| Oracle® Fusion Middleware Administrator's Guide for Oracle WebCenter 11g Release 1 (11.1.1) Part Number E12405-10 |
|
|
View PDF |
| Oracle® Fusion Middleware Administrator's Guide for Oracle WebCenter 11g Release 1 (11.1.1) Part Number E12405-10 |
|
|
View PDF |
This chapter describes how to secure Oracle WebCenter applications and components with SSL.
This chapter includes the following sections:
Section 27.1, "Securing the Browser Connection to WebCenter Spaces with SSL"
Section 27.2, "Securing the Browser Connection to a Custom WebCenter Application with SSL"
Section 27.3, "Securing the Connection from Oracle HTTP Server to WebCenter Spaces with SSL"
Section 27.4, "Securing the Browser Connection to the Wiki Service with SSL"
Section 27.5, "Securing the Browser Connection to the Discussions Service with SSL"
Section 27.6, "Securing the WebCenter Spaces Connection to Portlet Producers with SSL"
Section 27.7, "Securing the WebCenter Spaces Connection to the LDAP Identity Store"
Section 27.8, "Securing the WebCenter Spaces Connection to Oracle Content Server with SSL"
Section 27.9, "Securing the WebCenter Spaces Connection to IMAP and SMTP with SSL"
Section 27.10, "Securing a Custom WebCenter Application's Connection to IMAP and SMTP with SSL"
Section 27.11, "Securing the WebCenter Spaces Connection to Oracle SES with SSL"
Section 27.12, "Securing the WebCenter Spaces Connection to OWLCS with SSL"
Section 27.14, "Securing the WebCenter Spaces Connection to an External BPEL Server with SSL"
Note:
The following can use WS-Security with message protection, and consequently have no hard requirement for SSL:BPEL servers - Worklist service
WSRP Producers
Oracle WebLogic Communication Services (OWLCS) - IMP service
Microsoft Live Communication Server (LCS) - IMP service
Oracle WebCenter Discussions - Discussions and Announcements
The content of this chapter is intended for Fusion Middleware administrators (users granted the Admin role through the Oracle WebLogic Server Administration Console). Users with the Monitor or Operator roles can view security information but cannot make changes. See also, Section 1.8, "Understanding Administrative Operations, Roles, and Tools."
Securing the browser connection to WebCenter Spaces with SSL consists of the following steps:
The first step is to generate a custom keystore for WebCenter Spaces.
To create a custom keystore:
Go to JDK_HOME/bin/ and open a command prompt.
Using keytool, generate a key pair:
keytool -genkeypair -keyalg RSA -dname "dname" -alias alias -keypass key_password -keystore keystore -storepass keystore_password -validity days_valid
Where:
dname is the DN (distinguished name) to use (for example, cn=customidentity,dc=example,dc=com)
alias is the alias to use (for example, webcenter_wls)
key_password is the password for the new public key, (for example, welcome1)
keystore is the keystore name, (for example, webcenter_wls.jks)
keystore_password is the keystore password, (for example, welcome1)
days_valid is the number of days for which the key password is valid (for example, 360).
Note:
You must use the-keyalg parameter and specify RSA as its value as shown above as the default algorithm (DSA) used by keytool for generating the key is incompatible with Oracle WebServices Security Manager requirements.Export the certificate containing the public key so WebCenter Spaces clients can import it into their trust store:
keytool -exportcert -v -alias alias -keystore keystore -storepass keystore_password -rfc -file certificate_file
Where:
alias is the WebCenter Spaces alias (for example, webcenter_wls)
keystore is the keystore name, (for example, webcenter_wls.jks)
keystore_password is the keystore password, (for example, welcome1)
certificate_file is the file name for the certificate to export the key to (for example, webcenter_wls.cer)
Determine the trust store to use:
Since you are using a self-signed certificate, you must update it as a trusted certificate in the server trust store. To do this, you must determine your trust store by going to the server:
Log into the WebLogic Server Administration Console.
In the Domain Structure pane, expand Environments and click Servers.
In the list of servers, click WLS_Spaces.
Open the Configuration tab, and the Keystores subtab.
The Keystores Settings pane displays (see Figure 27-1).
Note down the location of the server in the Java Standard Trust Keystore field (shown in Figure 27-1).
Note that the cacerts file may be "read only", in which case you must change its permissions so that it's writable.
Import the self-signed certificate generated above in this trust store:
keytool -importcert -trustcacerts -alias alias -file certificate_file -keystore cacerts -storepass changeit
Where:
alias is the WebCenter Spaces alias (for example, webcenter_wls)
certificate_file is the file name for the certificate to export the key to (for example, webcenter_wls.cer)
When prompted whether to trust the self-signed certificate, answer yes.
The next step is to configure the Custom Identity and Java Trust keystores on the WebCenter Spaces server.
To configure the identity and trust keystores:
Log in to the WebLogic Server Administration Console.
For information on logging into the WebLogic Server Administration Console, see Section 1.12.2, "Oracle WebLogic Server Administration Console."
In the Domain Structure pane, expand Environment and click Servers.
The Summary of Servers pane displays (see Figure 27-2).
Click the WebCenter Spaces server (WLS_Spaces) to configure the identity and trust keystores.
The Settings pane for the WebCenter Spaces server displays (see Figure 27-3).
Figure 27-3 Settings Pane for WebCenter Spaces Server
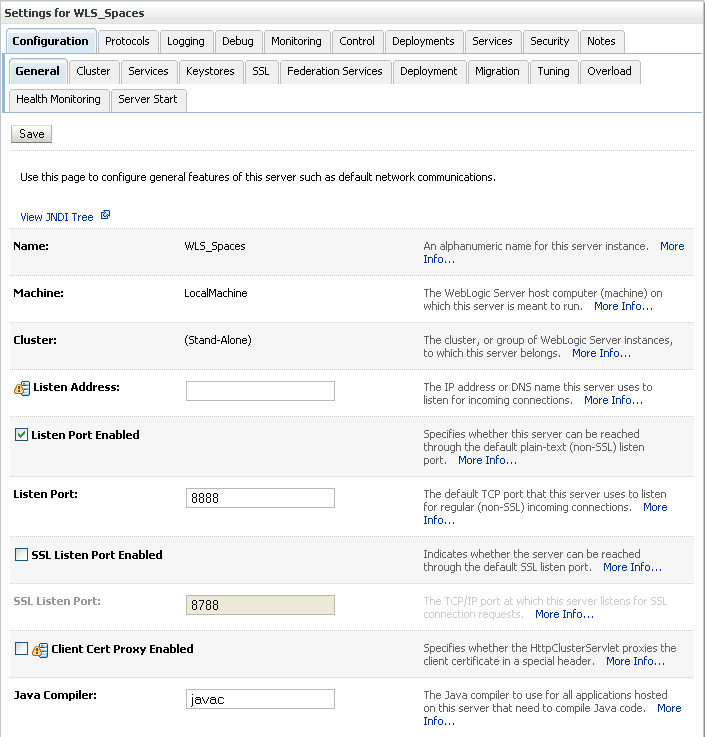
Open the Configuration tab, and then the Keystores subtab.
The Keystores pane displays (see Figure 27-4).
For Keystores, select Custom Identity and Java Standard Trust and click Save.
Under Identity, enter the path and filename of the Custom Identity Keystore you created in Section 27.1.1, "Creating the Custom Keystore."
Enter JKS as the Custom Identity Keystore Type.
Enter and confirm the Custom Identity Keystore password.
Under Trust, enter and confirm the Java Standard Trust Keystore password (typically set to changeit).
Click Save to save your entries.
Open the SSL tab.
Enter the Private Key Alias (for example, webcenter_wls).
Enter the Private Key Passphrase (for example, welcome1)
Click Save to save your entries.
To configure the SSL connection:
On the Settings pane for the WebCenter Spaces server, open the Configuration tab and then the General subtab.
The General Configuration pane displays (see Figure 27-5).
Check SSL Listen Port Enabled.
Enter an SSL Listen Port number and click Save.
Open the SSL subtab and expand the Advanced options at the bottom of the page.
The SSL advanced options are displayed (see Figure 27-6).
Figure 27-6 Advanced SSL Configuration Settings
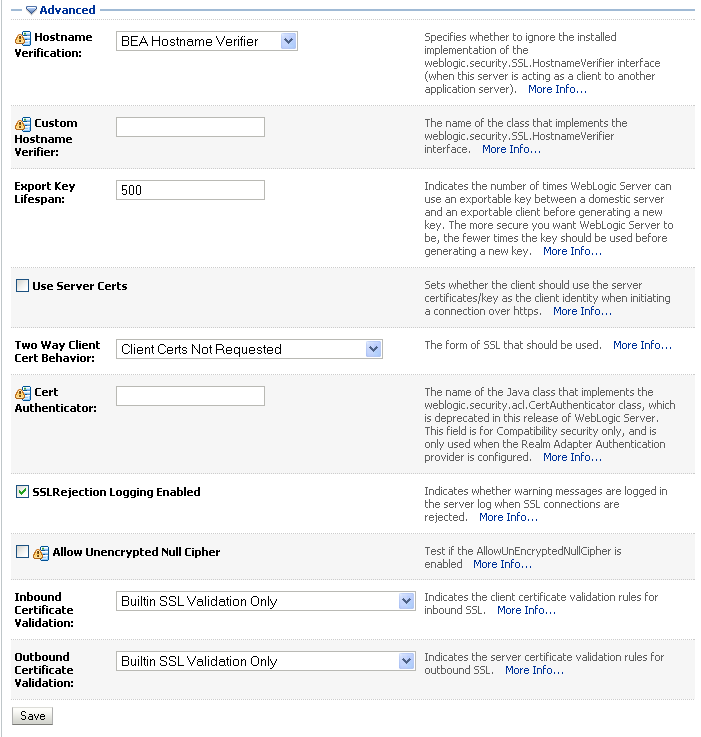
Check that the Two Way Client Cert Behavior option is set to Client Certs Not Requested and click Save.
Open the Control tab.
The Control Settings pane displays (see Figure 27-7).
Click Restart SSL.
Restart the WebLogic Server and open the SSL WebCenter Spaces URL.
For a development or test environment only (that is, not for a production environment), if the hostname in the certificate does not match the host name, then the server must be started with:
-Dweblogic.security.SSL.ignoreHostnameVerification=true
Accept the certificate for the session and log in.
Securing the browser connection to a custom WebCenter application uses the same configuration steps as for securing the browser connection to WebCenter Spaces. The only difference is that the configuration occurs on the managed server that is hosting the custom WebCenter application deployment rather than the WLS_Spaces server. For more information, see Section 27.1, "Securing the Browser Connection to WebCenter Spaces with SSL."
Securing the connection between the Oracle HTTP Server (OHS) and WebCenter Spaces is described in the following sections:
Section 27.3.1, "Configuring the Identity and Trust Keystores"
Section 27.3.4, "Wiring the WebCenter Spaces Ports to the HTTP Server"
For instructions on how to configure the Identity and Trust keystores, see Section 27.1, "Securing the Browser Connection to WebCenter Spaces with SSL."
To configure the SSL Connection:
On the Settings pane for the WebCenter Spaces server, open the Configuration tab and then the General subtab.
The General Configuration pane displays (see Figure 27-8).
Check SSL Listen Port Enabled.
Enter an SSL Listen Port number and click Save.
On the Configuration tab, open the SSL subtab, and then expand the Advanced options at the bottom of the page.
The SSL advanced options are displayed (see Figure 27-9).
Figure 27-9 Advanced SSL Configuration Settings

Set the Two Way Client Cert Behavior option to Client Certs Not Requested and click Save.
Open the Control tab on the Settings pane, and select the Start/Stop subtab.
Click Restart SSL.
Open the SSL WebCenter Spaces URL.
Accept the certificate for the session and log in.
In the WSL Administration Console, click View Changes and Restarts on the Change Center pane and restart any affected servers or components.
To install the Oracle HTTP Server:
Install the WebTier.
Do not select WebCache; only select the HTTP Server.
Uncheck the checkbox to associate a WebLogic server during install.
Navigate to the WT_ORACLE_HOME/instances/<your_instance>/bin directory and start OHS using the following command:
./opmnctl startall
Check the status of OHS using the following command:
./opmnctl status -l
To wire the WebCenter Spaces ports to the HTTP server:
Open the file WT_ORACLE_HOME/instances/<your_instance>/config/OHS/ohs1/mod_wl.conf.
Add the following entry to mod_wl.conf to make WebCenter Spaces work with OHS:
<IfModule mod_weblogic.c>
WebLogicHost host_id
WebLogicPort port
Debug OFF
WLLogFile /tmp/ohs.log
MatchExpression *.jsp
</IfModule>
<Location />
SetHandler weblogic-handler
</Location>
Replacing host_id and port with the WebCenter Spaces server ID and port number.
Open the file WT_ORACLE_HOME/instances/<your_instance>/config/OHS/ohs1/mod_ssl.conf.
Add the following entry to mod_ssl.conf to make WebCenter Spaces run on the OHS SSL port:
<IfModule mod_weblogic.c>
WebLogicHost host_id
WebLogicPort port
WLLogFile /tmp/ohs_ssl.log
Debug OFF
DebugConfigInfo ON
SecureProxy ON
MatchExpression *.jsp
WlSSLWallet SSL_wallet
</IfModule>
<Location />
SetHandler weblogic-handler
</Location>
Replacing host_id and port with the WebCenter SSL server ID and port number, and SSL_wallet with the path to the WebLogic SSL wallet (for example, WT_ORACLE_HOME/instances/<your_instance>/config/OHS/ohs1/keystores/default).
Go to WT_ORACLE_HOME/instances/<your_instance>/bin and start and check the status of OHS using the following commands:
./opmnctl stopall ./opmnctl startall ./opmnctl status -l
To configure the SSL certificates:
For OHS to trust WebCenter's certificate, the WLS_Spaces certificate must be imported into the OHS trust store. Export the certificate from the WLS_Spaces identity keystore:
keytool -exportcert -v -alias webcenter_wls -keystore webcenter_wls.jks -storepass <password> -rfc -file webcenter_wls.cer
Import the certificate into the wallet on the OHS side using orapki:
orapki wallet add -wallet . -trusted_cert -cert webcenter_wls.cer -auto_login_only
For WebCenter to trust OHS certificates, export the user certificate from OHS wallet and import it as a trusted certificate in the WebLogic trust store.
orapki wallet export -wallet . -cert cert.txt -dn 'CN=\"Self-signed Certificate for ohs1 \",OU=EXAMPLEORGUNIT,O=EXAMPLEORG,L=EXAMPLELOCATION,ST=CA,C=US'
Import the above certificate into the WLS_Spaces managed server trust store available in /scratch/wcwlsinstall/0408/wlshome/jrockit_160_05_R27.6.2-20/jre/lib/security/cacerts:
keytool -file cert.txt -importcert -trustcacerts -alias ohs_cert -keystore cacerts -storepass changeit
Restart OHS and the WLS_Spaces server.
You should now be able to access the SSL OHS, as well as the non-SSL OHS.
As with securing the browser connection to WebCenter Spaces, securing the Wiki service connection with SSL is described in the following sections:
To configure the identity and trust key stores:
Log in to the WebLogic Server Administration Console.
For information on logging into the WebLogic Server Administration Console, see Section 1.12.2, "Oracle WebLogic Server Administration Console."
In the Domain Structure pane, expand Environment and click Servers.
The Summary of Servers pane displays (see Figure 27-10).
Click the Services server (WLS_Services) to configure the identity and trust keystores.
The Settings pane for the services server displays (see Figure 27-11).
Figure 27-11 Settings Pane for Services Server
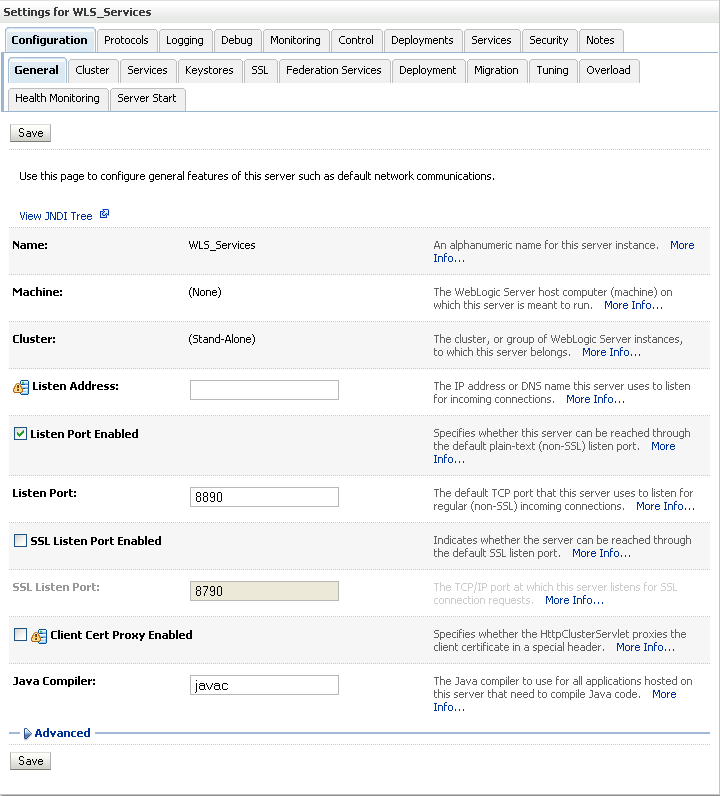
Open the Configuration tab, and then the Keystores subtab.
The Keystores pane displays (see Figure 27-12).
For Keystores, select Custom Identity and Java Standard Trust and click Save.
Open the Control tab.
The Control Settings pane displays (see Figure 27-13).
Click Restart SSL.
To configure the SSL connection:
On the Settings pane for the Services server, open the Configuration tab and then the General subtab.
The General Configuration pane displays (see Figure 27-14).
Check SSL Listen Port Enabled.
Enter an SSL Listen Port number and click Save.
On the Configuration tab, open the SSL subtab, and then expand the Advanced options at the bottom of the page.
The SSL advanced options are displayed (see Figure 27-15).
Figure 27-15 Advanced SSL Configuration Settings

Make sure that the Two Way Client Cert Behavior option is set to Client Certs Not Requested and click Save.
Restart the WLS_Services server and open the SSL Wiki URL at https://host:port/owc_wiki.
Accept the certificate for the session and log in.
Securing the browser connection to the Discussions service with SSL is described in the following sections:
The first step is to generate a custom keystore as shown below:
Go to JDK_HOME/bin/ and open a command prompt.
Using keytool, generate a key pair:
keytool -genkeypair -keyalg RSA -dname "dname" -alias owc_discussions -keypass key_password -keystore owc_discussions.jks -storepass keystore_password -validity days_valid
Where:
dname is the DN (distinguished name) to use (for example, cn=customidentity,dc=owc_discussions,dc=example,dc=com)
key_password is the password for the new public key, (for example, welcome1)
keystore_password is the keystore password, (for example, welcome1)
days_valid is the number of days for which the key password is valid (for example, 360).
Note:
You must use the-keyalg parameter and specify RSA as its value as shown above as the default algorithm (DSA) used by keytool for generating the key is incompatible with Oracle WebServices Security Manager requirements.Export the certificate containing the public key:
keytool -exportcert -v -alias owc_discussions -keystore owc_discussions.jks -storepass keystore_password -rfc -file owc_discussions.cer
Where:
keystore_password is the keystore password, (for example, welcome1)
Determine the trust store to use:
Since you are using a self-signed certificate, you must update it as a trusted certificate in the server trust store. To do this, you must determine your trust store by going to the server:
Log into the WebLogic Server Administration Console.
In the Domain Structure pane, expand Environments and click Servers.
In the list of servers, click WLS_Services.
Open the Configuration tab, and the Keystores subtab.
The Keystores Settings pane displays (see Figure 27-16).
Figure 27-16 Keystores Sub-tab for WLS_Services
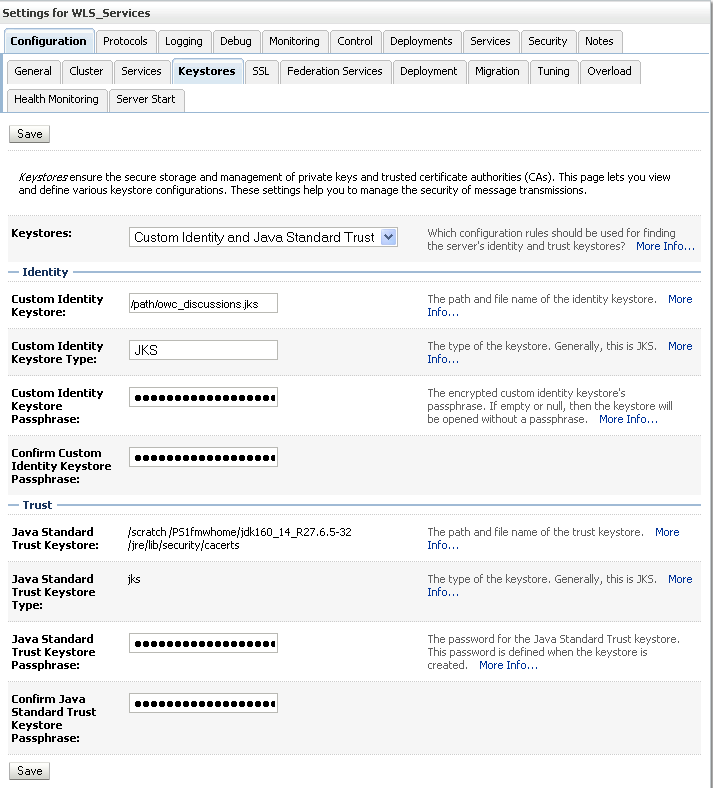
Note down the location of the server in the Java Standard Trust Keystore field (shown in Figure 27-1).
Note that the cacerts file may be "read only", in which case you must change its permissions so that it's writable.
Import the self-signed certificate generated above in this trust store:
keytool -importcert -trustcacerts -alias owc_discussions -file owc_discussions.cer -keystore cacerts -storepass changeit
When prompted to trust the self-signed certificate, say yes.
To configure the identity and trust key stores:
Log in to the WebLogic Server Administration Console.
For information on logging into the WebLogic Server Administration Console, see Section 1.12.2, "Oracle WebLogic Server Administration Console."
In the Domain Structure pane, expand Environment and click Servers.
The Summary of Servers pane displays (see Figure 27-17).
Click the Services server (WLS_Services) to configure the identity and trust keystores.
The Settings pane for the services server displays (see Figure 27-18).
Figure 27-18 Settings Pane for Services Server

Open the Configuration tab, and then the Keystores subtab.
The Keystores pane displays (see Figure 27-19).
For Keystores, select Custom Identity and Java Standard Trust.
Under Identity, specify the keystore as owc_discussions.jks.
Set the keystore type to JKS
Enter and confirm the keystore passphrase, (for example, welcome1)
Under Trust, set the Java Standard Trustore passphrase to changeit (this is fixed value) and click Save.
Go to WLS console -> servers -> WLS_Services -> Configuration tab -> General sub tab
Check the SSL Port enabled, specify a port that you want, and save
Go to WLS console -> servers -> WLS_Services -> Configuration tab -> SSL sub tab
Specify private key alias as owc_discussions, passwd -> welcome1
Open the Control tab.
The Control Settings pane displays (see Figure 27-20).
Click Restart SSL.
To configure the SSL connection:
On the Settings pane for the Services server, open the Configuration tab and then the General subtab.
The General Configuration pane displays (see Figure 27-21).
Check SSL Listen Port Enabled.
Enter an SSL Listen Port number and click Save.
On the Configuration tab, open the SSL subtab, and then expand the Advanced options at the bottom of the page.
The SSL advanced options are displayed (see Figure 27-22).
Figure 27-22 Advanced SSL Configuration Settings

Set the Two Way Client Cert Behavior option to Client Certs Not Requested and click Save.
Restart the WLS_Services server and open the SSL Discussions URL at https://host:port/owc_discussions.
Accept the certificate for the session and log in.
Securing the connection to WSRP and PDK-Java portlet producers with SSL is described in the following sections:
Section 27.6.1, "Configuring the Identity and Trust Key Stores"
Section 27.6.3, "Registering the SSL-enabled WSRP Producer and Running the Portlets"
Section 27.6.4, "Registering the SSL-enabled PDK-Java Producer and Running the Portlets"
To configure the identity and trust key stores:
Log in to the WebLogic Server Administration Console.
For information on logging into the WebLogic Server Administration Console, see Section 1.12.2, "Oracle WebLogic Server Administration Console."
In the Domain Structure pane, expand Environment and click Servers.
The Summary of Servers pane displays (see Figure 27-23).
Click the Portlet server (for example, WLS_Portlet) to configure the identity and trust keystores.
The Settings pane for the Portlet server displays (see Figure 27-24).
Figure 27-24 Settings Pane for Portlet Server

Open the Configuration tab, and then the Keystores subtab.
The Keystores pane displays (see Figure 27-25).
For Keystores, select Custom Identity and Java Standard Trust and click Save.
Open the Control tab.
The Control Settings pane displays (see Figure 27-26).
Click Restart SSL.
To configure the SSL connection:
In the Domain Structure pane, expand Environment and select Servers.
Click the Portlet server (for example, WLS_Portlet) for which you want to configure SSL.
Select Configuration.
Check SSL Listen Port Enable.
Enter a listen port number.
Select Configuration > SSL, and then open the Advanced options at the bottom of the page.
Select the Two Way Client Cert Behavior attribute and choose the Client Certs Not Requested option.
Click Save.
Restart the WebLogic Server and open the SSL URL.
Accept the certificate for the session and log in.
To register the SSL-enabled WSRP producer and run the portlets:
Configure the WebCenter Spaces managed server to use the Custom Identity and Java Standard Trust store. This also uses the certificates in JDK_HOME/jre/lib/security/cacerts.
Download the certificate of the HTTPS producer URL and save it in .PEM format.
Use Firefox 3.0 or later to download the certificate directly to .PEM format, or for other browsers use the WebLogic Server der2pem tool to convert to PEM format. For more information about using the der2pem tool, see "der2pem" in the Oracle Fusion Middleware Command Reference for Oracle WebLogic Server. Note that WebLogic does not recognize any other format other than .PEM format.
Import the certificate into the cacerts file in JDK_HOME/jre/lib/security using the following keytool command:
keytool -importcert -alias portlet_cert -file HOME/portlet_pem -keystore ./cacerts -storepass password
Where:
portlet_cert is the portlet certificate alias
portlet_pem is the portlet certificate file (for example, portlet_cert.pem)
password is the keystore password
Restart WLS_Spaces.
Start WLST as described in Section 1.12.3.1, "Running Oracle WebLogic Scripting Tool (WLST) Commands."
Connect to the Administration Server for the target domain with the following command:
connect('user_name','password, 'host_id:port')
Where:
user_name is the name of the user account with which to access the WLS_Spaces server (for example, weblogic)
password is the password with which to access the WLS_Spaces server
host_id is the host ID of the Administration Server
port is the port number of the Administration Server (for example, 7001).
Run the registerWSRPProducer WLST command to register the producer:
registerWSRPProducer('webcenter', 'sslwsrpprod','producer_wsdl)
Where:
sslwsrpprod is the name of the SSL-enabled WSRP producer
producer_wsdl is the WSDL URL of the SSL-enabled WSRP producer
For example:
registerWSRPProducer('webcenter', 'sslwsrpprod','https://example.oracle.com:7004/richtextportlet/portlets/wsrp2?WSDL')
Navigate to the HTTP or HTTPS WebCenter URL.
Create a page and go to the Portlets link.
Go to the registered WSRP producer.
Add the portlet to the page.
Go to the view mode of the page and check that the WSRP portlet renders correctly.
To register the SSL-enabled PDK-Java Producer and run the portlets:
Configure the WebCenter Spaces managed server to use the Demo Identity and Trust store. This also uses the certificates in JDK_HOME/jre/lib/security/cacerts.
Log in to the WebLogic Server Administration Console.
For information on logging into the WebLogic Server Administration Console, see Section 1.12.2, "Oracle WebLogic Server Administration Console."
On the Domain Structure pane, expand Environment and click Servers.
The Summary of Servers pane displays (see Figure 27-27).
Click WLS_Spaces in the servers list.
The Settings pane displays (see Figure 27-28).
Figure 27-28 Settings Pane (WLS_Spaces Server)
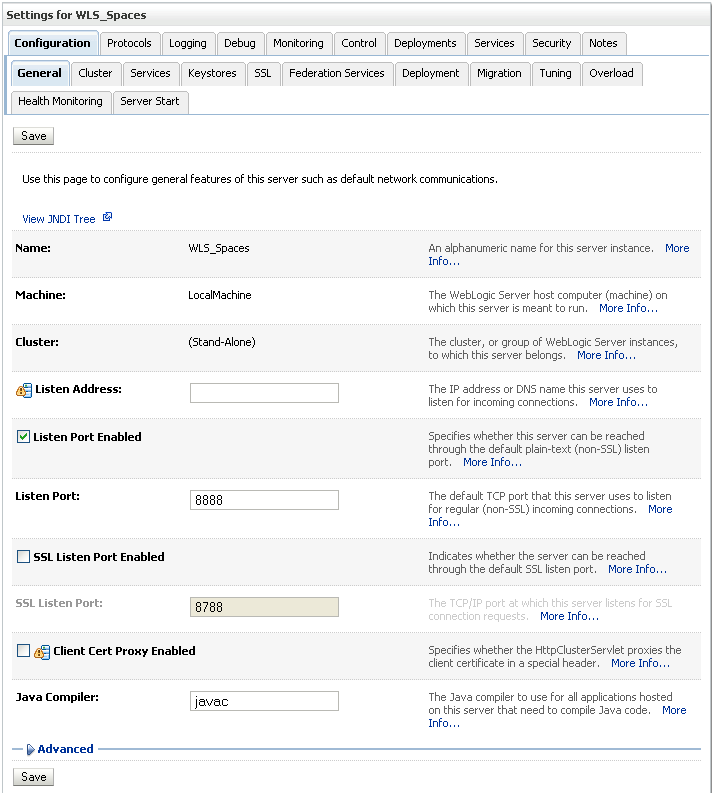
Open the Configuration tab and select the Keystores tab.
Make sure that the value for Demo Identity and Demo Trust is either jks or left blank.
Click Save.
Download the certificate of the HTTPS producer URL and save it in .PEM format.
Use Firefox 3.0 or later to download the certificate directly to .PEM format, or for other browsers use the WebLogic Server der2pem tool to convert to PEM format. For more information about using the der2pem tool, see "der2pem" in the Oracle Fusion Middleware Command Reference for Oracle WebLogic Server. Note that WebLogic does not recognize any other format other than .PEM format.
Import the certificate into the cacerts file in JDK_HOME/jre/lib/security using the following keytool command:
keytool -importcert HOME/portlet_cert.pem -keystore ./cacerts -storepass changeit
Restart WLS_Spaces.
Start WLST as described in Section 1.12.3.1, "Running Oracle WebLogic Scripting Tool (WLST) Commands."
Connect to the Administration Server for the target domain with the following command:
connect('user_name','password, 'host_id:port')
where:
user_name is the name of the user account with which to access the WLS_Spaces server (for example, weblogic)
password is the password with which to access the WLS_Spaces server
host_id is the host ID of the Administration Server
port is the port number of the Administration Server (for example, 7001).
Run the registerPDKJavaProducer command:
registerPDKJavaProducer('webcenter', 'ssljpdkprod', 'producer_wsdl')
Where:
ssljpdkprod is the name of the SSL-enabled PDK-Java producer
producer_wsdl is the WSDL URL of the SSL-enabled PDK-Java producer
This enables one-way SSL for a Web producer. That is, only the server side (web producer) uses certificates. The Web producer code also uses a shared key feature (discussed later) for client authentication.
Go to the HTTP or HTTPS WebCenter URL.
Create a page and go to the Portlets link.
Go to the registered PDK-Java producer.
Add the portlet to the page.
Go to the view mode of the page and check that the PDK-Java portlet renders correctly.
To configure the LDAP server port for SSL, refer to the appropriate administration documentation for the LDAP server. For Oracle Internet Directory (OID), an SSL port is installed by default. To use this port for LDAP communication from WebCenter, the identity store should be configured for authentication with the appropriate authenticator. See Chapter 24, "Configuring the Identity Store" for the steps to do this for the identity store.
Note:
When entering the Provider Specific information, be sure to specify an SSL port and to check the SSL Enabled checkbox.If the CA is unknown to the Oracle WebLogic server, complete the two additional steps described in the following subsections:
For more information, see "Setting Up a One- Way SSL Connection" in the Oracle Fusion Middleware Security Guide.
If the CA is unknown to the Oracle WebLogic server (the command prompts the user to enter the keystore password) you must use orapki to create a certificate. The following example shows how to use this command to create the certificate serverTrust.cert:
orapki wallet export -wallet CA -dn "CN=myCA" -cert oid_server_trust.cert
If the CA is unknown to the Oracle WebLogic server, use the utility keytool to import the Oracle Internet Directory's CA into the WebLogic trust store. The following example shows how to use keytool to import the file oid_server_trust.cert into the server trust store cacerts:
keytool -importcert -v -trustcacerts -alias oid_server_trust -file oid_server_trust.cer -keystore cacerts -storepass changeit
For instructions on how to configure Oracle Content Server (OCS) for SSL, see Section 11.2.1.2.3, "Configuring Secure Sockets Layer (SSL)." For instructions on adding a trusted certificate to the WebCenter Spaces trust store, see the section on importing the certificate into the trust store in Section 27.1.2, "Configuring the Custom Identity and Java Trust Keystores."
Before reconfiguring the mail server connection, you must first import the certificate into the trust store. Follow the steps below to put the certificate in the trust store and configure WebCenter Spaces to use the trust store.
To secure the WebCenter Spaces connection to IMAP and SMTP with SSL:
Open a browser and connect to your IMAP server with the following command:
https://imapserver:ssl_port
For example:
https:mailserver.example:993
Place your cursor on the page, right-click, and select Properties.
Click Certificate.
In the popup window, click the Details tab and click Copy to File...
Be sure to use the DER encoded binary(X.509) format and copy to a file.
Convert the .DER format certificate to .PEM format.
Use Firefox 3.0 or later to download the certificate directly to.PEM format, or for other browsers use the WebLogic Server der2pem tool to convert to PEM format. For more information about using the der2pem tool, see "der2pem" in the Oracle Fusion Middleware Command Reference for Oracle WebLogic Server. Note that WebLogic does not recognize any other format other than .PEM format.
Import the certificate into the cacerts in the JDK_HOME using the following command:
keytool -import -alias imap_cer -file cert_file.cer -keystore cacerts -storepass changeit
Where cert_file is the name of the certificate file you downloaded.
Register the mail server connection as described in Section 15.3, "Registering Mail Servers."
Restart Webcenter Spaces.
Log into WebCenter Spaces and provide your mail credentials.
To secure the connection to IMAP and SMTP with SSL for a custom WebCenter application:
Follow the steps in Section 27.9, "Securing the WebCenter Spaces Connection to IMAP and SMTP with SSL" up to and including step 7.
Add the following property to the truststore:
-Djavax.net.ssl.trustStore=C:\jive\mailtool\jssecacerts -Djavax.net.ssl.trustStorePassword=changeit
For example:
set JAVA_PROPERTIES=-Dplatform.home=%WL_HOME% -Dwls.home=%WLS_HOME% -Dweblogic.home=%WLS_HOME% -Djavax.net.ssl.trustStore=C:\jive\mailtool\jssecacerts -Djavax.net.ssl.trustStorePassword=changeit
Restart the custom WebCenter application.
Log into the application and provide your mail credentials.
Before registering the SES connection, you must first import the certificate into the trust store. Follow the steps below to put the certificate in the trust store and register the Oracle Secure Enterprise Search (SES) connection.
To download the certificate of the HTTPS URL and save it:
Use your browser to navigate to the Web Services URL that Oracle Secure Enterprise Search exposes to enable search requests at:
http://host:port/search/query/OracleSearch
For example:
https://example.com:7777/search/query/OracleSearch
Place your cursor on the page, right-click with your mouse, and select Properties.
Click Certificate.
In the popup window, open the Details tab, and click Copy to File...
Use DER encoded binary(X.509) format and copy the certificate to a file.
Convert the .DER format certificate to .PEM format.
Use Firefox 3.0 or later to download the certificate directly to.PEM format, or for other browsers use the WebLogic Server der2pem tool to convert to PEM format. For more information about using the der2pem tool, see "der2pem" in the Oracle Fusion Middleware Command Reference for Oracle WebLogic Server. Note that WebLogic does not recognize any other format other than .PEM format.
Import the certificate into DemoTrustKeyStore.jks or cacerts in the JDK_HOME using one of the following commands:
keytool -import -alias ses_cer -file cert_file.cer -keystore cacerts -storepass changeit
where cert_file is the name of the certificate file you downloaded.
Register the SES connection as described in Section 18.3.1, "Registering Oracle SES Services."
Restart WebCenter Spaces.
To secure the WebCenter Spaces connection to Oracle WebLogic Communication Services (OWLCS) with SSL, follow the steps below to import the certificate into the trust store, and point WebCenter Spaces to use the trust store. Note that securing the WebCenter Spaces connection to OWLCS with SSL is optional since OWLCS can be configured with confidentiality using WS-Security. See Section 28.4, "Securing Oracle WebLogic Communication Services (OWLCS) with WS-Security."
Before registering the OWLCS connection, you must first import the certificate into the trust store. Follow the steps below to put the certificate in the trust store:
Open your browser and go to the OWLCS server (for example, https://example.com:port/PresenceConsumerService/services/PresenceConsumer)
Place your cursor on the page, right-click, and select Properties.
Click Certificate.
In the popup window, open the Details tab and click Copy to File...
Use Firefox 3.0 or later to download the certificate directly to.PEM format, or for other browsers use the WebLogic Server der2pem tool to convert to PEM format. For more information about using the der2pem tool, see "der2pem" in the Oracle Fusion Middleware Command Reference for Oracle WebLogic Server. Note that WebLogic does not recognize any other format other than .PEM format.
Import the certificate into the cacerts using the following keytool command:
keytool -import -alias owlcs_cer -file cert_file.cer -keystore cacerts -storepass changeit
where cert_file is the name of the certificate file you downloaded.
Locate the cacerts file used by the OWLCS server in the OWLCS installation, and also update the OWLCS referenced cacerts file with this certificate:
keytool -import -alias owlcs_cer -file cert_file.cer -keystore cacerts -storepass changeit
Register the Oracle WebLogic Communication Services connection as described in Section 14.3, "Registering Instant Messaging and Presence Servers."
Restart the WebCenter Spaces server.
To secure the WebCenter Spaces connection to Microsoft Live Communication Server (LCS) or Office Communication Server 2007 (OCS) with SSL, follow the steps below to import the certificate into the trust store, and point WebCenter Spaces to use the trust store. Note that securing the WebCenter Spaces connection to Microsoft Live Communication Server or Office Communication Server with SSL is optional since they can be configured with confidentiality using WS-Security.
Before registering the LCS or OCS connection, you must first import the certificate into the trust store. Follow the steps below to put the certificate in the trust store:
Open your browser and go to the communication server (for example, https://example.com/RTC)
Place your cursor on the page, right-click, and select Properties.
Click Certificate.
In the popup window, open the Details tab and click Copy to File...
Use Firefox 3.0 or later to download the certificate directly to.PEM format, or for other browsers use the WebLogic Server der2pem tool to convert to PEM format. For more information about using the der2pem tool, see "der2pem" in the Oracle Fusion Middleware Command Reference for Oracle WebLogic Server. Note that WebLogic does not recognize any other format other than .PEM format.
Import the certificate into the cacerts using the following keytool command:
keytool -import -alias lcs_cer -file cert_file.cer -keystore cacerts -storepass changeit
where cert_file is the name of the certificate file you downloaded.
Locate the cacerts file used by the communication server in the installation, and also update the communication server referenced cacerts file with this certificate:
keytool -import -alias lcs_cer -file cert_file.cer -keystore cacerts -storepass changeit
Register the communication server connection as described in Section 14.3, "Registering Instant Messaging and Presence Servers."
Restart the WebCenter Spaces server.
This section describes how to secure the WebCenter Spaces connection to a BPEL server when the BPEL server resides in an external SOA domain.
Note:
When SOA is installed in an external domain, the Identity Asserter and Authenticator should be configured exactly as for WebCenter. For more information on configuring the Identity Asserter and Authenticator for an external LDAP identity store, see Section 24.1, "Reassociating the Identity Store with an External LDAP."To secure the WebCenter Spaces connection to an external BPEL server with SSL:
Copy the public certificate (webcenter_wls.cer) from WebCenter into the SOA domain.
Go to JDK_HOME/bin/ and open a command prompt.
Generate a custom keystore on the SOA domain naming the keystore soa_server1.jks, and the alias soa_server1 using the following keytool command:
keytool -genkeypair -keyalg RSA -dname dname -alias soa_soa_server1 -keypass key_pass -keystore soa_server1.jks -storepass keystore_password -validity days_valid
Where:
dname is the DN (distinguished name) to use (for example, cn=customidentity,dc=example,dc=com)
key_pass is the password for the new public key, (for example, welcome1)
keystore_password is the keystore password, (for example, welcome1)
days_valid is the number of days for which the key password is valid (for example, 360).
Export the certificate from soa_wls.jks using the following command:
keytool -exportcert -v -alias soa_server1 -keystore soa_server1.jks -storepass keystore_password -rfc -file soa_server1.cer
Where:
keystore_password is the keystore password, (for example, welcome1)
Log in to the WebLogic Server Administration Console on the SOA domain.
For information on logging into the WebLogic Server Administration Console, see Section 1.12.2, "Oracle WebLogic Server Administration Console."
In the Navigation pane, expand Environment and click Servers.
The Summary of Servers pane displays (see Figure 27-29).
From the Configuration tab, click soa_server1 in the list of servers.
The Settings page for soa_server1 displays (see Figure 27-30).
Figure 27-30 Settings Page for soa_server1
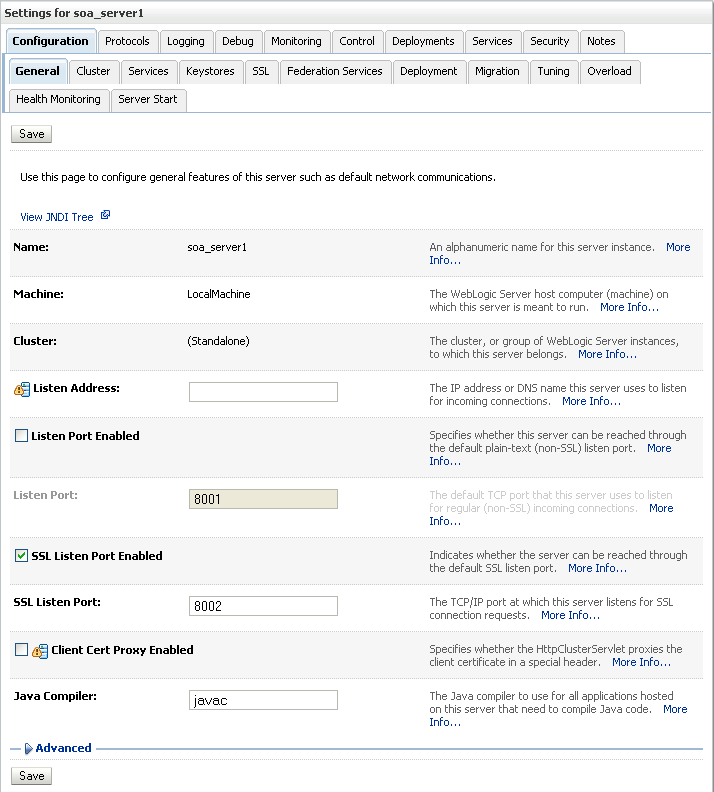
Open the Keystores tab.
The Keystore settings for soa_server1 displays (see Figure 27-31).
Figure 27-31 Keystore Settings for soa_server1
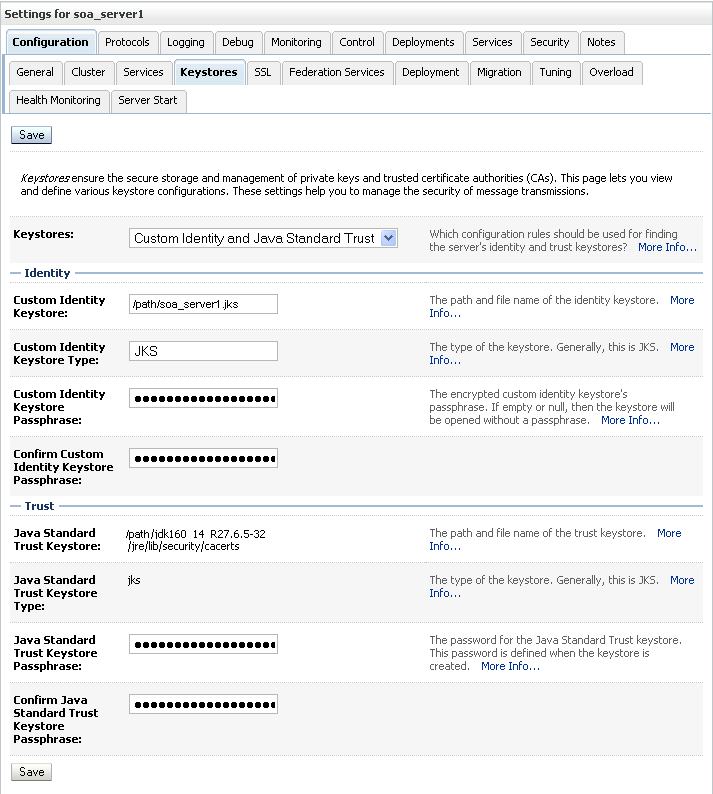
For Keystores, select Custom Identity and Java Standard Trust.
Specify the path and filename of keystore (soa_server1.jks) created above.
Go to the directory containing the java standard trust (cacerts file) specified in the Java Standard Trust Keystores field and import the SOA and WebCenter public certificates into this file so they may be trusted by the server:
keytool -importcert -trustcacerts -alias webcenter_wls -file webcenter_wls.cer -keystore cacerts -storepass keystore_password keytool -importcert -trustcacerts -alias soa_server1 -file soa_server1.cer -keystore cacerts -storepass keystore_password
Where:
keystore_password is the keystore password, (for example, welcome1)
Say yes when prompted to trust the certificate.
From the WLS Administration Console on the SOA domain, open the SSL tab.
The SSL settings for soa_server1 display (see Figure 27-32).
Figure 27-32 SSL Settings for soa_server1
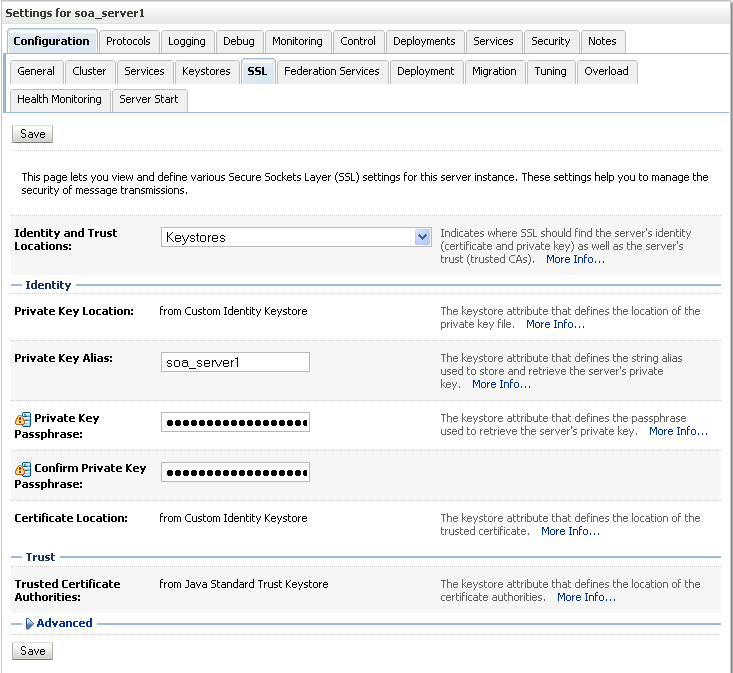
Specify soa_server1 as the Private Key Alias.
Enter and confirm the password for the private key (for example, welcome1) and click Save.
Open the General tab.
The General settings for soa_server1 display (see Figure 27-33).
Figure 27-33 General Settings for soa_server1
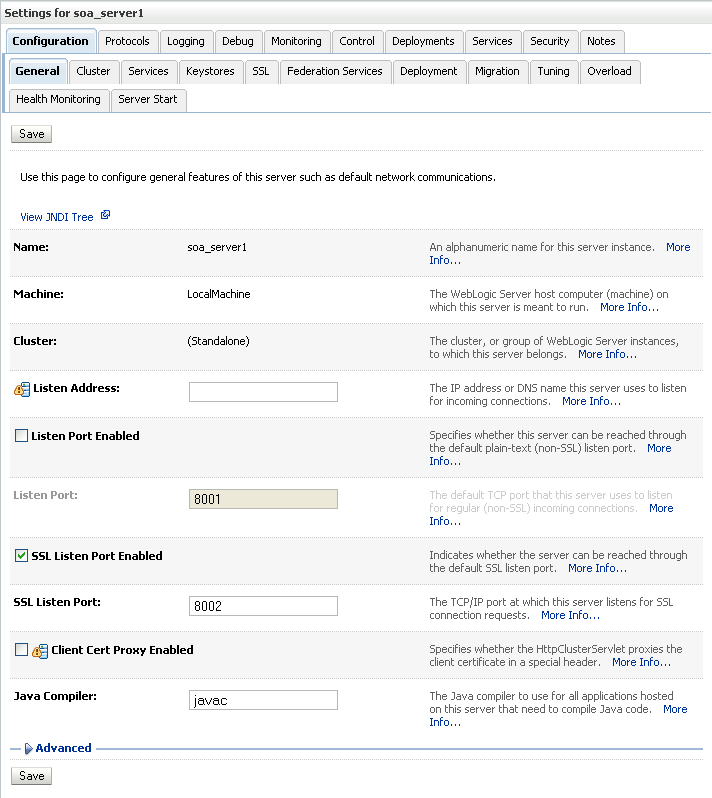
Make sure that Listen Port Enabled is not selected.
Select SSL Listen Port Enabled, specify the SSL Listen Port, and click Save.
Open the Control tab, and then open the Start/Stop sub-tab.
The Start/Stop settings for soa_server1 display (see Figure 27-34).
Figure 27-34 Start/Stop Settings for soa_server1
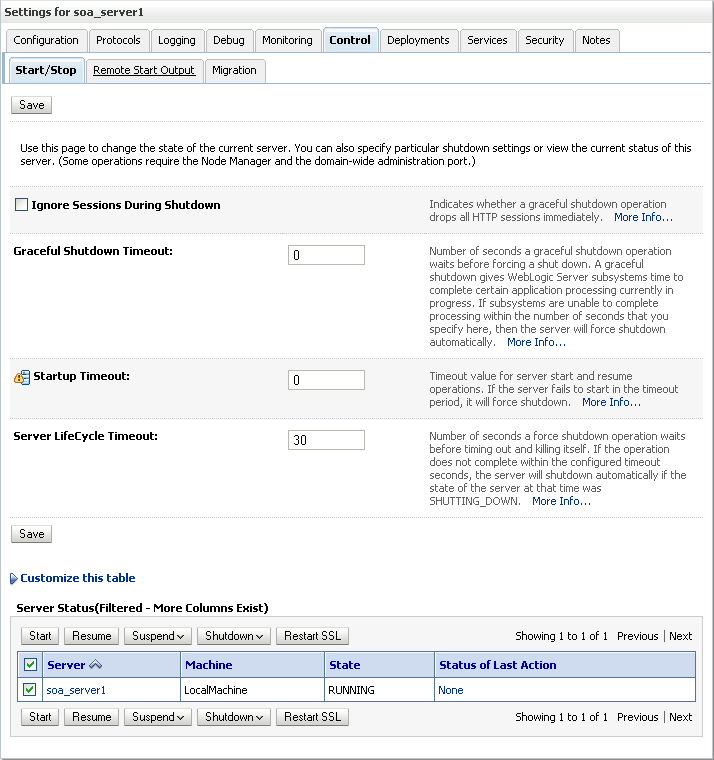
Select soa_server1 from the list of servers, and click Restart SSL.
Restart the soa_server1 Managed Server on the SOA domain.
From the WebCenter domain, import the soa_server1.cer certificate as a trusted certificate to the server trust store (cacerts) using the following keytool commands:
keytool -importcert -trustcacerts -alias soa_server1 -file soa_server1.cer -keystore cacerts -storepass changeit
Say yes when prompted to trust the certificate.
Add the Worklist connection on the WebCenter domain as described in Section 20.3.2, "Registering Worklist Connections" specifying the host:ssl_port settings for soa_server1 when defining the BPEL URL.
Restart the WLS_Spaces Managed Server.