| Oracle® Fusion Middleware Administrator's Guide for Oracle WebCenter 11g Release 1 (11.1.1) Part Number E12405-10 |
|
|
View PDF |
| Oracle® Fusion Middleware Administrator's Guide for Oracle WebCenter 11g Release 1 (11.1.1) Part Number E12405-10 |
|
|
View PDF |
This chapter describes how to reassociate the identity store with an external LDAP rather than the default embedded LDAP identity store. It also describes how to configure an LDAP server for Oracle Content Server and contains the following subsections:
Section 24.1, "Reassociating the Identity Store with an External LDAP"
Section 24.3, "Adding Users to the Embedded LDAP Identity Store"
Section 24.5, "Moving the Administrator Account to an External LDAP Server"
Section 24.6, "Granting the WebCenter Spaces Administrator Role to a WebCenter Spaces User"
Caution:
Before reassociating the identity store, be sure to back up the relevant configuration files:config.xml
jps-config.xml
system-jazn-data.xml
As a precaution, you should also back up the boot.properties file for the Administration Server for the domain.
Note that for custom WebCenter applications, the steps for Granting the WebCenter Spaces Administrator Role to a WebCenter Spaces User and Migrating the WebCenter Discussions Server to Use an External LDAP are not required. For more information about the identity store, see the Oracle Fusion Middleware Security Guide.
The content of this chapter is intended for Fusion Middleware administrators (users granted the Admin role through the Oracle WebLogic Server Administration Console). Users with the Monitor or Operator roles can view security information but cannot make changes. See also, Section 1.8, "Understanding Administrative Operations, Roles, and Tools."
In almost all cases, you must reassociate the identity store with an external LDAP server rather than using the default embedded LDAP. Although you can use many different types of LDAP servers (see Section 23.2, "Default Security Configuration" for a list of supported LDAPs), this section focuses on how to configure the identity store to use Oracle Internet Directory (OID).
To reassociate the identity store with OID:
Log in to the WebLogic Server Administration Console.
For information on logging into the WebLogic Server Administration Console, see Section 1.12.2, "Oracle WebLogic Server Administration Console."
In the Domain Structure pane (see Figure 24-1), click Security Realms.
The Summary of Security Realms pane displays (see Figure 24-10).
Figure 24-2 Summary of Security Realms pane
In the Name column, click the realm for which you want to reassociate the identity store.
The Realm Settings pane displays (see Figure 24-3).
Open the Providers tab.
The Providers Settings pane displays (see Figure 24-4).
Click New to add a new provider.
The Create a New Authentication Provider pane displays (see Figure 24-5).
Figure 24-5 Create a New Authentication Provider Pane
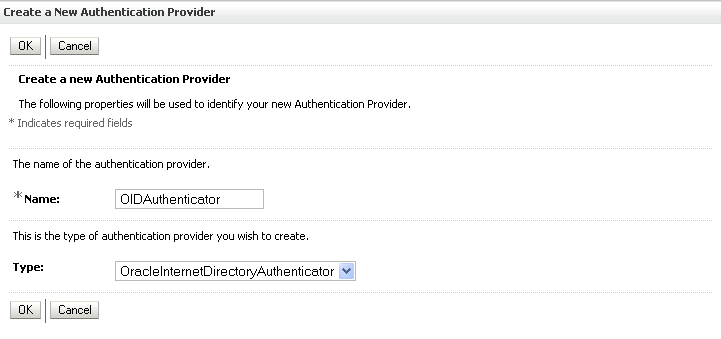
Enter a name for the provider (for example OIDAuthenticator for a provider that authenticates the user for the Oracle Internet Directory).
Select the authenticator appropriate for your LDAP directory from the list of authenticators.
Be sure to select the authenticator associated with the LDAP you are configuring rather than choosing the generic DefaultAuthenticator. For example, for OID select OracleInternetDirectoryAuthenticator, or for iPlanet select IPlanetAuthenticator.
Click OK to save your settings.
The Settings pane displays with the new authentication provider (see Figure 24-6).
Figure 24-6 Settings Pane - Authentication Providers
In the list of Authentication Providers, click the newly created provider.
The Settings Pane for the new authentication provider displays (see Figure 24-7).
Figure 24-7 Settings Pane for Authenticator
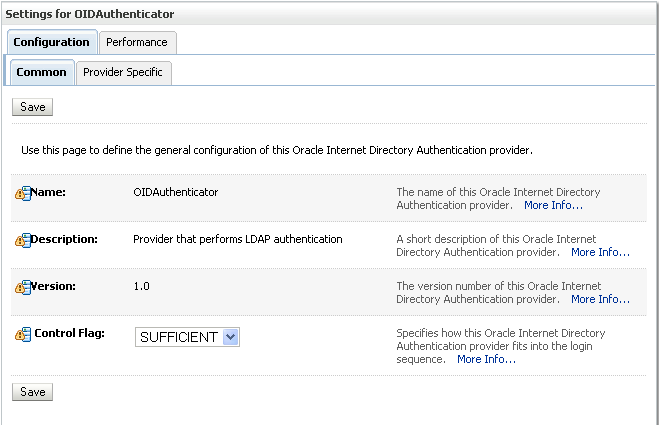
Set the Control Flag to SUFFICIENT.
Setting the Control Flag to SUFFICIENT indicates that if a user can be authenticated successfully by this authenticator, then the authentication provider should accept that authentication and should not invoke any additional authenticators.
Note:
If the authentication fails, it falls through to the next authenticator in the chain. Therefore, be sure all subsequent authenticators also have their control flag set toSUFFICIENT.Click Save to save this setting.
Open the Provider Specific tab to enter the details for the LDAP server.
The Provider Specific pane displays (see Figure 24-8).
Enter the details specific to your LDAP server.
| Parameter | Value | Description |
|---|---|---|
| Host: | The LDAP server's server ID (for example, <ldap_host>example.com) |
|
| Port: | The LDAP server's port number (for example, 3060) |
|
| Principal: | The LDAP user DN used to connect to the LDAP server (for example, cn=orcladmin) | |
| Credential: | The password used to connect to the LDAP server | |
| User Base DN: | Specify the DN under which your Users start (for example, cn=users,dc=example,dc=com) |
|
| Group Base DN: | Specify the DN that points to your Groups node (for example, cn=groups,dc=example,dc=com)
For Active Directory only, set the Group Base DN to |
|
| Use Retrieved User Name as Principal | Checked | Must be turned on |
| All Users Filter: | (&(uid=*)(objectclass=person)) |
Search to find all users under the User Base DN |
| User From Name Filter: | (&(uid=%u)(objectclass=person)) |
For Active Directory only, set this value to (&(sAMAccountName=%u)(objectclass=user)). |
| User Name Attribute: | uid |
If you modify a username attribute to something other than the default set for the LDAP server in the authenticator, you must also edit the jps-config.xml file to correspond to these values. Specifically, the username.attr and user.login.attr properties (highlighted below) must be added for user lookups to function correctly:
<!-- JPS WLS LDAP Identity Store Service Instance --> <serviceInstance name="idstore.ldap" provider="idstore.ldap.provider"> <property name="idstore.config.provider" value="oracle.security.jps.wls.internal.idstore.WlsLdapIdStoreConfigProvider"/> <property name="username.attr" value="uid"/> <property name="user.login.attr" value="uid"/> </serviceInstance>
For the permissible values for other LDAPs, such as Active Directory, see the appendix "OPSS System and Configuration Properties" in the Oracle Fusion Middleware Security Guide.
Click Save.
Return to the Providers tab and reorder the providers so that the new authentication provider is on top, followed by any other authenticators with the DefaultAuthenticator placed at the end of the list.
All should have their Control Flags set to SUFFICIENT so that subsequent authenticators can authenticate identities that fall through from the new provider all the way through to the DefaultAuthenticator (which is used only for the default file-based embedded LDAP). For example, logins such as the default administrator account are not typically created in the LDAP directory, but still need to be authenticated to start up the server. Unless identities are allowed to fall through to the DefaultAuthenticator, the default administrator account will not be authenticated. For more information about the DefaultAuthenticator and the default administrator account, see Section 24.5, "Moving the Administrator Account to an External LDAP Server."
Note:
WebCenter Spaces uses only the first authenticator to authenticate users in the identity store.Restart the Administration Server and the managed server for the changes to take effect.
For a production environment, Oracle recommends that you add the following configuration entry to the jps-config.xml file for best performance:
<serviceInstance provider="idstore.ldap.provider" name="idstore.ldap">
<property value="oracle.security.jps.wls.internal.idstore.WlsLdapIdStoreConfigProvider" name="idstore.config.provider"/>
<property name="CONNECTION_POOL_CLASS" value="oracle.security.idm.providers.stdldap.JNDIPool"/>
</serviceInstance>
You can add users to the embedded LDAP using the WebLogic Server Administration Console, or using an LDIF file and LDAP commands. Using an LDIF file lets you add additional attributes not available through the WebLogic Server Administration Console.
For Oracle Internet Directory, users are typically managed using ODSM (described in the section on "Managing Directory Entries" in the Oracle Fusion Middleware Administrator's Guide for Oracle Internet Directory).
Note:
If you are planning to reassociate your identity store with an external LDAP, perform that step first (as described in Section 24.1, "Reassociating the Identity Store with an External LDAP") to avoid having to migrate the users from the embedded LDAP to the newly configured external LDAP.WebCenter Spaces supports self-registration. New users who self-register with WebCenter Spaces are added directly to the identity store. For more information about self-registration, see Section 34.4, "Allowing Self-Registration."
Note:
Adding users to the identity store is typically a system administrator task and may not be a task for which application-level administrators have the required permissions.This section includes the following subsections:
Section 24.3.1, "Adding Users to the Identity Store Using the WLS Administration Console"
Section 24.3.2, "Adding Users to the Identity Store Using an LDIF File"
To add users to the embedded LDAP identity store from the WebLogic Server Administration Console:
Log in to the WebLogic Server Administration Console.
For information on logging into the WebLogic Server Administration Console, see Section 1.12.2, "Oracle WebLogic Server Administration Console."
In the Domain Structure pane (see Figure 24-9), click Security Realms.
The Summary of Security Realms pane displays (see Figure 24-10).
Figure 24-10 Summary of Security Realms pane

In the Name column, click the realm to which you want to add users.
The Realm Settings pane displays (see Figure 24-11).
Click the Users and Groups tab to display the list of current users.
Click New to add a new user.
On the Create a New User page, enter the new user login name in the Name field.
User names are case sensitive and must be unique. Do not use commas, tabs or any other characters in the following comma-separated list:
< >, #, |, &, ?, ( ), { }
In the Description field, enter a description for the user (for example, the user's full name).
From the Provider drop-down menu, select DefaultAuthenticator.
In the Password field, enter a password for the user.
The minimum password length for a user defined in the WebLogic Authentication provider is 8 characters (note that other LDAP providers may have different requirements for the password length). Do not use user name/password combinations such as weblogic/weblogic in a production environment.
Reenter the password in the Confirm Password field.
Click OK to save your changes and add the user.
The user should now appear in the list of users.
You can add users directly to the embedded LDAP identity store using an LDIF file. Using an LDIF file enables you to specify additional user attributes that are not available through the WebLogic Server Administration Console.As the embedded LDAP server is a conformant LDAP server, you can use LDAP commands to add or modify users. You can also search the directory, which is useful when exporting and importing user accounts.
To add users to the embedded LDAP using an LDIF file you must perform the following tasks:
When WebLogic Server is installed, the LDAP access credential is set as a randomized value and encrypted in the config.xml file. To enable external LDAP access, you must reset the access credential for the embedded LDAP.
To reset the access credential for the embedded LDAP:
Log in to the WebLogic Server Administration Console.
For information on logging into the WebLogic Server Administration Console, see Section 1.12.2, "Oracle WebLogic Server Administration Console."
In the Domain Structure pane (see Figure 24-13), click wc_domain.
Figure 24-13 Domain Structure Pane (wc_domain)
In the Settings pane for wc_domain, click the Security tab, and then click the Embedded LDAP tab.
The Settings Pane for wc_domain displays the embedded LDAP settings (see Figure 24-14).
Figure 24-14 Settings Pane with Embedded LDAP Settings
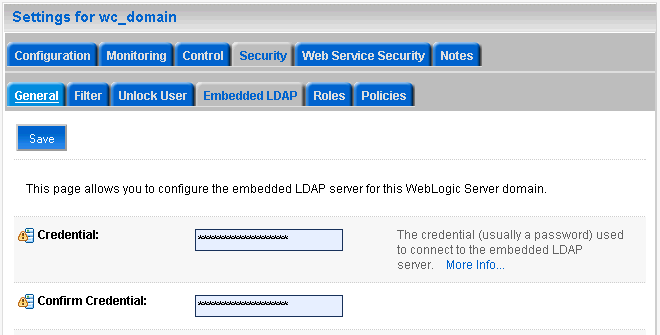
Enter a new password in the Credential field, and reenter it in the Confirm Credential field.
Click Save to save your settings.
Restart the WebLogic server.
After this, you are ready to access the LDAP server with the following values:
the DN value for admin access is "cn=Admin"
the password is the value you entered in the Credential field
the port is the same as the admin port, which by default is 7001
You can create an LDIF file with any text editor, and can include any attributes appropriate for the embedded LDAP directory. The objectclasses that are supported by default in the embedded LDAP server for WebLogic Server are the following:
person
inetOrgPerson
organizationalPerson
wlsUser
In order to interact successfully with the embedded LDAP server, you should understand the default layout of the directory information tree (DIT). The default layout in the embedded LDAP directory is shown in Figure 24-15.
Figure 24-15 Embedded LDAP Directory Information Tree
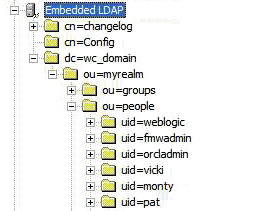
Note:
The naming attribute for the user entry in the embedded LDAP directory tree is "uid". This is different from the default configuration for Oracle Internet Directory (OID), where the naming attribute is "cn". Also, the location of the users in this tree is "ou=people,ou=myrealm,dc=wc_domain".The following example shows an LDIF file with the attributes that are displayed in WebCenter Spaces user profile screens:
dn: uid=john.doe,ou=people,ou=myrealm,dc=wc_domain description: John Doe cn: john.doe uid: john.doe sn: Doe objectclass: wlsUser objectclass: organizationalperson objectclass: inetOrgPerson objectclass: person objectclass: top userpassword: welcome1 displayName: John Doe employeeNumber: 12345 employeeType: Regular givenName: John homePhone: 650-555-1212 mail: john.doe@example.com title: Manager manager: uid=mary.jones,ou=people,ou=myrealm,dc=wc_domain preferredLanguage: en departmentNumber: tools facsimiletelephonenumber: 650-555-1200 mobile: 650-500-1200 pager: 650-400-1200 telephoneNumber: 650-506-1212 postaladdress: 200 Oracle Parkway l: Redwood Shores homepostaladdress: 123 Main St., Anytown 12345
To create a file with multiple user entries, just replicate the above lines as many times as required, with a blank line between entries.
Note:
WebCenter Spaces user profiles include some attributes that are only available in Oracle Internet Directory. These include the following attributes from theorclUserV2 objectclass:
orclTimeZone
orclDateOfBirth
maidenName
You cannot add these attributes to an embedded LDAP identity store.
The example below uses the ldappadd command, a part of the LDAP command line utilities provided with the Oracle Internet Directory server. For more information about using the ldappadd command, see "Oracle Internet Directory Data Management Tools" in the Oracle Fusion Middleware User Reference for Oracle Identity Management.
ldapadd -h weblogichost.example.com -p 7001 -D cn=Admin -w password -v -f newuser.ldif
add description:
John Doe
add cn:
john.doe
add uid:
john.doe
add sn:
Doe
add objectclass:
wlsUser
organizationalperson
inetOrgPerson
person
top
add userpassword:
password
add displayname:
John Doe
add employeenumber:
12345
add employeetype:
Regular
add givenname:
John
add homephone:
650-555-1212
add mail:
john.doe@example.com
add title:
Manager
add manager:
uid=mary.jones,ou=people,ou=myrealm,dc=wc_domain
add preferredlanguage:
en
add departmentnumber:
tools
add facsimiletelephonenumber:
650-555-1200
add mobile:
650-500-1200
add pager:
650-400-1200
add telephonenumber:
650-506-1212
add postaladdress:
200 Oracle Parkway
add l:
Redwood Shores
add homepostaladdress:
123 Main St., Anytown 12345
adding new entry uid=john.doe,ou=people,ou=myrealm,dc=wc_domain
modify complete
WebCenter Spaces provides a Users tab from which an administrator can add users defined in the identity store, and assign roles to those users within WebCenter Spaces. For information about managing users and user roles for WebCenter Spaces, see Chapter 34, "Managing Users and Roles for WebCenter Spaces ."
Caution:
The "Allow Password Change" property, which specifies whether users can change their passwords within WebCenter Spaces, should be carefully controlled for corporate identity stores. WebCenter Spaces administrators can set this property from the Profile Management Settings page in WebCenter Spaces. For more information, see Section 16.3.4, "Configuring Profile."The user interface and management tools with which to manage users and user roles for custom WebCenter applications depends on what has been implemented for the particular deployment. For more information about role-mapping for ADF-security based WebCenter applications, see the section What You May Need to Know About Application Roles and Enterprise Roles in the Oracle Fusion Middleware Fusion Developer's Guide for Oracle Application Development Framework.
When configuring the domain to use an external LDAP server, you can also optionally move the Fusion Middleware administrator account (weblogic by default) to the LDAP server.
If the Fusion Middleware administrator account, or any other appropriate user in LDAP, is in an LDAP group called "Administrators", then this account should be sufficient to manage the server, and the DefaultAuthenticator provider can be removed from the list of authentication providers. In this case, all users, including the administrator account, are authenticated against the external LDAP.
If you cannot create the weblogic (default) user in the external LDAP directory, there are two options. You can:
Keep the DefaultAuthenticator provider and use the weblogic account with the local embedded LDAP server in WebLogic Server to start and stop servers and do other administrator operations from the WebLogic Server Administration Console. If you keep the DefaultAuthenticator, make sure that the control flag for the DefaultAuthentication provider is set to SUFFICIENT. If you choose this option, you must also perform the additional steps described in Section 24.5.1, "Migrating the WebCenter Discussions Server to Use an External LDAP."
Note:
If theweblogic user account is used from the DefaultAuthenticator, this account should not be used to access the WebCenter Spaces application as the application code will not be able to find the user in the external LDAP store.Remove the DefaultAuthenticator and make sure that any valid user account used for administrator operations, such as starting and stopping servers, is included in an "Administrators" group or other named group that contains the list of users that are allowed to manage your domain in OID or other external LDAP. If a name other than "Administrators" is used, then you must update the group name in the definition of the WebLogic Server Global Administrator role. By default, this is defined as membership in the enterprise group called "Administrators". For information about changing the administrator group name, see Section 24.5.2, "Changing the Administrator Group Name."
If you've installed Oracle WebCenter Discussions Server and choose not to move the administrator account to an external LDAP (as described in Section 24.5, "Moving the Administrator Account to an External LDAP Server"), you must perform some additional steps to identify the new administrator account for the discussions server prior to reordering the authenticators on the WebLogic Server:
Select a user account from the external LDAP to be the administrator for the discussions server.
Create an administrator account in the DefaultAuthenticator (that is, the embedded LDAP) that matches the one you selected from the external LDAP. The account names in the embedded LDAP and the external LDAP server must be the same.
For information about adding users to the embedded LDAP, see Section 24.3, "Adding Users to the Embedded LDAP Identity Store."
Log in to the Oracle WebCenter Discussions Server Admin Console with the boot-identity account (that is, weblogic) at:
http://host:port/owc_discussions/admin
Where host and port are the host ID and port number of the WLS_Services managed server.
Click Settings > Admins/Moderators.
The Admins & Moderators page displays (see Figure 24-16).
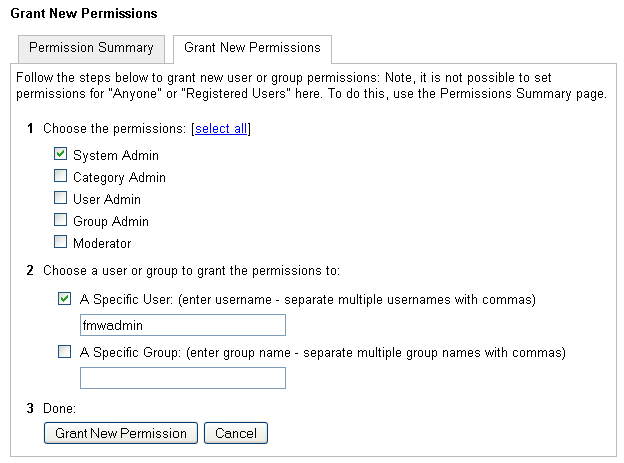
Click Grant New Permissions.
The Grant New Permissions pane displays (see Figure 24-17).
Grant System Admin privileges to the user you created, as shown in Figure 24-18.
Figure 24-18 Grant New Permissions Pane with New User
Click System > System Properties.
The Jive Properties page displays (see Figure 24-19).
Check that the properties marked in red have been added and are set as shown in Figure 24-20.
Log in to the WebLogic Server Administration Console.
For information on logging in to the WebLogic Server Administration Console, see Section 1.12.2, "Oracle WebLogic Server Administration Console."
In the Domain Structure pane (see Figure 24-20), click Security Realms.
The Summary of Security Realms pane displays (see Figure 24-21).
Figure 24-21 Summary of Security Realms pane

In the Name column, click the realm for which you want to change the administrator group name.
The Realm Settings pane displays (see Figure 24-22).
Select the Providers tab and the Authentication sub-tab, and reorder the authentication providers so that the authenticator for the external LDAP appears at the top of the list as shown in the example in Figure 24-23:
Figure 24-23 Providers Tab with Reordered Authentication Providers
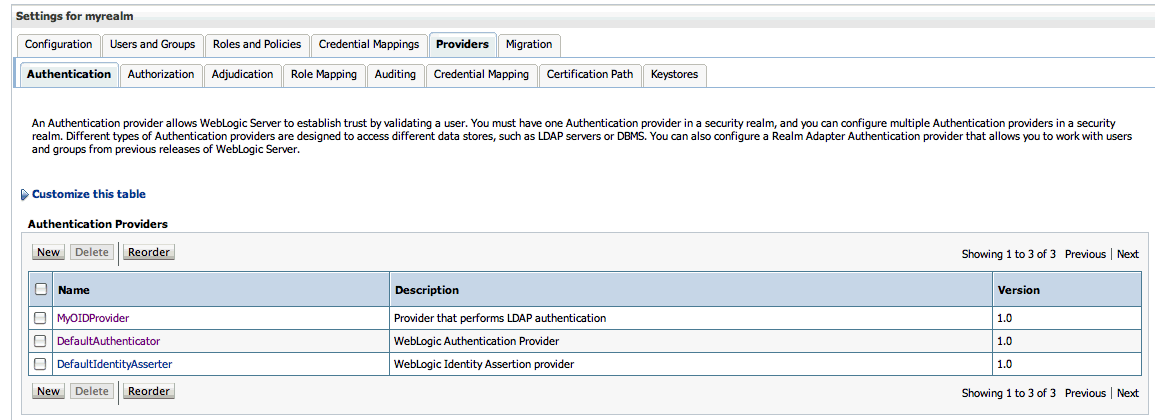
Restart the domain Administration Server and discussions server.
You can change the group name to any other valid enterprise role in your LDAP server that contains users authorized to manage the domain. This lets you delegate the administration of specific domains in your enterprise. You can create various administration groups in the directory and have the corresponding domains be configured to use the appropriate group for defining its administrators.
The following example LDIF file creates an administrative group in Oracle Internet Directory:
dn: cn=wc_domain_Admin,cn=groups,dc=example,dc=com cn: wc_domain_Admin uniquemember: cn=joe.admin,cn=users,dc=example,dc=com owner: cn=orcladmin displayname: WebLogic Administrators Group description: WebLogic Administrators Group objectclass: orclgroup objectclass: groupofuniquenames
Once this group is created, you must update the role definition for the WebLogic Server global Admin role using the WebLogic Server Administration Console.
To update the role definition for the WebLogic Server global Admin role:
Log in to the WebLogic Server Administration Console.
For information on logging into the WebLogic Server Administration Console, see Section 1.12.2, "Oracle WebLogic Server Administration Console."
In the Domain Structure pane (see Figure 24-24), click Security Realms.
The Summary of Security Realms pane displays (see Figure 24-25).
Figure 24-25 Summary of Security Realms pane

In the Name column, click the realm for which you want to change the administrator group name.
The Realm Settings pane displays (see Figure 24-26).
Open the Roles and Policies tab, and then the Realm Roles subtab.
The Realm Roles settings pane displays (see Figure 24-27).
Expand the Global Roles node, and then the Roles node.
Click View Role Conditions for the Admin role.
The Edit Global Role page displays (see Figure 24-28).
By default, the Administrators group in Oracle Internet Directory (or other configured identity store) defines who has the administrator role in WebLogic Server.
Click Add Conditions to add a different group name.
The Edit Global Role - Predicate List page displays (see Figure 24-29).
Figure 24-29 Edit Global Role Page - Predicate List
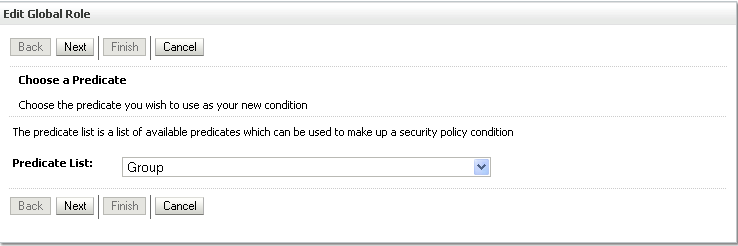
Select Group from the Predicate List list and click Next.
The Edit Global Role - Arguments page displays (see Figure 24-30).
Figure 24-30 Edit Global Role Page - Arguments
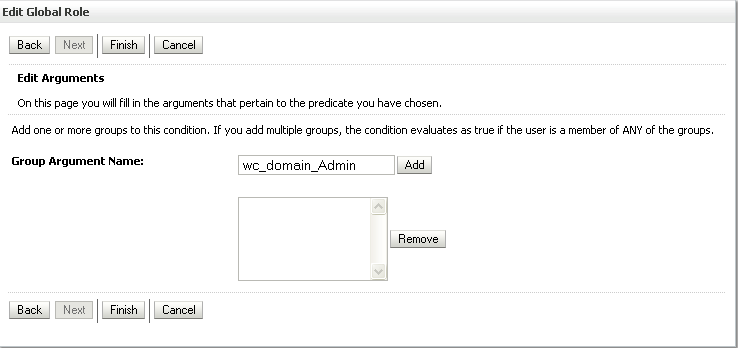
Enter the name for the new administrator group and click Add.
Select the pre-existing administrator group and click Remove to delete it leaving the new one you've selected in its place.
Click Finish to save your changes.
After making this change, any members of the new group specified are authorized to administer WebLogic Server.
WebCenter Spaces only recognizes users in the identity store that is mapped by the first authenticator. Since the WebCenter Spaces Administrator account is initially created only in the embedded LDAP server, if an external LDAP such as Oracle Internet Directory is configured as the primary authenticator for WebCenter Spaces, you must also create a user in that LDAP and grant that user the WebCenter Spaces Administrator role.
You can grant a user the WebCenter Administrator role using Fusion Middleware Control or WLST as shown below in the sections on:
Section 24.6.1, "Granting the WebCenter Spaces Administrator Role Using Fusion Middleware Control"
Section 24.6.2, "Granting the WebCenter Spaces Administrator Role Using WLST"
For more information, see "Granting the Administrator Role to a Non-Default User" in the Oracle Fusion Middleware Installation Guide for Oracle WebCenter.
This section describes how to grant the WebCenter Spaces administrator role to a user account other than the default "weblogic" account.
To grant the WebCenter Spaces Administrator role using Fusion Middleware Control:
Log into Fusion Middleware Control and select the WebLogic domain for WebCenter Spaces.
For information on logging into Fusion Middleware Control, see Section 6, "Starting Enterprise Manager Fusion Middleware Control."
From the WebLogic Domain menu, select Security -> Application Roles.
The Application Roles page displays (see Figure 24-31).
Search for the Administration application role by selecting the Application name for WebCenter Spaces (WLS_Spaces/webcenter), and providing the following internal identifier used by WebCenter Spaces as the Role Name:
s8bba98ff_4cbb_40b8_beee_296c916a23ed#-#Administrator
The search should return s8bba98ff_4cbb_40b8_beee_296c916a23ed#-#Administrator, which is the administrator role identifier.
Click the administrator role name (s8bba98ff_4cbb_40b8_beee_296c916a23ed#-#Administrator) in the Role Name column.
The Edit Application Role page displays (see Figure 24-32).
Click Add User.
The Add User pop-up displays (see Figure 24-33).
Use the Search function to search for the user to assign the Administrator role to.
Use the arrow keys to move the user from the Available Users column to the Selected Users column, and click OK.
On the Edit Application Role page, click OK.
To remove the weblogic role, on the Edit Application Role page under Users, click weblogic and the click Delete.
Restart the WLS_Spaces managed server.
When you login to WebCenter Spaces, the Administration link should appear and you should be able to perform all administrator operations. See also, Section 32.1, "Logging into WebCenter Spaces as an Administrator."
To grant the WebCenter Administrator role using WLST:
Start WLST as described in Section 1.12.3.1, "Running Oracle WebLogic Scripting Tool (WLST) Commands."
Connect to the WebCenter Spaces Administration Server for the target domain with the following command:
connect('user_name','password, 'host_id:port')
Where:
user_name is the name of the user account with which to access the Administration Server (for example, weblogic)
password is the password with which to access the Administration Server
host_id is the host ID of the Administration Server
port is the port number of the Administration Server (for example, 7001).
Grant the WebCenter Spaces administrator application role to the user in Oracle Internet Directory using the grantAppRole command as shown below:
grantAppRole(appStripe="webcenter", appRoleName="s8bba98ff_4cbb_40b8_beee_296c916a23ed#-#Administrator",
principalClass="weblogic.security.principal.WLSUserImpl", principalName="wc_admin")
Where wc_admin is the name of the administrator account to create.
To test the new account, log into WebCenter Spaces using the new account name.
The Administration link should appear, and you should be able to perform all administrator operations. See also, Section 32.1, "Logging into WebCenter Spaces as an Administrator."
After granting the WebCenter Spaces Administrator role to new accounts, remove this role from accounts that no longer need it or should no longer have it using the WLST revokeAppRole command. For example, if WebCenter Spaces was installed with a different administrator user name than "weblogic", the administrator role should be given to that user and should be revoked from the default "weblogic".
revokeAppRole(appStripe="webcenter", appRoleName="s8bba98ff_4cbb_40b8_beee_296c916a23ed#-#Administrator", principalClass="weblogic.security.principal.WLSUserImpl", principalName="weblogic")
Oracle Content Server (OCS) must be configured to use the same identity store LDAP server as Oracle WebCenter Spaces. For more information on configuring the OCS, see Section 11.2.1.2.1, "Configuring the Identity Store," and also "Configuring the Identity Store Service" in the Oracle Fusion Middleware Security Guide.