
Google’s goal is to make containers accessible to everyone, especially the enterprise, according to Anil Dhawan, product manager for the Google Cloud Platform.
When Google released Kubernetes as open source, one of the first challenges that the industry tackled was management, he said.
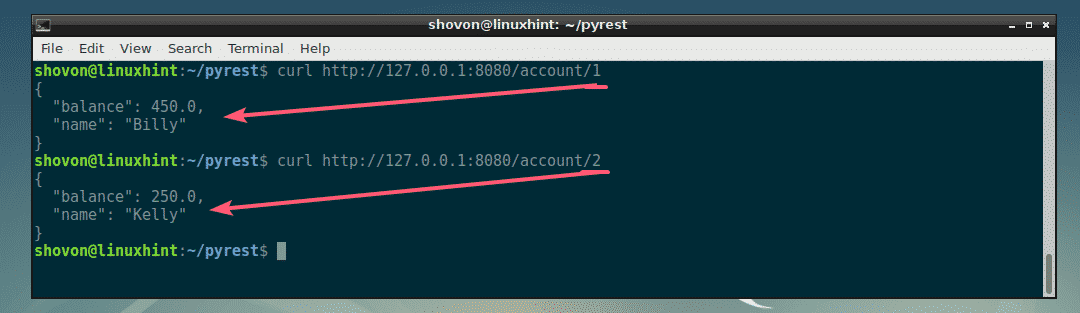
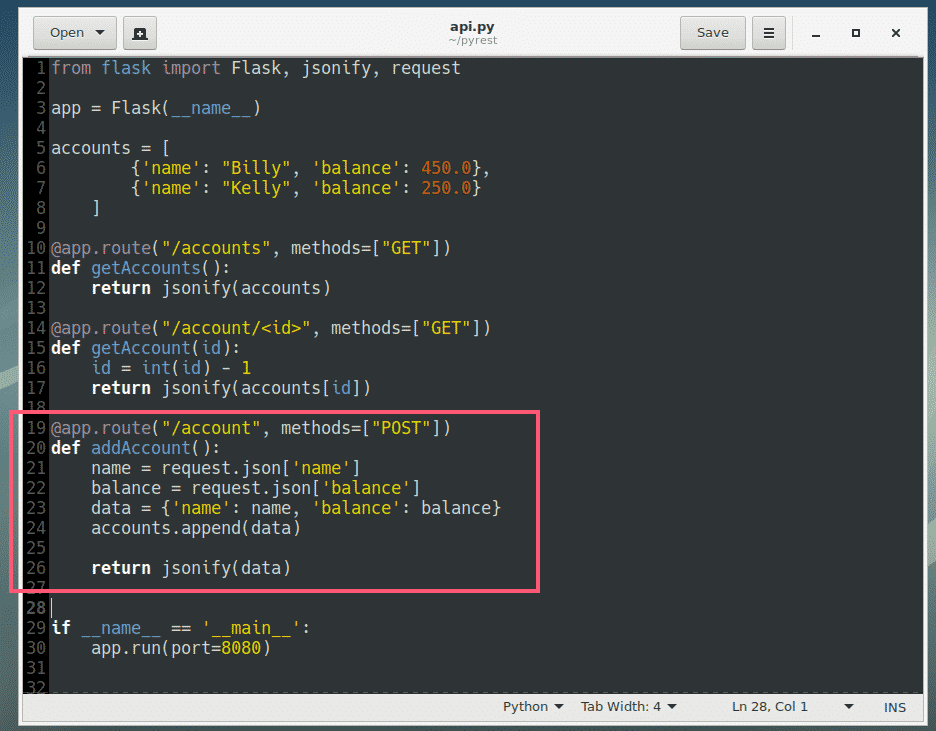
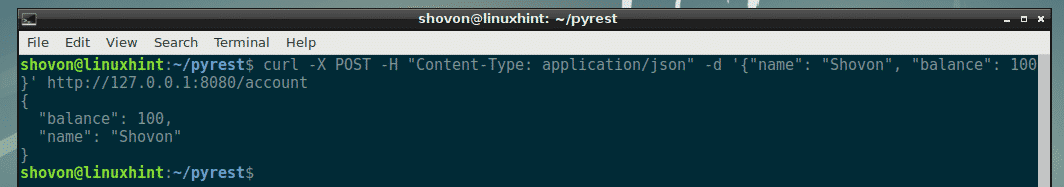
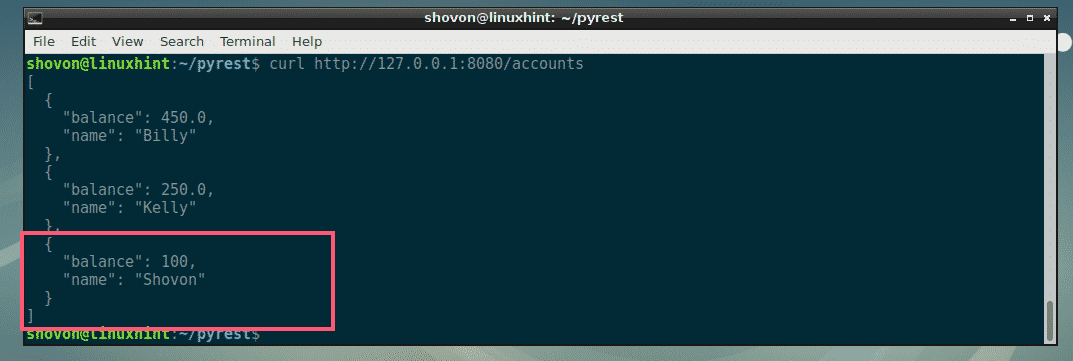
Google’s hosted Kubernetes Engine takes care of cluster orchestration and management. A bigger challenge to getting apps running on a Kubernetes cluster can be a manual, time-consuming process. GCP Marketplace provides prepackaged apps and deploys them onto any cluster, Dhawan noted.
Google makes the process safer by testing and vetting all Kubernetes apps listed on GCP Marketplace. That process includes vulnerability scanning and partner agreements for maintenance and support.
The security umbrella extends to all solutions available through the marketplace. That includes virtual machines, managed services, data sets, application programming interfaces, and Software as a Service.
The name change at one level is purely an effort to heighten the visibility of the Google Cloud Platform brand and to point attention to the new marketplace for ready-to-deploy apps, suggested Charles King, principal analyst at Pund-IT.
“Ideally, it will move interested businesses toward the marketplace, meaning that developers will see improved sales of their apps for GCP,” he told LinuxInsider.
More Behind the Move
Ultimately, Google’s enterprise cloud platform rebranding should make life easier for people managing container environments, said King. That will be the case especially if they happen to be studying or considering apps to buy and deploy.
“The impact on hybrid/multicloud is a bit harder to parse, though,” said King. “If the effort succeeds, it should impact Google’s GCP-related sales and business for the better.”
Google’s marketing move could be important for the future of hybrid and multicloud strategies, said Glen Kosaka, vice president of product at Kubernetes security firm
NeuVector.
“This is one really important step towards supporting and simplifying app deployment across clouds,” he told LinuxInsider.
Further, developers now have access to apps that can boost their own apps without having to worry about production deployment and scaling issues, noted Kosaka.
That should be a big deal to many devs, he added.
“Container management of marketplace apps now becomes more simplified, and customers — those responsible for container management — have the confidence that these Google Marketplace apps are tested and compatible with their cloud infrastructure,” Kosaka said.
Broader View Counts
Looking at the news in a strict and narrow sense, Google’s action appears to be little more than a rebranding witha clearer, more descriptive name. That is a fairly sensible move, suggested Alex Gounares, CEO of
Polyverse.
“From a broader perspective, this is the proverbial tip of the iceberg around a series of much bigger industry shifts to server-less computing and Containers as a Service,” he told LinuxInsider.
For one thing, Google’s rebranded platform means changes for developers. In the Internet’s early years, you had to build your own data centers, and build and manage your own applications. Effectively, everything was hand-built, on-premises and expensive, Gounares explained.
Then Salesforce.com came along, and the Software as a Service revolution was born. The same apps could be run in the cloud and delivered via a Web page.
That led to Amazon Web Services and to other cloud services providers letting folks effectively rent a data center on demand — the Infrastructure as a Service revolution.
For the application developer, physically acquiring the *hardware* became trivial, but from a software perspective, actually getting everything set up, configured, and running essentially was just as complicated as running things on premises, said Gounares.
Big Deal for Devs
Containers have revolutionized that. Now all of the complexity of something like a database or content management system or similar software can be packaged in a neat little box, according to Gounares.
That box can run alongside all the other pieces needed for a full solution. Configuration and management that used to take days or weeks to accomplish now can be done in a single command line.
“Renaming the service to address making one-click deployment of containers, and to open up new business models for software platform technology is a big, big, big deal,” remarked Gounares. “It is doing for software what Amazon AWS did for hardware and data centers.”
Deployment Factors
A big advantage to containers is their portability across environments. Users can develop their content and then move their workloads to any production environment, noted Google’s Dhawan.
Google works with open source Special Interest Groups, or SIGs, to create standards for Kubernetes apps. This brings the expertise of the open source community to the enterprise.
Google’s enhanced cloud platform speeds deployment on Kubernetes clusters, Kubernetes Engine, on-premises servers or other public clouds. A Marketplace window displays directly in the Kubernetes Engine console. That process involves clicking-to-deploy and specifying the location.
Third-party partners develop commercial Kubernetes apps, which come with support and usage-based billing on many parameters, such as API calls, number of hosts, and storage per month.
Google uses simplified license usage and offers more consumption options. For instance, the usage charges for apps are consolidated and billed through GCP, no matter where they are deployed. However, the non-GCP resources on which they run are not included, according to Dhawan.
A Win-Win Proposition
It is going to be orders of magnitude easier for developers to deploy both commercial and open source applications on Kubernetes. The launch of GCP Marketplace solves problems around scalability, operating in a virtual private cloud, and billing, noted Dan Garfield, chief evangelist at
Codefresh.
“For example, with Codefresh, our users can deploy our hybrid agent on Kubernetes so they can build on their own clusters, access code in their virtual private network, and bill everything through Google,” he told LinuxInsider. “As a third party, this makes the billing PO approval process a lot easier with enterprise customers where you normally have to become an approved vendor.”
For those responsible for container management, DevOps teams can consume “official” versions of software built for Kubernetes and keep them up to date, he added. This is especially important when you consider the security issues people have had with Dockerhub.
“The GCP Marketplace supports much more complex software stacks, and you can get the official packages rather than whatever someone has built and pushed to Dockerhub,” Garfield said.
What’s Available
GCP Marketplace features popular open source projects that are ready to deploy into Kubernetes. Each app includes clustered images and documented upgrade steps. This makes them ready to run in production. Packaged and maintained by Google Cloud, they implement best practices for running on Kubernetes Engine and GCP, according to Google.
Here is a sampling of some of the hundreds of apps featured on the GCP Marketplace:
- WordPress for blogging and content management;
- InfluxDB, Elasticsearch and Cassandra for big data and database;
- Apache Spark for big data/analytics;
- RabbitMQ for networking; and
- NGinx for Web serving.
A complete listing of apps available on the GCP Marketplace is
available here. No signup is needed to view the full list of available solutions.
Good for Hybrid and Multicloud Too
Anything that creates an additional wave of cloud-native applications is really great for the entire cloud marketplace. This includes different public cloud vendors, private cloud solutions, and even edge computing vendors, according to Roman Shaposhnik, VP for product & strategy at
Zededa.
“The platform can only be as successful as the number of killer apps that it hosts. This move by Google creates just the right kind of dynamics to get us the next crop of candidates for a killer cloud-native app,” he told LinuxInsider.
Hybrid cloud and multicloud deployments still have some way to go, however. What is missing is a way for seamlessly stretching container orchestrators across geographically distant locations, suggested Gaurav Yadav, founding engineering and product manager at
Hedvig.
“Unless we standardize container management operations across data centers and cloud locations separated by an unreliable network, true cloud-agnostic applications will always be hard to materialize,” he told LinuxInsider.
VMware became the de facto standard for virtual machine management because it took it out of the hands of admins, Yadav said. VMware made it simple, automated and scalable.
“For cloud-native applications, containers have the potential of replacing VMs as the standard for resource virtualization,” he suggested. “This is only possible if we bring the advanced capabilities that have been built over a decade for VM orchestration to the container management. This announcement is the next step towards this goal.”
The Right Move
Fundamentally, Google’s actions create a huge incentive for developers to transition their apps to a cloud-native architecture, said Zededa’s Shaposhnik.
“I would expect all of these to start being refactored and packaged for the GCP Marketplace,” he said, “and that is a good thing that goes way beyond immediate value on Google’s own cloud. Once an application is refactored and packaged to be truly cloud-native, you can transition between different clouds — including on-premises private clouds — in a much easier fashion.”
For container management, it is “yet another move in the right direction of making containers a ubiquitous, but completely invisible part of the IT infrastructure,” Shaposhnik added.
The Bottom Line
The changes that Google implemented are good news for developers, said Oleg Atamanenko, lead platform developer at
Kublr.
“It is a big step towards simplifying the experience when trying new applications,” he told LinuxInsider.
For IT management, on the other hand, the changes in Google’s GCP Marketplace mean cost reduction, reduced time-to-market, and faster innovation through streamlining application installation, Atamanenko said.
For developers, a change in name means little, but the direction Google has taken means a step forward in the enterprise world, said Stefano Maffulli, community director at
Scality.
Still, there is a down side, he told LinuxInsider.
Bitnami, which has been pushing to be the packaging tool to ship applications to the clouds, added support for Kubernetes early on.
“Now Google is making them less relevant on GCP, which can be a threat,” said Maffulli. “I wonder how long Bitnami and Google will stay partners.”

 Jack M. Germain has been an ECT News Network reporter since 2003. His main areas of focus are enterprise IT, Linux and open source technologies. He has written numerous reviews of Linux distros and other open source software.
Jack M. Germain has been an ECT News Network reporter since 2003. His main areas of focus are enterprise IT, Linux and open source technologies. He has written numerous reviews of Linux distros and other open source software.
Email Jack.
Source









 Jack M. Germain has been an ECT News Network reporter since 2003. His main areas of focus are enterprise IT, Linux and open source technologies. He has written numerous reviews of Linux distros and other open source software.
Jack M. Germain has been an ECT News Network reporter since 2003. His main areas of focus are enterprise IT, Linux and open source technologies. He has written numerous reviews of Linux distros and other open source software.

