| Oracle® Enterprise Manager Ops Center Feature Reference Guide 12c Release 1 (12.1.1.0.0) Part Number E27511-04 |
|
|
PDF · Mobi · ePub |
| Oracle® Enterprise Manager Ops Center Feature Reference Guide 12c Release 1 (12.1.1.0.0) Part Number E27511-04 |
|
|
PDF · Mobi · ePub |
The following information is included:
Oracle Enterprise Manager Ops Center supports Ethernet and InfiniBand network protocols. While the Ethernet interconnect is the established and common interconnect, InfiniBand is popular in high-performance computing environments because it maximizes the speed of transactions using the short, multiple connections found in clusters and data centers.
For an Ethernet network, both tagged and untagged VLANs are supported.
For an InfiniBand network, partitions are supported.
Note:
If you use an InfiniBand switch in an Ethernet network, the ports on the switch have Ethernet names.When you use Oracle Enterprise Manager Ops Center to discover a physical switch, all the fabrics that the switch supports are also discovered. One physical fabric supports many fabrics. Each port on an Ethernet switch can support 128 fabrics through its VLAN ID. Each partition on an InfiniBand switch can support 32000 partition keys.
The members of a partition are identified by partition keys or "P-keys," which act like Ethernet's VLAN tags. For example, if a server has two P-Keys, it participates in two different partitions.
Note:
For an Oracle Exalogic server that has Oracle Enterprise Manager Ops Center installed, all physical and logical fabrics are discovered. For an Exalogic server that does not have Oracle Enterprise Manager Ops Center installed but resides in a data center that uses Oracle Enterprise Manager Ops Center, the Exalogic server is discovered as a server and then all of its fabrics are discovered.The following table lists the tasks and the role required to complete the task. Contact your administrator if you do not have the necessary role or privilege to complete a task. See the Oracle Enterprise Manager Ops Center Administration Guide for information about the different roles and the permissions they grant.
Table 7-1 Network Roles and Permissions
| Task | Role |
|---|---|
|
Edit Network Domain |
Network Admin |
|
Edit Network Attributes |
Network Admin |
|
Edit Network Services |
Network Admin |
|
Aggregate Links |
Network Admin |
|
Create IPMP Groups |
Network Admin |
|
Attach Network to Server Pool |
Cloud Admin |
|
Create Network Domain |
Network Admin |
|
Create Network |
Network Admin |
|
Delete Network Domain |
Network Admin |
|
Delete Network |
Network Admin |
|
Manage Fabric |
Network Admin |
|
Delete Fabric |
Network Admin |
|
Assign Network |
Network Admin |
|
Connect Guests |
Network Admin |
|
Discover and Manage the Switches |
Network Admin |
|
Configure Network for Server Deployment |
Server Deployment Admin |
After a network is created, you can perform the following actions, depending on the requirements.
Edit Network Attributes
Edit Network Services
Aggregate Links
Create IPMP Groups
Attach Network to Server Pool
Create Network (manage network)
Delete Network
Assign Network
Connect Guests
Discover and manage the switches
Table 7-2 Location of Network Information in the BUI
| Object | Location |
|---|---|
|
Fabric |
Expand Networks in the Assets pane. Then select Fabrics. |
|
Physical Fabric |
Expand Networks in the Assets pane. Then select Fabrics and then select Network Switches. |
|
Network |
To see all networks, regardless of type, expand Networks in the Assets pane. Then select Network Domains. |
|
Services of a Network |
Network Services tab: time server, WINS, DNS, and NIS. To modify these services, edit the network services. You cannot change the network's IP address or name. |
|
Network Domain |
Expand Networks in the Assets pane. For the Default Network Domain, select first item in the hierarchy |
|
Physical switch |
Expand Assets and expand Network Switches. To see each port, click the Connectivity tab. |
A network domain is a container for managed networks and handles the relationship between the physical fabrics that support the networks and the virtualization hosts or server pools that use the networks. The fabrics provide network resources such as links and IP subnets to the network domain. Within the network domain, networks that have been discovered or specified are available for assignment. These are called public networks. Their network resources have been defined. Another type of network is dynamic, that is, the network is created when it is needed, using an IP address space available to the network domain. Because they exist only for a specific purpose and only within a specific network domain, they are called private networks.
In Oracle Enterprise Manager Ops Center, networks become part of a network domain in the following ways:
An asset that has a network is discovered.
A user creates a network.
A network is created when it is required. This is a dynamic network.
Oracle Enterprise Manager Ops Center operates on more than one layer of the Open Systems Interconnection model. All of the elements at all layers are managed in a network domain. Table 7-3 shows the physical to logical stack.
Table 7-3 Elements of a Network Domain
| Layer | Asset | What Is Managed | Capability |
|---|---|---|---|
|
Layer 3 Network: IP address |
For Ethernet: fabric networks For InfiniBand: non-fabric networks |
IP subnet and mask IP address range VLAN or Partition Services Routing |
The network provides connectivity. |
|
Layer 2 Data links |
For a tagged Ethernet: VLAN For an untagged Ethernet: portID For InfiniBand: partition |
VLAN IDs Partition keys (P-key) |
A virtual host uses the virtual NIC and a virtual switch in a VLAN or partition. |
|
Layer 1 Physical: switches, ports, host bus adapters |
Fabrics |
\ |
\ |
|
/ |
The switch is a managed asset. |
Can create a dynamic private network for each VLAN ID or partition key. |
|
|
/ |
The host of the switch is a managed asset. |
Can create a dynamic private network for each VLAN ID or partition key when you enable the VLAN IDs or partition keys on the switch ports connected to the host. |
|
|
/ |
The switch is discovered or declared during the discovery of another asset but is not managed. |
Cannot create dynamic private networks because the VLAN IDs or partition keys are not available. The networks you create on an unmanaged fabric are static private networks. |
The Oracle Enterprise Manager Ops Center software always has a Default Network Domain and all public networks are members of it. If you have upgraded your product software, the existing managed networks are now in the Default Network Domain. A new public network becomes a member of the default network domain. If you direct the new network to a user-defined network domain, the network is also a member of that network domain. Like the default network domain, a user-defined network domain provides network resources to a server pool or virtualization host.
You create a network domain to support the use of virtualization hosts, server pools, or a virtual datacenter. For example, a virtual datacenter uses server, storage, and network resources in a dynamic way, allocating and releasing resources whenever necessary. The network domain provides the network resources to the virtual datacenter.
When you create a network domain, you can set a limit on the number of networks that can be created in the network domain. Increase the number of networks when accounts in a virtual datacenter are not able to create vnets.
You can change the name and description of the network domain and you can change the number of dynamic networks that are in use simultaneously.
To Edit Attributes of a Network Domain
Expand Libraries in the Navigation pane.
Expand Networks in the Navigation pane.
Select the network domain.
Click Edit Attributes in the Actions pane.
The Details tab is displayed in the center pane. The Name Description, and Number of Networks fields are now editable.
Edit the name or description or increase the number of networks.
Click Save.
In Oracle Enterprise Manager Ops Center, networks are the discovered and managed IP subnets. Oracle Enterprise Manager Ops Center manages network resources for its virtualization hosts.
Note:
A network is defined only within Oracle Enterprise Manager Ops Center. These networks are not the network connections for servers and chassis.Networks are associated with server pools, which contain virtualization hosts, or standalone virtualization hosts. When you assign a network to a server pool, the network is accessible from each virtualization hosts in the pool and every guest of each virtualization host.
You can use networks to do the following:
Manage individual virtualization hosts
Connect virtualization hosts to the Proxy Controller
Allow guests to communicate with each other or with the Internet
Connect remote JMX with the public API
A network depends on the physical network interface card (PNIC) that is available to the host. You can create one network for each physical network interface card. If one host has two PNICs, it is a good practice to create two networks: a management network and a data network. Then place all guests on the data network, keeping them separate from the management network. The management network is dedicated to giving access to internal resources of the data center.
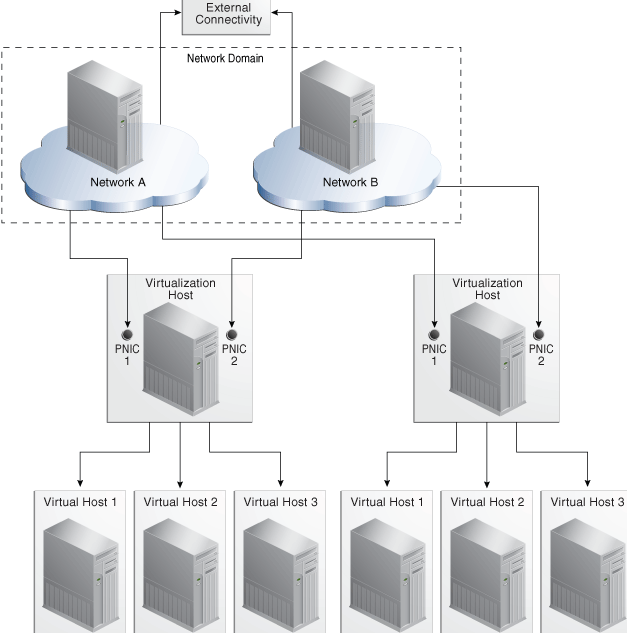
The following configuration shows how two virtualization hosts participate in two networks. The actual network connection is made to the PNICs in the virtualization host. Network A is connected to PNIC 1 of both hosts and Network B is connected to PNIC 2 of the hosts.
A network requires a physical network interface or a link aggregation and the following mandatory specifications:
IP address of the network
Netmask
If you use static IP addressing, the IP address of the management interface
If you use dynamic IP addressing, the range of allowed IP addresses and the gateway address
Oracle Enterprise Manager Ops Center creates virtual networks and provides them to a virtual datacenter. These networks are created from the resources of the network domain as needed. These networks are displayed in the vDC Management section of the Navigation pane.
A virtual network defines a virtual IP subnet that is divided into public external networks and private external networks. You specify the size of the virtual network, which sets the maximum number of IP addresses for a public external network.
The public external network can be shared among the accounts in a virtual datacenter. You can attach virtual servers from different accounts in a single public external network. When you create a virtual server, you specify the number of public external networks to which it can be associated.
You can reserve the IP address in a public external network for an account use only. When you create a virtual server, you can provide the reserved IP address. Otherwise, the virtual server is allocated the IP address from the server poo.l
A server pool must have at least one network. When a server pool has more than one network, all virtualization hosts in the server pool are associated with the same set of networks. When you add a virtualization host to a server pool, the virtualization host has access to all the networks defined for the pool and can be an active member of the pool. This ensures that all virtual hosts have network access, even when you migrate a virtual host from one virtualization host to another one within the pool.
The following figure illustrates an example of network connections to two virtualization hosts in a server pool. This server pool has two virtualization hosts and two network associations.
Figure 7-2 Network Connections for a Server Pool
You specify the networks that support a global zone. The network attached to a global zone also supports its non-global zones. You can attach one or more networks to a global zone using the Attach Networks action.
Although the fabric that supports the network does not change, you can specify the way the network works differently for each type of zone. A network that is assigned as shared on a global zone can be assigned as exclusive on another global zone.
In Shared IP mode, the network interface is used by more than one zone. You define the network interface when you assign the global zone to the network.
In Exclusive IP mode, the network interface is dedicated to the zone. An exclusive network must be declared for the global zone when you assign network to the global zone. Then you configure the IP configuration for the non-global zone.
For a complete description, see Manage Global Zone Networks in Chapter 14.
T he Oracle VM Server Control Domain's network support is specified when the Oracle VM Server software is installed to provide networking facilities for the logical domains. For each network connection, a virtual switch is created.
For a complete description of networks for Oracle VM Server for SPARC, see Attach Networks in Chapter 15.
For a complete description of networks for Oracle VM Server for x86, see Manage Networks in Chapter 16.
Each virtual datacenter uses server, storage, and network resources in a dynamic way, allocating and releasing resources when necessary.
The virtual datacenter inherits its network resources from the network domain that supports the server pool. These networks form the public external networks for the virtual datacenter. These networks can then be assigned to the accounts in the virtual datacenter. When the user of an account create a private vNet, either a dynamic private network is created or the static private network is made available for use in that account.
For a complete description of networks for virtual datacenters, see vNets Creation and Network Setup in Chapter 18.
Bandwidth management for data links is available for Oracle Solaris 11 operating system. A data link is a physical NIC, an aggregated link, or a virtual NIC. You define the flow on the data link, prioritizing the network traffic on the link and setting the maximum bandwidth limit.
When a new data link is created, its default bandwidth flow is created by Oracle Solaris 11 operating system. You cannot remove this flow. The flow is removed only when the physical link is removed. However, you can create new flows for the data link. The flow for a network interface is specified by its local and the remote IP address, Internet Protocol, and the type of service.
To create a new flow for a data link, specify a name for the flow and the physical network interface. Then set the new bandwidth properties:
Priority – Set the priority of the network traffic on the link as high, medium or low.
Bandwidth Limit – Enable the bandwidth limit to allocate guaranteed bandwidth to the specified link. Enter the maximum value for bandwidth limit in Kbps, Mbps or Gbps
Set attributes for the data flow to identify its network traffic:
Local and Remote IP - The source and destination IP address
Transport – The Internet Protocol used such as TCP, UDP. SCTP, ICMP.
Ports – The source and destination ports for TCP, UDP, and SCTP.
DS Field – The type of service field in the IP packets' header.
To View the Flows for a Data Link
Expand Assets in the Navigation pane.
Select an Oracle Solaris 11 operating system.
Click the Networks tab in the center pane.
Click the Bandwidth Management subtab in the center pane.
To modify a flow, click the Modify icon. To create a new link, click the Add icon.
Using IP Multipathing (IPMP), two or more physical network interface cards (NIC) form a group that use one IP address. If one NIC fails, the other NIC in the group maintains network access.
When you create a network, you define its network interface. The interface can be a physical network interface card (NIC) or, in the case of an Oracle Solaris OS asset, it can be an IPMP group or link aggregation You can implement both methods on the same network because they work at different layers of the network stack. See the Oracle Solaris 11 documentation at http://docs.oracle.com/cd/E23824_01/index.html and Oracle Solaris 10 documentation at http://www.oracle.com/technetwork/documentation/solaris-10-192992.html for information about these services and how to implement IPMP.
Note:
IPMP groups are supported only for IPv4 protocol.IPMP provides increased reliability, availability, and network performance for systems with multiple physical interfaces. It provides physical interface failure detection and transparent network access failover.
Occasionally, a physical interface or the networking hardware attached to that interface might fail or require maintenance. By using IPMP, you can configure one or more physical interfaces into an IPMP group. After configuring the IPMP group, the system monitors the interfaces in the IPMP group for failure. If an interface in the group fails or is removed for maintenance, IPMP migrates, or fails over, the failed interface's IP addresses. The failover feature of IPMP preserves connectivity and prevents disruption of any existing connections.
The association between an IPMP group and a network must be unique; an IPMP group can be associated with only one network and a network can be associated with only one IPMP group or individual NICs.
In an IPMP group, you define whether each interface is a failover or a standby one. The actions of each type differ if the current network interface fails:
Network access changes from the failed interface to the failover interface in the IPMP group and uses the failover interface data address. You must provide the data address for an interface that is defined as failover.
Network access changes from the failed interface to the standby interface in the IPMP group but does not change its data address. The data address of the failed interface migrates to the standby interface.
Link-based failure detection in an IPMP group is always enabled if your interface supports this type of failure detection. You can also set for probe-based failure detection by providing a test address for each interface in the group.
You can create a single IPMP group while provisioning an operating system. If you create IPMP groups manually, Oracle Enterprise Manager Ops Center identifies and displays the groups on the UI.
In an aggregated link, two or more NICs form a group and all members of the link aggregation provide network access at the same time. In addition to the high availability and load balancing that an IPMP group provides, an aggregated link can also provide increased throughput if the network ports are also aggregated.
When you create a network, you define its network interface. The interface can be a physical network interface card (NIC) or, in the case of an Oracle Solaris OS asset, it can be an IPMP group or link aggregation You can implement both methods on the same network because they work at different layers of the network stack.See the Oracle Solaris 11 documentation at http://docs.oracle.com/cd/E23824_01/index.html and Oracle Solaris 10 documentation at http://www.oracle.com/technetwork/documentation/solaris-10-192992.html for information about these services and how to implement link aggregation.
Link aggregation is a standard defined in IEEE802.3ad. An aggregated link consists of several interfaces on a system configured as a single, logical unit. Link aggregation increases the speed and high availability of a connection between a server and a switch. The most common protocol used to manage link aggregation is LACP (Linked Aggregation Control Protocol).
You can create one link aggregation while provisioning an OS. You can configure the interfaces together as a logical unit and define the link aggregation information if the following conditions are met:
All the members of the aggregated link are connected to the same switch.
The members of the aggregated link are of the same type. For example, NICs with the e1000g interface cannot be mixed with NICs that use the bge interface.
For Oracle Solaris OS, the required driver is GLDv3.
When interfaces have been aggregated, they are treated as a single network interface. Oracle Enterprise Manager Ops Center displays the link aggregation in the list of available NICs as if it were an individual interface. When you assign a network with a link aggregation to an Oracle VM Server, logical domain, global zone, or a non-global zone, select the link aggregation from the NIC list. You can view the link aggregation details on the Oracle VM Server's or global zone's Network tab.
The characteristics of a network are displayed in its Network Details tab. You can edit the network name and description, MTU size, assignable IP range, and default gateway. The network IP address, netmask, and its network type cannot be changed. You can also enable and disable DHCP service, VLAN tagging, and manage the static routes of the network. To change the MTU size, see the instructions in Maximum Transmission Unit (MTU).
Some environments have a mix of IPv4 and IPv6. Oracle Enterprise Manager Ops Center is "IPv6-aware." If an asset has an IPv6 network interface, Oracle Enterprise Manager Ops Center can read it and displays its information, but it cannot provision an IPv6 network or use IPv6 networks to discover, monitor, or provision assets.
A virtual host uses the network assigned to it according to the host's routing mode. You specify a virtual host's routing mode during its initial configuration if you do not accept the default mode, Automatic Routing. Oracle Enterprise Manager Ops Center supports the following routing modes:
Automatic Routing – This is the default routing mode. Applying the static routes depends on the following conditions:
If your site defined a default gateway or static route or retrieved one from the DHCP server, this route is used and dynamic routing is disabled.
If no default gateway or static route is available, dynamic routing is enabled.
Dynamic Routing Off – The virtual host uses the default gateway and any static routes configured for the network. The default gateway is retrieved from the DHCP server.
Dynamic Routing On – The virtual host uses routes provided by the dynamic routing service. The default gateway and any static routes configured for the network are ignored.
Static routes specify the route for external access. Although you define a default gateway for a network, it might not reach a particular subnet. In this case, you must also provide a static route for the subnet.
When you create a network, you can specify the static route. To add static routes after the network has been created, use the following procedure.
To Add a Static Route for the Network
Click Managed Networks in the Navigation pane.
Select a network from the list of networks.
Click Edit Network Attributes in the Actions pane.
Click the Add icon in the Static Routes table. A row is added to the table.
Type the values for destination IP, netmask, and gateway.
Click Finish.
You can delete a static route and change the order of the routes using the icons in the Static Routes table.
When you create a network, you specify how its IP address is assigned:
Static IP: A specific IP address is assigned to the network
Automatic: An available IP address is assigned to the network.
The default size for the network's Maximum Transmission Unit (MTU) is 1500 bytes. If your network interface card is one of the following types, you can change the size of the MTU to a size between 576 and 9216 bytes. However, to assign the network to a logical domain, the minimum MTU size is 1500 bytes.
nxge
ixgbe
hxge
e1000g
ce
bge
ipge
When you specify a size greater than 1500 bytes, Oracle Enterprise Manager Ops Center modifies the network interface card's MTU size. For other types of network interface cards, the MTU is changed when the card's driver firmware is updated to support the new MTU size. However, to change the MTU value for an IPMP group, you must edit the MTU value manually.
Note:
When you provision an operating system, the MTU size resets to the default value. You must change the MTU again after you provision the system.Oracle Enterprise Manager Ops Center collects information every five minutes on every managed asset and displays the last hour of data on the asset. To see utilization data for a network over longer periods of time, up to six months, create a Network Utilization chart, which includes operating system, operating system for a virtual machine, virtual host, and server pool. You can also create a network utilization chart for an OS group or host group.
Connectivity is the network interface of the system. You can view information about a hardware asset's Network Interface Card (NIC) on the Connectivity tab of the asset's dashboard, including name, connection status, MAC address, and the corresponding IP address.
For switch hardware, the Connectivity tab shows information about each port.
For an Oracle Solaris OS, the Connectivity tab includes IPMP groups and aggregated links.
The IPMP Groups subtab shows the group's name, its assigned network, and the type of failure detection, either link-based, probe-based, or both. For each IPMP group, the details include the state of the connection for each NIC, whether it is in standby mode or failover mode, and the IP address the NIC supports.
The Link Aggregation sub tab shows the aggregation's name, its MAC address, and its attributes. For each aggregated link, shows the state of the connection for each NIC, whether it is in standby mode or failover move, and the IP address the NIC supports.
Oracle Enterprise Manager Ops Center can manage Sun Ethernet 10GbE Fabric switches and Sun Datacenter InfiniBand switches. These switches reside in the system or blade system and provide the switch fabric.
The InfiniBand Gateway switch can expose the ports of a server that resides on an InfiniBand partition to an Ethernet network. To create an Ethernet on InfiniBand (EoIB) interface on the switch, you associate the switch's external port (eport) with the InfiniBand partition where the server resides, creating a virtual NIC (vNIC). The server's ports are displayed on the Switch Connectivity tab in the center pane.
For more information about these switches, see Switch Details or see Related Resources for Networks for links to the switch documentation.
The Network Interface Card (NIC) is the physical connection to a network. To see the NICs for a server, select the server and then click the Connectivity tab. The Server Processor Connectivity table lists all of the NICs.
Oracle Enterprise Manager Ops Center can manage Sun Ethernet 10GbE Fabric switches and Sun Datacenter InfiniBand switches. These switches reside in the system or blade system and provide the switch fabric.
For the Ethernet switches, both tagged and untagged VLANs are supported.
If you use an InfiniBand switch in an Ethernet network, the ports on the switch have Ethernet names.
For more information about these switches, see the product documentation:
For the Sun Ethernet 10GbE Fabric switch, see http://docs.oracle.com/cd/E19934-01/index.html
For Sun Datacenter InfiniBand switch, see http://docs.oracle.com/cd/E19654-01/index.html
Oracle Enterprise Manager Ops Center provides default profiles for the following operations:
Deploy a network – Create a network.
Monitor a network – Monitor for changes in membership and attributes, and any problems in the physical fabric, such as a change in port or link status.
Monitor Network hardware – Reports Cisco switch's connection to assets on the Switch Connectivity tab.
Discover a switch – Use a discovery profile with Cisco iOS credentials.
This section describes the requirements for the networks that Oracle Enterprise Manager Ops Center uses. This section does not discuss the networks that support virtual hosts and server pools.
You can implement Oracle Enterprise Manager Ops Center's network connections using any combination of VLANs and switches. However, each network, whether management, provisioning, or data, must be assigned to separate VLANs.
Use these guidelines to configure a network switch for a system running the Oracle Enterprise Manager Ops Center software.
Use an Virtual LAN (VLAN)-capable switch.
Discover and manage the switch.
Create a separate VLAN for Oracle Enterprise Manager Ops Center management and provisioning networks.
For Ethernet connectivity:
The management network must be a 10/100 connection.
The provisioning and data networks must be at least a 10/100/1000 (1 GB) connection.
Separate networks provide the highest security and the lowest number of points of failure.
Additional NICs are needed to support this configuration.
Figure 7-3 Separate Management, Provisioning, and Data Networks
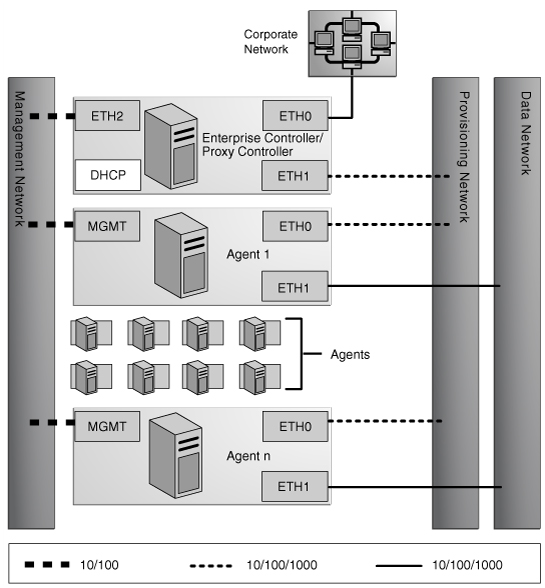
A configuration with separate management, provisioning, and data networks has these requirements:
Enterprise Controller/Proxy Controller
ETH0 connects the Enterprise Controller/Proxy Controller to the corporate network for external access. Configure the ETH0 IP address, netmask, and gateway to meet corporate connectivity requirements.
ETH1 connects the Enterprise Controller/Proxy Controller to the provisioning network and must be on the same network as the ETH0 connections of the Agent Controllers. Only the Enterprise Controller/Proxy Controller and the Agent Controllers must reside on the provisioning network. ETH1 must be a 1 Gb NIC interface.
ETH2 connects the Enterprise Controller/Proxy Controller to the management network and must be on the same network as the management port connections of the Agent Controllers. Configure the ETH2 IP address, netmask, and gateway to enable connectivity to the Agent Controllers' management port IP addresses. ETH2 must be a 100 Mb NIC interface.
The DHCP service allocates IP addresses to the Agent Controllers for provisioning operating systems.
Agent Controllers
Each Agent Controller's management port connects the Agent Controller to the management network and must be on the same network as the ETH2 connection of the Enterprise Controller/Proxy Controller. The management port must be a 100 Mb connection.
ETH0 connects the Agent Controller to the provisioning network and must be on the same network as the ETH1 connection of the Enterprise Controller/Proxy Controller. ETH0 must be a 1 GB connection.
ETH1 connects the Agent Controller to the data network through the switch to provide corporate network access to the Agent Controller. ETH1 must be a 1 GB connection.
Reduced system and network security.
No additional NIC is needed on the Enterprise Controller or Proxy Controller.
Figure 7-4 Combined Management and Provisioning Network and a Separate Data Network
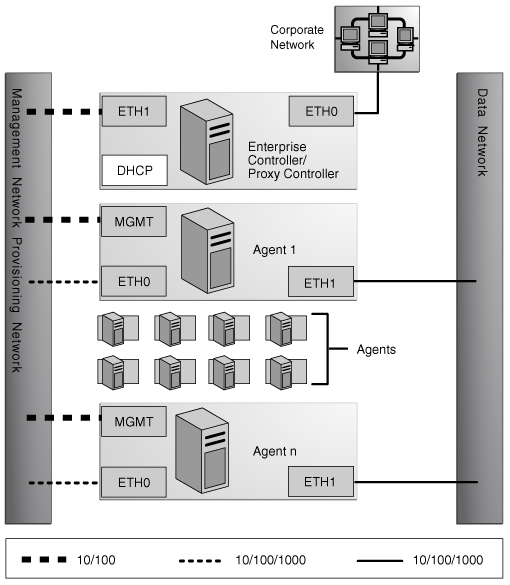
Enterprise Controller/Proxy Controller
ETH0 connects the Enterprise Controller/Proxy Controller to the corporate network to provide external access. Configure the ETH0 IP address, netmask, and gateway to meet corporate connectivity requirements.
ETH1 connects the Enterprise Controller/Proxy Controller to the management and provisioning network and must be on the same network as the MGMT and ETH0 connections of the Agent Controllers. Only the Enterprise Controller/Proxy Controller and the Agent Controllers must reside on the management and provisioning network. The ETH1 IP address, netmask, and gateway must be configured to enable connectivity to the Agent Controller's management port IP addresses. ETH1 must be a 1 Gb NIC interface.
The DHCP service allocates IP addresses to the Agent Controllers for provisioning operating systems.
Agent Controllers
Each Agent Controller's management port connects the Agent Controller to the management and provisioning network and must be on the same network as the ETH1 connection of the Enterprise Controller/Proxy Controller. The management port must be a 100 Mb connection.
ETH0 connects the Agent Controller to the management and provisioning network and must be on the same network as the ETH1 connection of the Enterprise Controller/Proxy Controller. ETH0 must be a 1 GB connection.
ETH1 connects the Agent Controller to the data network through the switch to provide corporate network access to the Agent Controller. ETH1 must be a 1-GB connection.
Figure 7-5 Combined Provisioning and Data Network and a Separate Management Network
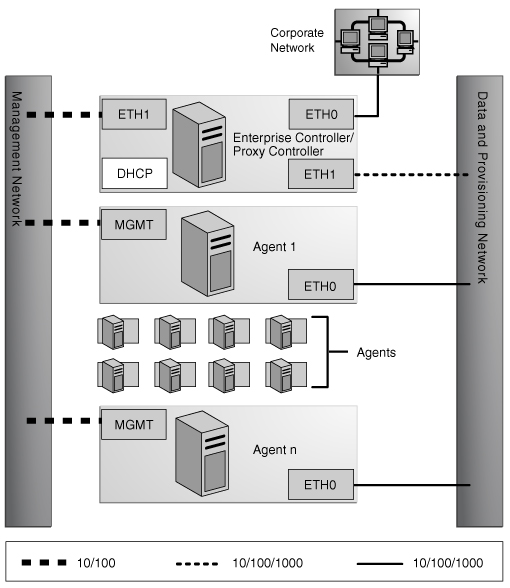
Enterprise Controller/Proxy Controller
ETH0 connects the Enterprise Controller/Proxy Controller to the corporate network to provide external access. Configure the ETH0 IP address, netmask, and gateway to meet corporate connectivity requirements.
ETH1 connects the Enterprise Controller/Proxy Controller to the provisioning and data network and must be on the same network as the ETH0 connections of the Agent Controllers. Only the Enterprise Controller/Proxy Controller and the Agent Controllers must reside on the data and provisioning network. ETH1 must be a 1 Gb NIC interface.
ETH2 connects the Enterprise Controller/Proxy Controller to the management network and must be on the same network as the management port connections of the Agent Controllers. Configure the ETH2 IP address, netmask, and gateway to enable connectivity to the Agent Controller's management port IP addresses. ETH2 must be a 100 Mb NIC interface.
The DHCP service allocates IP addresses to the Agent Controllers for provisioning operating systems.
Agent Controllers
The management port connects the Agent Controller to the management network and must be on the same network as the ETH2 connection of the Enterprise Controller/Proxy Controller. The management port must be a 100 Mb connection.
ETH0 connects the Agent Controller to the data and provisioning network to provide corporate network access to the Agent Controller. ETH0 connection must be on the same network as the ETH1 connection of the Enterprise Controller/Proxy Controller. ETH0 must be a 1 GB connection.
Least secure system and network
No additional NIC is needed for the Enterprise Controller/Proxy Controller.
Figure 7-6 Combined Provisioning, Data, and Management Network
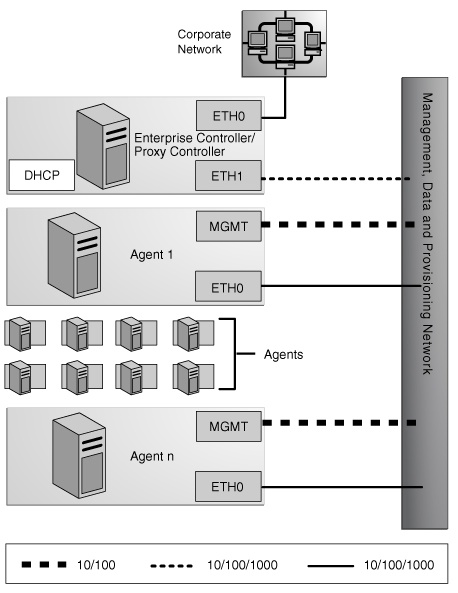
Enterprise Controller/Proxy Controller
ETH0 connects the Enterprise Controller/Proxy Controller to the corporate network to provide external access. Configure the ETH0 IP address, netmask, and gateway to meet corporate connectivity requirements.
ETH1 connects the Enterprise Controller/Proxy Controller to the combined management, provisioning, and data network and must be on the same network as the MGMT and ETH0 connections of the Agent Controllers. Only the Enterprise Controller/Proxy Controller and the Agent Controllers must reside on the combined network. ETH1 must be a 1 GB NIC interface.
The DHCP service allocates IP addresses to the Agent Controllers for provisioning operating systems.
Agent Controllers
Each Agent Controller's management port connects the Agent Controller to the management, provisioning, and data network and must be on the same network as the ETH1 connection of the Enterprise Controller/Proxy Controller. The management port must be a 100 MB connection.
ETH0 connects the Agent Controller to the management, provisioning, and data network, and must be on the same network as the ETH1 connection of the Enterprise Controller/Proxy Controller. ETH0 also connects the Agent Controller to the data network through the switch to provide external corporate network access to the Agent Controller. ETH0 must be a 1 GB connection.
The Enterprise Controller must reach some external sites. If you have explicit firewall rules enabled to allow access to these services from your Enterprise Controller, you must update these rules to allow access to the following addresses:
Table 7-4 IP Address and Port Requirements
| Site | IP Address | Port | Purpose |
|---|---|---|---|
|
|
- |
Port 80 and Port 443 |
Updates to OCDoctor utility Access to Oracle Solaris Cluster profiles and scripts. |
|
|
192.18.110.9 |
Port 443 |
Access to Oracle Knowledge Base for OS updates |
|
|
192.18.110.10 |
Port 443 |
Product registration |
|
|
192.18.110.11 |
Port 443 |
Product registration |
|
|
141.146.54.16 |
Port 443 |
My Oracle Support |
|
|
96.17.111.33 and 96.17.111.49 |
Port 80 |
- |
This section lists the ports and protocols used by Oracle Enterprise Manager Ops Center.
The Enterprise Controller's default port is 443. If port 443 is in use, the Enterprise Controller uses Port 11165. The following table describes the required ports and their protocols.
Table 7-5 Required Ports and Protocols
| Communication Direction | Protocol and Port | Purpose |
|---|---|---|
|
Enterprise Controller |
Port 8005 |
Enterprise Controller in Disconnected mode |
|
Enterprise Controller |
Port 443, then Port 11165 |
Enterprise Controller in Connected mode |
|
OCDoctor to |
HTTPS, TCP: Port 443 |
To acquire updates. |
|
Browser to Enterprise Controller |
HTTP, TCP: Port 80 |
Redirects to port 9443 |
|
Browser to Enterprise Controller |
HTTPS, TCP: Port 9443 |
Web interface |
|
Enterprise Controller to Database |
Port 11176 |
Oracle Listener port for local database |
|
Enterprise Controller to Proxy Controller |
SSH, TCP: Port 22 ICMP ping: Type 8 Code 0 (echo request |
Enterprise Controller installs or upgrades a Proxy Controller through the UI. |
|
Proxy Controllers to Enterprise Controller |
HTTP: Port 8004 HTTPS, TCP: Port 443 ICMP ping: Type 0 Code 0 (echo reply) |
WAN boot traffic Proxy Controller pushes data about assets to Enterprise Controller. Proxy Controller pulls data for jobs, updates, Agent Controllers, and OS images from the Enterprise Controller. Proxy Controllers use ICMP ping during upgrades. |
|
Proxy Controller to Targets |
FTPFoot 1 , TCP: Port 21 SSH, TCP: Port 22 TelnetFoot 2 , TCP: Port 23 DHCP: Port 67 SNMP, UDP: Port 161 IPMI, TCP+UDP: Port 623 Service Tags, TCP: Port 6481 ICMP ping: Type 8 Code 0 (echo request) |
Proxy Controller discovers manages, and monitors assets Proxy Controller performs bare-metal provisioning DHCP is used for OS provisioning. |
|
Target to Proxy Controller |
DHCP: Port 68 SNMP, UDP: Port 162 ICMP ping: Type 0 (echo reply) |
Asset reports status on update operation. Proxy Controller receives ICMP ping Type 3 (destination unreachable) for failed connection. |
|
Agent Controller to Proxy Controller |
HTTPS, TCP: Port 21165 |
Agent Controllers push asset data to Proxy Controller. Agent Controllers pull data for jobs. |
|
Agent Controller to Proxy Controller |
HTTPS, TCP: Port 8002 |
Agent Controllers pull updates from Proxy Controller. |
|
Agent Controller on Oracle Solaris OS and hardware to Proxy Controller |
SNMP: Port 1162, then ports 1100 through 1200 |
For monitoring, Agent Controller sends trap notifications and fault management (FMA) |
|
Proxy Controller to OS Host |
SSH, TCP: Port 22 TelnetFootref 2, TCP: Port 23 TCP: Port 6481 (discovery, monitoring by service tags) DHCP, UDP: Ports 67, 68 ICMP, Type 0 Code 0 (echo reply |
Proxy Controller discovers, manages, and monitors asset. Proxy Controller performs bare-metal OS provisioning |
|
OS Host to Proxy Controller |
HTTP, TCP: Port 8004 Oracle Solaris 11 Automated Installer: Port 5555 |
OS Host reports status of OS provisioning and status of Agent Controller installation. OS Host downloads Agent Controller archive file. The Automated Installer Web Server for Oracle Solaris 11 opens Port 5555 to accept requests from the OS Hosts during Oracle Solaris 11 provisioning. For provisioning handled by DHCP, the open port is on the Proxy Controller. For provisioning handled by WAN boot, the open port is on the Enterprise Controller or a Proxy Controller. |
|
OS Host to Proxy Controller |
DHCP, UDP: Ports 67, 68 TFTP, UDP: Port 69 TCP+UDP: Port 37 ICMP ping, Type 8 Code 0 (echo request |
OS Host responds to Proxy Controller inquiries during bare-metal OS provisioning |
|
Java client to public APIs |
Transport Layer Security (TLS): Port 11172 |
JMX access from clients |
|
WMI client to Agent Controller |
Port 11162 |
WMI client resides on the Proxy Controller and communicates with the WMI server on the Agent Controller. The Proxy Controller uses the DCOM protocol to monitor a Windows system. The Proxy Controller opens a TCP connection to the Windows DCOM registry port, TCP 135, which provides a lookup service to the WMI scripting DCOM object. The Proxy Controller connects to the DCOM object. The port number for this connection is allocated by the Windows system. |
|
Proxy Controller to NFS server |
Use an NFS server that is on the same side of the firewall as the Proxy Controller. Refer to your OS documentation to set up the NFS server. |
Proxy Controller pulls provisioning images from NAS Library |
|
Global Zones or Oracle VM Servers to NFS server |
Use an NFS server that is on the same side of the firewall as the Proxy Controller. Refer to your OS documentation to set up the NFS server. |
Global Zones and Oracle VM Servers push their metadata and virtual host images to NAS Library |
|
Proxy Controller to Service Processors |
SSH, TCP: Port 22 TelnetFootref 2, TCP: Port 23 IPMI, TCP, UDP: Port 623 TCP: Port 6481 (discovery by service tags) |
Proxy Controller discovers, manages, and monitors asset. Proxy Controller performs bare-metal OS provisioning and firmware provisioning. |
|
Proxy Controller to Service Processors |
SNMP, UDP: Port 161 TCP: Port 6481 by service tags |
Proxy Controller sends inquiries to service processors. |
|
Service Processors to Proxy Controller |
FTPFootref 1, TCP: Port 21 TFTP, UDP: Port 69 |
Service processors report status of firmware provisioning. |
|
Service Processors to Proxy Controller |
SNMP, UDP: Port 162 |
Service processors report status. |
Footnote 1 The FTP protocol is used only by servers with the ALOM service processor or by SPARC Enterprise M-Series servers.
Footnote 2 The telnet protocol is used only by servers with the ALOM service processor.
For instructions in performing actions or to learn more about the role of this feature, go to one of the following resources.
For the Sun Ethernet 10GbE Fabric switch, see http://docs.oracle.com/cd/E19934-01/index.html
For Sun Datacenter InfiniBand switch and gateway, see http://docs.oracle.com/cd/E19654-01/index.html