By Jack M. Germain
Oct 3, 2018 10:44 AM PT


Antergos 8.9, released last month, is one of the better Arch Linux options. It is a powerful and modern computing platform, elegantly designed. It gives power users almost all they could desire.
Arch distros are not for Linux newcomers — but for seasoned Linux users who are new to Arch, Antergos has much to offer.
One of the biggest challenges in getting started with any Arch distro is surviving the installation. A secondary challenge with Arch is its software management processes. Arch users who overcome those challenges gain a solid performing Linux desktop with more layers of security and little or no software bloat.
Antergos is not a perfect solution, but it certainly is one that offers a reasonable expectation of success. That is something I can not say about typical Arch distros.
There are a few other exceptions, though. Together, they form the upper crust winners among Arch Linux entry-level distros. In addition to Antergos, this elite group includes
ArchMerge,
Anarchy and
Manjaro.
Antergos is hawked on the developer’s website as a distro for everyone, but it actually is not for everyone — at least not until it is installed and running.
That said, Antergos does provide a less frustrating user experience through the installation process. The support options and easy-to-use desktops make Antergos a good fit for most users from that point forward. Still, I highly recommend some preparation before jumping into the Antergos distro or any Arch-based release.
For example, you need a better handle on how Arch Linux works to use Antergos successfully, or to use other Arch-based distros with less frustration. This entails considerable background reading to have things make sense and minimize the frustration.
Also, check out the community’s active forum, its well-maintained
Wiki, and the
ArchWiki. You can get additional help from the
Antergos IRC Channel.
Arch World Primer
What had been the Cinnarch distro until 2013 morphed into Antergos. Cinnarch was a single-flavored Arch distro running the Cinnamon desktop environment. That desktop gave Cinnarch a comfortable user experience. Its bottom panel bar, familiar two-column menu, and other attributes resembled what most users were accustomed to seeing on a computer screen.
Spanish developer Alex Filgueira rebranded his distro from its former iteration. He expanded the reborn Arch-based distro to offer a more complete range of desktops. That expansion includes the now-default GNOME 3 desktop, along with Cinnamon, KDE Plasma 5, Xfce, Mate and Openbox.
“Antergos” is a Galician word used to link the past with the present. Making an Arch distro simpler to install was Filgueira’s focus. Near-manual installation routines that relied on a command line process had been the Arch norm. Other Arch-based distros used a combination of scripts to semi-automate the installation routine.
The Antergos Cnchi graphical installer project hosted on GitHub is the tool that smooths out the installation process considerably. Cnchi is still in beta and has a few glitches, depending on your hardware and the desktop you select. Still, it does a better job than most other Arch-based distros.
About Antergos
The prime directive for all things Arch is simplicity, modernity and pragmatism. Added to that is a focus on centrality and versatility. It seems that in general, the founding principle of simplicity simply failed when it comes to installing most Arch Linux systems.
Antergos comes much closer to obeying that initial commandment, though. Numix is another system tool that helps Antergos to honor the founding articles that set out what Arch is supposed to be. Numix brings a distinctive design of icons and themes, for a unique look and feel in Antergos.
In true Arch fashion, Antergos relies on rolling releases. Once you install Antergos and have it running well, you never have to repeat the process. Updates roll in as they are ready, so the operating system always is loaded with the latest releases.
There are no point releases or reinstallation mandates. That provides a shining example of what simplicity should be in all Linux distros.
Getting Started
There are two download options. A Live Install Image includes a fully working environment that allows you to test how Antergos performs. The Minimal Install Image includes only what is required to run the installer and thus offers a much smaller initial download.
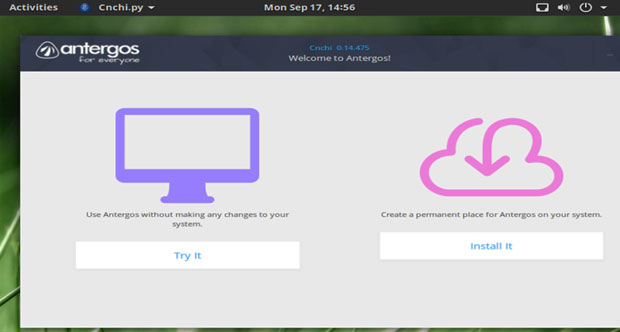
Within the live DVD session, you can start the installation process only from this spash screen.
After loading the live DVD, you click one button to run Antergos in live mode if you want to check out its performance and hardware compatibility. You click a second button to install it. If you decide to install Antergos, make sure to run the live session first, so you can establish an Internet connection. You must be connected to install this distro. You then can return to the splash screen to install the OS.
The ISO file that you download to burn the installation DVD contains all six desktop options. It sort of implies that you can load each one as part of the live session testing phase.
However, that is not the case. The Live session — whether you load it to test Antergos or install it — runs only the default GNOME 3 desktop. If you decide to install Antergos, the installer offers six desktop environment options once the installation routine gets under way.
Tread Carefully
Another tipping point is how to start an installation. The ISO is for direct installation. Typically, Arch distros do not have fully functional live session environments. Those that do require you to exit the live session environment to start the install process externally.
The “simplified” distros I mentioned above do provide the ability to fully test the Arch distros. When you boot into a live session, connect the PC to the Internet and wait for the installer to open automatically. Otherwise, it will not update and open properly.
If a glitch occurs, do not try to restart the installation process. The only cure is to reboot the PC. Then start the installation routine again.
Generally, the installation routine takes some time to complete. Be patient. Cnchi has to fetch the latest packages from the Internet. That burden is increased if you agree to the options to install proprietary graphics drivers, Flash add-ons and alternative Web browsers.
Updated Impressions
I last did a full-blown, hands-on test run of Antergos in March 2015. I have dabbled in a variety of its desktop options over the years since its Cinnarch days.
Antergos has not changed much in look and feel, regardless of which desktop is at play. To a point, that is a good thing. Stability and reliability continue to be staples of this Arch distro.
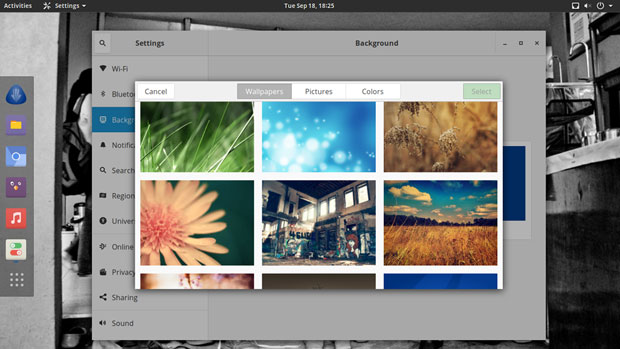
Antergos includes a nice collection of background images and color patterns.
However, I was less impressed this time around due to what struck me as complacency. Once the rather smooth installation was complete and the out-of-the-box reliability was evident, I found myself asking, “Is all there is?”
Like most Linux families — Arch, Debian, RPM-based, Ubuntu-based, Fedora-based or openSuse-based, to name a few — too many Linux distros look and play the same. In most cases, the desktop environments are all too lookalike.
That description is most true in working with the GNOME desktop. Since GNOME is still the default desktop still for Antergos, I installed that version for this review.
Arch’s other telltale traits fall to the background. GNOME is what you stare at most often while using the OS. Much like Arch Linux is Arch, so is GNOME desktop just Plane Jane uninviting GNOME.
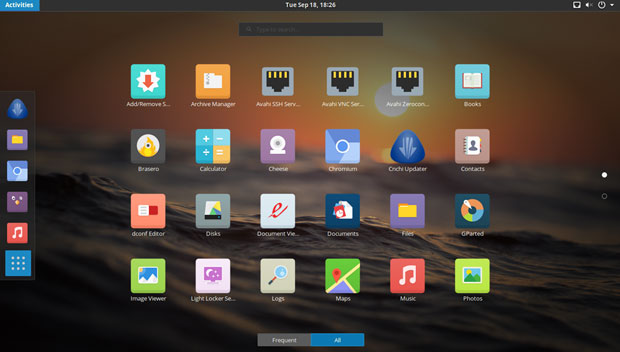
The GNOME 3 desktop is the default environment, but it lacks any distro-specific tweaking to make it unique or better. The same is true for the other five desktop options.
To make Antergos Linux a step better than other Arch-based distros running GNOME 3, the developer needs to build in some innovative tweaks to make the desktop’s integration just a tad bit more, umm, improved.
I have the same recommendation for Antergos’ other desktop options. This is clearly not something that all Linux developers do, but tweaking the desktop so that it is a unique part of the distro characteristics gives adopters a reason to stay with one distro.
Reasons to Go With Antergos
Desktop blandness aside, you should consider the reasons to select Antergos over other Arch Linux options. Perhaps the most important reason is that Antergos is 100 percent functional out of the box if you do not start off with the minimal installation ISO.
The preinstalled software is a small collection — that keeps bloat from setting in. You get the basics that include a video player, music software, text editor and other essentials, depending on the desktop environment.
You add to what you want from there. Additional software can be installed using the Pacman package manager. This is one of the best package managers available among Linux distributions.
Antergos uses the Arch Linux repositories. They contain the newest versions of all the software. The Arch Linux Archive is one of the best-maintained repositories.
Plus, you get access to more of the latest software additions that are not yet vetted into the official Arch repository through the Arch User Repository. This is a community-driven repository for Arch users.
Antergos comes with the Chromium Web browser by default. It runs Linux kernel 4.18.5.
Bottom Line
If you are already familiar with the Arch Linux family but want a quicker installation method, you will appreciate what Antergos brings to the Linux table. Those who are less familiar with the Arch Linux methodologies are sure to be much less enthusiastic about using the OS.
This distro gives you some of the most popular desktop environments all in one download. If you are clueless about a preferred desktop, though, you will be stuck staring at the default GNOME option. Antergos does not provide users with an easy switching tool to change the desktop option. The live session ISO does not let you try out any other option either.
Want to Suggest a Review?
Is there a Linux software application or distro you’d like to suggest for review? Something you love or would like to get to know?
Please
email your ideas to me, and I’ll consider them for a future Linux Picks and Pans column.
And use the Reader Comments feature below to provide your input!

 Jack M. Germain has been an ECT News Network reporter since 2003. His main areas of focus are enterprise IT, Linux and open source technologies. He has written numerous reviews of Linux distros and other open source software.
Jack M. Germain has been an ECT News Network reporter since 2003. His main areas of focus are enterprise IT, Linux and open source technologies. He has written numerous reviews of Linux distros and other open source software.
Email Jack.
Source
 On Kickstarter: SwitchDoc Labs’ “Smart Garden System” is a Raspberry Pi and Grove-based environmental monitoring and plant watering system with sensors for soil moisture, sunlight, air quality, temperature, and humidity.
On Kickstarter: SwitchDoc Labs’ “Smart Garden System” is a Raspberry Pi and Grove-based environmental monitoring and plant watering system with sensors for soil moisture, sunlight, air quality, temperature, and humidity.








 Jack M. Germain has been an ECT News Network reporter since 2003. His main areas of focus are enterprise IT, Linux and open source technologies. He has written numerous reviews of Linux distros and other open source software.
Jack M. Germain has been an ECT News Network reporter since 2003. His main areas of focus are enterprise IT, Linux and open source technologies. He has written numerous reviews of Linux distros and other open source software.





