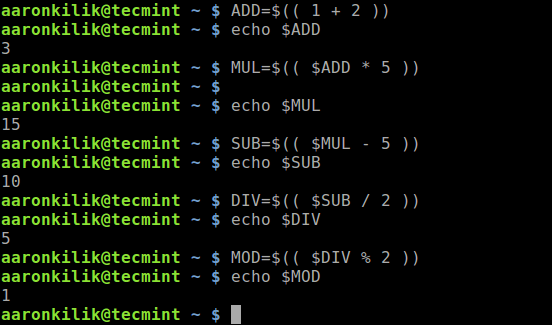
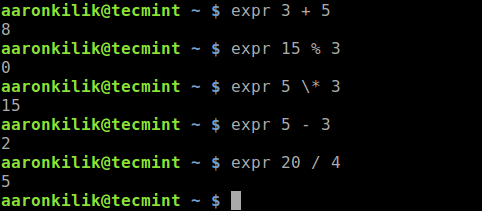
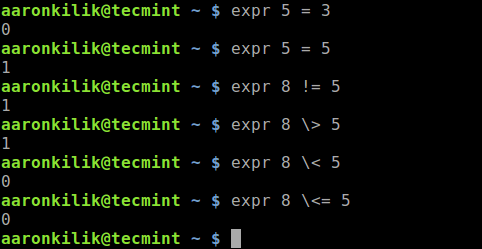
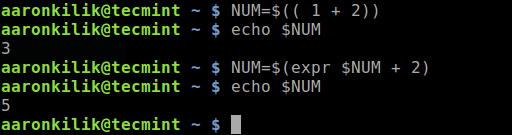
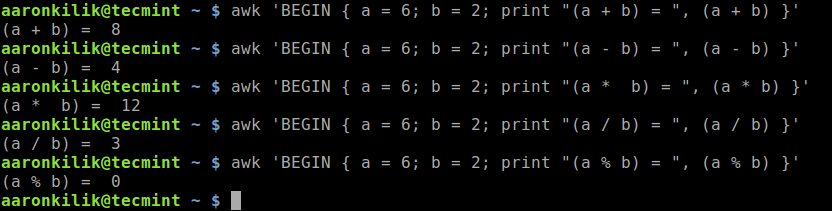
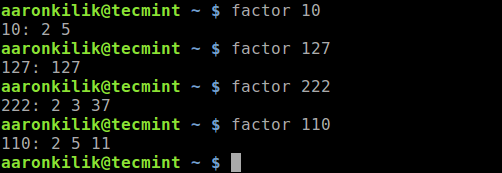
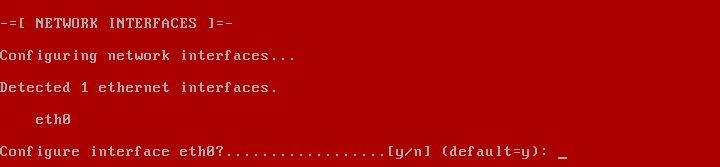
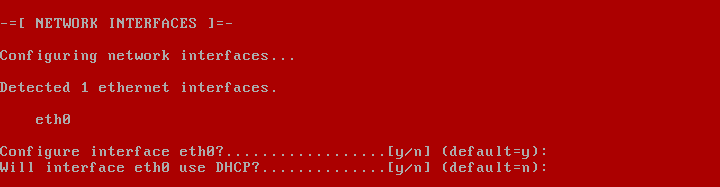
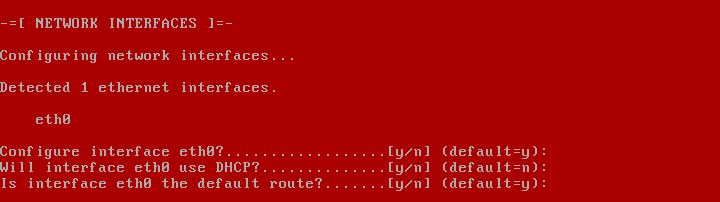
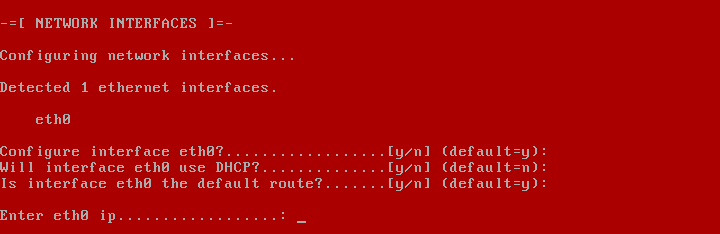
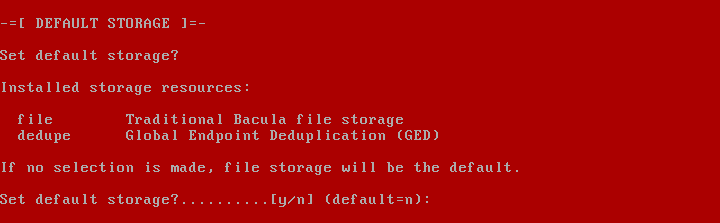
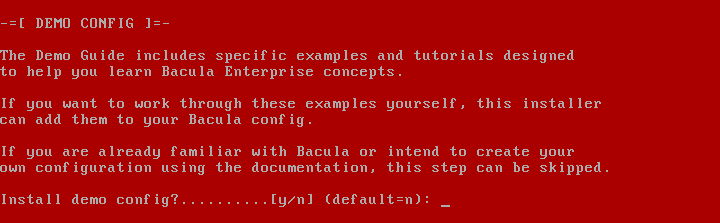
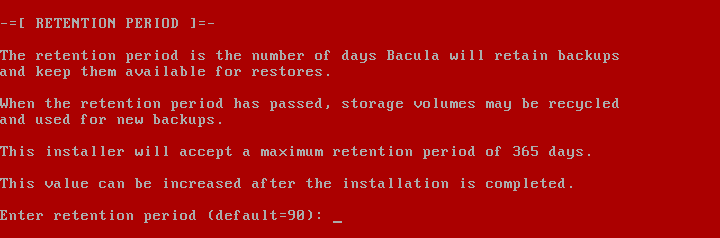
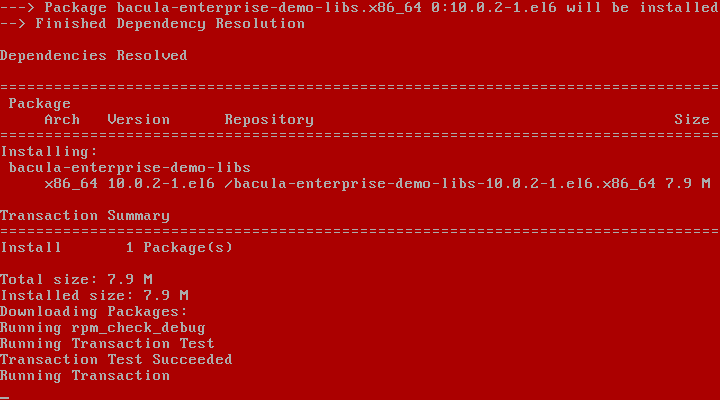
2019 is finally here folks! and what a better way to shed light on some of the best Linux distributions at your disposal. Even we have hundreds of distributions, we have created a list of distro based popularity, features and ease of usage.
In this article, we shall focus on the best Linux distributions for 2019. But remember each distro have their unique features and you should select based on your requirement.
Best Linux Distribution 2019 for Desktop/Laptops
# Ubuntu

Codenamed Cosmic Cuttlefish, Ubuntu 18.10 takes over from Ubuntu 18.04 Bionic Beaver LTS whose long-term support has now been extended to 10 years. On the other hand, Ubuntu 18.10 will only have 9 months support lasting up to July 2019. You can also look forward for Ubuntu 19.04 (named the ‘Disco Dingo’) release date is scheduled for April 18, 2019.
Nonetheless, Ubuntu 18.10 comes packed with an array of new features that improve the user experience. Among the new features are:
- GNOME 3.30
- Improved Battery life for laptops
- Fingerprint Scanner support
- Linux Kernel 4.18
- Faster installation and booting times
Before proceeding to install Ubuntu 18.10, ensure that your system meets the following requirements
- 2 GB RAM
- 2Ghz Dual core processor
- 25 GB of Free hard disk spaces
- 1024×768 screen resolution.
- A DVD drive or USB port for connecting to the installer media
Read Also: How to Install Ubuntu 18.04 Dual Boot with Windows 10
# Elementary

If you have been a long-term Linux user, ElementaryOS should top the favorite list. The latest version gives the user a vibrant feeling as it also helps when working with its intuitive smartphone interface. The OS (Elementary 5.0) is codenamed “Juno” and offers the most refined desktop version. Here are some of its specific features for Juno and any other ElementaryOS.
- Built-in Night Light
- The picture in Picture Mode
- Image Resizing Made Easy
- Easier App Funding
- Simple App Launcher
- Adaptive Panel
- Easily Available Keyboard Shortcut
- Bold Use of Color
- Easy Web Integration
- Transparent Readable Updates
Minimum Requirements for Installation
- Intel Core i3 or compatible dual core 64-bit processor
- 4GB RAM
- At least 15GB of SSD free space
- Internet access
- 1024 x 768
- CD/ DVD/ USB drive for installation
| Based on |
Ubuntu, Ubuntu in term based on Debian |
| Desktop Environment |
Pantheon, Pantheon built on top of GNOME |
| Package Management |
dpkg, Eddy Gui tool |
| General Purpose |
Desktop |
| Download Link |
https://elementary.io/ |
Read Also: How to Install Elementary OS 5.0 Juno with Windows 10
# Solus

Solus is one of the newcomers to the scene and is already making serious breakthroughs. The distribution will give you a clean and polished experience. The robust repositories include any software that you can imagine that are always get updates with every release.
The desktop environment is also known as ‘Budgie’ is attractive, simple and clean and offers a similar experience to Chrome OS without the need to purchase a Chromebook. You will get all the software that you need from the GNOME desktop environment, which is light and fast.
Budgie is clean and has a visually appealing user interface giving a wonderful and spectacular user experience. A single button opens the main menu as you have seen in a typical Windows 10 environment.
- A dual-core of at least 2GH and above
- 4GB RAM
- Direct X11 / GeForce 460 or higher
- 10GB available disk space
| Based on |
A distribution built from scratch |
| Desktop Environment |
Budgie, Uses GNOME technologies |
| Package Management |
PiSi package manager maintained as eopkg |
| General Purpose |
Desktop |
| Download Link |
https://getsol.us/download/ |
Read Also: How to Install Latest Solus from USB
# Fedora

Fedora 29 is the distro that defines new technologies that integrate into the Operating System resulting in some innovative features of any distribution. The only downside is the short support cycles that last for only a month after the release of the next version, which is usually six months.
- Gnome 3.30
- Fedora silverblue
- TLS 1.3
- Python 3.7
- Perl 5.28
- ZRAM support for ARM images
- New notification area
Minimum Requirements for Installation
- 6GB free hard disk space
- 2GB RAM
- Intel 64-bit processor
- AMD processor with AMD-V and AMD64 extensions
| Based on |
Redhat |
| Desktop Environment |
GNOME (default) |
| Package Management |
RPM, Built ‘dnf’ on top of it |
| General Purpose |
Desktop |
| Download Link |
https://getfedora.org/ |
# Mint

If you are moving from a Windows or Mac OS platform, you may want to use the simple Linux Mint as you try to find your way into the world of Linux. Mint is loaded fully packed with software you need to get back on track. Mint gives you a choice of four desktop environments with Cinnamon being the most closet to the Windows environment; however, MATE is still the popular choice because it is light on resources and loads faster using minimal memory.
Mint is always synchronized with the latest Ubuntu LTS releases meaning once you are running on Mint; there is no chance of getting malware threats.
The default theme on Linux mint is the Mint-Y, a successor to Mint-X. Mint-Y is available in three flavors. The light and the dark theme.
Linux Mint has two software managers known as the synaptic and the Software Manager. They both use APT front end. Synaptic installation window is plain text unlike the software manager, which is a GUI.
Minimum Requirements for Installation
- 64-bit x86 Processors
- 2GB of RAM
- 10GB of free hard disk space
- A graphics card that supports at least 1024 x 720 resolution
- CD/DVD/USB facilities
| Based on |
Debian and Ubuntu |
| Desktop Environment |
Cinnamon (default), Mate and Xfce |
| Package Management |
dpkg |
| General Purpose |
Desktop |
| Download Link |
https://linuxmint.com/download.php |
# Arch Linux

The Linux gaming platform has been a hot issue for many years, and gamers still cannot conclude whether Linux is a robust gaming platform or not. The verdict depends on strong support to make it a strong contender. Arch has many customization options that offer an opportunity for a gamer to free up system resources for gaming application and still be able to configure for general system performance.
The Operating System ships with the package management tool aptly referred to as Pacman that uses the command tar to package all installations. Pacman handles binary system packages and works with Arch Build System, which manages official Arch repositories, and own builds.
You only need to use pacman-syu to update all packages and to install group packages that come with the software run the command pacman-S gnome
Every time there is a rolling release update a large number of binary updates for the repositories. The timely releases are to make sure you do not need to re-install or update your OS at any given time. Instead, you need regular system updates to get the latest Arch Software.
Minimum Requirements for Installation
- An i686 or x86-64 based processors
- 2GB RAM (you can increase for better graphical performance)
- 10GB hard disk free space
| Based on |
Independent distribution relies on its own build system and repositories |
| Desktop Environment |
Cinnamon, GNOME, Budgie and more |
| Package Management |
pacman |
| General Purpose |
Desktop and Multipurpose |
| Download Link |
https://www.archlinux.org/download/ |
Read Also: Beginners Guide For Arch Linux Installation
# Antergos

The Antergos OS is one of the most underrated distributions in the Linux family. Antergos adheres to the arch principles of simplicity, modernity, versatility, centrality, and practicality. There is an option of using a GUI installer to make the task simple.
All the major desktop environments such as Gnome, Cinnamon, KDE, Openbox, Xfce, and Mate are supported. The icons on the interfaces provide superior that matches the beautiful theme.
Antergos is 100% functional straight from the box but with a limited number of packages. Additional packages are installed via the Pacman package manager, which contain new updates straight from the repos.
Minimum Requirements for Installation
- An i686 or x86-64 based processors
- 2GB RAM (you can increase for better graphical performance)
- 10GB hard disk free space
Read Also: How to Install Antergos Lastest Version
# Manjaro

Manjaro is an easy and user-friendly Operating System based on Arch Linux. Key features of this distro include the intuitive installation process, automatic hardware detection, stable updates with every release, uses special Bash scripts for managing graphics and more options available in supporting desktop configurations.
Manjaro comes with different desktop flavors such as GNOME 3.26, Xfce 4.12, KDE 5.11, MATE 1.18, Cinnamon 3.6, and Budgie 10.4.
The software comes packed with software such as Firefox, LibreOffice, and Cantata for all your music and library activities. Right click on the desktop to access several widgets that you can use to add icons on the desktop panel.
Use the Manjaro settings manager to give you an option of selecting the kernel version that you want to use as well as installing language packs and third-party drivers for specific hardware. The Manjaro settings are accessible on the M icon on the system tray under the Settings menu.
Cantatta is the default music app among other versions like clementine
Octopi package manager organizes packages and is easy to use
Minimum Requirements for Installation
- Intel-based i686 or i386 processor
- 1 GB RAM
- 8 GB free space on the hard disk
| Based on |
ArchLinux |
| Desktop Environment |
Cinnamon, GNOME, KDE Plasma 5, Xfce, Budgie, Deepin, Architect, and MATE |
| Package Management |
pacman |
| General Purpose |
Desktop and Multipurpose |
| Download Link |
https://manjaro.org/download/ |
# Pop Linux from System 76

POP Linux is a new Linux distro designed to have minimal clutter on the desktop. The creators of Pop OS system 76 specialize in building custom Linux PCs, and they have managed to tweak the Pop with the necessary improvements on the graphical interface. Switching between integrated Intel graphics and a dedicated NVidia graphics with a single mouse click. However, you can install NVidia drivers when doing the first time installation instead of using the open source Noveau drivers that are present in most distributions.
The Pop! _ OS does not support true hybrid graphics, as it is Windows. Switching between the Intel and NVidia graphics solutions is easy when you compare it with other Linux distributions. Pop! _OS works on any PC and with functionalities expected from a Linux distro. Forbes earlier suggested Pop OS is giving good Desktop experience on Lenovo ThinkPad X1 Laptop.
Pop OS is still emerging as a convenient tool for managing dual graphics options.
Prominent Features
- Ubuntu based
- Built from scratch
- Customized GNOME 3 as the preferred Desktop Environment
- Better Support
- Runs well on System 76 Laptops
Pop! Shop

This is an AppCenter, otherwise known as the Pop! _Shop is a project developed by the ElementaryOS team. The main purpose of this center is to make app organization easy to enable easy search experience.
Minimum Requirements for Installation
- 2GB RAM though the recommended is 4GB
- Minimum 16GB storage the recommended is 20GB
- 64-bit processors
| Based on |
Ubuntu |
| Desktop Environment |
GNOME (default), Budgie and more |
| Package Management |
dpkg |
| General Purpose |
Desktop and Multipurpose |
| Download Link |
https://system76.com/pop |
Read Also: How to Install Pop!_OS from System76
Best Linux Distro 2019 for Security
Online privacy is a big issue in this era of mass surveillance by both the state and online marketers. If you are keen on keeping these surveillance operations at bay, you need an operating system that has been created from the deep inside with one key thing in mind – security or privacy.
Therefore, with this in mind here are what we have in mind for the distros that will work for hackers, pen-testers, and the terminally paranoid.
# Kali Linux

Kali is becoming more popular in the cyber community for being Hackers number one priority. Kali has more than 300 tools that are applicable in different areas such as key-loggers, Wi-Fi scanners, scanning and exploiting targets, password crackers, probing and many other uses.
From the word go this is not a beginner friendly Operating System. Most of its courses are taught online on how to use it effectively, it the preferred choice for ethical hackers black hats, and penetration testers. Kali is relatable for its realism and attention to details. Kali Linux is Debian based OS that means all the software that you need can be installed the Debian commands.
The only available user on Kali is the root user, and all work within the OS works under this identity at all times. You can still add another account without the root privileges, but it will be at the logic of using Kali for security reasons.
Kali has many either penetration texting tools that can be GUI or CLI tools. Testing these applications means that you are aware that some commands may not work with your system or cause further problems to the network. When it comes to security applications ignorance is not an excuse.
If the software you want is not on the Debian packages within Kali, you can install but with the stern warning, that such additions only work to compromise system stability.
Minimum Requirements for Installation
- 128 MB RAM
- 2GB free disk space
- CPU that supports AMD64, i386, armel, arm64, and armhf
With the Desktop environment
- 2GB RAM
- 20 GB disk space
- CPU that supports AMD64, i386, armel, arm64, and armhf
| Based on |
Debian |
| Desktop Environment |
GNOME (default) |
| Package Management |
dpkg |
| General Purpose |
Penetration testing / Cyber security |
| Download Link |
https://www.kali.org/downloads/ |
# Tails

For anyone looking for the best online privacy, then Tails should be able to provide that security. Tails is another Debian based OS with privacy in mind; tails does not store any data by default that is why most developers refer to it as the amnesiac distribution.
Tails works with Tor browsers for all network connectivity and the OS can operate from a flash disk and can disguise itself to look like windows in public. Everything on Tails is encrypted this includes messaging, emails, and files.
The OS uses Gnome 3 classic as its Windows manager. Tails ships with multiple default software including an unsafe browser that you can use to access the internet without anonymity.
Once you boot into the system, a dialog box will pop up with the request to install more options. NO means that you will log in with no administrative privileges, YES will give a choice of setting up a password that allows the changing of network settings. Mac spoofing hides you on the network you just joined as well as giving you root access.
You can use the Onion Circuits to confirm connection details the moment you join the internet. The Tor browser is what any person obsessed with privacy and the latest updates use the Firefox 45.0.3 has new extensions that block any annoying ads.
KeyPassX saves all encrypted passwords, which are only unlocked using the master key. Installation of Tails is possible using a USB drive or installed on the computer and make it bootable
Minimum Requirements for Installation
- CD/DVD/USB ports
- 64 bit x86-64 processor
- 2GB RAM
Best Lightweight distro 2019
Why should you risk running the old insecure Windows XP with no support yet there are tons of secure Linux applications that are lightweight and will work with machines of that era. The outdated machine hardware configurations should not box you into loading unpredictable and insecure Operating System. The Linux distributions are more than light, and they are fast and secure.
# Lubuntu
Lubuntu makes it to the list of the lightweight Linux distributions that can work well in netbooks and older PCs. Lubuntu is an official Ubuntu, therefore, giving its users an opportunity to share the same software on the official Ubuntu software store.
Starting from Lubuntu 18.10 all 32-bit images will no longer get support from its developers, and therefore anyone with old 32-bit hardware configurations will have to move to 64-bit processors.
Lubuntu is a fast Operating System for old desktops that use the LXQt desktop environment alongside a selection of light applications. Switching from the previous LXDE desktop to the current LXQt started with Lubuntu 18.10. Comparing the two LXQt is modern after the merging of LXDE and Razor-qt.
All the necessary software that you need ship with the OS. Lubuntu is even better for anyone who is familiar with Ubuntu and wants to upgrade the old laptop or PC.
Minimum Requirements for Installation
- Pentium II or more
- 256MB RAM
- 5GB free disk space
| Based on |
Ubuntu |
| Desktop Environment |
LXQt, LXDE |
| Package Management |
dkpg |
| General Purpose |
Desktop and Multipurpose |
| Download Link |
https://lubuntu.net/downloads/ |
# Linux Lite

The growth of Linux Lite has been quite rapid in the recent past because beginners find it easy to use, it is attractive, and of course lightweight. It is another Ubuntu-based Linux Operating System running on Long-term Software (LTS) and has powerful and popular applications.
Using Linux Lite means you have a functional Linux desktop experience because it uses a more or less similar menu interface on Windows XP. The Xfce desktop environment is making things comfortable for a Linux newbie.
Linux Lite will handle with ease what other distributions are struggling with even with its lightweight structure. Linux Lite offers all the tools that promise the best performance. The latest Linux Lite at the moment is Linux Lite 4.2 that has an auto screen adjustment feature, the Redshift that adjusts the screen temperature at night or day.
Minimum Requirements for Installation
- 700MHz Processor
- 512MB RAM
- Screen Resolution of about 1024 x 768
# TinyCore

TinyCore is an incredibly compact distribution that is available in three different sizes. The barebone TinyCore is by far the tiniest of Linux distros that allow users to build their own variations.
The lightest TinyCore is about 11MB and has no graphical interface with an option of adding one after the installation. An alternative is the TinyCore Version 9.0, which is 16MB in size and has the option of FLTK or FLWM desktop environments. The third option is the install CorePlus that is more than 106MB and has a choice of Lightweight Window Managers such as IceWM and FluxBox. The CorePlus has support for Wi-Fi and non-US keyboards.
TinyCore saves on storage space because you need a cabled network during initial installation; therefore, it does not have many applications other than the terminal, basic text editor, and network connection manager.
Use the TinyCore Control Panel for quick access to different system configurations. Use the graphical package manager to install more software such as multimedia codecs.
Minimum Requirements for Installation
- 128MB RAM
- 32-bit and 64-bit processors. The system also accepts other versions such as PiCore
- 5GB disk space
| Based on |
Busy Box, flwm, Tiny X , Fltk |
| Desktop Environment |
GNOME , i3 , IceWM , HackedBox |
| Package Management |
tce-load |
| General Purpose |
Desktop |
| Download Link |
http://tinycorelinux.net/downloads.html |
# Puppy Linux

Puppy Linux is a veteran when it comes to the world of lightweight Linux world, and it boasts of a vast range of applications in different versions. The Operating System uses the Xenial Pup edition that works with Ubuntu Repositories.
Being one of the oldest lightweight distributions in the market, project developers have been making efforts to make it slim and light for more than a decade now. The different versions are the Slacko Puppy 6.3.2 based on Slackware while the XenialPulp 7.5 based on Ubuntu 16.04 LTS.
Puppy Linux Is full of apps with the most unusual apps like the Homebank, which helps in financial management, or the Gwhere that manages disk catalogs. A graphical tool is also available for managing samba shares and firewall.
The XenialPulp uses the QuickPet utility that manages the installation of the most popular apps.
Minimum Requirements for Installation
- 128MB RAM
- 32-bit and 64-bit processors
- 5GB disk space
Best Enterprise Server Distros 2019
In the Operating Systems server arena, Linux enjoys a bigger share because of things like stability, freedom, security, hardware support, and freedom. Linux servers are suitable for expert users and System Administrators as well as special users like programmers, gamers, programming, or ethical hackers.
These Operating Systems have special tools and enjoy long-term support. They give the user the best uptime, security, efficiency, and optimum performance. Let us look at the two of the most used Linux Server options.
# RedHat

Red Hat Enterprise Linux (RHEL) Server enjoys the same position held by Ubuntu in the world of Desktop Linux. Red Hat, the makers of RHEL, is a player that has been in the industry for a very long time. They have been able to refine this Server Operating system to ensure that most software packages and hardware get their certification support.
In addition, RHEL also has Long-term ongoing support that when it comes to Linux Servers Operating Systems.
The latest version comes in three disks that only need 38 minutes to install using the graphical interface. There is an option of having Desktop version installed for new users who want to try out the features. Installing the server version will only install software that supports server edition.
The Red Hat Server edition has two desktop environments the KDE 3.0 and GNOME 1.4. The Nautilus file manager and Ximian evolution will help you manage the system. You can comfortably use the Office Outlook environment with the presence of similar applications that support emails, calendar, contacts, and Palm OS integration.
The professional (paid) version offers the Sun Microsystems Star Office 5.2.
Minimum Requirements for Installation
- Any Pentium class processor (X86, POWER Architecture, z/Architecture, S/390)
- 5GB hard disk space
- 32MB RAM – no graphics, 64MB RAM – with graphics
- Network interface
# Suse Server

SUSE Linux Enterprise Server (SLES) is an Operating System that opens new avenues for the transformation in the software-defined era. SLES makes the IT infrastructure efficient by providing engaging system developers to help in solving critical workloads in the organization.
Bridges all software-defined infrastructure by giving a common base that enables easy migration of applications, improve system management, and make it easy to adopt containers.
SUSE automatically installs the minimal requires server packages, use the YaST Control Centre to configure network and most of the system settings. The Zypper package manager is good for downloading and installing essential server such as the postfix.
Minimum Requirements for Installation
- 4GB RAM
- 16GB disk space
- Network interface
| Based on |
RPM and RedHat |
| Desktop Environment |
GNOME (default), GNOME classic, ICeWM, SLE classic |
| Package Management |
Zypper |
| General Purpose |
Desktop and Server |
| Download Link |
https://www.suse.com/products/ |
Best Linux Distribution 2019 for Programmers
Most developers use Linux Based Operating Systems to get their work done or to create something new. Programmers more than anybody else are concerned with things like power, stability, compatibility, and flexibility found in any OS.
Ubuntu and Debian seem to be the leading contenders but there are several others, and today we will focus on Debian.
# Debian

The Debian GNU/Linux Distribution is the foundation many other Linux distros depend on. The latest version is otherwise known as the Stretch edition that also claims its position as the preferred programmers’ choice.
The infinite numbers of packages that are designed to be stable also have self-help tutorials that will help you solve issues as you work around your project. The Debian project has a testing branch where all the new software packages are stored. The testing site is a good site for advanced programmers and system administrators.
Linux Beginners will not find Debian to be friendly as its focus is on advanced programmers and users. The reason why you should consider Debian for your programming tasks is the ease of availability of resources, and you get to use the .deb package manager.
Version 9 of Debian uses GNOME3.22.2 and KDE 5.8. Other interfaces include the Budgie interface 10.2., Cinnamon, MATE, and LXQt. All are available from the software package manager.
Minimum Requirements for Installation
- 512MB
- 2GB free Hard disk space
| Based on |
Debian |
| Desktop Environment |
GNOME3, KDE 5.8 Cinnamon, MATE, Budgie 10.2 |
| Package Management |
dpkg |
| General Purpose |
Desktop and Multipurpose |
| Download Link |
http/www.debian.org/distrib |
Our thoughts
The effort to look for the best Linux Distribution gave us few excellent options in different categories. We tried and experimented with most of them and listed what we saw as the most appropriate in all categories in this article. When doing this we were so much alert to the fact that changes do take place and new things always pop up, we encourage your participation by adding to the list what you think was left out through the comment section below.
Please do not forget to tell us which ones you like or find to be a better distro.
Source