| Oracle® Fusion Middleware Setup Guide for Universal Records Management 11g Release 1 (11.1.1) Part Number E10640-02 |
|
|
View PDF |
| Oracle® Fusion Middleware Setup Guide for Universal Records Management 11g Release 1 (11.1.1) Part Number E10640-02 |
|
|
View PDF |
This section describes how to use the classification, classification guides, and supplemental marking functions to provide additional security. It covers the following topics:
Concepts
Tasks
Examples
Supplemental markings can be assigned to content and record folders to clarify document handling in addition to standard document classification. For example, you can add supplemental markings such as "Restricted Data" or "Originator Controlled." Or you can use supplemental markings in collaboration projects. Only people with specific markings will be able to access a group of content. Supplemental markings can be set at both the record folder and the content level.
This section covers the following topics:
In addition to using supplemental markings as a means of clarifying document handling, supplemental markings can be used as a security feature to further restrict users from accessing record folders and content.
To disable the use of supplemental markings as a security feature, clear the Supplemental Markings box on the Configure Retention Settings Page and do not assign the markings to users.
When supplemental markings are assigned to users, even if a user has access to a specific record folder, the supplemental marking further restricts access to folders and content. In circumstances where a folder or content has multiple supplemental markings, it can be required that a user match all assigned supplemental markings to access an item or record folder. When 'match all' is disabled, if a user matches just one of the multiple supplemental markings, the user can access the content or record folder object.
Figure 6-1 User Must Match All Supplemental Markings
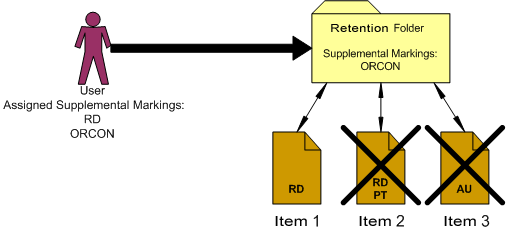
For example, in the diagram above, the user is assigned the supplemental markings "RD" and "ORCON." The folder is marked with "ORCON," therefore the user can access the folder. The content within the folders are assigned one or more of the markings, "RD," "PT," and "AU." If the security configuration for supplemental markings is set to force the user to match all supplemental markings, then the user can access the folder marked "ORCON" and its child "Item 1" marked with the supplemental marking "RD." Because the user has not been assigned the supplemental marking "PT" or "AU", the user cannot access "Item 2," which has the multiple markings "RD" and "PT," nor can the user access "Item 3" with the marking "AU."
Figure 6-2 User Must Match at Least One Supplemental Marking
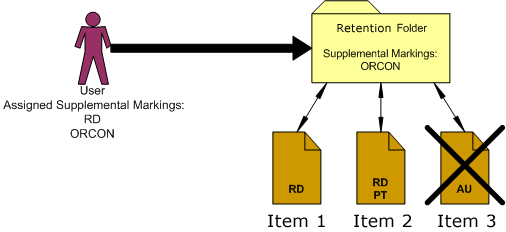
If the supplemental marking security configuration is not forcing a user to match all markings, then the user can now access Item 2, because the user matches at least one marking "RD" on the Item 2. Because the user has not been assigned the supplemental marking "AU," the user still cannot access Item 3, which has the supplemental marking "AU." The user would have to be assigned the supplemental marking "AU" in the User Admin application to access the item.
Supplemental markings are not inherited by record folders or content. Markings are checked at every folder and item level. Supplemental markings do not have any permissions hierarchy. All markings have equal permissions: access granted or access denied to users. In contrast, the classified security does have a hierarchy to its classification levels. For further information, see "Classified Records Security Hierarchy".
Two special supplemental markings, Restricted and Formerly Restricted, can be used to disable the following classification-related metadata fields on the content check-in and metadata update pages:
Declassify on event
Declassify on date
Downgrade instructions
Downgrade on event
Downgrade on date
To work with supplemental markings, you must have one of the following rights:
Admin.Triggers: This right enables you to view information about supplemental markings.
Admin.RecordManager: In addition to viewing information about supplemental markings, this right also enables you to create (add), edit, and delete supplemental markings.
Optionally, the following right may be useful for working with supplemental markings:
Record.Edit: This right is required to use metadata disabling based on supplemental markings.
Permissions:
Oracle UCM administrative permissions are required to perform this action.The following procedures are followed when managing supplemental markings:
You can enable and disable supplemental markings at any time. Enabling supplemental markings enforces the markings assigned to any users attempting to access marked items and record folders.
Disabling supplemental markings means the security provided by the markings is not in force; however, the supplemental markings can still be used generically as document handling instructions.
Permissions:
The Admin.RecordManager right is required to perform these actions. This right is assigned by default to the Records Administrator role.Click Records then Configure then Settings from the Top menu.
The Configure Retention Settings Page is displayed. Expand the Security section if needed.
Enable the Supplemental Markings box.
(Optional) To force a user to match all supplemental markings assigned to an item or record folder before granting access, click the User must match all Supplemental Markings box. To allow access if the user has at least one of the markings, leave the box unchecked.
Click Submit. The 'successful configuration' message is displayed.
To disable supplemental markings, clear the Supplemental Markings box and the User must match all supplemental markings box. Click Submit. A configuration successful message is displayed. Supplemental markings are now disabled and the Supplemental Marking selection field is hidden from view.
You can create supplemental markings only if they are enabled. See "Enabling or Disabling Supplemental Markings" for details.
After creating a supplemental marking, it is available for applying to content, record folders, and users.
When editing an existing supplemental marking, its description can be modified but not its name.
Permissions:
The Admin.RecordManager right is required to perform these actions. This right is assigned by default to the Records Administrator role.Click Records then Configure from the Top menu. Click Security then Supplemental Markings.
The Configure Supplemental Markings Page is displayed.
Click Add.
The Create or Edit Supplemental Marking Page is displayed.
Enter a unique supplemental marking with a maximum of 30 characters in the Supplemental Marking text box.
Enter a description of the marking with a maximum of 30 characters in the Brief Description text box.
Click Create.
The Supplemental Marking Information Page is displayed with a message indicating the creation was successful. Use that page to edit or delete the marking, or view references to the marking.
Click OK when done.
To edit an existing supplemental marking, complete the following steps:
Click Records then Configure from the Top menu. Click Security then Supplemental Markings.
The Configure Supplemental Markings Page is displayed.
You can edit the marking in one of two ways:
Click Edit Marking from the item's Action menu. The Create or Edit Supplemental Marking Page is displayed.
Click the name of the marking to edit. The Supplemental Marking Information Page is displayed. Click Edit on this page. The Create or Edit Supplemental Marking Page is displayed.
Make the changes and click Submit Update. The Supplemental Marking Information Page is displayed with a message indicating the creation was successful. Use this page to edit or delete the marking, or view references to the marking.
Click OK when done.
Permissions:
Either the Admin.Triggers or Admin.RecordManager right is required to perform these actions. The Admin.Triggers right is assigned by default to the Records Officer and Records Administrator roles, and the Admin.RecordManager right to the Records Administrator role.Click Records then Configure from the Top menu. Click Security then Supplemental Markings.
The Configure Supplemental Markings Page is displayed.
Click the name of the marking with information to view.
The Supplemental Marking Information Page is displayed. Use the page to edit or delete the marking, or view references to the marking.
Click OK when done.
You can delete supplemental markings regardless of whether markings are enabled. A supplemental marking cannot be deleted until any references to the marking in content or record folders is removed. The marking must also be manually removed from any assignments to users.
If a user attempts to delete a supplemental marking currently in use, a message is displayed stating the marking is in use by users (the marking is assigned to users and must be removed), by record folders, or by a content item. The marking must then be removed from the user, folder, or item before proceeding.
To remove the marking from any option lists, the schema must be republished after deleting the marking. See the Oracle Fusion Middleware Administrator's Guide for Universal Records Management for details about publishing schema.
Permissions:
The Admin.RecordManager right is required to perform this action. This right is assigned by default to the Records Administrator role.Click Records then Configure from the Top menu. Click Security then Supplemental Markings.
The Configure Supplemental Markings Page is displayed.
Click Delete from the item's Action menu. To delete multiple markings, click the checkbox next to the marking name and click Delete in the Table menu. A marking can also be deleted when viewing the marking's Supplemental Marking Information Page.
A message indicates the deletion was successful.
Click OK.
Tip:
You can search for supplemental markings from the Search page. Select the marking to search for from the Supplemental Markings list on the Search page. Use the search results to see which objects have the marking in use. You can also use screening folders to quickly isolate and sort objects by supplemental markings. For further information, see the Oracle Fusion Middleware Administrator's Guide for Universal Records Management.Permissions:
Administrator privileges in Oracle UCM are required to perform this action.Before assigning markings to users, make sure you have enabled supplemental markings, created the markings, assigned supplemental markings to record folders and retained content, and assigned roles to the users. For the most strict supplemental marking security, you can also force a user to pass all supplemental markings to access an item or record folder.
You may want to remove access from a user who is no longer authorized for a supplemental marking, or to delete a supplemental marking no longer in use. You must remove any references to a supplemental marking before you can delete it.
To disable use of supplemental markings as a security feature, do not assign the markings to users.
Click Admin Applets from the Administration menu.
Click the User Admin icon.
The User Admin utility starts.
On the Users tab, select the user in the Users list, and click Edit. The Info tab on the Edit User page is displayed.
In the Supplemental Markings field, select the markings to which the user should have access. Click the options list arrow, and highlight the marking. Multple markings can be assigned to a user.
Click OK. Repeat the process for each user who needs markings.
Restart the Content Server.
To remove a supplemental marking from a user, complete the following steps:
Click Admin Applets from the Administration menu.
The Administration Applets for the server are displayed.
Click the User Admin icon.
The User Admin utility starts.
On the Users tab, select the user in the Users list, and click Edit. The Info tab on the Edit User page is displayed.
In the Supplemental Markings field, delete a marking by editing the text in the Supplemental Markings text box. Use the delete or backspace key to remove the marking.
Caution:
Be careful when editing text in this field. Each supplemental marking must have a comma and a space between markings, or an "access denied" error occurs when trying to access content with multiple markings and 'match all markings' is enabled.Click OK. Repeat for each user who has a marking to be removed.
Restart the Content Server. For more information about restarting, see the Oracle Fusion Middleware System Administrator's Guide for Content Server.
Restricted Data and Formerly Restricted Data are supplemental markings shipped with the product. Those markings can be used alone or in combination with other markings to disable classified metadata fields on the content check-in and metadata update forms:
Enable supplemental markings (see "Enabling or Disabling Supplemental Markings").
Click Restricted Data or Formerly Restricted Data as the supplemental marking.
Restart the Content Server.
The classification of content is the process of identifying and safeguarding content requiring protection against unauthorized disclosure, for example, because it contains information sensitive to the national security of the United States or sensitive to the stability of a company.
Classification can be an additional way to restrict access when used with supplemental markings and custom security fields. Classification markings are at the content level only, unlike supplemental markings, which are at the content or record folder level.
This section discusses the following topics:
Oracle URM offers several features specifically geared to handling and processing classified content in accordance with the Chapter 4 requirements of the DoD 5015.2 specification. This functionality must be enabled for use (see "Enabling or Disabling Classified Security").
A content item is marked as a classified using a classification specifying the security level of the item. Several built-in classifications ("Top Secret," "Secret," and "Confidential") are available, but custom classifications can be created (see "Creating or Editing a Custom Security Classification").
Content is either classified, unclassified, or declassified:
Classified content has an initial classification and a current classification. The initial classification is specified when the item is first filed. All changes to classification are tracked in the audit logs in the Record History reports.
Unclassified content is not and has never been classified.
Declassified content was formerly classified. When an item is filed and classified, it typically must be declassified within a ten year period. Any exceptions to this must be given an exemption category. When a declassify date exceeds the ten year period after the publication (filing) date, an alert reminds the user to enter an exemption category for the item.
The standard security categories (classification scheme), from highest to lowest, are as follows:
Top Secret
Secret
Confidential
No markings (unclassified)
When using security classification for corporate use only (that is, if you are not concerned with DoD compliance), these terms can be defined as necessary for the organization's infrastructure. For example, "Top Secret" may apply to that content which is critical to the operation of your company and should never be deleted, while "Confidential" may apply to content which must be kept limited to a specific group of individuals, such as Human Resource representatives or members of your accounting team.
Custom classifications can also be defined. See "Creating or Editing a Custom Security Classification".
The following descriptions are applicable for those companies which are using the Oracle URM product for DoD compliance.
If complying with DoD Section 1508, the Top Secret classification (according to Executive Order 12958) is "applied to information, the unauthorized disclosure of which could be expected to cause exceptionally grave damage to the national security that the original classification authority is able to identify or describe."
If complying with DoD Section 1508, only the President of the United States has the authority to classify content as Top Secret, pursuant to the Executive Order 12958. For further details, access the following link:
According to EO 12958, the Secret classification level is "applied to information, the unauthorized disclosure of which could be expected to cause serious damage to the national security that the original classification authority is able to identify or describe."
Every retention user has access to unclassified content, provided all other security criteria are met (such as supplemental markings, right, roles, and so on).
A user who has access to Top Secret classification has access to all lower classifications as well, as shown for User A in the figure below. User B has access to Confidential content and unclassified content.
The following tasks are included in managing classifications:
You can enable and disable classified security at any time. Enabling classified security enforces the security classifications assigned to users who attempt to access classified data.
After enabling classified security, create any custom security classifications required by the organization. If additional security classifications are created, make sure to indicate the classification's place within the marking hierarchy. For further information, see "Setting the Order of Security Classifications".
Permissions:
The Admin.RecordManager right is required to perform this action. This right is assigned by default to the Records Administrator role.Click Records then Configure then Settings from the Top menu.
The Configure Retention Settings Page is displayed. If necessary, expand the Security section.
Enable the Classified Security box.
Click Submit. A message is displayed stating the configuration was updated successfully.
Caution:
Disabling classified security puts sensitive classified items at risk of being accessed by unauthorized people. After your classified security is in force, it is recommended that you do not disable it.To disable classified security, complete the following steps:
Click Records then Configure then Settings from the Top menu.
The Configure Retention Settings Page is displayed.
Clear the Classified Security box.
Click Submit. A message is displayed stating the configuration was updated successfully. Classified security is now disabled and the security classification selection field is hidden from view on the content check-in form.
Use this procedure to create a new security classification. After creating a custom classification, indicate its order in the hierarchy. If not done, the security classification is ignored. For further information, see "Setting the Order of Security Classifications".
Security classifications can be created only if the classified security feature has been enabled (see "Enabling or Disabling Classified Security").
When editing an existing security classification, the description can be modified but not its name.
Permissions:
The Admin.RecordManager and Admin.SecurityClassifications rights are required to perform these actions. These rights are assigned by default to the Records Administrator role.Click Records then Configure from the Top menu. Click Security then Security Classification.
The Configure Security Classification Page is displayed.
Click Add.
The Create or Edit Security Classification Page is displayed.
Enter a unique classification up to 30 characters in the Security Classification text box.
Enter a description up to a maximum of 30 characters in the Brief Description text box.
Click Create. A message indicates creating the classification was successful.
Click OK. The Configure Security Classification Page is displayed with the new classification in the list. A user must be assigned the classification level or a higher level to be able to view the security classification level. Make sure to indicate the placement of the new classification in the hierarchy. For further information, see "Setting the Order of Security Classifications".
Permissions:
When editing a classification, you must also be assigned the highest security level to view all of the available classifications for editing.To edit an existing security classification, complete the following steps:
Click Records then Configure from the Top menu. Click Security then Security Classification.
The Configure Security Classification Page is displayed.
Click the Edit icon (a pencil) next to the classification to edit.
The Create or Edit Security Classification Page is displayed.
Make any changes in the Brief Description text box, and click Submit Update. A message is displayed stating the security classification was updated successfully.
Click OK.
Prerequisites
Create any custom security classifications that are required. See "Creating or Editing a Custom Security Classification".
Assign yourself the highest classification level so you can view and reorder all levels. See "Changing a User's Classification".
Permissions:
The Admin.RecordManager and Admin.SecurityClassifications rights are required to perform this action. These rights are assigned by default to the Records Administrator role. You must also have the specific security classification level assigned to you to view or work with it.Use this procedure to indicate the order of the security classifications within the security classification hierarchy. If only the built-in security classifications are used in their default order, this procedure is not needed.
Click Records then Configure from the Top menu. Click Security then Security Classification.
The Configure Security Classification Page is displayed.
Use the up arrow (and down arrow) to move a selected security classification up or down in the classification hierarchy. The highest classification should be at the top of the list and the lowest at the bottom.
Important:
The last item in the list will be unclassified regardless of the name you assign to it. Make sure you have a "classification" in your hierarchy that you intend to be unclassified.Click Submit Update. A message is displayed stating the configuration was updated successfully.
A classification cannot be deleted until any references to the classification in content are removed (see "Viewing Security Classification References"). Security classification assignments must also be manually removed from users (see "Removing a User's Classification"). If you attempt to delete a security classification still in use, a message is displayed stating the classification is in use by users (it is assigned to users and must be removed) or by content.
Search for security classifications from the Search page. Use the search results to see which items have the classification in use. Screening can also be used to quickly isolate content. For further information, see the Oracle Fusion Middleware Administrator's Guide for Universal Records Management.
Permissions:
The Admin.RecordManager and Admin.SecurityClassifications rights are required to perform this action. These rights are assigned by default to the Records Administrator role. You must also be assigned the highest security level to view all of the available classifications for deleting.Click Records then Configure from the Top menu. Click Security then Security Classification.
The Configure Security Classification Page is displayed.
Click the Delete icon (a red X) next to the classification to delete.
A message is displayed stating the security classification was deleted successfully.
Click OK.
Classified items are automatically declassified after 25 years unless they were exempted from declassification. When an item is declassified, the Declassify On Date field is compared to the Publication Date, and if the retention period for classification status exceeds ten years, an alert is presented to the user.
Permissions:
The Admin.PrivilegedEnvironment right is required to perform this action. This right is assigned by default to the Records Officer and Records Administrator roles.Click Records then Configure then Settings from the Top menu.
The Configure Retention Settings Page is displayed. If necessary, expand the Security section.
In the "Maximum years before declassifying" field, enter the number of years after which items will be declassified (the default is 25). If this field is not available, the Admin.PrivilegedEnvironment right is not assigned to the user viewing the page.
f this field is set to 0 and auto-computation of declassification dates is chosen, any classified items currently in the system are set to declassified.
Click Submit Update. A message is displayed stating the configuration was successful.
Click OK.
Use this procedure to view references to a security classification (those disposition rules which use the security classification in their definitions).
Permissions:
The Admin.RecordManager and Admin.SecurityClassifications rights are required to perform this action. These rights are assigned by default to the Records Administrator role. You must also be assigned the highest security level to view all of the available classifications for viewing.Click Records then Configure from the Top menu. Click Security then Security Classification.
The Configure Security Classification Page is displayed.
Select the security classification to view, and click the Info icon.
The Security Classification Information Page is displayed.
Click Reference from the Page menu.
The Security Classification References Page is displayed
This page shows all users and content assigned to the selected security classification level. If any of the content links are clicked, the associated content information page for that item is displayed.
You can assign security classifications only if the classified security feature has been enabled (see "Enabling or Disabling Classified Security").
Permissions:
Administrator privileges in Oracle UCM ('sysadmin' permissions) are required to assign user access to classifications. Your own assigned classification level must also be at least the level being assigned to users. For example, if you are assigned the classification level 'Secret', you cannot assign the classification level 'Top Secret' to users.Click Admin Applets from the Administration menu.
The Administration Applets for the server are displayed.
Click the User Admin icon.
The User Admin utility starts.
On the Users tab, select the user in the Users list, and click Edit. The Edit User page is displayed.
Make sure the Info tab is active.
In the Security Classification field, select the maximum security level the user should have access to from the option list available on the pull-down menu.
Click OK. Repeat the process for each user.
Note the following considerations:
If a user is not assigned any security classification, the user cannot pick an initial classification while checking in a content item. Because specifying the initial classification is mandatory, the user cannot check the item into the repository.
It is recommended that the highest security classification be assigned to the Records Administrator and overall administrator. This allows them to perform all classification-related tasks (for example, on behalf of someone who must downgrade or declassify an item but does not have the required classification privileges).
The assigned security classification of users determines what items they can access.
Permissions:
Administrator privileges in Oracle UCM are required to perform this action. Your own assigned classification level must also be at least the level being accessed.Click Admin Applets from the Administration menu.
The Administration Applets for the server are displayed.
Click the User Admin icon.
The User Admin utility starts.
On the Users tab, select the user in the Users list, and click Edit. The Edit User page is displayed.
Make sure the Info tab is active.
In the Security Classification field, select the new maximum security level the user should have access to. Click the options list arrow, and click the classification needed.
Click OK.
You may want to remove access from a user who is no longer authorized for a classification or to delete a classification no longer in use. Remove any references to a classification before deletion it.
Permissions:
Administrator privileges in Oracle UCM are required to perform this action. Your own assigned classification level must also be at least the level being accessed.Click Admin Applets from the Administration menu.
The Administration Applets for the server are displayed.
Click the User Admin icon.
The User Admin utility starts.
On the Users tab, select the user in the Users list, and click Edit. The Edit User page is displayed.
Make sure the Info tab is active.
In the Security Classification field, delete the current security level (using the keyboard or by selecting the blank line from list).
Click OK.
Custom security is optional and are another layer of security in addition to supplemental markings (see "Supplemental Markings").
Two types of custom security are available:
Simple custom security fields, where custom field are configured to be matched by a user rather than a designated supplemental marking. This is called custom supplemental markings in the DoD 5015 standard,
Advanced custom security, where security is applied to fields that use option lists. Security can be applied to individual items in the option list.
Unlike supplemental markings, custom security is enforced at the item level. Supplemental markings are enforced at both the record folder and the item level.
This section covers the following topics:
To work with custom security, you need to have one of the following rights:
Admin.Triggers: This right enables you to view information.
Admin.RecordManager: In addition to viewing information, this right also enables you to create (add), edit, and delete custom security.
A simple custom security field pairs a custom content field with a custom user field. For example, you can create a custom security field such as "Project Name." Users must be assigned the appropriate project name or names to access or view an item assigned with custom security. If the "match all" setting is enabled, a user must be assigned to all the same projects as an item is assigned to for the user to access an item with multiple project assignments. If a user does not match all project names, the user cannot access an item.
You can opt to select the "match all" feature for custom security fields just as you can with supplemental markings. Content is then checked in with one or more custom security field options, such as a particular project name, assigned to the content.
For instance, "user1" is assigned project name "Pangea" only. The user named "user2" is assigned both project name "Pangea" and "Tectonic." If content is checked in with multiple field options assigned (for example, "Pangea" and "Tectonic"), then only a user with all project names assigned (user2) can access that content. If the "match all" setting is disabled, then a user only must match one field option to access an item.
Advanced custom security also limits access to content items. However, advanced security can also restrict access based on aliases as well as individual users. This type of security assigns security at the item level for option lists. When using this type of security, the only metadata that can be used is that which has an option list associated with it. Access can then be restricted to individual items in the option list by limiting which accounts, which users, or which aliases of users can access specific options.
The following tasks are often performed when managing custom security:
Use this procedure to enable the custom security feature. It can be enabled or disabled at any time.
Permissions:
The Admin.RecordManager right is required to enable custom security. This right is assigned by default to the Records Administrator role.Click Records then Configure then Settings from the Top menu.
The Configure Retention Settings Page is displayed. Expand the Security section if needed.
Click the Custom Security box.
Click Submit Update. A message is displayed saying the configuration was successful.
Click OK.
To disable the feature, clear the Custom Security box.
Use this procedure to create a new simple custom security field.
Important:
Make sure you have defined the custom field for the items in the Configuration Manager utility, and the custom field for the users in the User Admin utility before performing this task. See "Simple Custom Security Field Example" for a step-by-step sample of setting up a simple custom security field.You can create custom security fields only if the custom security field feature has been enabled (see "Enabling or Disabling Custom Security Usage").
Permissions:
The Admin.RecordManager right is required to perform this action. This right is assigned by default to the predefined Records Administrator role.Click Records then Configure from the Top menu. Click Security then Custom Security.
The Configure Custom Security Page is displayed.
In the Custom Security Field area, click Add.
The Create or Edit Simple Custom Security Field Page is displayed.
Enter a name for the field in the Custom Security Field text box.
Select the document metadata name for the content field from the Content Field list.
Select the metadata name of the user field from the User Field list.
(Optional) Click the Match all box to force the user entries to match all content field entries. Leave this box cleared to allow only one content field to match the user field.
Click Create. The successfully created custom security field message is displayed.
Click OK.
To edit an existing custom security field, complete the following steps:
Click Records then Configure from the Top menu. Click Security then Custom Security.
The Configure Custom Security Page is displayed.
Click Edit Field from the field's Actions menu.
Make the necessary edits:
Select the name of the metadata field from the Content Field list.
Select the name of the user metadata field in the User Field list.
Select or clear the Match all box.
Click Submit Update. A message indicates the update was successful.
Click OK.
Use this procedure to add advanced security to an existing field. The field used must be one which has an option list associated with it.
You can add custom security only if the custom security feature is enabled (see "Enabling or Disabling Custom Security Usage").
Permissions:
The Admin.RecordManager right is required to perform this action. This right is assigned by default to the predefined Records Administrator role.Click Records then Configure from the Top menu. Click Security then Custom Security.
The Configure Custom Security Page is displayed. If necessary, click the Advanced Custom Security tab to display that page.
Click Add.
The Select Security Dialog is displayed.
Select a field from the list. Note that only fields with option lists are available for selection.
Click OK.
The Advanced Custom Security Option Page is displayed showing the option items associated with the field that was chosen.
Click the Actions menu for the option item which needs security. Click Edit Security.
The Select Security Dialog is displayed.
Select users or aliases who will have access to content items with that individual option list value. See "Setting ACLs During Software Use" for details about choosing users or aliases.
If needed, select a security group from the list.
The Advanced Custom Security Option Page is re-displayed, showing the selections just made.
To alter custom security for a field (including removing the security), complete the following steps:
Click Records then Configure from the Top menu. Click Security then Custom Security.
The Configure Custom Security Page is displayed.
In the Advanced Custom Security area, click Edit Security on the Actions menu of the option item. To remove security for the option item, click Remove Security on the Actions menu of the option item.
When editing, the Advanced Custom Security Dialog is displayed.
Select a field from the list. Note that only fields with option lists are available for selection.
Click OK.
The Advanced Custom Security Option Page is displayed showing the option items associated with the field that was chosen.
Click the Actions menu for the option item which needs security. Click Edit Security.
The Select Security Dialog is displayed.
Select users or aliases who will have access to content items with that individual option list value. See "Setting ACLs During Software Use" for details about choosing users or aliases.
If needed, select a security group from the list.
The Advanced Custom Security Option Page is re-displayed, showing the selections just made. The security is now in place.
Permissions:
Either the Admin.Triggers or Admin.RecordManager right is required to perform this action. The Admin.Triggers right is assigned by default to the Records Officer and Records Administrator roles, and the Admin.RecordManager right to the Records Administrator role.Click Records then Configure from the Top menu. Click Security then Custom Security.
The Configure Custom Security Page is displayed.
In the custom field area, click the field to view.
The Custom Security Field Information Page is displayed.
Click OK when done.
You can delete a custom security field without having to remove references to it by users and content, unlike supplemental markings and security classifications.
Permissions:
The Admin.RecordManager right is required to delete a custom security field. This right is assigned by default to the Records Administrator role.Click Records then Configure from the Top menu. Click Security then Custom Security.
The Configure Custom Security Page is displayed.
Click Delete from the item's Actions menu. To delete multiple fields, select the checkbox next to the field name and click Delete in the Table menu. A field can also be deleted when viewing the field's Custom Security Field Information Page.
A message displays, indicating the deletion was successful.
Click OK.
This example gives step-by-step instructions for setting up a custom security field called "Project Name." It includes the following processes:
Create the Custom Security Field in User Admin. Oracle UCM assigns the "u" prefix. Assign the field options to the user.
Rebuild the Content Server search index, and restart the server. Complete instructions are in the Oracle Fusion Middleware System Administrator's Guide for Content Server.
Create the Custom Security Field using the exact field names defined in the Oracle UCM utilities.
After the custom security field is set up, test the field by checking in and accessing items assigned field options. See Verify the Custom Security Field.
This portion of the example creates the custom security field as a document field within the Configuration Manager utility. The field will be available for use on the check-in form.
Click Admin Applets from the Administration menu on the left.
The Administration Applets for the server are displayed.
Click the Configuration Manager icon.
The Configuration Manager utility starts.
Click the Information Fields tab.
Click Add.
The Add Custom Info Field page is displayed.
Type ProjectName, and click OK. The Add Custom Info Field page is displayed. Specify the field attributes:
In the Field Caption text box, enter a space between any compound words (in the above example, "Project" and "Name") so the field label displays properly.
In the Field Type list, click Long Text.
Click the Enable Options List box. The Configure button becomes enabled. Click this button.
The Configure Option List page opens. In the Options List Type, click the Edit and Multiselect List option.
Click Edit next to Use Option List. The Option List page is displayed.
In the options list, type Pangea. Press Enter for a carriage return, then type Tectonic. Click OK three times.
Click Update Database Design.
This portion of the example creates the custom security field as an information field called "Project Name" within the User Admin utility.
Click Admin Applets from the Administration menu.
The Administration Applets for the server are displayed.
Click the User Admin icon.
The User Admin utility starts.
Open the Information Fields tab.
Click Add.
The Add Custom Info Field page is displayed.
Type ProjectName and click OK. The Add Metadata Field page is displayed. Specify the field attributes:
In the Field Caption text box, enter a space between any compound words (as in the example, "Project" and "Name") so the field label displays properly.
In the Field Type list, click Long Text.
Click the Enable Options List box. The Options List Settings tab becomes enabled.
In the Options List Type, click the Edit and Multiselect List option.
Click Edit. The Option List page is displayed.
In the options list, type Pangea. Press Enter for a carriage return, and then type Tectonic. Click OK twice.
Click Update Database Design.
Click the Users tab. Create a uesr named 'user1' then select that name and click Edit. The Edit User "user1" page is displayed.
In the Project Name list, click the down arrow, and click the project name "Pangea" from the list. Repeat for "Tectonic." You now have a comma-separated list of project names assigned to user1.
Click OK.
Restart the Content Server.
This portion of the example creates the custom security field. Make sure the Custom Security Field option is enabled in the Configure Retention Settings Page, and you have defined the document and user fields in the appropriate administration utilities.
Click Configure then Custom Security Fields from the Configure Retention Settings Page.
On the Configure Custom Security Page, click Add.
The Create or Edit Simple Custom Security Field Page is displayed.
In the Custom Security Field text box, type Project Name.
From the Content Field list, click ProjectName.
From the User Field list, click ProjectName.
Click the Match all box to force a user to match all content field entries. This is the strictest setting. If a user is not assigned all project names assigned to an item, the user cannot access that item.
Click Create.
This portion of the example demonstrates how the custom security field restricts access.
Log in as user1 and check in an item with both "Pangea" and "Tectonic" selected as project names in the check-in form. Search for the item you just checked in as user1. The search should be successful.
Now log in as a new user without any custom field assignments. Attempt to access the item user1 just checked in. The attempt to view the item should not be successful because the new user does not have any assigned field options.
Log in as an administrator and assign the new user the field option "Pangea." Disable the Match all option for the custom security field. Log in as the new user and attempt to access the item with "Pangea" and "Tectonic" assigned as the project name. The access should now be successful because only one field list option has to match, and the user is assigned the appropriate field list option.
Note:
Classification guides can be set up only if the ClassifiedEnhancements component is enabled.Classification guides are used to facilitate the proper and uniform derivative classification of information. Specifically, Executive Order 12958 defines "derivative classification" as incorporating, paraphrasing, restating or generating in new form information already classified, and marking the newly developed material consistent with the classification markings applying to the source information.
Classification guides are not the same as classifying a piece of content with a setting such as Top Secret, and so on. Guides are separate from classifications.
This section covers the following topics:
Classification guides (and their associated topics) enable convenient implementation of multiple classification schemes.
They are used to define default values for the following classification-related metadata fields on the content check-in page:
Initial Classification (xInitialClassification)
Reason(s) for classification (xClassificationReason)
Declassify exemption category (xDeclassifyExemptionCategory)
Declassify on event (xDeclassifyOnEventDescription)
Declassify on date (xDeclassifyOnDate)
This makes checking in classified content easier and more consistent, with similar content having the same classification metadata. The Records Administrator can define multiple classification guides. Each classification guide consists of one or more topics, which provide a further level of detail for grouping classified content.
The default metadata field values associated with a classification topic are suggestions only; they can be overridden. Classification guides can be set up only if the ClassifiedEnhancements component is enabled.
The following tasks are performed when managing classification guides:
Permissions:
The Admin.ClassificationGuide right is required to perform this action. This right is assigned by default to the Records Officer and Records Administrator roles.Click Records then Configure from the Top menu. Click Security then Classification Guide.
The Configure Classification Guide Page is displayed.
Click Add.
The Create or Edit Classification Guide Page is displayed.
Provide a guide ID and a guide name (description), and click Create.
A "Successfully created classification guide" page is displayed showing the identifier and name of the newly created classification guide. The page also includes an Actions menu, where current classification guides can be edited or deleted or add topics added to it. See "Creating or Editing a Classification Topic".
Click OK to return to the Configure Classification Guide Page).
Use this procedure to edit a classification guide:
Click Configure then Classification then Configure Classification Guide from the Configure Retention Settings Page.
The Configure Classification Guide Page is displayed.
Select a classification guide to edit from the list and click Info.
The Classification Guide Information Page is displayed.
Click Edit then click Edit Classification Guide from the Page menu.
The Create or Edit Classification Guide Page is displayed.
Change the classification guide name as required. The guide ID cannot be modified. Click Submit Update when done.
A "Successfully updated classification guide" page is displayed showing the identifier and modified name of the classification guide. The page also includes a menu where the current classification guide can be edited or deleted or have topics added to it. See "Creating or Editing a Classification Topic".
Click OK to return to the Configure Classification Guide page.
Permissions:
The Admin.ClassificationGuide right is required to perform this action. This right is assigned by default to the Records Officer and Records Administrator roles.Click Configure then Classification then Configure Classification Guide from the Configure Retention Settings Page.
The Configure Classification Guide Page is displayed.
Select the classification guide to delete from the menu and click Delete.
The classification guide is deleted.
Click OK to return to the Configure Classification Guide Page.
Permissions:
The Admin.ClassificationGuide right is required to perform this action. This right is assigned by default to the Records Officer and Records Administrator roles.Click Configure then Classification then Configure Classification Guide from the Configure Retention Settings Page.
The Configure Classification Guide Page is displayed.
Select the classification guide whose information to view from the menu and click Info.
The Configure Classification Guide Page is displayed.
The page shows the identifier and name of the selected classification guide. The page also includes a menu where the current classification topic can be edited or deleted or have topics added to it See "Creating or Editing a Classification Topic".
Click OK to return to the Configure Classification Guide Page.
Permissions:
The Admin.ClassificationGuide right is required to perform this action. This right is assigned by default to the Records Officer and Records Administrator roles.Click Configure then Classification then Configure Classification Guide from the Configure Retention Settings Page.
The Configure Classification Guide Page is displayed.
Select the classification guide in the list to create the topic for, and click Info.
The Configure Classification Guide Page is displayed.
From the Page menu, click Edit then click Configure Topics.
The Administer Classification Topic Page is displayed.
Click Add.
The Create or Edit Classification Topic Page is displayed.
Provide a name and description for the classification topic, and click Create when done.
The Configure Topic Settings Page is displayed.
Provide default values for each of the metadata fields, and click Submit Update when done.
Use this procedure to edit an existing classification topic:
Click Configure then Classification then Configure Classification Guide from the Configure Retention Settings Page.
The Configure Classification Guide Page is displayed.
In the list, select the classification guide to edit and click Info.
The Classification Guide Information Page is displayed.
From the Actions menu, choose Configure Topics.
The Administer Classification Topic Page is displayed.
From the Topic Name list, select the classification topic to edit, and click Info.
The Classification Topic Information Page is displayed.
From the Actions menu, choose Edit.
Edit the description for the classification topic, and click Submit Update when done.
A "Successfully updated classification topic" page is displayed.
Click OK to return to the Administer Classification Topic Page.
Permissions:
The Admin.ClassificationGuide right is required to perform this action. This right is assigned by default to the Records Officer and Records Administrator roles.Click Configure then Classification then Configure Classification Guide from the Configure Retention Settings Page.
The Configure Classification Guide Page is displayed.
From the list select the classification guide to edit topic settings for, and click Info.
The Classification Guide Information Page is displayed.
From the Actions menu, choose Configure Topics.
The Administer Classification Topic Page is displayed.
From the Topic Name list, select the classification topic whose settings to edit, and click Info.
The Classification Topic Information Page is displayed.
From the Page menu, choose Edit then Edit Topic Settings.
Modify the default metadata field values as required, and click Submit Update when done.
The Edited Topic Settings page is displayed.
Click OK to return to the Administer Classification Topic Page.
Permissions:
The Admin.ClassificationGuide right is required to perform this action. This right is assigned by default to the Records Officer and Records Administrator roles.Click Configure then Classification then Configure Classification Guide from the Configure Retention Settings Page.
The Configure Classification Guide Page is displayed.
In the list select the classification guide whose topic to delete, and click Info.
The Classification Guide Information Page is displayed.
From the Page menu, choose Configure Topics.
The Administer Classification Topic Page is displayed.
From the Topic Name list, select the classification topic to delete, and click Delete.
A message is displayed stating the classification topic was successfully deleted.
Click OK to return to the Administer Classification Topic Page.
Permissions:
The Admin.ClassificationGuide right is required to perform this action. This right is assigned by default to the Records Officer and Records Administrator roles.Click Configure then Classification then Configure Classification Guide from the Configure Retention Settings Page.
The Configure Classification Guide Page is displayed.
In the list, select the classification guide whose topic information is to be viewed, and click Info.
The Classification Guide Information Page is displayed.
From the Page menu, choose Edit then choose Configure Topics.
The Administer Classification Topic Page is displayed.
From the Topic Name list, select the classification topic to view, and click Info.
The Classification Topic Information Page is displayed.
Click OK to return to the Administer Classification Topic Page.