By Jack M. Germain
Oct 10, 2018 5:00 AM PT


Manjaro Linux offers the best of two worlds. It puts a user-friendly face on an Arch-based distro, and it gives you a choice of sensible and productive desktop interfaces.
The Manjaro Linux team released its latest updates running the KDE, Xfce and GNOME desktops, Manjaro Linux 18.0 Beta 7, late last month. All three are solid performers and seem to be ready for final release. A key benefit of Manjaro Linux is the rolling release method to push new versions to users without requiring full reinstallation, as is the case with most other Linux distributions.
Manjaro Linux is a fast, traditional desktop-oriented operating system based on Arch Linux. Arch itself is renowned for being an exceptionally fast, powerful and lightweight distribution that provides access to the very latest cutting-edge — and bleeding-edge — software. Manjaro exceeds that reputation and delivers more benefits.
Using an Arch-based distro such as Manjaro is not the same thing as using a pure Arch Linux descendant, however. Arch is geared toward more experienced or technically minded users.
Arch-based distros generally are beyond the reach of those who lack the technical expertise (or persistence) required to use it. If for no other reason, Arch Linux derivatives are monsters to install and configure. Those processes require more than a passing knowledge with the command line interface. Manjaro Linux is different.
Developed in Austria, France and Germany, Manjaro provides all the benefits of the Arch operating system with a focus on user-friendliness and accessibility. The prime directive for all things Arch is simplicity, modernity and pragmatism.
Manjaro Linux’s in-house system tools, easy installation application and better range of software packages make it a better Arch-based distro than Arch Linux itself. Manjaro offers much more.
Arch-Based or Real Arch?
Manjaro Linux is not Arch Linux — but yes, it is based on Arch underpinnings and Arch principles. That is a good thing.
Nor is using Manjaro Linux the same as using pure Arch or more direct derivatives, such as Antergos Linux, which I recently
reviewed. Even if Arch is outside your comfort zone, though, you will be rewarded with a satisfying computing experience with Manjaro Linux.
I have not seriously looked at Manjaro Linux in several years. I had a take-it-or-leave-it reaction to the much earlier version I checked out back then. However, Manjaro has come a long way. The developers’ goal to be an independent Arch branch is the key to the distro’s success.
Manjaro is independent of Arch and has its own development team. Manjaro’s user base targets newcomers, not the more technically inclined, experienced Linux user.
Manjaro breaks away from the pure Arch mold to make a better Arch-based platform. It is easier to use. A few more distinct differences separate Manjaro and Arch.
A Better Way
Manjaro’s independence is one of its key distinguishing traits. That is clearly evident in its software packages. Manjaro has its own repositories that are not affiliated with Arch Linux. The benefit is that fewer things break, because the Manjaro team takes more time to make sure its software packages are compatible. In addition, the repositories contain software packages the Arch community does not provide.
Manjaro also includes its own distribution-specific tools, such as the Manjaro Hardware Detection utility and the Manjaro Settings Manager. Also, Manjaro has its own way of doing system functions, compared to Arch.
Manjaro’s developers built this Arch Linux derivative around a series of system apps that make using it much easier. For example, Arch distros usually require familiarity with terminal windows to carry out package installations and removals. Manjaro’s front-end assistance and improved system tools give less-experienced users considerable handholding.
One software feature Manjaro closely shares with Arch Linux is compatibility with the AUR, or Arch Users Repository. This added access expands your free software stores within the Arch community. It has more of the latest software additions that are not yet vetted for the official Arch repository. This is a community-driven repository for Arch Linux users.
An added benefit of using the AUR is a simplified package installation process in Manjaro. Community members port applications to the AUR and provide scripts to install applications not packaged for Arch or Manjaro.
Another invaluable tool is the console-based net-installer Manjaro-Architect. You can install any of Manjaro’s official or community-maintained editions, or you can configure your own custom-built Manjaro system.
If you have several desktop or laptop computers and want to create identical systems, this is the way to get that job done efficiently and painlessly. Manjaro-Architect downloads all packages in their latest versions during installation. Manjaro-Architect supports systemd, disk encryption, and a variety of file systems, including LVM and btrfs. You can view a tutorial for using the architect tool on the Manjaro forum.
Manjaro Kudos
I was particularly impressed with Manjaro’s hardware support, especially for Broadcom wireless cards. Several of my laptops are plagued with problems related to these quirky wireless devices. More times than not, they fail to be detected when I test a Linux distro. Manjaro eliminates that issue.
I like not having to configure PPAs (Personal Package Archives) in a package manager when I install less standard software packages in other distros. The large software repository Manjaro provides plus the Arch User Repository make PPAs unnecessary.
This year I’ve noticed increasing delays with other Linux distros in booting into the desktop screen. Some of these delays are caused by patches needed to work around vulnerability issues with Intel and AMD processor chips. That is less of a problem with Manjaro Linux. It has a fast bootup sequence.
Extra Editions
I downloaded the latest official Manjaro ISOs for the KDE, Xfce and GNOME desktop editions for testing. I was pleased to see that the only real difference among them was the look and feel of the desktop environments. The specialized in-house system apps and Manjaro-specific software provided a unified computing platform across all three desktop editions.
Numerous community-maintained editions provide some newer and experimental alternative desktop editions. These community releases still carry the release label of 17.1.12, indicating last year’s base releases. According to a note on the website, these community desktop alternatives are updated with the latest software, however.
The Manjaro-GNOME desktop includes the latest refinements that make GNOME easy to use.
These alternative desktop environments range from a few better-known choices to a couple of very obscure desktop projects: Awesome, Bspwm, Budgie, Cinnamon, Deepin, i3, LXDE/LXQT, Mate and Openbox.
The community editions might be more suitable for less-experienced Linux users. The only drawback is a delay in updating the current versions.
Tough Choices
Picking a preferred desktop from the three primary candidates — KDE, Xfce and GNOME — is largely a matter of personal choice. All three desktop environments worked as expected.
Some Linux distros use in-house modifications to the desktop to tweak performance or better align the desktop environment with the distro’s philosophy and design styles. All three releases appeared to be fairly standard versions.
The Xfce desktop is a lightweight environment that is fast and uses fewer system resources. It is visually appealing with little to no eye candy or animations. Despite its so-called lightweight structure, Xfce is a fully functional desktop with modern features and a fair amount of configurability.
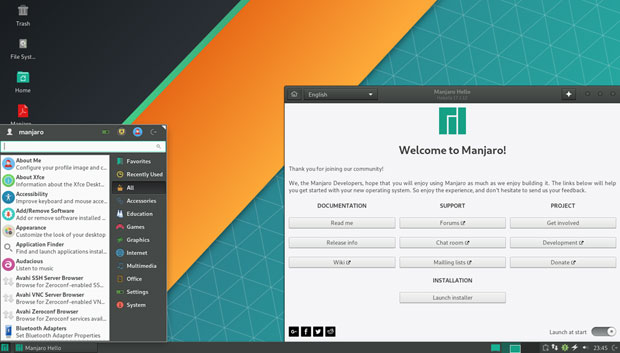
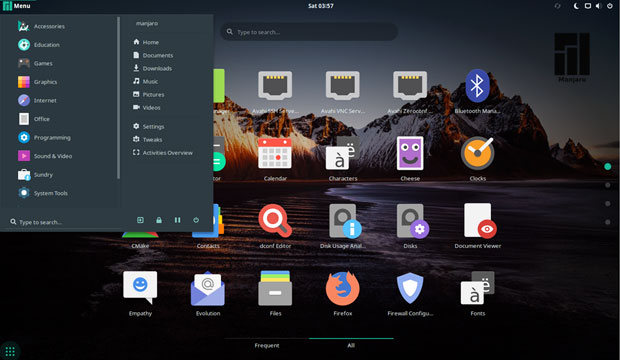
The Manjaro-Xfce edition sports the welcome screen common to all Manjaro editions. The standard Xfce user interface offers a modern integration of classic Linux bottom panel and simplified main menu.
The GNOME Desktop Environment uses the Wayland display server by default. It has a simplified appearance with a less impressive feature set. Most of its customization potential is done via extensions.
The KDE desktop is the most feature-rich and versatile desktop environment of the three. It provides several different menu styles to access applications. Its built-in interface provides easy access for installing new themes.
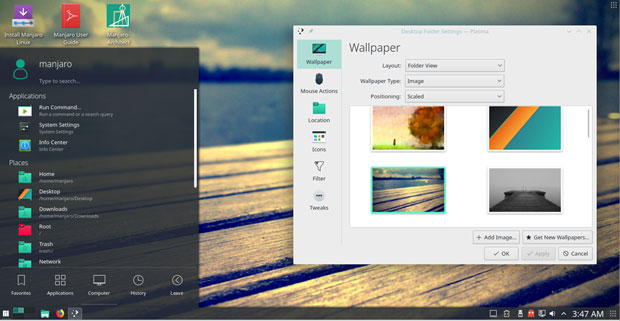
The Manjaro-KDE edition has an attractive collection of background images, along with a multipurpose main menu panel, plus lots of eye candy displays that make the user interface fun and productive.
One of the pluses in running the KDE edition is the desktop customization. You have access to a collection of snappy widgets you can add to your desktop. The result is a much more configurable resource-heavy desktop.
Bottom Line
Regardless of which desktop you select, the welcome screen introduces Manjaro tools and get-acquainted details such as documentation, support tips, and links to the project site.
You can get a full experience in using the live session ISOs without making any changes to the computer’s hard drive. That is another advantage to running Manjaro Linux over a true Arch distro. Arch distros usually do not provide live session environments. Most that do lack any automatic installation launcher from within the live session.
Caution: When you attempt to run the boot menu from the Manjaro DVD, pay attention to the startup menu. It is a bit confusing. To start the live session, go halfway down the list of loading choices to select the Boot Manjaro option. The other menu options let you configure non-default choices for keyboard, language, etc.
After the live medium loads the Manjaro live session, browse the categories in the welcome window. You can click the Launch Installer button in the welcome window or launch it after experiencing the live session by clicking on the desktop install icon or running the installation program from the main menu.
Installation is a simple and straightforward process. The Calamares installer allows newcomers to easily set up the distro. It gives advanced users lots of customization options.
Want to Suggest a Review?
Is there a Linux software application or distro you’d like to suggest for review? Something you love or would like to get to know?
Please
email your ideas to me, and I’ll consider them for a future Linux Picks and Pans column.
And use the Reader Comments feature below to provide your input!

 Jack M. Germain has been an ECT News Network reporter since 2003. His main areas of focus are enterprise IT, Linux and open source technologies. He has written numerous reviews of Linux distros and other open source software.
Jack M. Germain has been an ECT News Network reporter since 2003. His main areas of focus are enterprise IT, Linux and open source technologies. He has written numerous reviews of Linux distros and other open source software.
Email Jack.
Source


 The Automotive Grade Linux project has released Unified Code Base 6.0 in-vehicle infotainment stack with new software profiles for telematics and instrument cluster.
The Automotive Grade Linux project has released Unified Code Base 6.0 in-vehicle infotainment stack with new software profiles for telematics and instrument cluster.



 Jack M. Germain has been an ECT News Network reporter since 2003. His main areas of focus are enterprise IT, Linux and open source technologies. He has written numerous reviews of Linux distros and other open source software.
Jack M. Germain has been an ECT News Network reporter since 2003. His main areas of focus are enterprise IT, Linux and open source technologies. He has written numerous reviews of Linux distros and other open source software.


 Konqi from the early days who replaced Kandalf (right)
Konqi from the early days who replaced Kandalf (right)