This article shows some examples of using the dir command to list the contents of a directory. The dircommand is not a commonly used command in Linux. Though it works more less like the ls command which most Linux users prefer to use. We’ll be discussing the dir command where we shall look at how to use different options and arguments.
The general syntax of the dir command is as follows.
# dir [OPTION] [FILE]
dir Command Usage with Examples
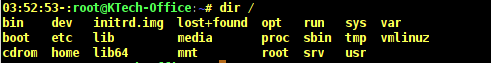
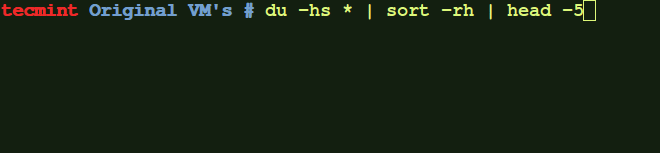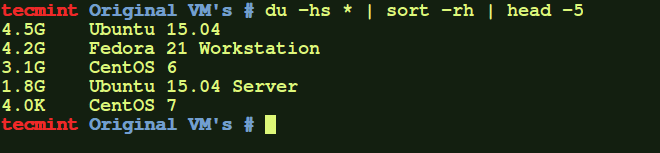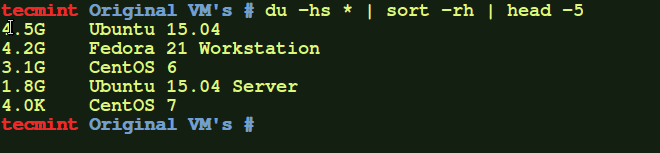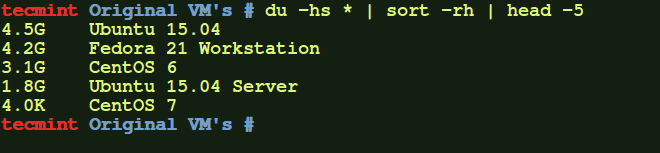
Simple output of the dir command
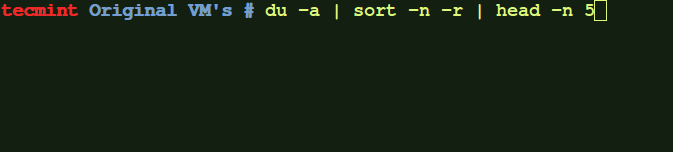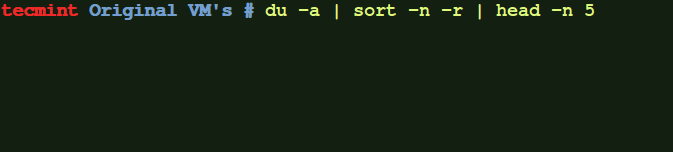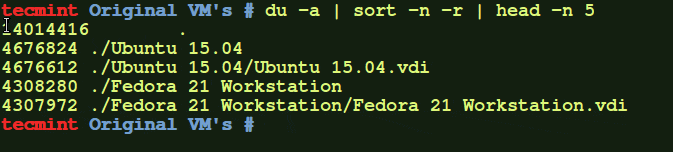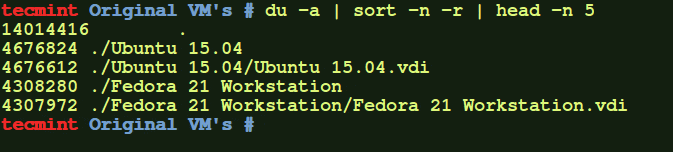
# dir /
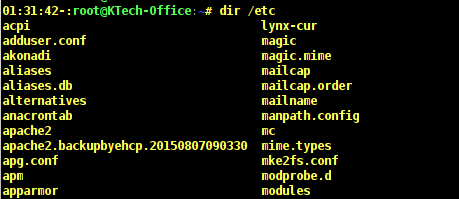
Output of the dir command with the /etc directory file is as follows. As you can see from the output not all files in the /etc directory are listed.
# dir /etc
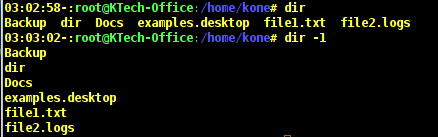
To list one file per line use -1 option as follows.
# dir # dir -1
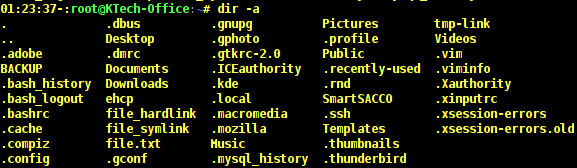
View all files in a directory including hidden files
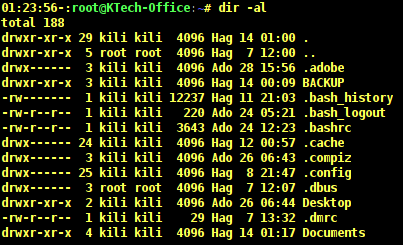
To list all files in a directory including . (hidden) files, use the -a option. You can include the -l option to format output as a list.
# dir -a # dir -al
View directory entries instead of content
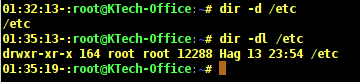
When you need to list only directory entries instead of directory content, you can use the -d option. In the output below, the option -d lists entries for the /etc directory.
When you use -dl, it shows a long listing of the directory including owner, group owner, permissions.
# dir -d /etc # dir -dl /etc
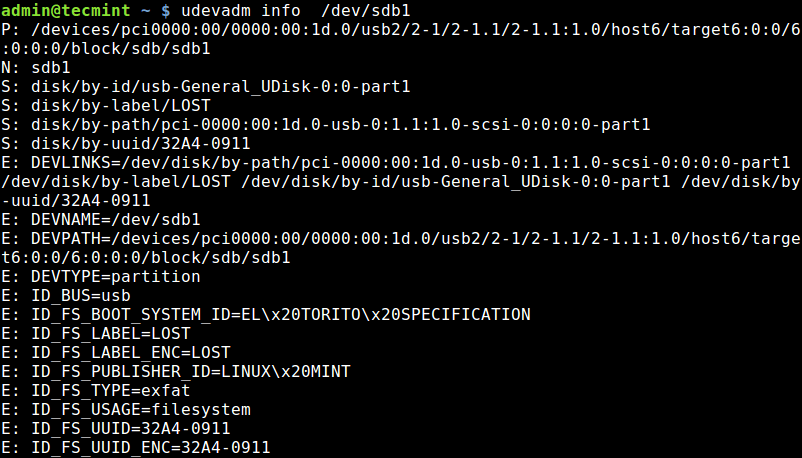
View index number of files
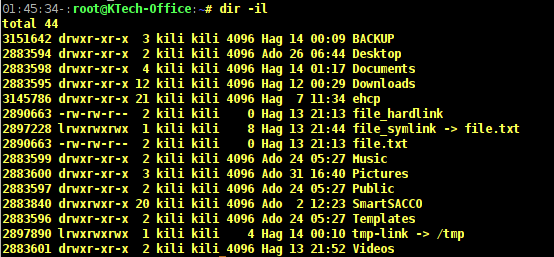
In case you want to view the index number of each file, use the option -i. From the output below, you can see that first column shows numbers. These numbers are called inodes which are sometimes referred to as index nodes or index numbers.
An inode in Linux systems is a data storage on a filesystem that stores information about a file except the filename and its actual data.
# dir -il
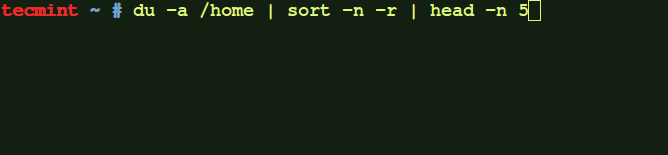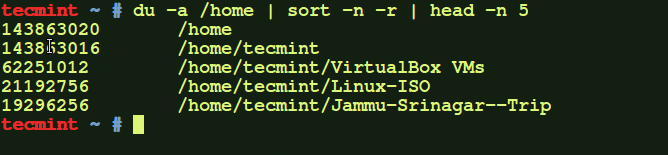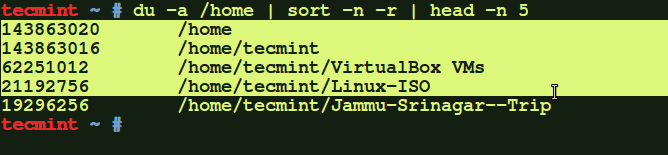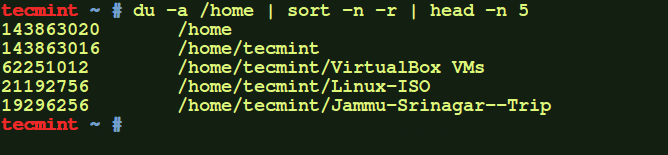
List files and their allocated sizes in blocks
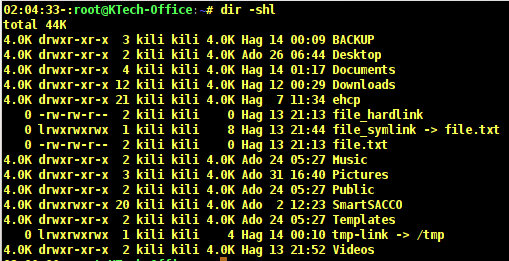
You can view files sizes using the -s option. If you need to sort the files according to size, then use the -S option.
In this case you need to also use the -h option to view the files sizes in a human-readable format.
# dir -shl
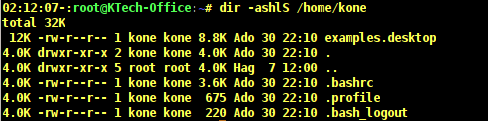
In the output above, the first column shows the size of files in Kilobytes. The output below shows a sorted list of files according to their sizes by using the -S option.
# dir -ashlS /home/kone
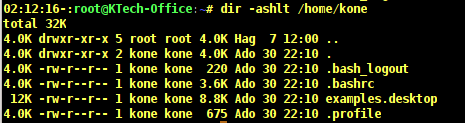
You can also sort by modification time, with the file that has recently been modified appearing first on the list. This can be done using the -t option.
# dir -ashlt /home/kone
List files without owner or group owner
To list files without their owners, you have to use -g option which works like the -l option only that it does not print out the file owner. And to list files without group owner use the -G option as follows.
# dir -ahgG /home/kone
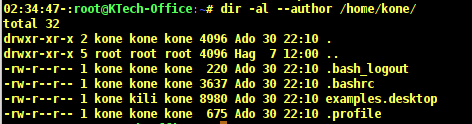
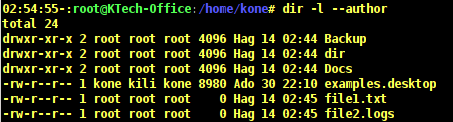
As you can notice from the output above that the name of the file owner and the group owner are not printed. You can as well view the author of a file by using the –author flag as follows.
# dir -al --author /home/kone
In the output above, the fifth column shows the name of the author of a file. The examples.desktop files is owned by user kone, belongs to group kili and it was authored by user kone.
List directories before other files
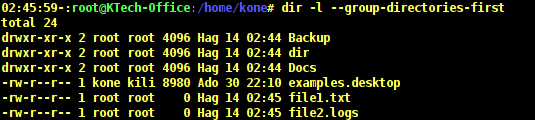
You may wish to view directories before all other files and this can be done by using the –group-directories-firstflag as follows.
# dir -l --group-directories-first
When you observe the output above, you can see that all the directories are listed before the regular files. The letter d before the permissions indicates a directory and a indicates a regular file.
You can also view subdirectories recursively, meaning that you can list all other subdirectories in a directory using the -R option as follows.
# dir -R
In the above output, the (.) sign means the current directory and home directory of user Kone has three subdirectories that is Backup, dir and Docs.
The Backup subdirectory has two other subdirectories that is mariadb and mysql which have no subdirectories.
The dir subdirectory does not have any subdirectory. And the Docs subdirectory has two subdirectories namely Books and Tuts which do not have subdirectories.
View user and group IDs instead of names
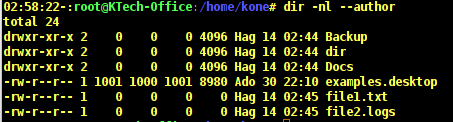
To view user and group IDs, you need to use -n option. Let us observe the difference between the next two outputs.
Output without -n option.
# dir -l --author
Output with -n option.
# dir -nl --author
View entries separated by commas
This can be archived by using -m option.
# dir -am
To find help in using the dir command use –help flag and to view version details of dir use –version.
Conclusion
These are just examples of basic usage of the dir command, to use many other options see the manual entry for dir command on your system.