Swatchdog (the “Simple WATCH DOG”) is a simple Perl script for monitoring active log files on Unix-like systems such as Linux. It watches your logs based on regular expressions that you can define in a configuration file. You can run it from the command line or in the background, detached from any terminal using the daemon mode option.
Note that the program was originally called swatch (the “Simple Watcher”) but a request by the old Swiss watch company for a name change saw the developer change its name to swatchdog.
Read Also: 4 Good Open Source Log Monitoring and Management Tools for Linux
Importantly, swatchdog has grown from a script for watching logs produced by Unix’s syslog facility, and it can monitor just about any kind of logs.
How to Install Swatch in Linux
The package swatchdog is available to install from the official repositories of mainstream Linux distributions as a package “swatch” via a package manager as shown.
$ sudo apt install swatch [On Ubuntu/Debian] $ sudo yum install epel-release && sudo yum install swatch [On RHEL/CentOS] $ sudo dnf install swatch [On Fedora 22+]
To install most latest version of swatchdog, you need to compile it from source using following commands in any Linux distribution.
$ git clone https://github.com/ToddAtkins/swatchdog.git $ cd swatchdog/ $ perl Makefile.PL $ make $ sudo make install $ sudo make realclean
Once you have installed the swatch, you need to create its configuration file (default location is /home/$USER/.swatchdogrc or .swatchrc), to determine what types of expression patterns to look for and what type of action(s) should be taken when a pattern is matched.
$ touch /home/tecmint/.swatchdogrc OR $ touch /home/tecmint/.swatchrc
Add your regular expression in this file and each line should contain a keyword and value (sometimes optional), separated by a space or an equal (=) sign. You need to specify a pattern and an action(s) to be taken when a pattern is matched.
We will use a simple configuration file, you can find more options in the swatchdog man page, for instance.
watchfor /sudo/ echo red mail=admin@tecmint.com, subject="Sudo Command"
Here, our regular expression is a literal string – “sudo”, means any time the string sudo appeared in the log file, would be printed to the terminal in red text and mail specify the action to be taken, which is to echo the matched pattern on the terminal and send an e-mail to the specified address, receptively.
After you have configured it, swatchdog reads the /var/log/syslog log file by default, if this file is not present, it reads /var/log/messages.
$ swatch [On RHEL/CentOS & Fedora] $ swatchdog [On Ubuntu/Debian]
You can specify a different configuration file using the -c flag as shown in the following example.
First create a swatch configuration directory and a file.
$ mkdir swatch $ touch swatch/secure.conf
Next, add the following configuration in the file to monitor failed login attempts, failed SSH login attempts, successful SSH logins from the /var/log/secure log file.
watchfor /FAILED/ echo red mail=admin@tecmint.com, subject="Failed Login Attempt" watchfor /ROOT LOGIN/ echo red mail=admin@tecmint.com, subject="Successful Root Login" watchfor /ssh.*: Failed password/ echo red mail=admin@tecmint.com, subject="Failed SSH Login Attempt" watchfor /ssh.*: session opened for user root/ echo red mail=admin@tecmint.com, subject="Successful SSH Root Login"
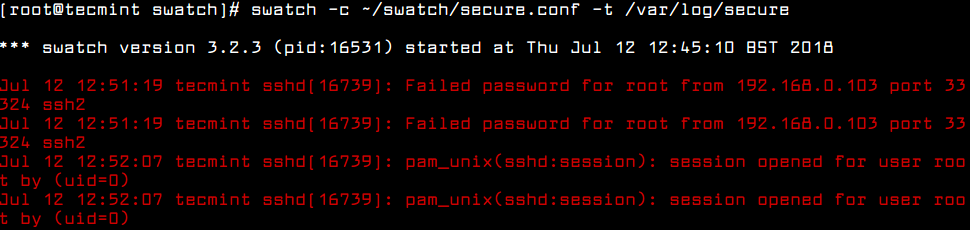
Now run the Swatch by specifying the configuration file using the -c and log file using -t flag as shown.
$ swatchdog -c ~/swatch/secure.conf -t /var/log/secure
To run it in the background, use the --daemon flag; in this mode, it is detached from any terminal.
$ swatchdog ~/swatch/secure.conf -t /var/log/secure --daemon
Now to test the swatch configuration, try to login into server from the different terminal, you see the following output printed to the terminal where Swatchdog is running.
*** swatch version 3.2.3 (pid:16531) started at Thu Jul 12 12:45:10 BST 2018 Jul 12 12:51:19 tecmint sshd[16739]: Failed password for root from 192.168.0.103 port 33324 ssh2 Jul 12 12:51:19 tecmint sshd[16739]: Failed password for root from 192.168.0.103 port 33324 ssh2 Jul 12 12:52:07 tecmint sshd[16739]: pam_unix(sshd:session): session opened for user root by (uid=0) Jul 12 12:52:07 tecmint sshd[16739]: pam_unix(sshd:session): session opened for user root by (uid=0)
You can also run multiple swatch processes to monitor various log files.
$ swatchdog -c ~/site1_watch_config -t /var/log/nginx/site1/access_log --daemon $ swatchdog -c ~/messages_watch_config -t /var/log/messages --daemon $ swatchdog -c ~/auth_watch_config -t /var/log/auth.log --daemon
For more information, check out the swatchdog man page.
$ man swatchdog
Swatchdog SourceForge Repository: https://sourceforge.net/projects/swatch/
The following are some additional log monitoring guides that you will find useful:
- 4 Ways to Watch or Monitor Log Files in Real Time
- How to Create a Centralized Log Server with Rsyslog
- Monitor Server Logs in Real-Time with “Log.io” Tool
- lnav – Watch and Analyze Apache Logs from a Linux Terminal
- ngxtop – Monitor Nginx Log Files in Real Time in Linux
Swatchdog is a simple active log file monitoring tool for Unix-like systems such as Linux. Try it out and share your thoughts or ask any questions in the comments section.