Contents
- Installation
- Sniffing Traffic
- Getting password
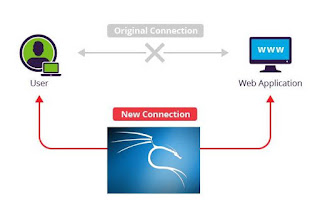
We will be installing Bettercap, doing a quick sniffing exercise, and then a more detailed section on grabbing the password. Will demonstrate the password grabbing on outlook.com, which seems to be particularly vulnerable to this attack.
Installing bettercap
Installation is simple-
apt-get update
apt-get dist-upgrade
apt-get install bettercap
The above three commands will leave you with latest versions of Kali and bettercap.
PS: I am writing this tutorial from a location with slow internet connection, and hence didn’t perform the dist-upgrade step. However, bettercap seems to be running mostly fine. There may be a few difference in what you observe and what I show in this demo due to this difference in versions. For those who want to know the versions of various utilities that I’m using, take a look below. If you are unfamiliar with Linux, you’re best off using the latest versions of everything, which can be obtained by running the three commands I mentioned earlier.
new@kali:~$ uname -a
Linux kali 4.7.0-kali1-amd64 #1 SMP Debian 4.7.6-1kali1 (2016-10-17) x86_64 GNU/Linux
new@kali:~$ ruby -v
ruby 2.3.1p112 (2016-04-26) [x86_64-linux-gnu]
Not on Kali?
The readme on
github repository of bettercap
is quite comprehensive, and would help you install bettercap on most linux distributions. After installation the process should be same for Kali or any other Linux distribution.
Sniffing Traffic
There’s nothing special about the usual sniffing traffic functionailty of bettercap. Bettercap can easily performing sniffing on your local area network. It also lets you write the output to a pcap file and later analyze it with WireShark or some other tool of your choice. I’ll just give a simple demo here. The real fun is in the capturing passwords section.
Run the command-
bettercap –sniffer
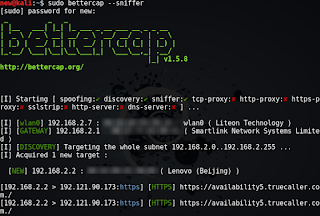 |
| Sniffing traffic: Screenshot shows my lenovo smartphone’s requests to truecaller being sniffed |
You’ll see all the websites being visited by all the devices on the network. Press ctrl+c to stop.
Take a look at the help manual for more commands, or read the wonderful documentation.
Internet stopped working
There are plenty of open issues on the github page of bettercap. The one problem I faced was that after bettercap had finished running, the internet connection on the
attacker machine
(Kali) would be killed. I fixed it by simply turning restarting the wlan0 interface (turn it off and on from the gui or use ifconfig commands).
reported that Bettercap killed internet connection for
all hosts.
If you face a different issue, take a look here and
see if you can find a solution
Capturing passwords
The fun part lies here. Bettercap uses sslstrip to change https webpages to simple http ones, which ensures that the passwords are transferred in clear text, and you can read them without any issues. I will be targeting my lenovo phone from my Kali machine. First, you must find the IP of your target. This can be done by simply running bettercap and waiting for all machines on your network to show up. Once they do, you can identify the one you’re trying to attack, and note it’s IP. Then use this IP as the target IP. Let’s look at the steps first.
PS: I’m assuming you connected to the network you are attacking using the wlan0 interface. If not, specify your interface using the -I option.
- Run the command bettercap on the terminal
- Wait for bettercap to acquire targets.
- When bettercap discovers the target you’re looking for, note down it’s IP address. Let’s call it TARGET_IP.
- Press ctrl+c to stop bettercap (if internet connectivity is lost, as was in my case, restart your wlan0 interface)
- Run this command – bettercap -T TARGET_IP –proxy -P POST (replace TARGET_IP with the appropriate IP)
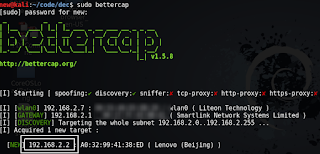 |
| In my case, my target was my Lenovo smartphone. It was detected by bettercap,
and i noted down it’s IP. 192.162.2.2 is what I’ll use as my TARGET_IP |
Now your attacker machine is ready and listening for traffic on the network. Once your victim opens any login page, bettercap will use sslstrip to remove the https from the URL, and once the target enters his/her login credentials, you will see them in cleartext.
Let’s look at a demo run of the above procedure.
Capturing passwords entered on Outlook by smartphone user on same LAN/WLAN
This section is simply going to be a set of pictures with captions below them explaining stuff. It should be easy to follow I hope.
From this test run, here are the limitations of the tool that I observed-
- The biggest problem – It does not work on all sites. Before trying outlook, I tried to see if I could carry out this MITM attack over Facebook, Gmail, Twitter, etc. Unfortunately, I wasn’t able to. It only seems to work with some websites.
- The difference in the URL if easily visible. Anyone who knows what https is, will notice the lack of it. I, for one, would never enter my credentials on an http page.The extra Ws in the www don’t help eitheir.
- The tool isn’t perfect. There are a few bugs.
Update : Giorgio’s comment on the tutorial addresses the first and the third issues. The reason why Facebook and Gmail don’t give in to the attack is because they don’t have an http version of their websites. Bettercap can’t force Facebook to replace it’s https page with an http one, simply because there is no http version of Facebook. Secondly, Yahoo looks buggy because it’s CSS files (ones hostel by google) are served over https, and an attempt to get an http version would yield nothing, since http versions aren’t available. Hence, the CSS files are missing, and while the parts of the page which operate over http load well, the ones which are exclusively https do not.
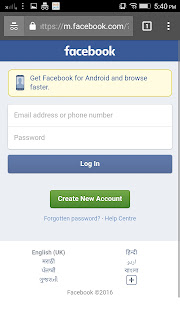 |
| Facebook seems immune to the attack |
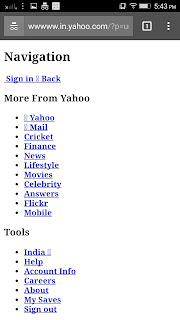 |
| Yahoo’s response is buggy, but you’ll notice that sslstrip did it’s job, the page is regular http now |
The tutorial ends here, a few personal insights ahead, not very important.
How to be safe
This demo must scare you. I, for one, wasn’t sure if this tool would work at all. However, it did work very well with outlook, and somewhat worked with yahoo as well (not shown in demo). Facebook and Gmail seem to be immune to it, but I didn’t really try hard to get them, and after writing this post, I’ll try to see if I can get the tool to grab Facebook and gmail logins as well. Regardless, we see how easy it can be for someone to grab your credentials if they are on the same network as you. So how can you be safe?
Here are some pointers-
This tutorial is supposed to serve as an introduction to sniffing, MITM and bettercap. I have observed that posts with too much theory don’t perform too well, so I just demonstrated the functionality of the tool. However, this was a very basic exercise, and for both me you, there are things to do-
- Try other functionalities offered by this tool.
- Try to get it to work with Facebook and Gmail. I’ll have to approach facebook and Gmail in a different manner, read the comment by Giorgio below for more information.
If I am able to get it to work with Facebook/Gmail, I’ll write another tutorial, showing you how you can do it too.