As a debianized Penguin, some time ago I reviewed Secure-K OS, a commercial Linux-based live operating system meant to be run from a USB key and “developed with security in mind”, according to its developers.
In the review I praised its innovative overall system architecture:
At the end of the day, Secure-K OS is a live operating system which saves my data encrypted on the key and it is capable of system and kernel update. I also appreciate how a kernel update improves the overall security of a live system (specially while connected to the Internet) in the long run.
In fact, none of the existing live operating systems provide a kernel update feature: the kernel and the initrd are the only components that a live operating system cannot update, because they lay outside of the data persistence partition (if any) and usually the system partition is ISO9660-formatted. This will soon lead to an outdated operating system, particularly unsafe if used as a desktop-replacement or for security-critical activities.
Good news is that the upstream developers have in the meanwhile open-sourced the liveng (live next generation) whitepaper, the architectural technology upon which Secure-K OS insists and a Community edition of the operating system itself on GitHub, named Open Secure-K OS.

As stated in the project’s home page on GitHub:
Open Secure-K OS is an operating system booting from a USB key in which you can safely create and store your personal and private data. It is an advanced Debian Stretch Linux-based live USB operating system built for security and ease of use: user and system data are saved encrypted within the USB key (AES 512bit), so the system can be used as a clean and safe environment for your on-line security-critical activities. Moreover Secure-K does not rely on the PC hard drive and, being a Linux derivative, it’s immune to most viruses and it’s spyware / adware / backdoor free.
Open Secure-K OS features a unique partitioning scheme, which allows complete system and kernel update. GRUB is the bootloader for both BIOS and UEFI; the Linux Foundation’s preloader assures the Secure Boot compliance.
Unique system features are:
- native encrypted persistence;
- kernel update (on a standard live ISO 9660 filesystem!);
- UEFI, with UEFI Secure Boot compatibility, with a real efi partition;
user creation wizard upon the first boot. Live operating systems use to have the “live” user already created, while Open Secure-K OS pops up the Initial Setup interface in order to create one, together with language, keyboard and time zone.
How to build the initial ISO image
The Open Secure-K OS ISO image is built using the standard Debian live-build framework, project’s home page contains all the instructions on how to build the system by your own. A 32 bit image will be built (the resulting .iso file).
How to deploy the initial ISO image
The Open Secure-K OS Deployer tool is used to write the Open Secure-K OS initial system image onto a USB key:
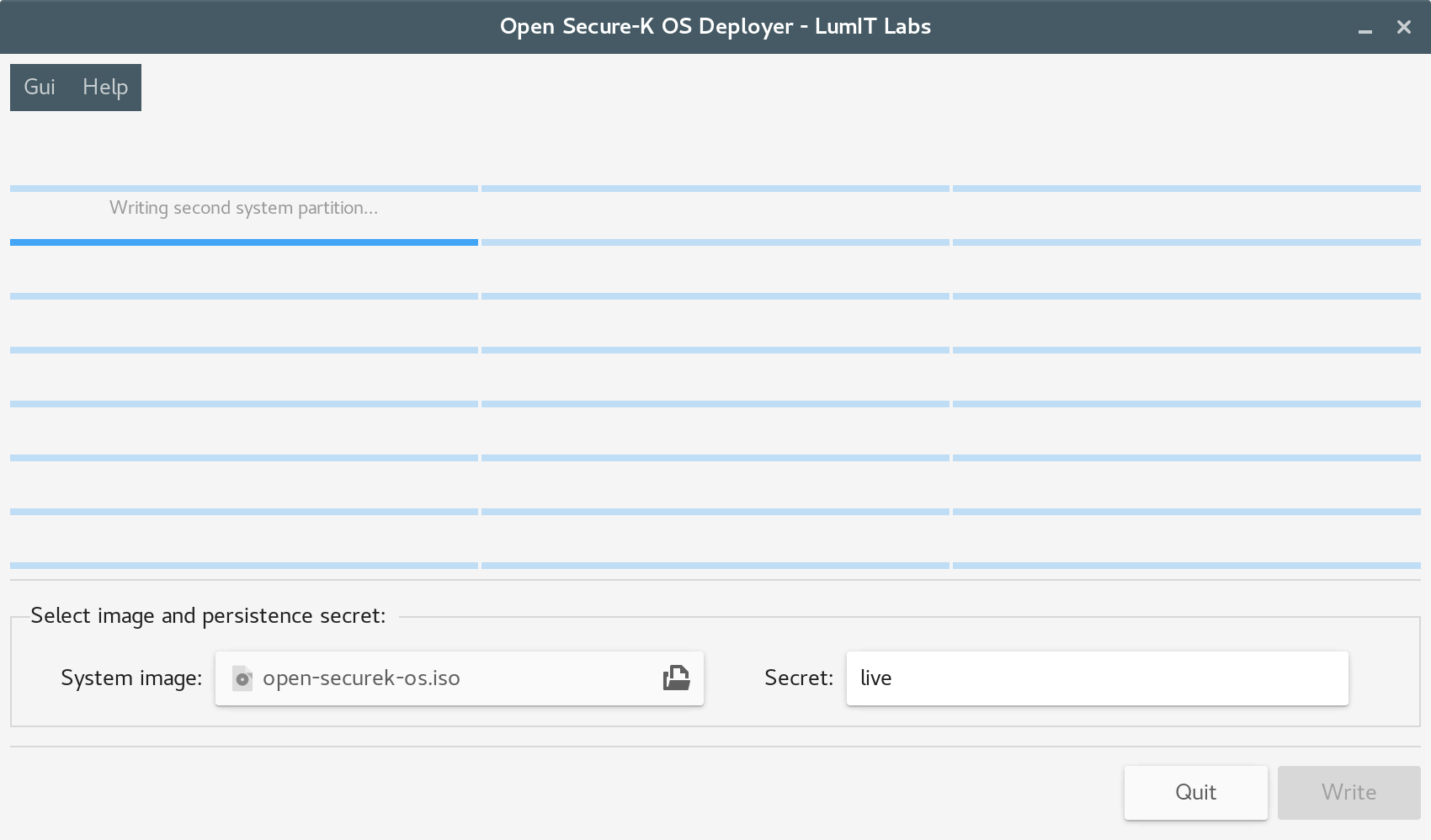
Open Secure-K OS Deployer is the deployment system for writing the initial Open Secure-K OS ISO image onto a USB key – it will create the liveng partitioning scheme: run the Deployer, select the image you have built (or downloaded) and type in a passphrase of your choice for LUKS-encrypting the data persistence partition (remember: Open Secure-K OS features native encrypted persistence), then click on Write. Deployer will write the Open Secure-K OS ISO image onto all the plugged-in (and listed) USB devices, thus creating the complete Open Secure-K OS operating system.
The Deployer tool has been open-sourced as well, so you can contribute to its codebase on GitHub.
