installed as part of Oracle Internet Directory 10g Release 2 (10.1.2). However, during the installation process you can also choose to install Oracle Delegated Administration Services by itself. In this manner, you can install multiple instances of Oracle Delegated Administration Services on separate servers that communicate with a single instance of Oracle Application Server.
|
Note: During installation,Oracle Delegated Administration Services is deployed in the OC4J_SECURITY instance. Because most of the Oracle Delegated Administration Services setup depends on this instance, its important that the name of this instance not be changed. |
|
See Also: Oracle Application Server installation documentation for your operating system |
You can use Oracle Enterprise Manager 10g Application Server Control Console to verify that Oracle Delegated Administration Services is running as follows:
On the main Application Server Control Console page, select the name of the Oracle Application Server instance you want to manage in the Standalone Instances section. The Oracle Application Server home page opens for the selected instance.
Locate OC4J_SECURITY in the System Components table. The Status column will contain one of the following:
An up arrow, which indicates the component is up and running
A down arrow, which indicate the component is down and not running
An icon in the shape of a stopwatch, which indicates that the Application Server Control Console is unable to determine the status of the component
If Oracle Delegated Administration Services is not running, then start it by following the instructions in Starting and Stopping Oracle Delegated Administration Services.
|
See Also: Oracle Internet Directory Administrator's Guide for information on how to work with the Oracle Enterprise Manager 10g Application Server Control Console |
Alternatively, you can verify that Oracle Delegated Administration Services are running using the following command-line procedures:
To do this, use the following command:
ps -ef | grep http
|
See Also: Table 1-1 to find log file locations for components in the Oracle Delegated Administration Services environment |
Use the following command:
ps -ef | grep java
Be sure that the Java process is running. If it is not, then consult the log file.
Using any browser, enter:
http://host_name:port_number/orasso/
where host_name is the name of the computer on which the Oracle HTTP Server is running, and port_number is the corresponding port number. The default port number of the Oracle HTTP Server is 7777. Try to log in by using the Oracle Application Server Single Sign-On login window.
Using any browser, enter:
http://host_name:port_number/oiddas/
where host_name is the name of the computer on which the Oracle HTTP Server is running, and port_number is the corresponding port number. The default port number of the Oracle HTTP Server is 7777. This displays the Oracle Delegated Administration Services home page.
If Oracle Delegated Administration Services is not running, then start it by following the instructions in "Starting and Stopping Oracle Delegated Administration Services".
To do this, follow the instructions in the section "Configuring an Identity Management Realm by Using the Self-Service Console".
To do this, follow the instructions in the section "Configuring User Entries by Using the Self-Service Console".
Table 1-1 tells you where to find the log files for components in the Oracle Delegated Administration Services environment.
Table 1-1 Log Files for Components In Oracle Delegated Administration Services Environment
This section contains these topics:
To start Oracle Delegated Administration Services by using the command line, enter:
$ORACLE_HOME/opmn/bin/opmnctl startproc type=oc4j instancename=OC4J_SECURITY
To stop Oracle Delegated Administration Services by using the command line, enter:
$ORACLE_HOME/opmn/bin/opmnctl stopproc type=oc4j instancename=OC4J_SECURITY
To start, stop, or restart a component from the Oracle Enterprise Manager 10g Application Server Control Console:
On the main Application Server Control Console page, select the name of the Oracle Application Server instance you want to manage in the Standalone Instances section. The Oracle Application Server home page opens for the selected instance.
In the System Components table, select OC4J_SECURITY in the Name column. This OC4J_SECURITY page opens.
In the General section, select the Start, Stop, or Restart button.
|
See Also:
|
You can embed Oracle Delegated Administration Services into both Oracle and third-party self-service applications that use Oracle Internet Directory. For example, if you are building a Web portal, you can add Oracle Delegated Administration Services to enable end users to change application passwords stored in the directory.
Each unit has a corresponding URL stored in the directory. To invoke a Oracle Delegated Administration Services unit, an application queries the directory at runtime for the corresponding URL.
This section contains these topics:
|
See Also: The chapter on the Oracle Delegated Administration Services URL API in Oracle Internet Directory Application Developer's Guide |
Oracle Delegated Administration Services can perform these operations regarding user entries:
Search for a user entry
Create a user entry
Self-edit a password
Select a user entry and edit it
Select a user entry and delete it
Select a user entry and assign a privilege to that user
View profile of the user who is logged in
User list of values (LOV), a popup window that enables you to lookup and select a user
Edit a user by passing the orclguid attribute to the URL. The entry is then displayed without the user needing to perform a search.
Delete a user by passing the orclguid attribute to the URL. The entry is then displayed without the user needing to perform a search.
Assign a privilege to a user by passing the orclguid attribute to the URL. The entry is then displayed without the user needing to perform a search.
Oracle Delegated Administration Services can perform these operations regarding group entries:
Search for a group entry
Create a group entry
Select a group entry and edit it
Select a group entry and delete it
Select a group entry and assign a privilege to that group
Group list of values (LOV), a popup window that enables you to lookup and select a group
Edit a group by passing the orclguid attribute to the URL. The entry is then displayed without the user needing to perform a search.
Delete a group by passing the orclguid attribute to the URL. The entry is then displayed without the user needing to perform a search.
Assign a privilege to a group by passing the orclguid attribute to the URL. The entry is then displayed without the user needing to perform a search.
You can use Oracle Enterprise Manager 10g Application Server Control Console to configure Oracle Delegated Administration Services in the Oracle Identity Management Oracle home. When you do this, Enterprise Manager:
Sets up the URL for Oracle Delegated Administration Services
Configures the appropriate privileges
Deploys Oracle Delegated Administration Services in an OC4J_SECURITY instance
|
Note: Before configuring Oracle Delegated Administration Services, ensure that Oracle Application Server Single Sign-On is configured. Configuring Oracle Application Server Single Sign-On also configures mod_osso, which is required by Oracle Delegated Administration Services. mod_osso is an Oracle HTTP Server module that communicates with the OracleAS Single Sign-On server. |
To configure Oracle Delegated Administration Services by using Oracle Enterprise Manager 10g Application Server Control Console:
On the main Application Server Control Console page, select the name of the Oracle Application Server instance you want to manage in the Standalone Instances section. The Oracle Application Server home page opens for the selected instance.
Select the Configure Components button, located just above the System Components table. The Select Component page appears.
|
Note: The Configure Component button is available only if you have installed but not configured any Oracle Application Server components. |
Select Oracle Delegated Administration Services, then choose Continue. The Login page appears.
Enter the user name and password of the directory super user. The default user name is cn=orcladmin.
Choose Finish to complete the configuration.
Start Oracle Delegated Administration Services as follows:
In the System Components table, select OC4J_SECURITY in the Name column. The OC4J_SECURITY page opens.
In the General section, select the Start button.
Oracle Delegated Administration Services is configured automatically as part of the default Identity Management and Metadata Repository installation in which Oracle Internet Directory, Oracle Delegated Administration Services, and OracleAS Single Sign-On are selected. In some situations, you may need to configure it on a computer other than that on which the infrastructure is configured. You can do this in one of two ways: either by performing a standalone Oracle Delegated Administration Services installation using the Oracle Installer, or manually.
This section contains these topics:
Performing a Standalone Oracle Delegated Administration Services Installation
Manually Deploying Oracle Delegated Administration Services in a New Oracle Home
To perform a standalone Oracle Delegated Administration Services installation, when prompted by the Oracle Installer, select the Identity Management installation type. On the Configuration Options screen, select Delegated Administration Service.
|
Note: If you configure Oracle Application Server Single Sign-On and Oracle Delegated Administration Services in separate installations against the same Oracle Internet Directory, then be sure to configure OracleAS Single Sign-On first. This is because Oracle Delegated Administration Services depends onmod_osso, which is not set up during installation unless the Oracle Internet Directory it points to already has OracleAS Single Sign-On configured.
|
|
See Also: Oracle Application Server 10g Installation Guide for further instructions |
To manually deploy Oracle Delegated Administration Services in a separate Oracle home, follow these steps:
Verify that the computer has at least a core installation that points to an existing Oracle Internet Directory and Oracle Application Server Single Sign-On.
Navigate to the ORACLE_HOME/dcm/bin directory.
Create a new component by using the following command:
dcmctl createcomponent -verbose -debug -ct oc4j -co OC4J_SECURITY
Start the component by using the following command:
dcmctl start -verbose -debug -co OC4J_SECURITY
Deploy the oiddas.ear file by using the following command:
dcmctl deployApplication -debug -verbose -a oiddas -f
ORACLE_HOME/ldap/das/oiddas.ear -co OC4J_SECURITY
Perform the following steps to add the LD_LIBRARY_PATH and DISPLAY environment variables to the opmn.xml file:
Navigate to the ORACLE_HOME/opmn/conf directory and open opmn.xml in a text editor.
Add the following lines in the OC4J_SECURITY section of opmn.xml:
For a UNIX environment:
<environment>
<prop name="LD_LIBRARY_PATH" value="%ORACLE_HOME%/lib"/>
</environment>
For a Windows environment:
<environment>
<prop name="PATH" value="%ORACLE_HOME%/bin"/>
</environment>
Note the placement of the section <environment> in the following example.
<oc4j maxRetry="3" instanceName="OC4J_DAS" gid="OC4J_SECURITY" numProcs="1"> <config-file path="/home/ias902/j2ee/OC4J_ DAS/config/server.xml"/> <oc4j-option value="-properties"/> <port ajp="3001-3100" jms="3201-3300" rmi="3101-3200"/> <environment> <prop name="LD_LIBRARY_PATH" value="/home/ias902/lib"/> </environment> </oc4j>
Navigate to the ORACLE_HOME/dcm/bin directory.
Save the changes to the repository by using the following command:
dcmctl updateconfig -verbose -debug -ct opmn
Restart OPMN by using the following command:
dcmctl restart -verbose -ct opmn
Stop and start the OC4J_SECURITY instance by using the following commands:
dcmctl stop -verbose -debug -ct oc4j -co OC4J_SECURITY
dcmctl start -verbose -debug -ct oc4j -co OC4J_SECURITY
Set the necessary permissions for Oracle Delegated Administration Services. Modify the group by using either Oracle Directory Manager or the command-line tool. Add the DN of the new Oracle Application Server instance where Oracle Delegated Administration Services is currently being deployed as the uniquemember.
DN of the group to be modified: cn=Associated Mid-tiers,orclApplicationCommonName=DASApp,cn=DAS,cn=Products,cn=OracleContext
The DN on the Oracle Application Server instance is:
orclApplicationCommonName=name of Oracle Application Server instance,cn=IAS Instances, cn=IAS, cn=Products, cn=OracleContext
where name of Oracle Application Server instance is obtained from $ORACLE_HOME/config/ias.properties.
When configuring Oracle Delegated Administration Services in an environment where Oracle Application Server Single Sign-On is to be configured on separate middle tier nodes, follow the instructions in Chapter 8, "Advanced Configurations" in the Oracle Application Server Single Sign-On Administrator's Guide.
Because Oracle Delegated Administration Services is a stateful application, if you deploy multiple instances of Oracle Delegated Administration Services behind a load balancer, then the load balancer must be configured to support session binding in order to maintain a consistent user experience. Session binding refers to a user session being bound to an origin server in order to maintain state for a specified period of time. In other words, you should configure the load balancer so it routes all requests for each user to the same Oracle Delegated Administration Services middle tier.
To configure Oracle Delegated Administration Services and Oracle Application Server Single Sign-On for a replication environment, follow these steps:
Navigate to the $ORACLE_HOME/config folder and open the ias.properties file in a text editor.
Change the value assigned to the DAS.LaunchSuccess parameter from true to false.
Restart Oracle Delegated Administration Services by following the procedures described in Starting and Stopping Oracle Delegated Administration Services.