| Oracle® Fusion Middleware Administrator's Guide for Oracle WebCenter 11g Release 1 (11.1.1) Part Number E12405-02 |
|
|
View PDF |
| Oracle® Fusion Middleware Administrator's Guide for Oracle WebCenter 11g Release 1 (11.1.1) Part Number E12405-02 |
|
|
View PDF |
This chapter describes how to configure your WebCenter application to handle authentication and authorization, and other aspects of application security.
This chapter includes the following sections:
Section 14.1, "Introduction to WebCenter Application Security"
Section 14.4, "Configuring the Policy and Credential Store to Use OID"
Section 14.6, "Configuring WebCenter Applications and Components to Use SSL"
Section 14.7, "Configuring a WebCenter Application to Use Single Sign-On"
Audience
The content of this chapter is intended for Fusion Middleware administrators (users granted the Admin role through the Oracle WebLogic Server Administration Console). Users with the Monitor or Operator roles can view security information but cannot make changes. See also, Section 1.8, "Understanding Administrative Operations, Roles, and Tools".
The recommended security model for Oracle WebCenter is based on Oracle ADF Security, which implements the Java Authentication and Authorization Service (JAAS) model. For more information about Oracle ADF Security, see the Oracle Fusion Middleware Fusion Developer's Guide for Oracle Application Development Framework.
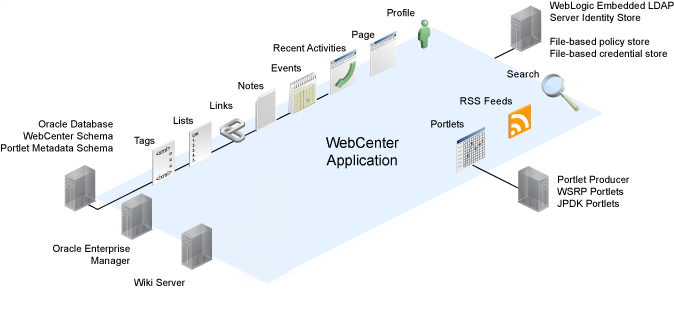
Figure 14-1 shows the relationship between a WebCenter application deployment and its services, servers, portlets, portlet producers, its identity, credential and policy stores, and Oracle Enterprise Manager.
Figure 14-1 Basic WebCenter Application Architecture
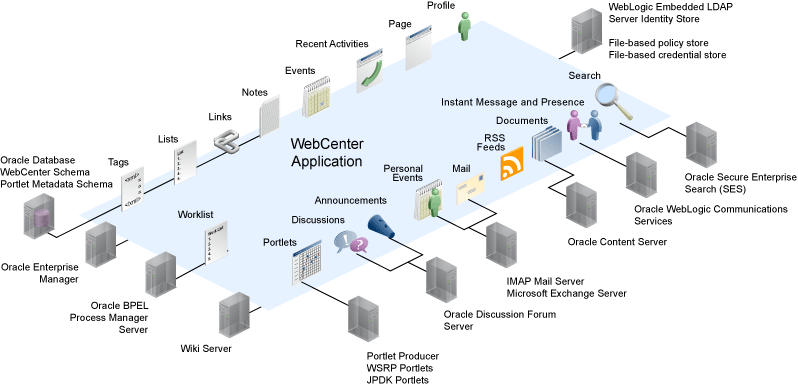
The diagram in Figure 14-2 shows a basic WebCenter application after deployment with its back-end server connections.
Figure 14-2 WebCenter Application Architecture with Back-end Server Connections
The diagram in Figure 14-3 shows the security layers for the WebCenter Spaces application.
Figure 14-3 WebCenter Spaces Security Layers
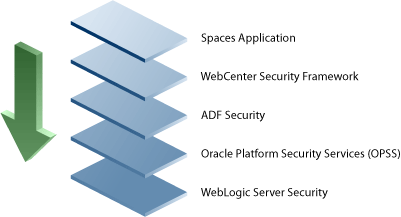
The security layers for a WebCenter application could have the same four bottom layers (WebCenter Security Framework, ADF Security, OPSS, and WebLogic Server Security) depending on how the application was structured. The application layer will, of course, depend on the implementation.
WebCenter Spaces Application Security
WebCenter Spaces provides support for:
Application role management and privilege mapping
Self-registration
Group space security management
Account management
External application credential management
WebCenter Security Framework
WebCenter Security Framework provides support for:
Service Security Extension Framework
Permission-based authorization
Role-mapping based authorization
External applications and credential mapping
ADF Security
ADF Security provides support for:
Page authorization
Task flow authorization
Secure connection management
Credential mapping APIs
Logout invocation, including logout from SSO enabled configurations with Oracle Access Manager and Oracle SSO
Secured login URL for ADF Security-based applications (the adfAuthentication servlet)
Oracle Platform Security Services (OPSS)
Anonymous-role support
Authenticated-role support
Identity store, policy store, and credential store
Identity Management Services
Oracle Web Service Manager Security
WebLogic Server Security
WebLogic Server Security provides support for:
WebLogic authenticators
Identity asserters
J2EE container security
SSL
This section describes the security configuration that is in place when custom WebCenter applications and WebCenter Spaces are deployed, and the tasks that need to be carried out after deployment:
Custom WebCenter applications do not contribute any pre-seeded accounts, and therefore rely on the administrator account (weblogic by default) that is set up when Fusion Middleware is installed. Use this administrator account to log into Fusion Middleware Control and set up new accounts.
Although WebCenter Spaces does not contribute any pre-seeded accounts, there are certain pre-seeded grants that are given to the default administrator account (weblogic) for the WebCenter Spaces application. If your installation does not use weblogic as the account name for the administrator role, you will need to configure one or more other users for this role as described in Section 14.3.5.1, "Granting the WebCenter Spaces Administrator Role Using Fusion Middleware Control".
Application roles and permissions are defined within WebCenter Spaces and are stored in an application-specific stripe of the policy store. Consequently, WebCenter Spaces roles apply only to WebCenter Spaces; WebCenter Spaces roles and permissions do not extend to other applications.
Application roles differ from roles that appear in the identity store portion of the embedded LDAP server or in roles defined by the enterprise LDAP provider. Application roles are specific to an application and defined in the application policy store.
Enterprise roles, which are stored in the enterprise identity store, apply at the enterprise level. That is, the roles and permissions that you or a system administrator define within the enterprise identity store do not imply permissions within WebCenter Spaces.
Within WebCenter Spaces you can add users defined in the corporate identity store and assign them roles and permissions. You can also add roles defined in the enterprise identity store and assign permissions to those roles for WebCenter Spaces.
Note:
When Groups (enterprise roles) are assigned to a group space role in WebCenter Spaces, the users that belong to that group (rather than the enterprise role) are added individually to the group space role. Consequently, be careful not to add groups with inordinately large amounts of users as performance during authentication may be affected.By default, WebCenter applications are configured to use a file-based embedded LDAP identity store to store application-level user IDs, and a file-based LDAP policy store to store policy grants.
Although secure, the embedded LDAP identity store is not a "production-class" store and should be replaced with an external LDAP-based identity store such as Oracle Internet Directory for enterprise production environments.
The default file-based policy store can only be used for single-node WebCenter Spaces configurations. For multi-node configurations, you must reassociate the policy and credential store with an external LDAP-based store (such as Oracle Internet Directory) as described in Section 14.4, "Configuring the Policy and Credential Store to Use OID".
The policy store can be configured to use Oracle Internet Directory 11gR1 and 10.1.4.3, and OVD 11gR1 with the Local Store Adapter (LSA).
The identity store can be configured to use the following LDAP servers:
Oracle Virtual Directory (OVD) 11gR1 and 10.1.4
Sun iPlanet version 4.1.3
Active Directory shipped as part of Windows 2000
Open LDAP version 2.0.7
Novell NDS version 8.5.1
For more information on reconfiguring the identity and policy stores, see Section 14.3, "Configuring the Identity Store" and Section 14.4, "Configuring the Policy and Credential Store to Use OID".
Note:
The Oracle Content Server and Oracle WebCenter Discussions back-ends can only be configured to use an external LDAP-based identity store. Consequently, the Documents service, which relies on the Oracle Content Server back-end, requires that you reassociate the identity store with on of the external LDAP servers listed above. It is also recommended that WebCenter Spaces and the Oracle Content Server share the same LDAP server.The out-of-the-box credential store is wallet-based (that is, file-based) and is contained in the file cwallet.sso. The location of this file is specified in the Oracle Platform Security configuration file jps-config.xml. When you reassociate the policy store to an LDAP directory, the application credentials are automatically migrated to the same LDAP directory as the policy store.
The ADF Security permissions model supports both permission-based and role-based authorization. These two types of authorization are discussed in the following sections:
Use permission-based authorization for services, such as the Lists service, where access control is implemented within the WebCenter application using Oracle Platform Security Services (OPSS). WebCenter Spaces provides extensive user and role management tools with which you can create application roles, and define what permissions should be granted to those roles. For information on managing users and roles in WebCenter Spaces, see Managing Application Roles and Permissions.
Services that need to access "remote" (back-end) resources require role-mapping based authorization. For example, for the Discussions service, role mapping is required when the users of a WebCenter application (mapping to one or more group space roles) need to be mapped to another set of roles on the Oracle WebCenter Discussions Server (or Oracle Content Server).
The following points should be considered when provisioning role-mapping based authorization in WebCenter Spaces:
Default application and group space roles for WebCenter Spaces are mapped to the corresponding service roles (see Table 14-1, "WebCenter Role Permissions" for the default mappings).
When a new user is granted an application or group space role, a similar grant (privilege) is granted in the back-end server. For example, when user Pat is granted Discussions-Manage permissions in WebCenter Spaces, Pat is granted corresponding permissions in the back-end discussion server. See also, Section 19.1.4, "Understanding Discussions Server Role and Permission Mapping".
Table 14-1 shows the pre-seeded roles in the WebCenter policy store (WebCenter Seeded Roles). The Community of Interest Role Template and Group Space Project Role Template are policy entries that are kept in the corresponding group space templates. When a new group space is created, the roles and corresponding permissions are added to the policy store at runtime.
Table 14-1 WebCenter Role Permissions
| Permission grants to roles in WebCenter | WebCenter- admin | Spaces- User | Public- User | Community of Interest | Community of Interest | Community of Interest | Group Space Project | Group Space Project | Group Space Project |
|---|---|---|---|---|---|---|---|---|---|
| Role Mapping | moderator | participant | viewer | moderator | participant | viewer | |||
|
WebCenterPermission(Application) |
|||||||||
|
manage |
✔ |
||||||||
|
configure |
✙ |
||||||||
|
view |
✙ |
✔ |
✔ |
||||||
|
SpacePermission (Group Spaces) |
|||||||||
|
manage |
✔ |
✔ |
✔ |
||||||
|
configure |
✙ |
✙ |
✙ |
||||||
|
view |
✙ |
✙ |
✔ |
✔ |
✙ |
✔ |
✔ |
||
|
create |
✙ |
✔ |
|||||||
|
PagePermission(Page) |
|||||||||
|
manage |
✔ |
✔ |
✔ |
||||||
|
create |
✙ |
✔ |
✙ |
✙ |
|||||
|
delete |
✙ |
✙ |
✙ |
||||||
|
edit |
✙ |
✙ |
✙ |
||||||
|
personalize |
✙ |
✙ |
✙ |
✔ |
|||||
|
view |
✙ |
✙ |
✔ |
✔ |
✙ |
✔ |
✔ |
||
|
ListPermission*(Lists) |
|||||||||
|
manage |
✔ |
✔ |
|||||||
|
create |
✙ |
✔ |
✙ |
✔ |
|||||
|
delete |
✙ |
✔ |
✙ |
✔ |
|||||
|
edit |
✙ |
✔ |
✙ |
✔ |
|||||
|
update |
✙ |
✔ |
✙ |
✔ |
✔ |
||||
|
view |
✙ |
✔ |
✔ |
✙ |
✔ |
✔ |
|||
|
EventPermission(Events) |
|||||||||
|
manage |
✔ |
✔ |
|||||||
|
create |
✙ |
✔ |
✙ |
✔ |
|||||
|
delete |
✙ |
✔ |
✙ |
✔ |
|||||
|
edit |
✙ |
✔ |
✙ |
✔ |
|||||
|
view |
✙ |
✔ |
✔ |
✙ |
✔ |
✔ |
|||
|
NotePermission(Notes) |
|||||||||
|
manage |
✔ |
✔ |
|||||||
|
create |
✙ |
✔ |
✙ |
✔ |
|||||
|
delete |
✙ |
✔ |
✙ |
✔ |
|||||
|
update |
✙ |
✔ |
✙ |
✔ |
|||||
|
view |
✙ |
✔ |
✔ |
✙ |
✔ |
✔ |
|||
|
Discussions |
|||||||||
|
manage (Forum Moderator Role) |
✔ |
✔ |
✔ |
||||||
|
edit (Forum Writer Role) |
✙ |
✔ |
✙ |
✔ |
|||||
|
view (Forum Reader Role) |
✙ |
✔ |
✙ |
✔ |
|||||
|
Document Library roles (Role id/Enum name/short description)**(Documents) |
|||||||||
|
1/SUPER_ADMINISTRATOR (manage) |
|||||||||
|
2/DELETE (delete) |
✔ |
✔ |
|||||||
|
3/WRITE (create) |
✔ |
✔ |
✔ |
✔ |
|||||
|
4/READ (view) |
✔ |
✔ |
✔ |
✔ |
✔ |
✔ |
|||
|
Announcements |
|||||||||
|
manage |
✔ |
✔ |
|||||||
|
edit |
✙ |
✔ |
✙ |
✔ |
|||||
|
view |
✙ |
✔ |
✙ |
✔ |
|||||
|
Links |
|||||||||
|
manage |
✔ |
✔ |
✔ |
||||||
|
delete |
✙ |
✔ |
✙ |
✔ |
|||||
|
create |
✙ |
✔ |
✙ |
✔ |
|||||
|
ProfilePermission |
|||||||||
|
manage |
✔ |
||||||||
|
edit |
✙ |
✔ |
* For the Lists service, "Edit" means the ability to edit a definition as well as content, and "update" means the ability to edit content. "Manage", for lists and elsewhere in this table, means the ability to make configuration and security changes.
** The Documents service uses integer identifiers for roles. The role mapping information in the policy store therefore refers to the corresponding service role's integer identifier. Each service role has an associated short and long description. The WebCenter security provisioning screens show the corresponding description instead of IDs.
| Legend | Description |
|---|---|
| ✔ | Shows an explicitly granted permission, action, or role mapping. |
| ✙ | Shows an implied permission as a result of an explicitly granted permission. The permission implementation itself does the implication. |
Some WebCenter application and framework code calls APIs from the security platform that are secured with Permission checks. The WebCenter code needs to be granted the appropriate permissions to invoke the OPSS APIs, and itself should authorize access to the various operations exposed in the User Interface. For example, the permission to access policy store and grant or revoke permissions (PolicyStoreAccessPermission), CRUD on application roles, is granted to the "webcenter" application out of the box. The WebCenter code must then pre-authorize access to the various operations, using the above WebCenter-specific permissions, and then invoke the OPSS APIs as privileged actions.
After deploying your WebCenter application, consider the following configuration tasks for your site:
SSL
Secure Sockets Layer (SSL) provides additional security for connections between WebCenter applications or components by providing an additional authentication layer, and by encrypting the data exchanged. For connections between applications or components where the data exchanges is sensitive, consider securing the connection with SSL. For a list of the connections that can and should be protected with SSL in a production environment, see Section 14.6, "Configuring WebCenter Applications and Components to Use SSL".
Note:
Using SSL is computationally intensive and adds overhead to a connection. SSL should therefore not be used where it is not required, and is best reserved for production environments.SSO
Single Sign-On (SSO) allows users to log in once across WebCenter applications and components rather than having to log in for each sub-application (for example, for accessing a wiki page in WebCenter Spaces). Users do not have to maintain a separate user ID and password for each application or component that they access. However, you can still configure a variety of authentication methods, so that more sensitive applications can be protected using more stringent methods. WebCenter supports four single sign-on solutions: Oracle Access Manager (OAM), Oracle Single Sign-on (OSSO), a SAML-based single sign-on solution for Oracle WebCenter applications only, and an SSO solution for Microsoft clients, using Windows authentication based on the Simple and Protected Negotiate (SPNEGO) mechanism and the Kerberos protocol. For a discussion of these solutions and an overview of single sign-on, see Section 14.7, "Configuring a WebCenter Application to Use Single Sign-On".
Reassociate the identity store to use an external LDAP
By default, WebCenter applications use an embedded LDAP for its identity store. Although secure, the out-of-the-box embedded LDAP may not scale appropriately for large enterprise production environments. For instructions on how to configure the identity store to use an external LDAP such as Oracle Internet Directory (OID), see Section 14.3, "Configuring the Identity Store".
Note:
Oracle Content Server and Oracle WebCenter Discussions Server must use an external LDAP identity store rather the default embedded LDAP identity store. Consequently, if you plan on using the Documents or Discussions services in your WebCenter application, you must reconfigure the identity store to use an external LDAP. For more information on reconfiguring the identity store, see Section 14.3, "Configuring the Identity Store".Reassociate the policy store to use an external LDAP
By default, WebCenter uses a file-based system-jazn-data.xml policy store to store policy grants. You should consider using an LDAP-based policy store. For information on how to configure the policy store to use LDAP, see Section 14.4, "Configuring the Policy and Credential Store to Use OID".
WS-Security
Although the use of WS-Security adds complexity to the configuration and management of a WebCenter application and the set of producers it consumes, it helps ensures the security of the information being published by the WebCenter application. Adding WS-Security provides authentication for the consumer, and message-level security.
For information on how to configure WS-Security for WebCenter applications and components, see Section 14.8, "Configuring WS-Security".
This section describes how to reassociate the identity store with an external LDAP rather than the default embedded identity store. It also provides additional configuration information for configuring services such as the discussions server, and contains the following subsections:
Section 14.3.1, "Reassociating the Identity Store with an External LDAP"
Section 14.3.4, "Moving the Administrator Account to an External LDAP Server"
Section 14.3.5, "Granting the WebCenter Administrator Role to a WebCenter Spaces User"
Section 14.3.6, "Configuring the Discussions Server to Share the Identity Store LDAP Server"
Section 14.3.8, "Configuring the Oracle Content Server to Share the Identity Store LDAP Server"
Note that for custom WebCenter applications, the steps for Granting the WebCenter Administrator Role to a WebCenter Spaces User and Configuring the Discussions Server to Share the Identity Store LDAP Server are not required. For more information about the identity store, see the Oracle Fusion Middleware Security Guide.
Caution:
Before reassociating the identity store, be sure to back up the relevant configuration files:config.xml
jps-config.xml
system-jazn-data.xml
As a precaution, you should also back up the boot.properties file for the domain Administration Server for the domain.
This section describes how to configure the identity store to use an external LDAP server, such as Oracle Internet Directory, rather than the default embedded LDAP.
To reassociate the identity store:
Log in to the WLS Administration Console.
For information on logging into the WLS Administration Console, see Section 1.12.2, "Oracle WebLogic Server Administration Console".
In the Domain Structure pane (see Figure 14-12), click Security Realms.
The Summary of Security Realms pane displays (see Figure 14-13).
Figure 14-5 Summary of Security Realms pane
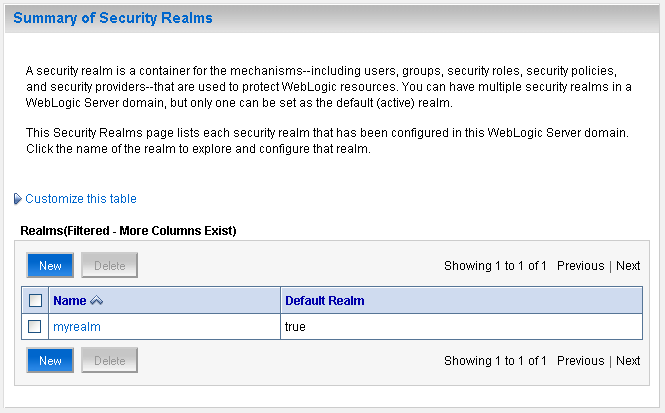
In the Name column, click the realm for which you want to reassociate the identity store.
The Realm Settings pane displays (see Figure 14-6).
Open the Providers tab.
The Providers Settings pane displays (see Figure 14-7).
Click New to add a new provider.
The Create a New Authentication Provider pane displays (see Figure 14-8).
Figure 14-8 Create a New Authentication Provider Pane
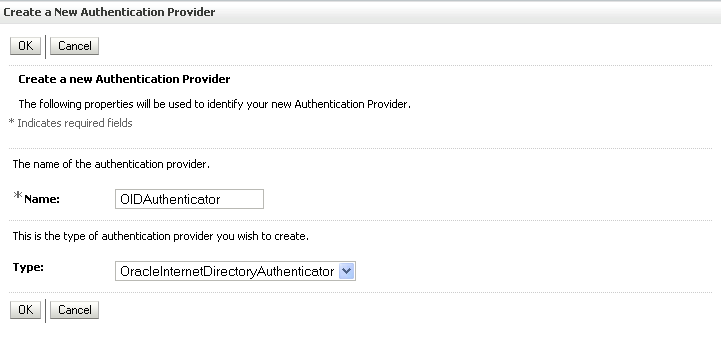
Enter a name for the provider (for example OIDAuthenticator for a provider that will authenticate the user for the Oracle Internet Directory).
Select the authenticator appropriate for your LDAP directory from the list of authenticators.
Be sure to select the authenticator associated with the LDAP you are configuring rather than choosing the generic DefaultAuthenticator. For example, for OID select OracleInternetDirectoryAuthenticator, or for iPlanet select IPlanetAuthenticator. Move the authenticator to the top of the authenticator list and set its Control Flag (and any other authenticator Control Flags in the list), to SUFFICIENT.
See Section 14.3.4, "Moving the Administrator Account to an External LDAP Server" for information about how to configure the default administrator account.
Note:
If more than one authenticator is configured, WebCenter Spaces will work only with the users in the identity store mapped by the first authenticator.The identity store access APIs use the first REQUIRED authenticator in the list. If there are no REQUIRED authenticators, it uses the first SUFFICIENT one. Therefore, for stacked authenticators, be sure to list the authenticator mapping the primary identity store to be used with the identity store access APIs first, and set all other authenticator control flags to SUFFICIENT.
Click OK to save your settings.
The Settings pane displays with the new authentication provider (see Figure 14-9).
Figure 14-9 Settings Pane - Authentication Providers
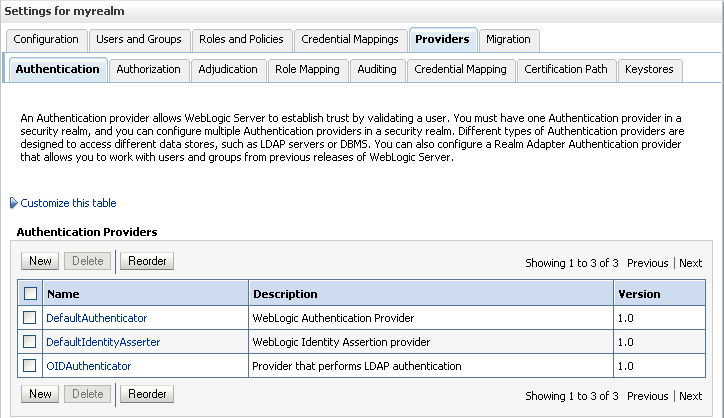
In the list of Authentication Providers, click the newly created provider.
The Settings Pane for the new authentication provider displays (see Figure 14-10).
Figure 14-10 Settings Pane for Authenticator
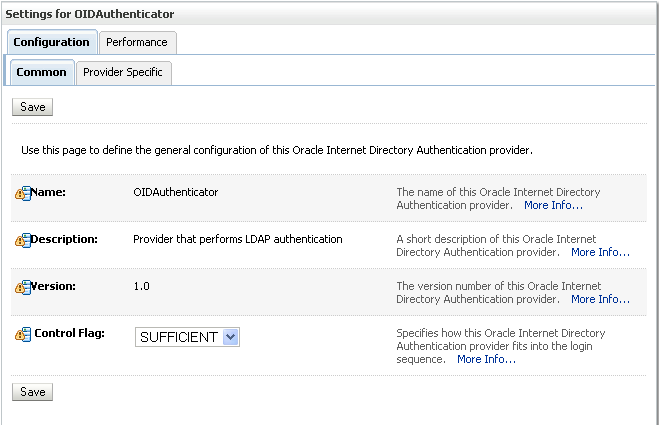
Set the Control Flag to SUFFICIENT.
Setting the Control Flag to SUFFICIENT indicates that if a user can be authenticated successfully by this authenticator, then the authentication provider should accept that authentication and should not invoke any additional authenticators.
Note:
If the authentication fails, it will fall through to the next authenticator in the chain. Therefore, be sure all subsequent authenticators also have their control flag set toSUFFICIENT.Click Save to save this setting.
Open the Provider Specific tab to enter the details for the LDAP server.
The Provider Specific pane displays (see Figure 14-11).
Enter the details specific to your LDAP server.
| Parameter | Value | Description |
|---|---|---|
| Host: | The LDAP server's server ID (for example, <ldap_host>example.com) |
|
| Port: | The LDAP server's port number (for example, 3060) |
|
| Principal: | The LDAP user DN used to connect to the LDAP server (for example, cn=orcladmin) | |
| Credential: | The password used to connect to the LDAP server | |
| User Base DN: | Specify the DN under which your Users start (for example, cn=users,dc=example,dc=com) |
|
| Group Base DN: | Specify the DN that points to your Groups node (for example, cn=groups,dc=example,dc=com) |
|
| Use Retrieved User Name as Principal | Checked | Must be turned on |
| All Users Filter: | (&(uid=*)(objectclass=person)) |
Search to find all users under the User Base DN |
| User From Name Filter: | (&(uid=%u)(objectclass=person)) |
|
| User Name Attribute: | uid |
If you modify a username attribute to something other than the default set for the LDAP server in the authenticator, you must also edit the jps-config.xml file to correspond to these values. Specifically, the username.attr and user.login.attr properties (highlighted below) must be added for user lookups to function correctly:
<!-- JPS WLS LDAP Identity Store Service Instance --> <serviceInstance name="idstore.ldap" provider="idstore.ldap.provider"> <property name="idstore.config.provider" value="oracle.security.jps.wls.internal.idstore.WlsLdapIdStoreConfigProvider"/> <property name="username.attr" value="uid"/> <property name="user.login.attr" value="uid"/> </serviceInstance>
Click Save.
Return to the Providers tab and reorder the providers so that the new authentication provider is on top, followed by any other authenticators with the DefaultAuthenticator placed at the end of the list.
All should have their Control Flags set to SUFFICIENT so that subsequent authenticators can authenticate identities that fall through from the new provider all the way through to the DefaultAuthenticator (which is used only for the default file-based embedded LDAP). For example, logins such as the default administrator account are not typically created in the LDAP directory, but still need to be authenticated to start up the server. Unless identities are allowed to fall through to the DefaultAuthenticator, the default administrator account will not be authenticated. For more information about the DefaultAuthenticator and the default administrator account, see Section 14.3.4, "Moving the Administrator Account to an External LDAP Server".
Restart the Administration Server and the managed server for the changes to take effect.
For a production environment, we recommended that you add the following configuration entry to the jps-config.xml file for best performance:
<serviceInstance provider="idstore.ldap.provider" name="idstore.ldap">
<property value="oracle.security.jps.wls.internal.idstore.WlsLdapIdStoreConfigProvider" name="idstore.config.provider"/>
<property name="CONNECTION_POOL_CLASS" value="oracle.security.idm.providers.stdldap.JNDIPool"/>
</serviceInstance>
You can add users to the embedded LDAP or an external LDAP using the WLS Administration Console. For Oracle Internet Directory, although users are typically managed using ODSM (described in the section on "Managing Directory Entries" in the Oracle Fusion Middleware Administrator's Guide for Oracle Internet Directory), you can also use the WLS Administration Console as described below.
Note:
If you are planning to reassociate your identity store with an external LDAP, carry out that step (as described in Section 14.3.1, "Reassociating the Identity Store with an External LDAP") prior to adding users to avoid having to migrate the users from the embedded LDAP to the newly configured external LDAP.For WebCenter Spaces, users who self-register are added directly to the identity store. For more information about self-registration, see Section 19.4, "Allowing Self-Registration".
You can also add users directly into the embedded LDAP identity store using an LDIF file and LDAP commands. Using an LDIF file lets you add additional attributes not available through the WLS Administration Console.
Note:
Adding users to the identity store is typically a system administrator task and may not be a task for which application-level administrators have the required permissions.This section includes the following subsections:
To add users to the embedded LDAP or to an external LDAP from the WLS Administration Console:
Log in to the WLS Administration Console.
For information on logging into the WLS Administration Console, see Section 1.12.2, "Oracle WebLogic Server Administration Console".
In the Domain Structure pane (see Figure 14-12), click Security Realms.
The Summary of Security Realms pane displays (see Figure 14-13).
Figure 14-13 Summary of Security Realms pane

In the Name column, click the realm to which you want to add users.
The Realm Settings pane displays (see Figure 14-14).
Click the Users and Groups tab to display the list of current users.
Click New to add a new user.
On the Create a New User page, enter the new user login name in the Name field.
User names are case sensitive and must be unique. Do not use commas, tabs or any other characters in the following comma-separated list:
< >, #, |, &, ?, ( ), { }
In the Description field, enter a description for the user (for example, the user's full name).
From the Provider drop-down menu, select the Authentication provider for the user.
If multiple WebLogic Authentication providers are configured in the security realm, they will appear in the list. For the embedded LDAP, choose DefaultAuthenticator; for Oracle Internet Directory, choose OracleInternetDirectoryAuthenticator. For other external LDAPs, choose the authenticator associated with that LDAP.
In the Password field, enter a password for the user.
The minimum password length for a user defined in the WebLogic Authentication provider is 8 characters (note that other LDAP providers may have different requirements for the password length). Do not use user name/password combinations such as weblogic/weblogic in a production environment.
Re-enter the password in the Confirm Password field.
Click OK to save your changes and add the user.
The user should now appear in the list of users.
To add users to the embedded LDAP using an LDIF file you need to carry out the following tasks:
The WLS Administration Console does not provide support for adding any additional attributes. However, the embedded LDAP server is in fact, a proper LDAP server, and so you can use LDAP commands to add or modify users. You can also search the directory, which can be useful when exporting and importing user accounts.
Enable External LDAP Access
When WLS is installed, the LDAP access credential is set as a randomized value and encrypted in the config.xml file. To enable external LDAP access, you need to reset the access credential for the embedded LDAP.
To reset the access credential for the embedded LDAP:
Log in to the WLS Administration Console.
For information on logging into the WLS Administration Console, see Section 1.12.2, "Oracle WebLogic Server Administration Console".
In the Domain Structure pane (see Figure 14-16), click on wc_domain.
Figure 14-16 Domain Structure Pane (wc_domain)
In the Settings pane for wc_domain, click the Security tab, and then click the Embedded LDAP tab.
The Settings Pane for wc_domain displays the embedded LDAP settings (see Figure 14-17).
Figure 14-17 Settings Pane with Embedded LDAP Settings
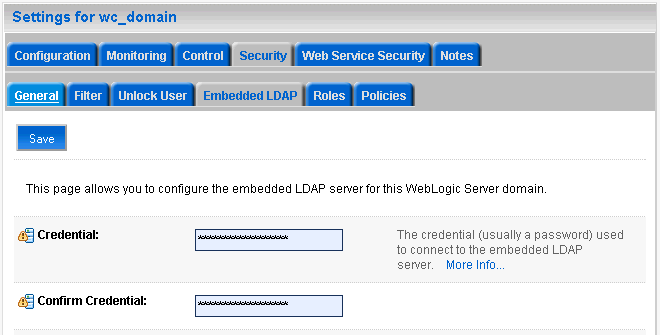
Enter a new password in the Credential field, and re-enter it in the Confirm Credential field.
Click Save to save your settings.
Restart the WebLogic server.
After this, you are ready to access the LDAP server with the following values:
the DN value for admin access is "cn=Admin"
the password is the value you entered in the Credential field
the port is the same as the admin port, which by default is 7001
Create an LDIF File
You can create an LDIF file with any text editor, and can include any attributes appropriate for the embedded LDAP directory. The objectclasses that are supported by default in the embedded LDAP server for WLS are the following:
person
inetOrgPerson
organizationalPerson
wlsUser
In order to interact successfully with the embedded LDAP server, you should understand the default layout of the directory information tree (DIT). The default layout in the embedded LDAP directory is shown in Figure 14-18.
Figure 14-18 Embedded LDAP Directory Information Tree
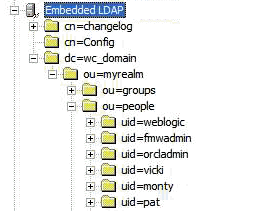
Note:
The naming attribute for the user entry in the embedded LDAP directory tree is "uid". This is different from the default configuration for Oracle Internet Directory (OID), where the naming attribute is "cn". Also, the location of the users in this tree is "ou=people,ou=myrealm,dc=wc_domain".The following example shows an LDIF file with the attributes that are displayed in the WebCenter Spaces Profile Details screen:
dn: uid=john.doe,ou=people,ou=myrealm,dc=wc_domain description: John Doe cn: john.doe uid: john.doe sn: Doe objectclass: wlsUser objectclass: organizationalperson objectclass: inetOrgPerson objectclass: person objectclass: top userpassword: welcome1 displayName: John Doe employeeNumber: 12345 employeeType: Regular givenName: John homePhone: 650-555-1212 mail: john.doe@example.com title: Manager manager: uid=mary.jones,ou=people,ou=myrealm,dc=wc_domain preferredLanguage: en departmentNumber: tools facsimiletelephonenumber: 650-555-1200 mobile: 650-500-1200 pager: 650-400-1200 telephoneNumber: 650-506-1212 postaladdress: 200 Oracle Parkway l: Redwood Shores homepostaladdress: 123 Main St., Anytown 12345
To create a file with multiple user entries, just replicate the above lines as many times as required, with a blank line between entries.
Note:
Note that the WebCenter Spaces Profile Details screen also lists some attributes that are only available in an Oracle Internet Directory. These cannot be entered when using the embedded LDAP identity store. These include the following attributes, from theorclUserV2 objectclass:
orclTimeZone
orclDateOfBirth
maidenName
Add the Users
The example below uses the ldappadd command, a part of the LDAP command line utilities provided with the Oracle Internet Directory server. For more information about using the ldappadd command, see "Oracle Internet Directory Data Management Tools" in the Oracle Fusion Middleware User Reference for Oracle Identity Management.
ldapadd -h weblogichost.example.com -p 7001 -D cn=Admin -w password -v -f newuser.ldif
add description:
John Doe
add cn:
john.doe
add uid:
john.doe
add sn:
Doe
add objectclass:
wlsUser
organizationalperson
inetOrgPerson
person
top
add userpassword:
password
add displayname:
John Doe
add employeenumber:
12345
add employeetype:
Regular
add givenname:
John
add homephone:
650-555-1212
add mail:
john.doe@example.com
add title:
Manager
add manager:
uid=mary.jones,ou=people,ou=myrealm,dc=wc_domain
add preferredlanguage:
en
add departmentnumber:
tools
add facsimiletelephonenumber:
650-555-1200
add mobile:
650-500-1200
add pager:
650-400-1200
add telephonenumber:
650-506-1212
add postaladdress:
200 Oracle Parkway
add l:
Redwood Shores
add homepostaladdress:
123 Main St., Anytown 12345
adding new entry uid=john.doe,ou=people,ou=myrealm,dc=wc_domain
modify complete
When configuring the domain to use an external LDAP server, you can also optionally move the administrator account (weblogic by default) to the LDAP server.
If the administrator account, or any other appropriate user in LDAP, is in an LDAP group called "Administrators", then this account should be sufficient to manage the server, and the DefaultAuthenticator provider can be removed from the list of authentication providers. In this case, all users and including the administrator account are looked up from the external LDAP.
If you cannot create the weblogic (default) user in the external LDAP directory, there are two options. You can:
Keep the DefaultAuthenticator provider and use the weblogic account with the local embedded LDAP server in WLS to start and stop servers and do other administrator operations from the WLS Administration Console. If you keep the DefaultAuthenticator, make sure that the control flag for the DefaultAuthentication provider is set to SUFFICIENT.
Remove the DefaultAuthenticator and make sure that any valid user account used for administrator operations, such as starting and stopping servers, is included in an "Administrators" group in Oracle Internet Directory or other named group that contains the list of users that are allowed to manage your domain. If a name other than "Administrators" is used, then you need to update the group name in the definition of the WLS Global Administrator role. By default, this is defined as membership in the enterprise group called "Administrators".
Changing the Administrator Group Name
You can change the group name to any other valid enterprise role in your LDAP server that contains users authorized to manage the domain. This lets you delegate the administration of specific domains in your enterprise. You can create various administration groups in the directory and have the corresponding domains be configured to use the appropriate group for defining its administrators.
The following example LDIF file creates an administrative group in Oracle Internet Directory:
dn: cn=wc_domain_Admin,cn=groups,dc=example,dc=com cn: wc_domain_Admin uniquemember: cn=joe.admin,cn=users,dc=example,dc=com owner: cn=orcladmin displayname: WebLogic Administrators Group description: WebLogic Administrators Group objectclass: orclgroup objectclass: groupofuniquenames
Once this group is created, you need to update the role definition for the WLS Global Admin role in WLS:
To update the role definition for the WLS Global Admin role in WLS
Log in to the WLS Administration Console.
For information on logging into the WLS Administration Console, see Section 1.12.2, "Oracle WebLogic Server Administration Console".
In the Domain Structure pane (see Figure 14-19), click Security Realms.
The Summary of Security Realms pane displays (see Figure 14-20).
Figure 14-20 Summary of Security Realms pane

In the Name column, click the realm for which you want to reassociate the identity store.
The Realm Settings pane displays (see Figure 14-21).
Open the Roles and Policies tab, and then the Realm Roles subtab.
The Realm Roles settings pane displays (see Figure 14-22).
Expand the Global Roles node, and then the Roles node.
Click View Role Conditions for the Admin role.
The Edit Global Role page displays (see Figure 14-23).
By default, the Administrators group in Oracle Internet Directory (or other configured identity store) defines who has the administrator role in WebLogic Server.
Click Add Conditions to add a different group name.
The Edit Global Role - Predicate List page displays (see Figure 14-24).
Figure 14-24 Edit Global Role Page - Predicate List
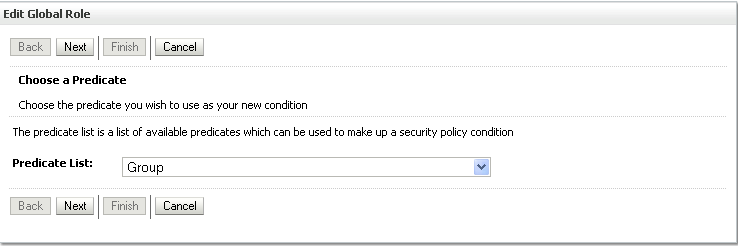
Select Group from the Predicate List list and click Next.
The Edit Global Role - Arguments page displays (see Figure 14-25).
Figure 14-25 Edit Global Role Page - Arguments
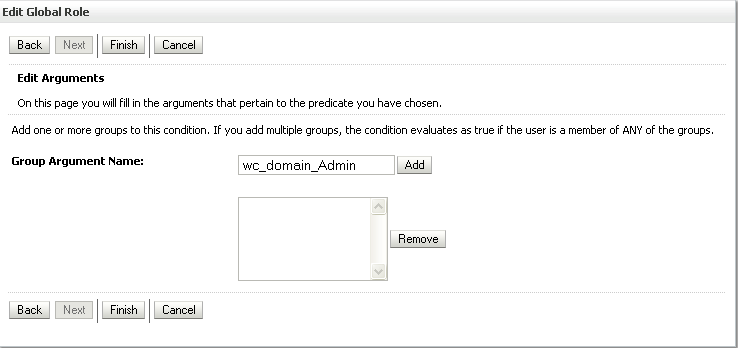
Enter the name for the new administrator group and click Add.
Select the pre-existing administrator group and click Remove to delete it leaving the new one you've selected in its place.
Click Finish to save your changes.
After making this change, any members of the new group specified will be authorized to administer WebLogic Server.
WebCenter Spaces only recognizes users in the identity store that is mapped by the first authenticator. Since the WebCenter Spaces Administrator account is initially created only in the embedded LDAP server, if an external LDAP such as Oracle Internet Directory is configured as the primary authenticator for WebCenter Spaces, you must also create a user in that LDAP and grant that user the WebCenter Spaces Administrator role. For more information, see "Granting Administrator Role to a Non-Default User" in the Oracle Fusion Middleware Installation Guide for Oracle WebCenter.
You can grant a user the WebCenter Administrator role using Fusion Middleware Control or WLST as shown below in the sections on:
This section describes how to grant the WebCenter Spaces administrator role to a user account other than the default "weblogic" account.
To grant the WebCenter Spaces Administrator role using Fusion Middleware Control:
Log into Fusion Middleware Control and select the WebLogic domain for WebCenter Spaces.
For information on logging into Fusion Middleware Control, see Section 6, "Starting Enterprise Manager Fusion Middleware Control".
From the WebLogic Domain menu, select Security -> Application Roles.
The Application Roles page displays (see Figure 14-26).
Search for the Administration application role by selecting the Application name for WebCenter Spaces (WLS_Spaces/webcenter), and providing the following internal identifier used by WebCenter Spaces as the Role Name:
s8bba98ff_4cbb_40b8_beee_296c916a23ed#-#Administrator
The search should return s8bba98ff_4cbb_40b8_beee_296c916a23ed#-#Administrator, which is the administrator role identifier.
Click the administrator role name (s8bba98ff_4cbb_40b8_beee_296c916a23ed#-#Administrator) in the Role Name column.
The Edit Application Role page displays (see Figure 14-27).
Click Add User.
The Add User pop-up displays (see Figure 14-28).
Use the Search function to search for the user to assign the Administrator role to.
Use the arrow keys to move the user from the Available Users column to the Selected Users column, and click OK.
On the Edit Application Role page, click OK.
After granting the WebCenter Spaces Administrator role to new accounts, remove this role from accounts that no longer need it or should no longer have it using the WLST revokeAppRole command described below. For example, if WebCenter Spaces was installed with a different administrator user name than "weblogic", the administrator role should be given to that user and should be revoked from the default "weblogic".
revokeAppRole(appStripe="webcenter", appRoleName="s8bba98ff_4cbb_40b8_beee_296c916a23ed#-#Administrator", principalClass="weblogic.security.principal.WLSUserImpl", principalName="weblogic")
Restart the WLS_Spaces managed server.
When you login to WebCenter Spaces, the Administration link should appear and you should be able to perform all administrator operations. See also, Section 17.1, "Logging into WebCenter Spaces as an Administrator".
To grant the WebCenter Administrator role using WLST:
Start WLST as described in Section 1.12.3.1, "Running Oracle WebLogic Scripting Tool (WLST) Commands".
Connect to the WebCenter Spaces Administration Server for the target domain with the following command:
connect('user_name','password, 'host_id:port')
Where:
user_name is the name of the user account with which to access the Administration Server (for example, weblogic)
password is the password with which to access the Administration Server
host_id is the host ID of the Administration Server
port is the port number of the Administration Server (for example, 7001).
Grant the WebCenter Spaces administrator application role to the user in Oracle Internet Directory using the grantAppRole command as shown below:
grantAppRole(appStripe="webcenter", appRoleName="s8bba98ff_4cbb_40b8_beee_296c916a23ed#-#Administrator",
principalClass="weblogic.security.principal.WLSUserImpl", principalName="wc_admin")
Where wc_admin is the name of the administrator account to create.
To test the new account, log into WebCenter Spaces using the new account name.
The Administration link should appear, and you should be able to perform all administrator operations. See also, Section 17.1, "Logging into WebCenter Spaces as an Administrator".
After granting the WebCenter Spaces Administrator role to new accounts, remove this role from accounts that no longer need it or should no longer have it. For example, if WebCenter Spaces was installed with a different administrator user name than "weblogic", the administrator role should be given to that user and should be revoked from the default "weblogic".
After installing Oracle Discussions, it must also be configured to use the same Identity Store as WebCenter Spaces. The Discussions server can be configured to use either the default embedded LDAP or an external LDAP server (such as Oracle Internet Directory Server) depending on the identity store used by WebCenter Spaces. The steps below describe how to configure Oracle WebCenter Discussions Server to share the same external LDAP server as the WebCenter Spaces identity store. For information on how to configure the Oracle WebCenter Discussions Server to use the same embedded LDAP server as the WebCenter Spaces identity store, see Section 14.3.7, "Configuring the Discussions Server to Share the Identity Store Embedded LDAP Server".
To configure the discussions server to share the same external LDAP server as the identity store:
Locate the jive_startup.xml file in your WebCenter installation (it can be found in MW_HOME/user_projects/domains/<my_domain>/config/fmwconfig/servers/WLS_Services/owc_discussions_11.1.1.1.0), and make a backup copy.
Change the line with the content:
<setup>true</setup>
to
<setup>false</setup>
Save the file and restart the WLS_Services managed server.
Connect to the Oracle WebCenter Discussions Server administration console at:
http://host:port/owc_discussions
where host and port are the host ID and port number of the WLS_Services managed server.
On the Database Settings page, choose JNDI Datasource, and click Continue.
On the Datasource Settings page, enter jdbc/OWC_DiscussionsDS as the JNDI Datasource Name, and click Continue.
On the User, Group and Authentication Systems page, choose LDAP and click Continue.
On the LDAP User System page, enter the LDAP values of the identity store and click Continue.
On the Other Settings page, check and correct the SMTP settings as appropriate for your WebCenter configuration and click Continue.
On the LDAP User Data Storage Mode page, specify a user in LDAP that should be set as the discussions server administrator (typically orcladmin), and click Continue.
The is the same administrator account as the one specified on the discussion connection. See also, Section 11.1, "Setting Up Connections for the Discussions and Announcements Services".
Restart the WLS_Services managed server.
After installing Oracle Discussions, it must also be configured to use the same Identity Store as WebCenter Spaces. The Discussions server can be configured to use either the default embedded LDAP or an external LDAP server (such as Oracle Internet Directory Server) depending on the identity store used by WebCenter Spaces. The steps below describe how to configure the Oracle WebCenter Discussions Server to use the embedded LDAP server used by the WebCenter Spaces identity store. For information on how to configure the Oracle WebCenter Discussions Server to share the same external LDAP server as the WebCenter Spaces identity store, see Section 14.3.6, "Configuring the Discussions Server to Share the Identity Store LDAP Server".
Follow the steps below to configure the Discussions server to use the embedded LDAP server:
To interact with the embedded LDAP server, you first need to set up the credential for external access as the admin user ("cn=Admin") as described under Enable External LDAP Access in the section "Adding Users to the Embedded LDAP Using an LDIF File" in the Oracle Fusion Middleware Administrator's Guide for Oracle WebCenter.
Continue by adding users to the embedded LDAP server using an LDIF file as described under Create an LDIF File and Add the Users in the same section. Be sure to add an email address (for example, mail: john.doe@example.com) for each user added.
Note:
Although you can add users to an LDAP server using the WLS Administration Console, Oracle Discussions requires that every user created has an associated email address, which can only be done through an LDIF file.Stop the Discussions server (WLS_Services by default).
Locate the jive_startup.xml file in your WebCenter installation (it can be found in MW_HOME/user_projects/domains/<my_domain>/config/fmwconfig/servers/WLS_Services/owc_discussions_11.1.1.1.0), and make a backup copy.
Change the line with the content:
<setup>true</setup>
to
<setup>false</setup>
Save the file and start the Discussions server (WLS_Services by default).
Log in to the Discussions Server Administration Console at:
http://host:port/owc_discussions/admin
where host and port are the host ID and port number of the WLS_Services managed server (the default port is 8890).
On the Installation Checklist page, click Continue.
On the Database Settings page, choose JNDI Datasource, and click Continue.
Enter jdbc/OWC_DiscussionsDS in the JNDI Datasource Name field and click Continue.
For User, Group and Authentication Systems, enter the values for the embedded LDAP system and click Continue.
For Other Settings, check that your email server settings are correct and click Continue.
For Admin Account Setup, enter the user name of the user for the Discussions (Jive) administrator.
Click Continue.
You can now log in to Oracle Discussions with any user available in the LDAP server at:
http://<host>:8890/owc_discussions
You can log in to the Oracle Discussions Admin Console at:
http://<host>:8890/owc_discussions/admin
Oracle Content Server (OCS) must be configured to use the same identity store LDAP server as Oracle WebCenter Spaces. For more information on configuring the OCS, see the section "Configuring the Identity Store Service" in the Oracle Fusion Middleware Security Guide.
Reassociating the policy and credential store with Oracle Internet Directory (OID) consists of creating a root node in the LDAP directory, and then reassociating the policy and credential store with the OID server using Fusion Middleware Control, or from the command line using WLST as described in the following sections:
The first step in reassociating the policy and credential store with OID, is to create an LDIF file in the LDAP directory and add a root node under which all data is added. After creating the file and adding the node, continue by reassociating the store using either Fusion Middleware Control or WLST.
To create a root node:
Create a root node by adding the following to an LDIF file (for example, root.ldif) in the LDAP directory:
dn: cn=root_webcenter_xxxx cn: root_webcenter_xxxx objectclass: top objectclass: orclcontainer
Where xxxx is a string (for example, the server name) that uniquely identifies the node.
Add this node to the directory by running the following LDAP command from your LDAP installation directory:
OID_HOME/as_1/bin/ldapadd -h ldap_host_name -p ldap_port -D cn=orcladmin -w password -v -f root.ldif
where:
OID_HOME is the directory in which LDAP is installed
ldap_host_name is the host name of the OID server
ldap_port is the OID server port number
password is the password with which to access the OID server
Note that each root container must have a unique name.
When initially installed, WebCenter Spaces and Enterprise Manager are already associated and deployed in the same domain.
Before reassociating the policy and credential store with Oracle Internet Directory, you must first have created the root node as described in Section 14.4.1, "Creating a root Node."
To reassociate the policy and credential store with the OID server:
Open Fusion Middleware Control and log into your target instance.
For information on logging into Fusion Middleware Control, see Section 6, "Starting Enterprise Manager Fusion Middleware Control".
In the Navigation pane, click your domain.
From the WebLogic Domain menu, select Security and then Security Provider Configuration.
The Security Provider Configuration page displays (see Figure 14-29).
Figure 14-29 Security Provider Configuration Page
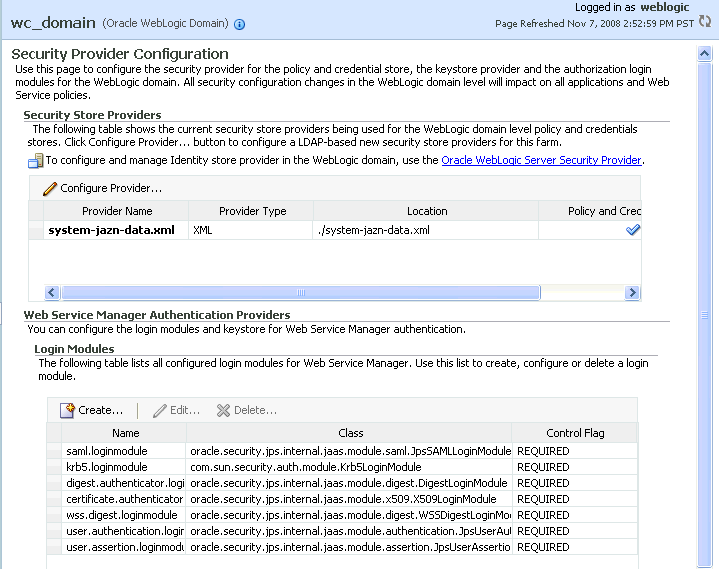
On the Security Provider Configuration page, click Configure... to add the new Oracle Internet Directory provider.
The Set Security Provider page displays (see Figure 14-30).
Under LDAP Server Details, select Oracle Internet Directory as the LDAP Server Type.
In the Host and Port fields, enter the host name and the LDAP port for Oracle Internet Directory.
Set the User DN field to cn=orcladmin, and enter the associated password in the Password field.
Under JPS Root Node Details, set the JPS Root DN field to the one you added to the root.ldif file (for example, cn=root_webcenter_abcd99). Be sure to include the cn=.
Click OK to begin the reassociation. Restart the WebLogic server when prompted after migration.
Before reassociating the policy and credential store with Oracle Internet Directory, you must first have created the root node as described in Section 14.4.1, "Creating a root Node".
Start WLST as described in Section 1.12.3.1, "Running Oracle WebLogic Scripting Tool (WLST) Commands".
Connect to the Administration Server for the target domain with the following command:
connect('username>,'password', 'host_id:port')
where:
username is the administrator account name used to access the Administration Server (for example, weblogic)
password is the administrator password used to access the Administration Server (for example, weblogic)
host_id is the server ID of the Administration Server (for example, example.com)
port is the port number of the Administration Server (for example, 7001).
Reassociate the policy and credential store using the reassociateSecurityStore command:
reassociateSecurityStore(domain="domain_name", admin="admin_name", password="password", ldapurl="ldap_uri", servertype="ldap_srvr_type", jpsroot="root_webcenter_xxxx")
Where:
domain_name specifies the domain name where reassociation takes place.
admin_name specifies the administrator's user name on the LDAP server. The format is cn=usrName.
password specifies the password associated with the user specified for the argument admin.
ldap_uri specifies the URI of the LDAP server. The format is ldap://host:port, if you are using a default port, or ldaps://host:port, if you are using a secure LDAP port. The secure port must have been configured to handle an anonymous SSL connection, and it is distinct from the default (non-secure) port.
ldap_srvr_type specifies the kind of the target LDAP server. Valid types are OID (Oracle Internet Directory) or OVD (Oracle Virtual Directory).
root_webcenter_xxxx specifies the root node in the target LDAP repository under which all data is migrated. Be sure to include the cn=. The format is cn=nodeName.
All arguments are required. For example:
reassociateSecurityStore(domain="myDomain", admin="cn=adminName", password="myPass", ldapurl="ldaps://myhost.example.com:3060", servertype="OID", jpsroot="cn=testNode")
WebCenter Spaces provides a Users tab from which an administrator can add users defined in the identity store, and assign roles to those users within WebCenter Spaces. For information about managing users and user roles for WebCenter Spaces, see Chapter 19, "Managing Users and Roles for WebCenter Spaces ".
Caution:
The "Allow Password Change" property, which specifies whether users can change their passwords within WebCenter Spaces, should be carefully controlled for corporate identity stores. WebCenter Spaces administrators can set this property from the Profile Management Settings page in WebCenter Spaces. For more information, see Section 18.9, "Managing Personal Profiles".The user interface and management tools with which to manage users and user roles for custom WebCenter applications depends on what has been implemented for the particular deployment. For more information about role-mapping for ADF-security based WebCenter applications, see the section What You May Need to Know About Application Roles and Enterprise Roles in the Oracle Fusion Middleware Fusion Developer's Guide for Oracle Application Development Framework.
This section includes the following sub-sections:
Securing the Browser Connection to WebCenter Spaces with SSL
Securing the Browser Connection to a Custom WebCenter Application with SSL
Securing the Connection from Oracle HTTP Server to WebCenter Spaces with SSL
Securing the Browser Connection to the Wiki Service with SSL
Securing the WebCenter Spaces Connection to Portlet Producers with SSL
Securing the WebCenter Spaces Connection to the LDAP Identity Store
Securing the WebCenter Spaces Connection to IMAP and SMTP with SSL
Securing the WebCenter Spaces Connection to Oracle SES with SSL
Securing the WebCenter Spaces Connection to Microsoft Live Communication Server with SSL
Note:
The following can use WS-Security with message protection, and consequently have no hard requirement for SSL:BPEL servers - Worklist service
WSRP Producers
Oracle WebLogic Communication Services (OWLCS) - IMP service
Microsoft Live Communication Server (LCS) - IMP service
Oracle WebCenter Discussions - Discussions and Announcements
Securing the browser connection to WebCenter Spaces with SSL consists of the following steps:
The first step is to generate a custom keystore for WebCenter Spaces.
To create a custom keystore:
Go to JAVA_HOME/bin/ and open a command prompt.
Using keytool, generate a key pair:
keytool -genkeypair -keyalg RSA -dname "dname" -alias alias-keypass key_password -keystore keystore -storepass keystore_password-validity days_valid
Where:
dname is the DN (distinguished name) to use (for example, cn=customidentity,dc=example,dc=com)
alias is the alias to use (for example, webcenter_wls)
key_password is the password for the new public key, (for example, welcome1)
keystore is the keystore name, (for example, webcenter_wls.jks)
keystore_password is the keystore password, (for example, welcome1)
days_valid is the number of days for which the key password is valid (for example, 360).
Note:
You must use the-keyalg parameter and specify RSA as its value as shown above as the default algorithm (DSA) used by keytool for generating the key is incompatible with Oracle WebServices Security Manager requirements.Export the certificate containing the public key so WebCenter Spaces clients can import it into their trust store:
keytool -exportcert -v -alias alias -keystore keystore-storepass keystore_password -rfc -file certificate_file
Where:
alias is the WebCenter Spaces alias (for example, webcenter_wls)
keystore is the keystore name, (for example, webcenter_wls.jks)
keystore_password is the keystore password, (for example, welcome1)
certificate_file is the file name for the certificate to export the key to (for example, webcenter_wls.cer)
Determine the trust store to use:
Since you are using a self-signed certificate, you must update it as a trusted certificate in the server trust store. To do this, you must determine your trust store by going to the server:
Log into the WLS Administration Console.
In the Domain Structure pane, expand Environments and click Servers.
In the list of servers, click WLS_Spaces.
Open the Configuration tab, and the Keystores subtab.
The Keystores Settings pane displays (see Figure 14-31).
Note down the location of the server in the Java Standard Trust Keystore field (shown in Figure 14-31).
Note that the cacerts file may be "read only", in which case you will need to change it's permissions so that it's writable.
Import the self-signed certificate generated above in this trust store:
keytool -importcert -trustcacerts -alias alias -file certificate_file-keystore cacerts -storepass changeit
Where:
alias is the WebCenter Spaces alias (for example, webcenter_wls)
certificate_file is the file name for the certificate to export the key to (for example, webcenter_wls.cer)
The next step is to configure the identity and trust keystores on the WebCenter Spaces server.
To configure the identity and trust keystores:
Log in to the WLS Administration Console.
For information on logging into the WLS Administration Console, see Section 1.12.2, "Oracle WebLogic Server Administration Console".
In the Domain Structure pane, expand Environment and click Servers.
The Summary of Servers pane displays (see Figure 14-32).
Click the WebCenter Spaces server (WLS_Spaces) to configure the identity and trust keystores.
The Settings pane for the WebCenter Spaces server displays (see Figure 14-33).
Figure 14-33 Settings Pane for WebCenter Spaces Server
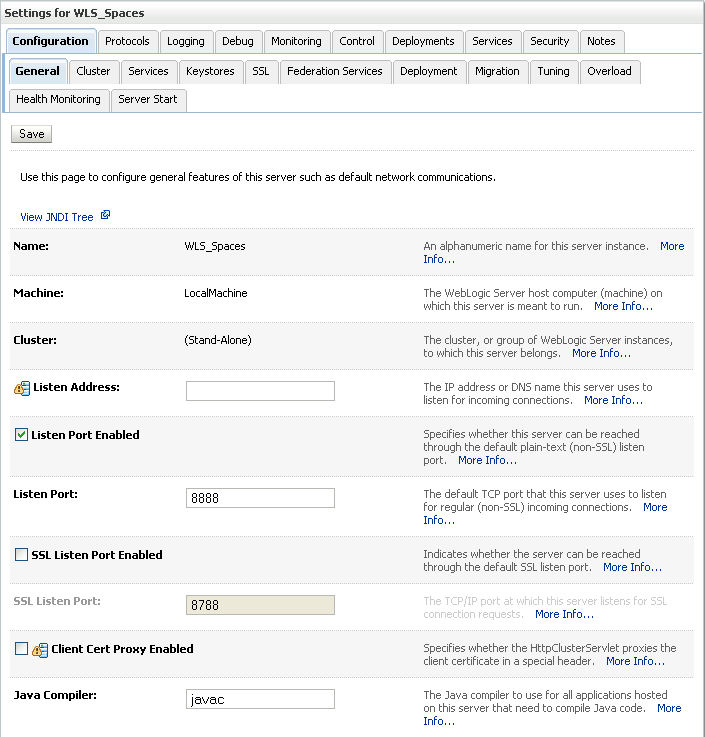
Open the Configuration tab, and then the Keystores subtab.
The Keystores pane displays (see Figure 14-34).
For Keystores, select Custom Identity and click Save.
Enter the path of the custom identity store in the Java Standard Trust Keystore field.
Enter jks as the Java Standard Trust Keystore Type.
Enter and confirm the Java Standard Trust Keystore.
Click Save to save your entries.
Open the SSL tab.
Enter the Private Key Alias.
Enter the Private Key Passphrase.
Click Save to save your entries.
To configure the SSL connection:
On the Settings pane for the WebCenter Spaces server, open the Configuration tab and then the General subtab.
The General Configuration pane displays (see Figure 14-35).
Check SSL Listen Port Enabled.
Enter an SSL Listen Port number and click Save.
Open the SSL subtab and expand the Advanced options at the bottom of the page.
The SSL advanced options are displayed (see Figure 14-36).
Figure 14-36 Advanced SSL Configuration Settings
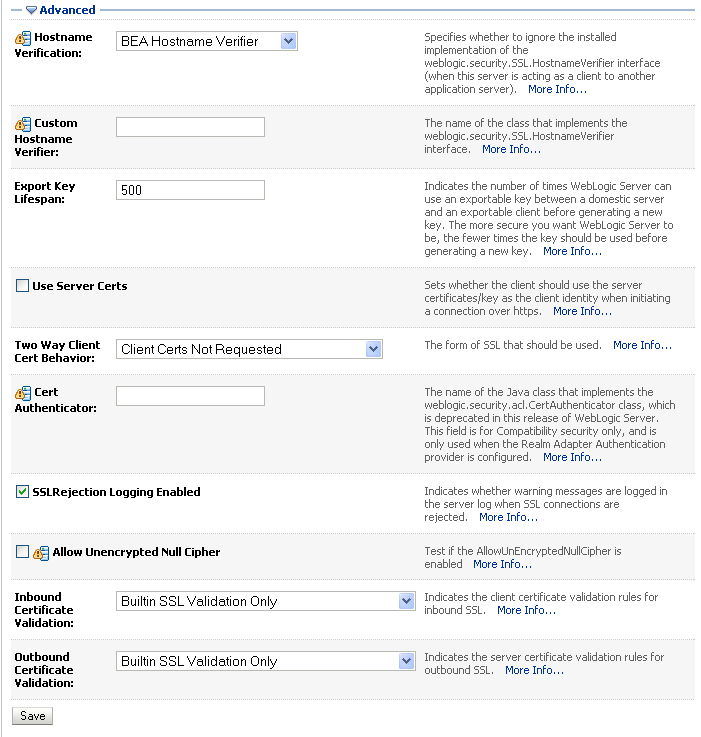
Set the Two Way Client Cert Behavior option to Client Certs Not Requested and click Save.
Open the Control tab.
The Control Settings pane displays (see Figure 14-37).
Click Restart SSL.
Restart the WebLogic Server and open the SSL WebCenter Spaces URL.
Accept the certificate for the session and log in.
Securing the browser connection to a custom WebCenter application uses the same configuration steps as for securing the browser connection to WebCenter Spaces. The only difference is that the configuration occurs on the managed server that is hosting the custom WebCenter application deployment rather than the WLS_Spaces server. For more information, see Section 14.6.1, "Securing the Browser Connection to WebCenter Spaces with SSL".
Securing the connection between the Oracle HTTP Server (OHS) and WebCenter Spaces consists of these steps:
Configure the Identity and Trust Keystores
For instructions on how to configure the Identity and Trust keystores, see Section 14.6.1, "Securing the Browser Connection to WebCenter Spaces with SSL".
Configure the SSL Connection
On the Settings pane for the WebCenter Spaces server, open the Configuration tab and then the General subtab.
The General Configuration pane displays (see Figure 14-38).
Check SSL Listen Port Enabled.
Enter an SSL Listen Port number and click Save.
On the Configuration tab, open the SSL subtab, and then expand the Advanced options at the bottom of the page.
The SSL advanced options are displayed (see Figure 14-39).
Figure 14-39 Advanced SSL Configuration Settings

Set the Two Way Client Cert Behavior option to Client Certs Not Requested and click Save.
Open the Control tab on the Settings pane, and select the Start/Stop subtab.
Click Restart SSL.
Open the SSL WebCenter Spaces URL.
Accept the certificate for the session and log in.
In the WSL Administration Console, click View Changes and Restarts on the Change Center pane and restart any affected servers or components.
Install OHS
Install the WebTier.
Do not select WebCache; only select the HTTP Server.
Uncheck the checkbox to associate a WebLogic server during install.
Navigate to the OHS_HOME/instances/instance1/bin directory and start OHS using the following command:
./opmnctl startall
Check the status of OHS using the following command:
./opmnctl status -l
Wire WebCenter Spaces Ports to OHS
Open the file OHS_HOME/instances/instance1/config/OHS/ohs1/mod_wl.conf
Add the following entry to mod_wl.conf to make WebCenter Spaces work with OHS:
<IfModule mod_weblogic.c>
WebLogicHost host_id
WebLogicPort port
Debug OFF
WLLogFile /tmp/ohs.log
MatchExpression *.jsp
</IfModule>
<Location />
SetHandler weblogic-handler
</Location>
Replacing host_id and port with the WebCenter Spaces server ID and port number.
Open the file OHS_HOME/instances/instance1/config/OHS/ohs1/mod_ssl.conf.
Add the following entry to mod_ssl.conf to make WebCenter Spaces run on the OHS SSL port:
<IfModule mod_weblogic.c>
WebLogicHost host_id
WebLogicPort port
WLLogFile /tmp/ohs_ssl.log
Debug OFF
DebugConfigInfo ON
SecureProxy ON
MatchExpression *.jsp
WlSSLWallet SSL_wallet
</IfModule>
<Location />
SetHandler weblogic-handler
</Location>
Replacing host_id and port with the WebCenter SSL server ID and port number, and SSL_wallet with the path to the WebLogic SSL wallet (for example, OHS_HOME>/oracle/product/11.1.1/as_1/instances/instance1/config/OHS/ohs1/keystores/default).
Go to OHS_HOME>/instances/instance1/bin and start and check the status of OHS using the following commands:
./opmnctl stopall ./opmnctl startall ./opmnctl status -l
Configure the SSL Certificates
For OHS to trust WebCenter's certificate, the WLS_Spaces certificate must be imported into the OHS trust store. Export the certificate from the WLS_Spaces identity keystore:
keytool -exportcert -v -alias webcenter_wls -keystore webcenter_wls.jks -storepass <password> -rfc -file webcenter_wls.cer
Import the certificate into the wallet on the OHS side using orapki:
orapki wallet add -wallet . -trusted_cert -cert webcenter_wls.cer -auto_login_only
For WebCenter to trust OHS certificates, export the user certificate from OHS wallet and import it as a trusted certificate in the WebLogic trust store.
orapki wallet export -wallet . -cert cert.txt -dn 'CN=\"Self-signed Certificate for ohs1 \",OU=EXAMPLEORGUNIT,O=EXAMPLEORG,L=EXAMPLELOCATION,ST=CA,C=US'
Import the above certificate into the WLS_Spaces managed server trust store available in /scratch/wcwlsinstall/0408/wlshome/jrockit_160_05_R27.6.2-20/jre/lib/security/cacerts:
keytool -file cert.txt -importcert -trustcacerts -alias ohs_cert -keystore cacerts -storepass changeit
Restart OHS and the WLS_Spaces server.
You should now be able to access the SSL OHS, as well as the non-SSL OHS.
As with securing the browser connection to WebCenter Spaces, securing the Wiki service connection with SSL consists of two steps:
Configure the identity and trust keystores
Log in to the WLS Administration Console.
For information on logging into the WLS Administration Console, see Section 1.12.2, "Oracle WebLogic Server Administration Console".
In the Domain Structure pane, expand Environment and click Servers.
The Summary of Servers pane displays (see Figure 14-40).
Click the Services server (WLS_Services) to configure the identity and trust keystores.
The Settings pane for the services server displays (see Figure 14-41).
Figure 14-41 Settings Pane for Services Server
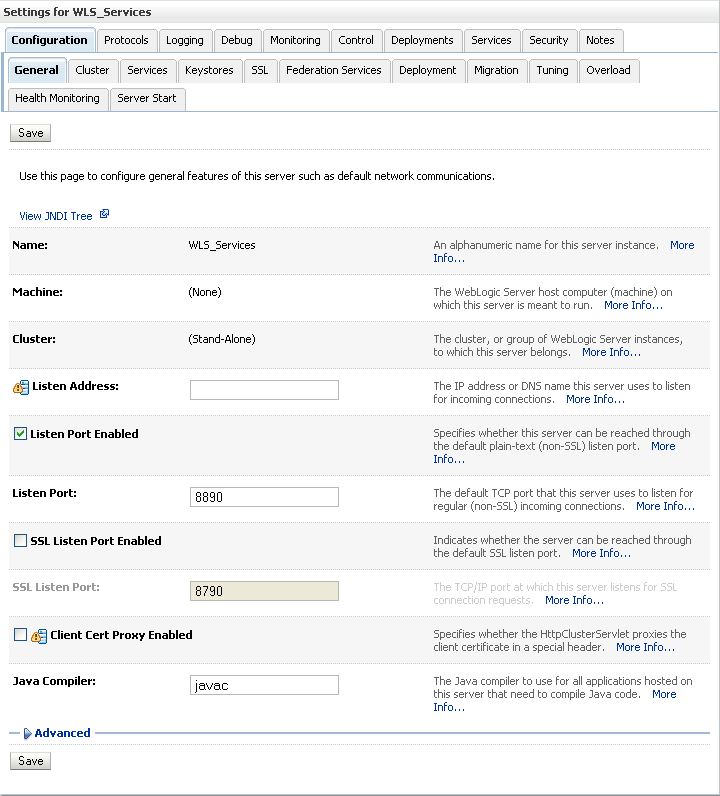
Open the Configuration tab, and then the Keystores subtab.
The Keystores pane displays (see Figure 14-42).
For Keystores, select Custom Identity and Java Standard Trust and click Save.
Open the Control tab.
The Control Settings pane displays (see Figure 14-43).
Click Restart SSL.
Configure the SSL connection
On the Settings pane for the Services server, open the Configuration tab and then the General subtab.
The General Configuration pane displays (see Figure 14-44).
Check SSL Listen Port Enabled.
Enter an SSL Listen Port number and click Save.
On the Configuration tab, open the SSL subtab, and then expand the Advanced options at the bottom of the page.
The SSL advanced options are displayed (see Figure 14-45).
Figure 14-45 Advanced SSL Configuration Settings

Set the Two Way Client Cert Behavior option to Client Certs Not Requested and click Save.
Restart the WLS_Services server and open the SSL Wiki URL at https://host:port/owc_wiki.
Accept the certificate for the session and log in.
Securing the connection to WSRP and PDK-Java portlet producers with SSL consists of the following steps:
Configure the identity and trust keystores
Log in to the WLS Administration Console.
For information on logging into the WLS Administration Console, see Section 1.12.2, "Oracle WebLogic Server Administration Console".
In the Domain Structure pane, expand Environment and click Servers.
The Summary of Servers pane displays (see Figure 14-46).
Click the Portlet server (for example, WLS_Portlet) to configure the identity and trust keystores.
The Settings pane for the Portlet server displays (see Figure 14-47).
Figure 14-47 Settings Pane for Portlet Server

Open the Configuration tab, and then the Keystores subtab.
The Keystores pane displays (see Figure 14-48).
For Keystores, select Custom Identity and Java Standard Trust and click Save.
Open the Control tab.
The Control Settings pane displays (see Figure 14-49).
Click Restart SSL.
Configure the SSL connection
In the Domain Structure pane, expand Environment and select Servers.
Click on the Portlet server (for example, WLS_Portlet) for which you want to configure SSL.
Select Configuration.
Check SSL Listen Port Enable.
Enter a listen port number.
Select Configuration > SSL, and then open the Advanced options at the bottom of the page.
Select the Two Way Client Cert Behavior attribute and choose the Client Certs Not Requested option.
Click Save.
Restart the WebLogic Server and open the SSL URL.
Accept the certificate for the session and log in.
Register the SSL-enabled WSRP producer and run the portlets
Configure the WebCenter Spaces managed server to use the Custom Identity and Java Standard Trust store. This also uses the certificates in javahome/jre/lib/security/cacerts.
Download the certificate of the HTTPS producer URL and save it in .PEM format.
Use Firefox 3.0 or later to download the certificate directly to .PEM format, or for other browsers use the WLS der2pem tool to convert to PEM format. For more information about using the der2pem tool, see "der2pem" in the Oracle Fusion Middleware Command Reference for Oracle WebLogic Server. Note that WebLogic does not recognize any other format other than .PEM format.
Import the certificate into the cacerts file in JAVAHOME/jre/lib/security using the following keytool command:
keytool -importcert -alias portlet_cert -file HOME/portlet_pem -keystore ./cacerts -storepass password
Where:
portlet_cert is the portlet certificate alias
portlet_pem is the portlet certificate file (for example, portlet_cert.pem)
password is the keystore password
Restart WLS_Spaces.
Start WLST as described in Section 1.12.3.1, "Running Oracle WebLogic Scripting Tool (WLST) Commands"
Connect to the Administration Server for the target domain with the following command:
connect('user_name','password, 'host_id:port')
Where:
user_name is the name of the user account with which to access the WLS_Spaces server (for example, weblogic)
password is the password with which to access the WLS_Spaces server
host_id is the host ID of the Administration Server
port is the port number of the Administration Server (for example, 7001).
Run the registerWSRPProducer WLST command to register the producer:
registerWSRPProducer('webcenter', 'sslwsrpprod','producer_wsdl)
Where:
sslwsrpprod is the name of the SSL-enabled WSRP producer
producer_wsdl is the WSDL URL of the SSL-enabled WSRP producer
For example:
registerWSRPProducer('webcenter', 'sslwsrpprod','https://example.oracle.com:7004/richtextportlet/portlets/wsrp2?WSDL')
Navigate to the HTTP or HTTPS WebCenter URL.
Create a page and go to the Portlets link.
Go to the registered WSRP producer.
Add the portlet to the page.
Go to the view mode of the page and check that the WSRP portlet renders correctly.
Register the SSL-enabled PDK-Java Producer and run the portlets
Configure the WebCenter Spaces managed server to use the Demo Identity and Trust store. This also uses the certificates in javahome/jre/lib/security/cacerts.
Log in to the WLS Administration Console.
For information on logging into the WLS Administration Console, see Section 1.12.2, "Oracle WebLogic Server Administration Console".
On the Domain Structure pane, expand Environment and click Servers.
The Summary of Servers pane displays (see Figure 14-50).
Click WLS_Spaces in the servers list.
The Settings pane displays (see Figure 14-51).
Figure 14-51 Settings Pane (WLS_Spaces Server)
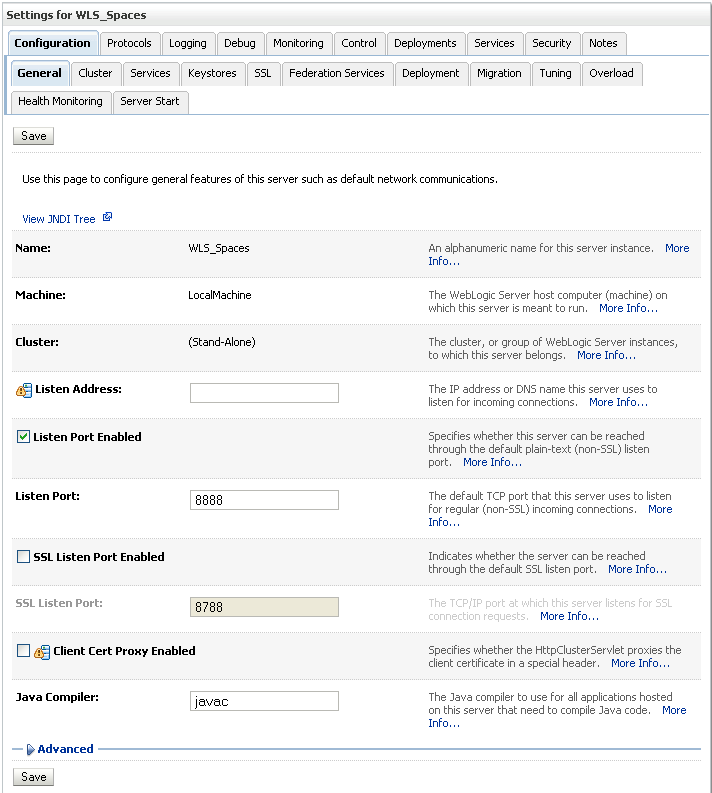
Open the Configuration tab and select the Keystores tab.
Make sure that the value for Demo Identity and Demo Trust is either jks or left blank.
Click Save.
Download the certificate of the HTTPS producer URL and save it in .PEM format.
Use Firefox 3.0 or later to download the certificate directly to .PEM format, or for other browsers use the WLS der2pem tool to convert to PEM format. For more information about using the der2pem tool, see "der2pem" in the Oracle Fusion Middleware Command Reference for Oracle WebLogic Server. Note that WebLogic does not recognize any other format other than .PEM format.
Import the certificate into the cacerts file in JAVAHOME/jre/lib/security using the following keytool command:
keytool -importcert HOME/portlet_cert.pem -keystore ./cacerts -storepass changeit
Restart WLS_Spaces.
Start WLST as described in Section 1.12.3.1, "Running Oracle WebLogic Scripting Tool (WLST) Commands".
Connect to the Administration Server for the target domain with the following command:
connect('user_name','password, 'host_id:port')
where:
user_name is the name of the user account with which to access the WLS_Spaces server (for example, weblogic)
password is the password with which to access the WLS_Spaces server
host_id is the host ID of the Administration Server
port is the port number of the Administration Server (for example, 7001).
Run the registerPDKJavaProducer command:
registerPDKJavaProducer('webcenter', 'ssljpdkprod', 'producer_wsdl')
Where:
ssljpdkprod is the name of the SSL-enabled PDK-Java producer
producer_wsdl is the WSDL URL of the SSL-enabled PDK-Java producer
This will enable one-way SSL for a Web producer. That is, only the server side (web producer) uses certificates. The Web producer code also uses a shared key feature (discussed later) for client authentication.
Go to the HTTP or HTTPS WebCenter URL.
Create a page and go to the Portlets link.
Go to the registered PDK-Java producer.
Add the portlet to the page.
Go to the view mode of the page and check that the PDK-Java portlet renders correctly.
To configure the LDAP server port for SSL, refer to the appropriate administration documentation for the LDAP server. For Oracle Internet Directory (OID), an SSL port is installed by default. To use this port for LDAP communication from WebCenter, the identity store should be configured for authentication with the appropriate authenticator. See Section 14.3, "Configuring the Identity Store" for the steps to do this for the identity store.
Note:
When entering the Provider Specific information, be sure to specify an SSL port and to check the SSL Enabled checkbox.If the CA is unknown to the Oracle WebLogic server, complete the two additional steps described in the following subsections:
For more information, see "Setting Up a One- Way SSL Connection" in the Oracle Fusion Middleware Security Guide.
If the CA is unknown to the Oracle WebLogic server (the command prompts the user to enter the keystore password) you will need to use orapki to create a certificate. The following example shows how to use this command to create the certificate serverTrust.cert:
orapki wallet export -wallet CA -dn "CN=myCA" -cert oid_server_trust.cert
If the CA is unknown to the Oracle WebLogic server, use the utility keytool to import the Oracle Internet Directory's CA into the WebLogic trust store. The following example shows how to use keytool to import the file oid_server_trust.cert into the server trust store cacerts:
keytool -importcert -v -trustcacerts -alias oid_server_trust -file oid_server_trust.cer -keystore cacerts -storepass changeit
For instructions on how to configure Oracle Content Server (OCS) for SSL, see Section 10.2.1.2.3, "Configuring Secure Socket Layer (SSL)". For instructions on adding a trusted certificate to the WebCenter Spaces trust store, see the section on importing the certificate into the trust store in Section 14.6.1.2, "Configuring the Identity and Trust Keystores".
Before associating you need to first import the certificate into the trust store. Follow the steps below to put the certificate in the trust store and configure WebCenter Spaces to use the trust store.
To secure the WebCenter Spaces connection to IMAP and SMTP with SSL:
Open a browser and connect to your IMAP server with the following command:
https://imapserver:ssl_port
For example:
https:mailserver.example:993
Place your cursor on the page, right-click, and select Properties.
Click Certificate.
In the popup window, click the Details tab and click Copy to File...
Be sure to use the DER encoded binary(X.509) format and copy to a file.
Convert the .DER format certificate to .PEM format.
Use Firefox 3.0 or later to download the certificate directly to.PEM format, or for other browsers use the WLS der2pem tool to convert to PEM format. For more information about using the der2pem tool, see "der2pem" in the Oracle Fusion Middleware Command Reference for Oracle WebLogic Server. Note that WebLogic does not recognize any other format other than .PEM format.
Import the certificate into the cacerts in the jdk_home using the following command:
keytool -import -alias imap_cer -file cert_file.cer -keystore cacerts -storepass changeit
Where cert_file is the name of the certificate file you downloaded.
Register the mail server connection as described in Section 11.3.3, "Registering Mail Servers".
Restart Webcenter Spaces.
Log into WebCenter Spaces and provide your mail credentials.
Before associating you need to first import the certificate into the trust store. Follow the steps below to put the certificate in the trust store and register the Oracle Secure Enterprise Search (SES) connection.
To download the certificate of the HTTPS URL and save it:
Use your browser to navigate to the Web Services URL that Oracle Secure Enterprise Search exposes to enable search requests at:
http://host:port/search/query/OracleSearch
For example:
https://example.com:7777/search/query/OracleSearch
Place your cursor on the page, right-click with your mouse, and select Properties.
Click Certificate.
In the popup window, open the Details tab, and click Copy to File...
Use DER encoded binary(X.509) format and copy the certificate to a file.
Convert the .DER format certificate to .PEM format.
Use Firefox 3.0 or later to download the certificate directly to.PEM format, or for other browsers use the WLS der2pem tool to convert to PEM format. For more information about using the der2pem tool, see "der2pem" in the Oracle Fusion Middleware Command Reference for Oracle WebLogic Server. Note that WebLogic does not recognize any other format other than .PEM format.
Import the certificate into DemoTrustKeyStore.jks or cacerts in the jdk_home using one of the following commands:
keytool -import -alias ses_cer -file cert_file.cer -keystore cacerts -storepass changeit
where cert_file is the name of the certificate file you downloaded.
Register the SES connection as described in Section 11.4.3, "Registering Oracle Secure Enterprise Search Services".
Restart WebCenter Spaces.
To secure the WebCenter Spaces connection to Oracle WebLogic Communication Services (OWLCS) with SSL, follow the steps below to import the certificate into the truststore, and point WebCenter Spaces to use the truststore. Note that securing the WebCenter Spaces connection to OWLCS with SSL is optional since OWLCS can be configured with confidentiality using WS-Security. See Section 14.8.3, "Securing Oracle WebLogic Communication Services (OWLCS) with WS-Security".
Before associating you need to first import the certificate into the truststore. Follow the steps below to put the certificate in the truststore:
Open your browser and go to the OWLCS server (for example, https://example.com:port/PresenceConsumerService/services/PresenceConsumer)
Place your cursor on the page, right-click, and select Properties.
Click Certificate.
In the popup window, open the Details tab and click Copy to File...
Use Firefox 3.0 or later to download the certificate directly to.PEM format, or for other browsers use the WLS der2pem tool to convert to PEM format. For more information about using the der2pem tool, see "der2pem" in the Oracle Fusion Middleware Command Reference for Oracle WebLogic Server. Note that WebLogic does not recognize any other format other than .PEM format.
Import the certificate into the cacerts using the following keytool command:
keytool -import -alias owlcs_cer -file cert_file.cer -keystore cacerts -storepass changeit
where cert_file is the name of the certificate file you downloaded.
Locate the cacerts file used by the OWLCS server in the OWLCS installation, and also update the OWLCS referenced cacerts file with this certificate:
keytool -import -alias owlcs_cer -file cert_file.cer -keystore cacerts -storepass changeit
Register the Oracle WebLogic Communication Services connection as described in Section 11.2.3, "Registering Instant Messaging and Presence Servers".
Restart the WebCenter Spaces server.
To secure the WebCenter Spaces connection to Microsoft Live Communication Server with SSL, follow the steps below to import the certificate into the truststore, and point WebCenter Spaces to use the truststore. Note that securing the WebCenter Spaces connection to Microsoft Live Communication Server with SSL is optional since Microsoft Live Communication Server can be configured with confidentiality using WS-Security.
Before associating you need to first import the certificate into the truststore. Follow the steps below to put the certificate in the truststore:
Open your browser and go to the Microsoft Live Communication Server (for example, https://example.com:port/PresenceConsumerService/services/PresenceConsumer)
Place your cursor on the page, right-click, and select Properties.
Click Certificate.
In the popup window, open the Details tab and click Copy to File...
Use Firefox 3.0 or later to download the certificate directly to.PEM format, or for other browsers use the WLS der2pem tool to convert to PEM format. For more information about using the der2pem tool, see "der2pem" in the Oracle Fusion Middleware Command Reference for Oracle WebLogic Server. Note that WebLogic does not recognize any other format other than .PEM format.
Import the certificate into the cacerts using the following keytool command:
keytool -import -alias lcs_cer -file cert_file.cer -keystore cacerts -storepass changeit
where cert_file is the name of the certificate file you downloaded.
Locate the cacerts file used by the Microsoft Live Communication Server in the Microsoft Live Communication Server installation, and also update the Microsoft Live Communication Server referenced cacerts file with this certificate:
keytool -import -alias lcs_cer -file cert_file.cer -keystore cacerts -storepass changeit
Register the Microsoft Live Communication Server connection as described in Section 11.2.3, "Registering Instant Messaging and Presence Servers".
Restart the WebCenter Spaces server.
Oracle Access Manager (OAM), part of Oracle's enterprise class suite of products for identity management and security, provides a wide range of identity administration and security functions, including several single sign-on options for WebCenter Spaces and custom WebCenter applications. OAM is the recommended single sign-on solution for Oracle WebCenter 11g installations.
For deployment environments that are already invested in Oracle 10g infrastructure, and where the Oracle Application Server Single Sign-On (OSSO) server is used as the primary SSO solution, WebCenter 11g can also be configured to use OSSO for single sign-on.
For smaller scale Oracle WebCenter 11g installations, where you do not have an enterprise-class single sign-on infrastructure like Oracle Access Manager or Oracle SSO, and you only need to provide a single sign-on capability within WebCenter Spaces and its associated web applications like Wiki, Discussions, RSS and Worklist, you can configure a SAML-based SSO solution. If you need to provide single sign-on with other enterprise applications, this solution is not recommended.
If your enterprise uses Microsoft desktop logins that authenticate with a Microsoft domain controller with user accounts in Active Directory, then configuring SSO with Microsoft Clients may also be an option to consider.
The setup required for each of these SSO solutions is described in the following subsections:
Oracle Access Manager (OAM) provides flexible and extensible authentication and authorization, and provides audit services. This section describes how to configure WebCenter Spaces and custom WebCenter applications for OAM single sign-on authentication, including how to configure the WebLogic server side and the WebCenter application as the partner application participating in SSO.
Much of the configuration can be done using scripts (recommended). To use the scripts, follow the instructions in Section 14.7.1.2, "Configuring OAM Using Scripts," and complete the instructions in Section 14.7.1.3, "Configuring the Webtier Components" and Section 14.7.1.6, "Configuring the Policy Manager," and any additional configurations as appropriate in Section 14.7.1.7, "Additional Configurations."
To perform the configuration manually, complete the instructions in all of the subsections, with the exception of Section 14.7.1.2, "Configuring OAM Using Scripts."
The scripted and equivalent manual configuration steps are presented in the following subsections:
Figure 14-52 shows the components and topology required to set up single sign-on with Oracle Access Manager for a WebCenter application.
Figure 14-52 OAM Single Sign-On Components and Topology
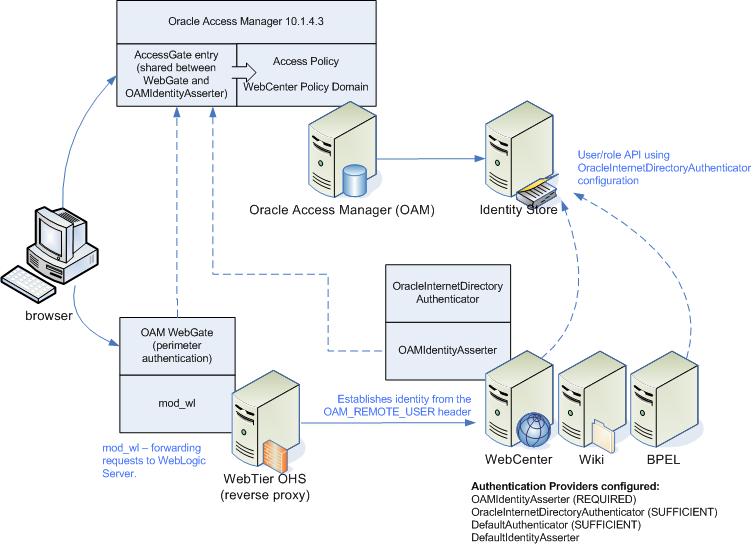
OAM consists of the following components:
Access Server - a standalone server that provides authentication, authorization, and auditing services for Access Gates. There is one access server set up on OAM. This is done as part of the OAM install itself.
WebGate - an out-of-the-box plugin that intercepts Web resource (HTTP) requests and forwards them to the Access Server for authentication and authorization.
Identity Assertion Provider (IAP) - a type of security provider that asserts the identity of the user based on header information that is set by perimeter authentication. The OAM integration provides an OAM ID Asserter that can be configured as the OAM IAP. The OAM ID Asserter can be used for authentication or for identity assertion. For OAM SSO integration, the OAM ID Asserter should be configured as an Identity Assertion Provider (IAP) by selecting obSSOCookie under Active Types in the provider's Common settings.
These steps assume that you've installed Oracle WebCenter (see Section 2.3, "Installing WebCenter Spaces"). By default, an Oracle WebCenter installation creates a WLS domain, including an Administration Server and three managed servers: WLS_Spaces, WLS_Services and WLS_Portlet.
Install the WebTier, which contains the Oracle HTTP Server (OHS) and mod_wl (see the Oracle Fusion Middleware Installation Guide for Oracle WebCenter for information on how to install the WebTier).
Configure the module mod_wl in the WebTier OHS so that it forwards requests to the Oracle WebLogic Server for WebCenter, as described in Section 14.7.1.3.1, "Configure mod_weblogic (mod_wl_ohs.conf)."
Determine which access server to use.
Log onto the Access Manager.
Click Access System Console.
Open the Access System Configuration tab.
Click Access Server Configuration to display a list of all access servers.
Click an access server in the list to see server details.
The host name and port are the values you need for the oam_aaa_host and oam_aaa_port parameters respectively in the script.
Run the following command.
The oamcfgtool.jar is available in ORACLE_HOME/modules/oracle.oamprovider_11.1.1/oamcfgtool.jar in the WebCenter installation. Values in bold are the one that you need to supply based on the settings of your WebCenter and OAM instances.
java -jar $ORACLE_HOME/modules/oracle.oamprovider_11.1.1/oamcfgtool.jar mode=CREATE app_domain="your_domain_name" protected_uris="/webcenter/adfAuthentication,/owc_wiki/user/login.jz,/owc_wiki/adfAuthentication,/integration/worklistapp, /workflow/sdpmessagingsca-ui-worklist/faces/adf.task-flow,/workflow/WebCenterWorklistDetail/faces/adf.task-flow, /workflow/sdpmessagingsca-ui-worklist,/rss/rssservlet,/owc_discussions/login!withRedirect.jspa, /owc_discussions/login!default.jspa,/owc_discussions/login.jspa,/owc_discussions/admin" public_uris="/webcenter,/owc_wiki,/owc_discussions,/rss,/workflow" app_agent_password=<Password to be provisioned for App Agent> ldap_host=<Hostname of LDAP server> ldap_port=<Port of LDAP server> ldap_userdn=<DN of LDAP Admin User, usually "cn=orcladmin"> ldap_userpassword=<Password of LDAP Admin User> oam_aaa_host=<HOST of OAM server> oam_aaa_port=<Port of OAM server>
We recommend that you register your domain (for <your_domain_name>) as something like "webtier.example.com", where "webtier.example.com" is your Webtier, so that you can easily distinguish the various policies in OAM.
If your command ran successfully, you should see something like the following output depending on the values you used:
Processed input parameters Initialized Global Configuration Successfully completed the Create operation. Operation Summary: Policy Domain : webtier.example.com Host Identifier: webtier.example.com Access Gate ID : webtier.example.com_AG
You can also run the Validate command to validate your configurations:
java -jar ORACLE_HOME/modules/oracle.oamprovider_11.1.1/oamcfgtool.jar mode=VALIDATE app_domain="your_domain_name" ldap_host=<Hostname of LDAP server> ldap_port=<Port of LDAP server> *ldap_userdn=<DN of LDAP Admin User, usually "cn=orcladmin">* ldap_userpassword=<Password of LDAP Admin User> oam_aaa_host=<HOST of OAM server> oam_aaa_port=<Port of OAM server> test_username=<Username to be used for policy validation> test_userpassword=<Userpassword to be used for policy validation>
If your command runs successfully, you should see the same output as above.
Check the Policy Domain settings.
Log on to the Oracle Access Manager.
Click Policy Manager.
Click My Policy Domains.
You should see the domain you just created in the list of policy domains. In the URL prefixes column, you should also see the URIs you specified during the creation of this domain.
Click the domain you just created and open the Resources tab.
The URIs you specified should be showing. You can also open other tabs to view and verify other settings, and manually add additional resources later, if required.
Check the Access Gate Configurations.
Click on Access System Console.
Open the Access System Configuration tab.
Click AccessGate Configuration.
Enter some search criteria and click Go.
When the Access Gate for the domain you just created shows up (it will have the suffix _AG), click on it to see the setting details.
Run the WebGate Installer as described in the section on "Installing the WebGate" in the Oracle Fusion Middleware Enterprise Deployment Guide for Oracle Identity Management.
The InstallShield Wizard will prompt you for several inputs during the installation. Supply the information requested based on the settings for your environment.
Continue with the steps for configuring the Policy Manager in Section 14.7.1.6, "Configuring the Policy Manager", and any further configurations, as required, in Section 14.7.1.7, "Additional Configurations".
Configuring the Webtier components is described in the following sections:
Configure the module mod_wl in the WebTier OHS so that it forwards requests to the Oracle WebLogic Server for WebCenter, by uncommenting lines at WEBTIER_HOME/instances/<your_instance>/config/OHS/ohs1/mod_wl_ohs.conf. This file is included by the httpd.conf file.
To configure Web Tier OHS to work with multiple non-clustered servers, use the example below in mod_wl_ohs.conf. Make sure that the WebLogic port numbers match your configuration.
<IfModule mod_weblogic.c> MatchExpression /webcenter WebLogicHost=webcenter.example.com|WebLogicPort=8888 MatchExpression /rss WebLogicHost=webcenter.example.com|WebLogicPort=8890 MatchExpression /owc_wiki WebLogicHost=webcenter.example.com|WebLogicPort=8890 MatchExpression /owc_discussions WebLogicHost=webcenter.example.com|WebLogicPort=8890 MatchExpression /workflow WebLogicHost=soa.example.com|WebLogicPort=8888 MatchExpression /integration/worklistapp WebLogicHost=soa.example.com|WebLogicPort=8888 MatchExpression /integration/services WebLogicHost=soa.example.com|WebLogicPort=8888 MatchExpression /soa-infra WebLogicHost=soa.example.com|WebLogicPort=8888 </IfModule>
Note:
The entries in theMatchExpression list above map the incoming paths to the appropriate WLS managed servers on which the corresponding applications reside.An AccessGate entry needs to be created on the Access Manager to be shared by the OAM Identity Assertion Provider (IAP), and the WebGate performing perimeter authentication on the webtier reverse proxy.
Note:
If you are doing the configuration using theoamcfgtool scripted installation, this step is not required, as the installation script does it automatically.To create an AccessGate entry:
Log in to the Access Server Console using your browser to navigate to:
http://host:port/access/oblix
Where host is the host ID of the server hosting the Access Manager (for example, oam.example.com), and port is the HTTP port number (for example, 8888).
Open the Access System Configuration page.
Click Add New AccessGate to create a new AccessGate entry.
Click List Access Servers on the Details pane and bind the AccessGate to the Access Server that has been set up for OAM Single Sign-on.
Some of the settings specified here will be needed for WebGate installation and OAM Identity Assertion Provider (IAP) setup. Table 14-2 shows settings for a typical AccessGate entry.
Table 14-2 Sample Settings for AccessGate Entry
| Setting | Value |
|---|---|
|
AccessGate Name |
webcenter-access-gate |
|
Description |
|
|
State |
Enabled |
|
Hostname |
webtier.example.com |
|
Port |
9010 |
|
Access Gate Password |
<Not Displayed> |
|
Debug |
Off |
|
Maximum user session time (seconds) |
3600 |
|
Idle Session Time (seconds) |
3600 |
|
Maximum Connections |
1 |
|
Transport Security |
Open |
|
IPValidation |
On |
|
IPValidationException |
|
|
Maximum Client Session Time (hours) |
24 |
|
Failover threshold |
1 |
|
Access server timeout threshold |
|
|
Sleep For (seconds) |
60 |
|
Maximum elements in cache |
100000 |
|
Cache timeout (seconds) |
1800 |
|
Impersonation username |
|
|
Impersonation password |
<Not Displayed> |
|
ASDK Client |
|
|
Access Management Service |
On |
|
Web Server Client |
|
|
Primary HTTP Cookie Domain |
.example.com |
|
Preferred HTTP Host |
webtier.example.com:9010 |
|
Deny On Not Protected |
Off |
|
CachePragmaHeader |
no-cache |
|
CacheControlHeader |
no-cache |
|
LogOutURLs |
This section describes how to install the WebGate.
To install the WebGate:
Copy the ZIP file (Oracle_Access_Manager10_1_4_3_0_linux_GCClib.zip) containing the two gcc libraries required for the installation (libgcc_s.so.1 and libstdc++.so.5) to a /tmp directory.
Run the installation as root. For example, from the /tmp directory run:
sudo -u root ./Oracle_Access_Manager10_1_4_3_0_linux_OHS11g_WebGate
Follow the installation runtime instructions, providing the installation directory, information of the AccessGate that you created earlier and the absolute path to the httpd.conf file of the web server. For example:
WEBTIER_HOME/instances/instance1/config/OHS/ohs1/httpd.conf
Information for the AccessGate can be found in the Access System Console. For more information, see Section 14.7.1.3.2, "Create an AccessGate Entry".
After the installation a new section is inserted in the httpd.conf file between the following entries:
#** BEGIN WEBGATE SPECIFIC *** #** END Oblix NetPoint Specific ***
Check to see if the content is consistent with your environment.
To configure the Access System, you need to add a host identifier:
Log in to the Access Server Console using your browser to navigate to:
http://host:port/access/oblix
Where host is the host ID of the server hosting the Access Manager (for example, oam.example.com), and port is the HTTP port number (for example, 8888).
Open the Access System Configuration page.
On the navigation pane, click Host Identifiers.
Add a host identifier for the webtier and enter the Host Identifier name (for example, webtier), a Description, and all Hostname variations. The hostname variations should include all the ways that a browser could issue a request to the webtier. For example, webtier and webtier.example.com if the webtier is using the default port; and additionally webtier:8080 and webtier.example.com:8080 if the webtier is not using the default port.
This section describes the steps to set up the WebCenter Policy Domain that will configure the WebCenter application for OAM SSO authentication.
To configure the WebCenter Policy Domain:
Log in to the Access Server Console using your browser to navigate to:
http://host:port/access/oblix
where host is the host ID of the server hosting the Access Manager (for example, oam.example.com), and port is the HTTP port number (for example, 8888).
Click Policy Manager.
The Policy Manager pane displays (see Figure 14-53).
Click Create Policy Domain in the Navigation pane to create a new policy domain to protect the WebCenter resources.
The Create Policy Domain page displays (see Figure 14-54).
Enter a Name (for example, webtier.example.com) and Description for the policy domain and click Save.
Open the Resources tab and click Add.
The Resource page displays (see Figure 14-55).
Add the resources that need to be secured. For each resource:
Select http as the Resource Type.
Select the Host Identifier for the WebCenter webtier.
Enter the URL Prefix for the resources you want to protect.
The following resources can be protected:
/adf.task-flow /faces/adf.task-flow /integration/worklistapp /owc_discussions/login!withRedirect.jspa /owc_discussions/login!default.jspa /owc_discussions/login.jspa /owc_discussions/admin /owc_wiki/user/login.jz /owc_wiki/acl /owc_wiki/adfAuthentication /owc_wiki/admin /owc_wiki/attachments /owc_wiki/default /owc_wiki/domain /owc_wiki/export /owc_wiki/index_dir /owc_wiki/install /owc_wiki/js /owc_wiki/layouts /owc_wiki/macro /owc_wiki/page /owc_wiki/pages /owc_wiki/remote /owc_wiki/tags /owc_wiki/templates /owc_wiki/user /owc_wiki/vhost /owc_wiki/wp /rss/rssservlet /webcenter/adfAuthentication /workflow/sdpmessagingsca-ui-worklist /workflow/WebCenterWorklistDetail/faces /workflow/sdpmessagingsca-ui-worklist
Enter a Description for the resource.
Make sure that Update Cache is selected, and then click Save.
Open the Authorization Rules tab and click Add.
The Authorization Rules page displays (see Figure 14-56).
Enter a Name for the new rule (for example, Default_Authorization) and Description.
Select Yes for Enabled, and No for Allow takes precedence, and click Save.
Click Allow Access on the Authorization Rules tab and click Add.
The Allow Access page displays (see Figure 14-57).
In the Role drop down list, select Any one and click Save.
Open the Default Rules tab and click Add.
The Access Manager Authentication Rule page displays (see Figure 14-58).
Figure 14-58 Access Manager Authentication Rules Page
Enter a Name (for example, Default_SSO) and Description for the rule.
Set the Authentication Scheme to Oracle: Form Authentication (or a form-based authentication scheme that was previously created) and click Save.
Click Authorization Expression on the Default Rules tab, and click Add.
The Authorization Expression page displays (see Figure 14-59).
Figure 14-59 Authorization Expression Page
Add the Default-Authorization authorization rule (or the rule you created previously) to the Authorization Expression and click Add to add it to the Authorization Expression list.
Click Save.
Click Actions on the Authorization Expression subtab and click Add.
The Actions page displays (see Figure 14-60).
Under Authorization Success, specify what actions should be invoked when the authorization succeeds. Add two Return Attribute entries, specifying the Return Type, Name and Return Attribute as:
HeaderVar, REMOTE_USER, uid
HeaderVar, OAM_REMOTE_USER, uid
Note:
Be careful not to put these values under the row for Return Value. The settings should be placed under Return Attribute.Click Save.
Open the Policies tab and click Add.
The Policies page displays (see Figure 14-61).
Enter a Name (for example, Public URI Policy) and Description for the policy that will identify which resources are to be secured to trigger authentication.
Set the Resource Type to http.
Select GET, and POST as the Resource Operations.
Select the Host Identifier (the host identifier of the WebCenter webtier) to which to apply the policy (for example, webtier.example.com) and click Save.
Configuring the Policy Manager is described in the subsections below.
Assuming Oracle Internet Directory is backing the OAM identity store, an Oracle Internet Directory authenticator (OracleInternetDirectoryAuthenticator) should be configured for the LDAP server that is used as the identity store of OAM, and the provider should be set to SUFFICIENT.
To configure the Oracle Internet Directory authenticator:
Log in to the WLS Administration Console.
For information on logging into the WLS Administration Console, see Section 1.12.2, "Oracle WebLogic Server Administration Console".
From the Domain Structure pane, click Security Realms.
The Summary of Security Realms pane displays (see Figure 14-62).
Figure 14-62 Summary of Security Realms Pane
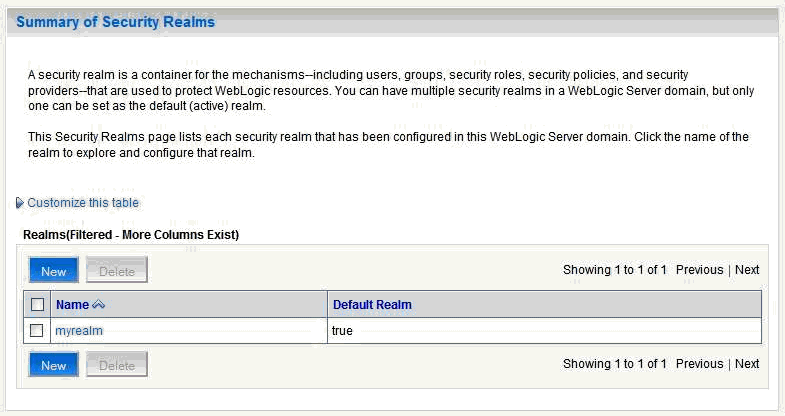
Click the realm entry for which to configure the OAM authenticator.
The Settings pane for the realm displays (see Figure 14-63).
Open the Providers tab.
The Provider Settings display (see Figure 14-64).
Click New to create a new provider.
The Create a New Authentication Provider pane displays (see Figure 14-65).
Figure 14-65 Create a New Authentication Provider Pane
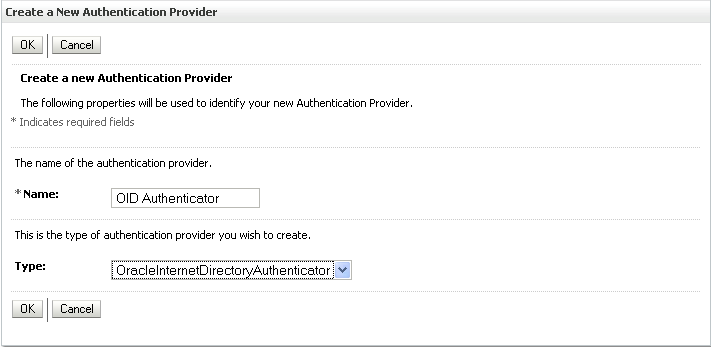
Enter a name for the new provider (for example, OID Authenticator), select OracleInternetDirectoryAuthenticator as its type and click OK.
On the Providers tab, click the newly added provider.
The Common Settings pane for the authenticator displays (see Figure 14-66).
Set the control flag to SUFFICIENT and click Save.
Open the Provider Specific tab.
The Provider Specific Settings pane for the authenticator displays (see Figure 14-67).
Figure 14-67 Provider Specific Settings for OID Authenticator
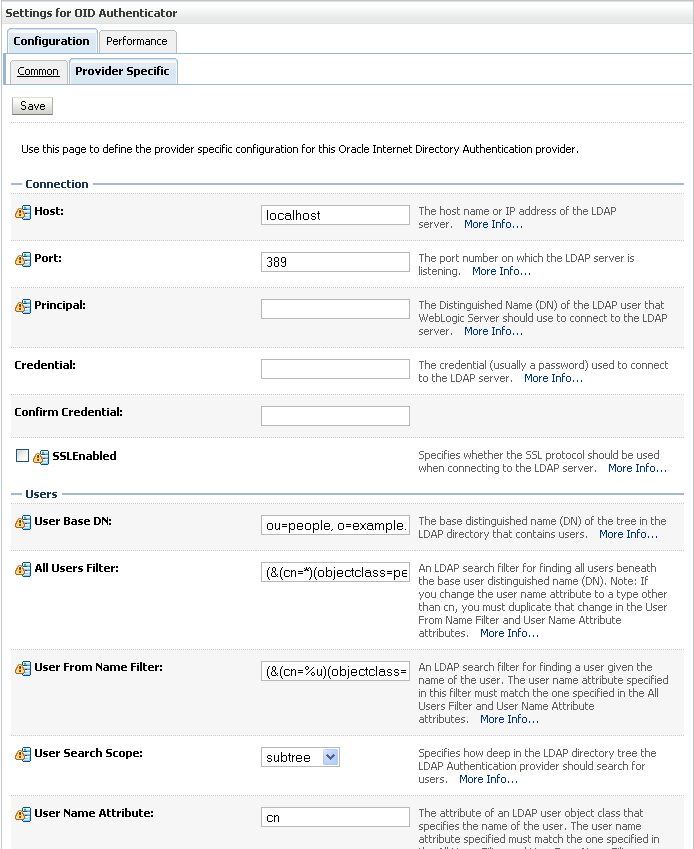
Complete the fields as shown in the table below. Leave the rest of the fields set to their default values.
| Field | Value | Comment |
|---|---|---|
| Host: | The host ID for the LDAP server | |
| Port: | The LDAP server port number | |
| Principal: | The LDAP administrator principal (for example, cn=orcladmin) | |
| Credential: | <password> |
The administrator principal password |
| Confirm Credential: | <password> |
|
| User Base DN: | User Search Base - this value would be same as #1.d in OAM Access Manager Setup | |
| All Users Filter: | "(&(uid=*)(objectclass=person))" | |
| User Name Attribute: | "uid" | |
| Group Base DN: | Group search base - Same as User Base DN |
Click Save.
Restart the WebCenter Administration Server and managed server and validate the configuration by navigating to the Realm Settings page in the WLS Administration Console and opening the Users and Groups tab.
An OAM identity asserter needs to be configured with the provider Control Flag set to REQUIRED.
To configure the OAM Identity asserter:
Log in to the WLS Administration Console.
For information on logging into the WLS Administration Console, see Section 1.12.2, "Oracle WebLogic Server Administration Console".
From the Domain Structure pane, click Security Realms.
The Summary of Security Realms pane displays (see Figure 14-68).
Figure 14-68 Summary of Security Realms Pane

Click the realm entry for which to configure the OAM identity asserter.
The Settings pane for the realm displays (see Figure 14-69).
Open the Providers tab.
The Provider Settings display (see Figure 14-70).
Click New to create a new provider.
The Create a New Authentication Provider pane displays (see Figure 14-71).
Figure 14-71 Create a New Authentication Provider Pane
Enter a name for the new provider (for example, OAM ID Asserter), select OAMIdentityAsserter as its type and click OK.
On the Providers tab, click the newly added provider.
The Common Settings pane for the authenticator displays (see Figure 14-72).
Set the control flag to REQUIRED and check that ObSSOCookie is set for Active Types.
Click Save.
Open the Provider Specific tab.
The Provider Specific Settings pane for the OAMIdentityAsserter displays (see Figure 14-73).
Figure 14-73 Provider Specific Settings for the OAMIdentityAsserter
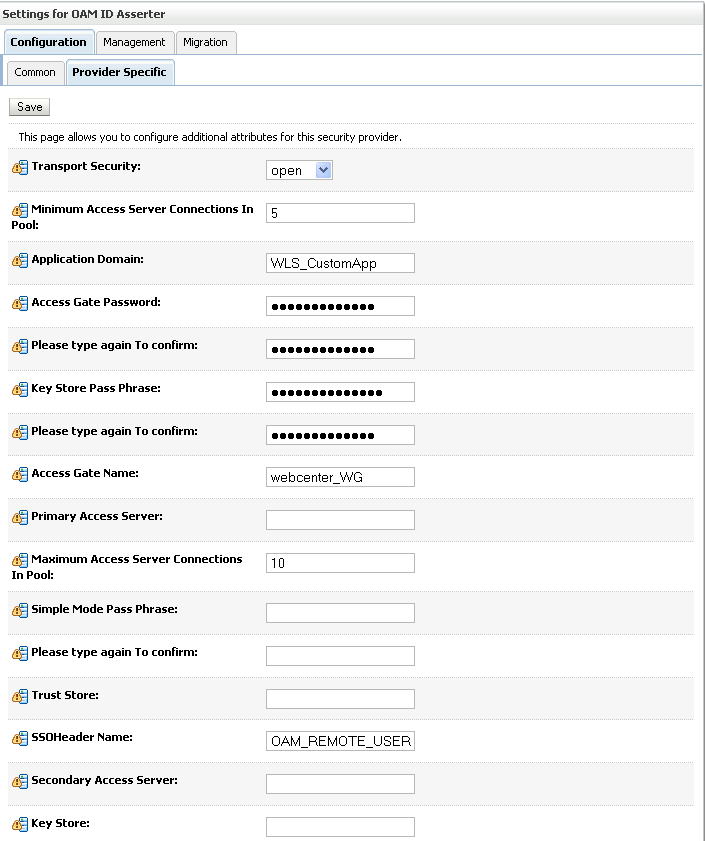
Complete the fields as shown in the table below. Leave the rest of the fields set to their default values.
| Field | Value | Comment |
|---|---|---|
| Primary Access Server: | The OAM server endpoint information in HOST:PORT format | |
| Access Gate Name: | Name of the Access Gate | |
| Access Gate Password: | Provide the Access Gate password and confirm in the field below. |
Click Save to save your settings.
After configuring the OAM identity asserter, make sure that the default authenticator's control flag is set to SUFFICIENT and reorder the providers as shown below:
Navigate to the Provider Settings pane (see Figure 14-70).
Open the Default Authenticator and check that the control flag is set to SUFFICIENT.
Do the same for any providers other than the two you just created.
On the Settings Pane, reset the provider order to:
OAMIdentityAsserter (REQUIRED)
OracleInternetDirectoryAuthenticator (SUFFICIENT)
DefaultAuthenticator (SUFFICIENT)
DefaultIdentityAsserter
Configure the applications for SSO by adding a setting to EXTRA_JAVA_PROPERTIES.
There is a system property that tells WebCenter and ADF that the application is configured in SSO mode and some special handling is required. The following system property is required in this mode:
| Field | Value | Comment |
|---|---|---|
oracle.webcenter.spaces.osso |
true |
This flag tells WebCenter that SSO is being used, so no login form should be displayed on the default landing page. Instead, it will render a login link that the user can click to invoke the SSO authentication. |
To set this property, edit the setDomainEnv.sh script located in your <domain>/bin directory. Add the property to the EXTRA_JAVA_PROPERTIES variable, as follows:
EXTRA_JAVA_PROPERTIES="-Dweblogic.security.SSL.ignoreHostnameVerification=true -Doracle.mds.bypassCustRestrict=true
-Djps.update.subject.dynamic=true -Doracle.webcenter.spaces.osso=true
-noverify ${EXTRA_JAVA_PROPERTIES}"
After making this change, restart the following servers:
WebCenter's Administration Server
All the domain's managed servers
WebTier OHS
The following configurations may be necessary or helpful in providing additional security for your site:
This section describes how to optionally set up OAM single sign-on for the WLS Administration Console and Enterprise Manager.
Note:
Setting up OAM SSO for Enterprise Manager and the WLS Administration Console would provide single sign-on access to same set of users for whom OAM SSO access has been configured. If want the Webtier to be accessible to external users through OAM, but want administrators to log in directly to Enterprise Manager and the WLS Administration Console, then you may not want to complete this additional configuration step.To set up OAM SSO for the WLS Administration Console and Enterprise Manager:
Log in to the Access Server Console using your browser to navigate to:
http://host:port/access/oblix
Where host is the host ID of the server hosting the Access Manager (for example, oam.example.com), and port is the HTTP port number (for example, 8888).
Click Policy Manager.
The Policy Manager pane displays (see Figure 14-74).
Search for the policy domain that you created earlier to protect WebCenter resources in Section 14.7.1.5, "Manually Defining the WebCenter Policy Domain".
Open the Resources tab and click Add.
The Resource page displays (see Figure 14-75).
Add the resources that need to be secured. For each resource:
Select http as the Resource Type.
Select the Host Identifier for the WebCenter webtier.
Enter the URL Prefix for the WLS Administration Console or Enterprise Manager.
Enter a Description for the resource.
Make sure that Update Cache is selected, and then click Save.
In your webtier, modify the mod_wl_ohs.conf file (in WEBTIER_HOME/instances/your_instance/config/OHS/ohs1/) to include the WLS Administration Console and Enterprise Manager, using the actual host ID for the WebCenter Administration Server for WebLogicHost.
<IfModule mod_weblogic.c> MatchExpression /webcenter WebLogicHost=example.com|WebLogicPort=8888 MatchExpression /rss WebLogicHost=example.com|WebLogicPort=8888 MatchExpression /owc_wiki WebLogicHost=example.com|WebLogicPort=8890 MatchExpression /owc_discussions WebLogicHost=example.com|WebLogicPort=8890 MatchExpression /console WebLogicHost=example.com|WebLogicPort=7001 MatchExpression /em WebLogicHost=example.com|WebLogicPort=7001 </IfModule>
Restart the Oracle HTTP Server for your changes to take effect.
You should now be able to access the WLS Administration Console and Enterprise Manager with the following links:
http://host:OHS port/console http://host:OHS port/em
and be prompted with the OAM SSO login form.
Prior to configuring the Oracle WebCenter Discussions Server for SSO, you may need to deploy it.
To deploy the discussions server:
Log into the WLS Administration Console.
For information on logging into the WLS Administration Console, see Section 1.12.2, "Oracle WebLogic Server Administration Console".
In the Domain Structure pane, click Deployments.
The Deployments Summary pane displays (see Figure 14-76).
On the Deployment Summary page, select owc_discussions stop and delete and click Install.
Using the Install Application Assistant Path field, locate the SSO enabled owc_discussions .EAR file (typically in MW_HOME/Oracle_WC1/discussionserver).
Select the owc_discussions_sso.ear file and click Next.
Select Install this deployment as an application and click Next.
Deploy the .EAR file with all default options except the Name, which should be set to owc_discussions.
Restart the WLS_Services managed server.
Now, when you access the discussion server's Admin Console through the OHS port:
http://<host>:<OHS port>/owc_discussions/admin/
you should be challenged by the WebGate login form.
This section describes how to configure Oracle WebCenter Discussions Server for OAM single sign-on. Before configuring the discussions server for OAM SSO, deploy it as shown in Section 14.7.1.7.2, "Deploying the Discussions Server", and configure it to use the same identity store LDAP as WebCenter Spaces, as described in Section 14.3.6, "Configuring the Discussions Server to Share the Identity Store LDAP Server".
To set up the discussions server for OAM SSO
Log in to the Oracle WebCenter Discussions Server Admin Console at:
http://host:port/owc_discussions/admin
Where host and port are the host ID and port number of the WLS_Services managed server.
Open the System Properties page and edit (if it already exists) or add the AuthFactory.className property setting it's value to oracle.jive.sso.OracleSSOAuthFactory.
Edit or add the jiveURL property to point to the base URL of the SSO server. For example:
jiveURL = example.com:8890/owc_discussions
Deploy the SSO-enabled owc_discussions application.
To create a discussions server connection for WebCenter Spaces
Log into Fusion Middleware Control and select the WebLogic domain for WebCenter Spaces.
For information on logging into Fusion Middleware Control, see Section 6, "Starting Enterprise Manager Fusion Middleware Control".
In the Navigation pane, open the WebCenter node, and then the WebCenter Spaces node, and click WebCenter Spaces (WLS_Spaces).
Register the discussion server as described in Section 11.1.3.1, "Registering Discussion Servers Using Fusion Middleware Control".
For Server URL, enter http://<host>:<port>/owc_discussions .
Restart the WLS_Spaces managed server.
When you log into WebCenter Spaces, you automatically sign on to the discussion server as well.
Wiki page functionality is supported as a portlet, which you can embed in a Web page, and OAM single sign-on is supported this way. Since the Oracle WebCenter Wiki and Blog Server does not require or support an identity store, there is no need to configure the LDAP.
To add a wiki page to a WebCenter identity store, follow the steps below:
Log in to WebCenter Spaces, and open a group space.
Add a page, choosing Web Page as the Style.
When the page is created, click the Edit icon.
The Component properties dialog displays.
Enter the following URL in the Source box:
http://host:OHS port/owc_wiki/page/show.jz?inline=1&scope=#{communityContext.communityName}
Where host is the host ID of the WLS_Spaces server, and OHS_port is the port number of the Oracle HTTP Server. The OHS port is used so the call goes through the WebGate which will initiate SSO.
After specifying the component properties you will see the wiki page contents.
Save the changes.
Follow the steps below to only allow users to access WebCenter and other services through the WebTier OHS ports so that they can be properly authenticated.
Log in to the WLS Administration Console.
For information on logging into the WLS Administration Console, see Section 1.12.2, "Oracle WebLogic Server Administration Console".
In the Domain Structure pane, select the domain you want to configure (for example, webcenter).
Open the Security tab and the Filter subtab.
The Security Filter Settings pane displays (see Figure 14-77).
Figure 14-77 Security Filter Settings Page
Check Connection Logger Enabled to enable the logging of accepted messages.
The Connection Logger logs successful connections and connection data in the server. This information can be used to debug problems relating to server connections.
In the Connection Filter field, specify the connection filter class to be used in the domain.
To configure the default connection filter, specify weblogic.security.net.ConnectionFilterImpl.
To configure a custom connection filter, specify the class that implements the network connection filter. Note that this class must also be present in the CLASSPATH for WebLogic Server.
In the Connection Filter Rules field, enter the syntax for the connection filter rules.
For example:
<webtier IP>/0 * * allow 0.0.0.0/0 * * deny
which says: allow all traffic coming from the local host and disallow all traffic from any other IP address. You should, of course, write the network filter(s) that are relevant to your environment. For more information about writing connection filters, see "Developing Custom Connection Filters" in Oracle Fusion Middleware Programming Security for Oracle WebLogic Server.
Click Save and activate the changes.
Restart all the managed servers and the Administration Server.
Verify that all direct traffic to the WLS server is blocked by attempting to navigate to:
http://host:WLS_port/webcenter
This should produce the following error:
"The Server is not able to service this request: [Socket:000445]Connection rejected, filter blocked Socket, weblogic.security.net.FilterException: [Security:090220]rule 3"
You should, however, still be able to access WebCenter through the OHS port:
http://host:OHS_port/webcenter
In a default installation, WebCenter uses the HTTP ports in the WLS managed server created for WebCenter. To configure WebCenter with Oracle Single Sign-On, WebCenter needs Oracle HTTP Server and the associated Module mod_osso to integrate with Oracle Single Sign-On (OSSO).
Note:
The BPEL Console does not support SSO integration. When WebCenter is configured for SSO, login to BPEL must still be done through the standard login page on the BPEL Console.This section includes the following subsections
In a default installation, WebCenter uses the HTTP ports of the WLS managed server created for WebCenter. To configure WebCenter with Oracle Single Sign-On, WebCenter needs the Oracle HTTP Server and the associated Module mod_osso, to integrate with Oracle SSO. The diagram below (Figure 14-78) shows the overall architecture of this integration:
Figure 14-78 OSSO Components and Topology
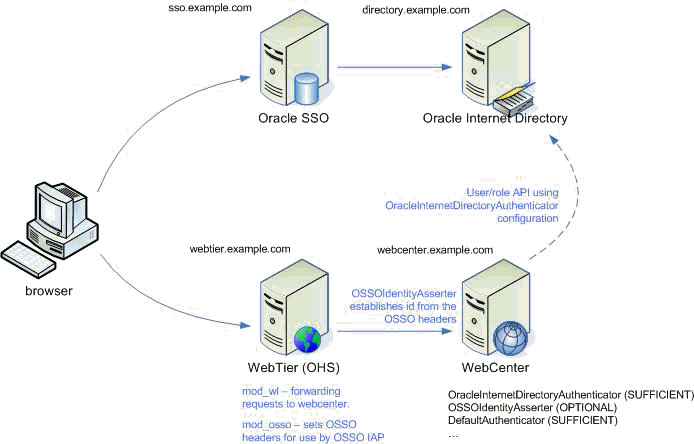
This section describes how to load and configure the Oracle HTTP Server and associated mods.
To load and configure the Oracle HTTP Server and associated mods
Install the WebTier, which contains Oracle HTTP Server (OHS) and associated mods (mod_osso and mod_wl).
Configure the module mod_wl in WebTier OHS so that it forwards requests to the Oracle WebLogic Server for WebCenter.
Uncomment the lines at WEBTIER_HOME/instances/your_instance/config/OHS/ohs1/mod_wl_ohs.conf. This file is included by the httpd.conf file and looks like the following:
LoadModule weblogic_module ORACLE_HOME/ohs/modules/mod_wl_22.so <IfModule mod_weblogic.c> MatchExpression /webcenter WebLogicHost=webcenter.example.com|WebLogicPort=8888 MatchExpression /rss WebLogicHost=webcenter.example.com|WebLogicPort=8890 MatchExpression /owc_wiki WebLogicHost=webcenter.example.com|WebLogicPort=8890 MatchExpression /owc_discussions WebLogicHost=webcenter.example.com|WebLogicPort=8890 MatchExpression /workflow WebLogicHost=soa.example.com|WebLogicPort=8888 MatchExpression /integration WebLogicHost=soa.example.com|WebLogicPort=8888 </IfModule>
Include the OSSO Identity Assertion Provider (IAP) provider in the Oracle WebLogic domain for WebCenter. Use the WLS Administration Console to add the OSSO IAP to your domain as shown in the steps below.
To configure the OSSOIdentityAsserter:
Log in to the WLS Administration Console.
For information on logging into the WLS Administration Console, see Section 1.12.2, "Oracle WebLogic Server Administration Console".
From the Domain Structure pane, click Security Realms.
The Summary of Security Realms pane displays (see Figure 14-79).
Figure 14-79 Summary of Security Realms Pane

Click the realm entry to which to add the provider.
The Settings pane for the realm displays (see Figure 14-80).
Click the Providers tab.
The Provider Settings display (see Figure 14-81).
Click New to create a new provider.
The Create a New Authentication Provider pane displays (see Figure 14-82).
Figure 14-82 Create a New Authentication Provider Pane
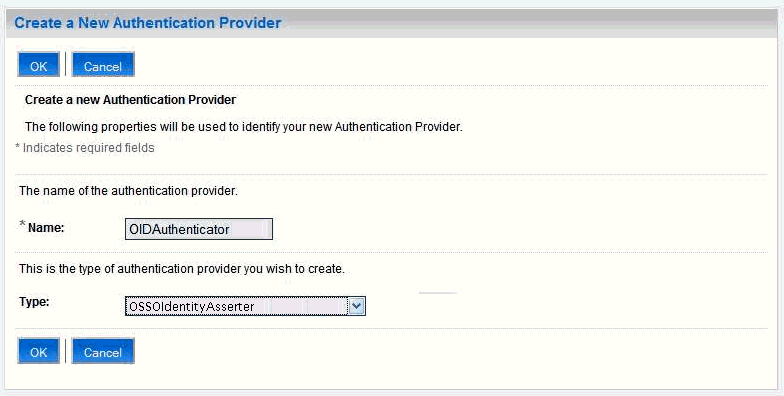
Enter a name for the new provider, select OSSOIdentityAsserter as its type and click OK.
On the Providers tab, click the newly added provider.
Set the control flag to OPTIONAL.
Make sure that OracleInternetDirectoryAuthenticator is set as the primary authenticator for the domain so that the user profile info can be obtained from the associated Oracle Internet Directory server.
The provider list should appear as follows:
OracleInternetDirectoryAuthenticator (SUFFICIENT)
OSSOIdentityAsserter (OPTIONAL)
DefaultAuthenticator (SUFFICIENT)
DefaultIdentityAsserter (OPTIONAL)
Also make sure that the default jpsContext in WebCenter's jps-config.xml file is set to the idstore.ldap serviceInstance.
Configure the Provider Specific details of the OSSO IAP with the settings for the following fields:
| Field | Value | Comment |
|---|---|---|
LDAPPort |
The LDAP port of the OID server | |
Password |
The password of the LDAP entry to be used for the connection (for example, cn=orcladmin, or other less privileged account) |
|
| Confirm Password | Re-enter the password to confirm. | |
| Admin DN | The account to be used for the connection | |
| Use Retrieved User Name As Principal | True | |
| Cache TTL | 60 | |
| Rolefetching Enabled | False | |
| Level | 1 | |
| Initial Cache Capacity | 128 | |
| LDAPHost | The host name of the OID server | |
| Maximum Cache Capacity | 1024 |
Register the module mod_osso in the WebTier OHS with the SSO Server as a partner application by following the steps below.
To register OHS with Oracle SSO:
Run ssoreg from the SSO server to generate an osso.conf file and manually copy it to the partner application (WEBTIER_HOME).
This example shows how you would register a remote partner application on a SSO Server:
bash-3.00$ ORACLE_HOME/sso/bin/ssoreg.sh -site_name webtier.example.com:80 -config_mod_osso TRUE -mod_osso_url http://webtier.example.com -remote_midtier -config_file webtier.example.com.osso.conf
Running this command creates a webtier.example.com.osso.conf file.
Copy the WEBTIER_HOME/instances/your_instance/config/OHS/ohs1/disabled/mod_osso.conf file to WEBTIER_HOME/instances/your_instance/config/OHS/ohs1/moduleconf. All files in the moduleconf directory are included in the httpd.conf file.
Add a static rule to the mod_osso.conf file to protect the /webcenter URL with Oracle SSO.
The mod_osso.conf file should look similar to this:
LoadModule osso_module ORACLE_HOME/ohs/modules/mod_osso.so
<IfModule mod_osso.c>
OssoIpCheck off
OssoIdleTimeout off
OssoSecureCookies Off
# whatever the location of your real osso.conf file is, that was generated from the ssoreg.sh command.
OssoConfigFile /OracleWebTier/webtier.example.com.osso.conf
#______-
# Notes
#______-
# 1. Here's what you need to add to protect a resource,
# e.g. <ApacheServerRoot>/htdocs/private:
# 2. if an application is protected by SSO then no matter what Apache will always
# send no-cache headers practically undoing whatever the Apache configuration or
# the ADF faces Cache library do. To allow caching for SSO protected resources
# add "OssoSendCacheHeaders off " as following.
<Location /webcenter/adfAuthentication>
OssoSendCacheHeaders off
require valid-user
AuthType Osso
</Location>
<Location /owc_wiki/user/login.jz>
OssoSendCacheHeaders off
require valid-user
AuthType Osso
</Location>
<Location /rss/rssservlet>
OssoSendCacheHeaders off
require valid-user
AuthType Osso
</Location>
<Location /owc_discussions/login!withRedirect.jspa>
OssoSendCacheHeaders off
require valid-user
AuthType Osso
</Location>
<Location /owc_discussions/login!default.jspa>
OssoSendCacheHeaders off
require valid-user
AuthType Osso
</Location>
<Location /owc_discussions/login.jspa>
OssoSendCacheHeaders off
require valid-user
AuthType Osso
</Location>
<Location /owc_discussions/admin>
OssoSendCacheHeaders off
require valid-user
AuthType Osso
</Location>
<Location /owc_wiki/adfAuthentication>
OssoSendCacheHeaders off
require valid-user
AuthType Osso
</Location>
<Location /integration/worklistapp>
OssoSendCacheHeaders off
require valid-user
AuthType Osso
</Location>
<Location /workflow/WebCenterWorklistDetail>
OssoSendCacheHeaders off
require valid-user
AuthType Osso
</Location>
<Location /workflow/sdpmessagingsca-ui-worklist>
OssoSendCacheHeaders off
require valid-user
AuthType Osso
</Location>
</IfModule>
#
# If you would like to have short hostnames redirected to
# fully qualified hostnames to allow clients that need
# authentication via mod_osso to be able to enter short
# hostnames into their browsers uncomment out the following
# lines
#
#PerlModule Apache::ShortHostnameRedirect
#PerlHeaderParserHandler Apache::ShortHostnameRedirect
Be sure to change the OssoConfigFile parameter to point to the location (and filename if you've changed it) of your osso.conf file.
Restart the WebTier so that the configuration changes to mod_osso and mod_wl to take effect.
For the Worklist service changes to take effect, run the following command on the WebCenter Adminstration server:
setBPELConnection('webcenter','WebCenter-Worklist', 'http://webcenter-stage.example.com')
To only allow users to access WebCenter and other services through the WebTier OHS ports so that they can be properly authenticated, follow the steps in Section 14.7.1.7.5, "Restricting Access with Connection Filters".
Security Assertion Markup Language (SAML) enables cross-platform authentication between Web applications or Web Services running in a WebLogic Server domain and Web browsers or other HTTP clients. WebLogic Server supports single sign-on (SSO) based on SAML. When users are authenticated at one site that participates in a single sign-on (SSO) configuration, they are automatically authenticated at other sites in the SSO configuration and do not need to log in separately.
This SSO mechanism can be used for departmental WebCenter installations for which there is no existing Oracle SSO or Oracle Access Manager single sign-on infrastructure, but single sign-on between only WebCenter Spaces and its services is required. For High Availability and large enterprise deployments, the Oracle Access Manager SSO configuration is recommended.
This section describes how to set up SAML 1.1-based single sign-on for Oracle WebCenter Spaces and the Wiki and Worklist services running on different managed servers within the same domain.
This section includes the following subsections:
Figure 14-84 shows the components and their interaction in a SAML-based single sign-on configuration that includes WebCenter Spaces and the Wiki service.
A SAML-based single sign-on solution consists of the following components:
SAML Credential Mapper - The SAML Credential Mapping provider acts as a producer of SAML security assertions, allowing WebLogic Server to act as a source site for using SAML for single sign-on. The SAML Credential Mapping provider generates valid SAML 1.1 assertions for authenticated subjects based on the configuration of the target site or resource.
Inter Site Transfer Service (ITS) - an addressable component that generates identity assertions and transfers the user to the destination site.
Assertion Retrieval Service (ARS) - an addressable component that returns the SAML assertion that corresponds to the artifact. The assertion ID must have been allocated at the time assertion was generated.
SAML Identity Asserter - The SAML Identity Assertion provider acts as a consumer of SAML security assertions, allowing WebLogic Server to act as a destination site for using SAML for single sign-on. The SAML Identity Assertion provider processes valid SAML 1.1 assertions for authenticated subjects obtained from the source site or resource.
Assertion Consumer Service (ACS) - an addressable component that receives assertions and/or artifacts generated by the ITS and uses them to authenticate users at the destination site
SAML Relying party - A SAML Relying Party is an entity that relies on the information in a SAML assertion produced by the SAML source site. You can configure how WebLogic Server produces SAML assertions separately for each Relying Party or use the defaults established by the Federation Services source site configuration for producing assertion.
SAML Asserting party - A SAML Asserting Party is a trusted SAML Authority (an entity that can authoritatively assert security information in the form of SAML Assertions).
Figure 14-83 shows the components and flow for a POST-configured SAML SSO configuration that includes both a WebCenter and SOA domain. The flow is similar for other destination applications participating in single sign-on such as RSS, Worklist applications, and Discussions.
Figure 14-83 Detailed SAML Single Sign-on Components and Topology (POST Profile Configured)
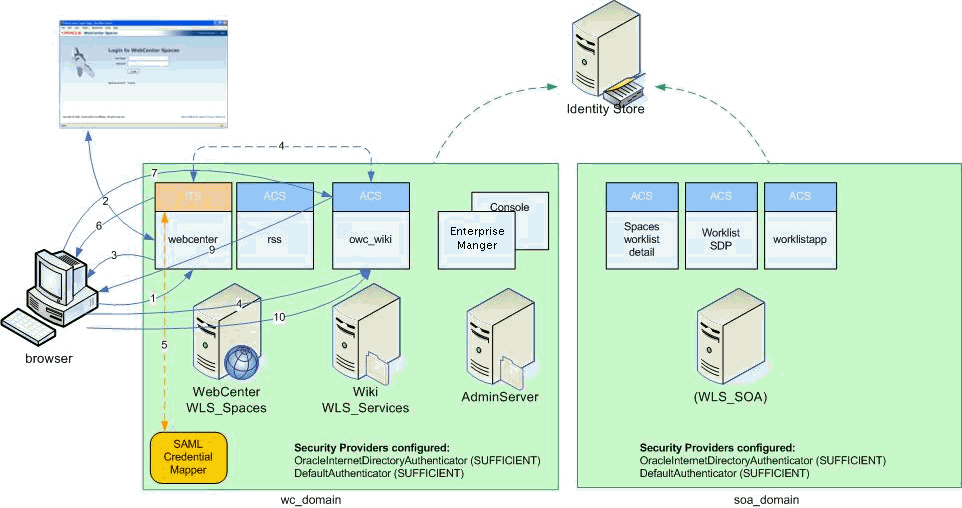
Figure 14-84 shows a simplified version of the components and flow for a POST-configured SAML SSO configuration, including the SAML SSO flow between WebCenter Spaces and the OWC Wiki application.
Figure 14-84 SAML Single Sign-on Components and Topology (POST Profile Configured)
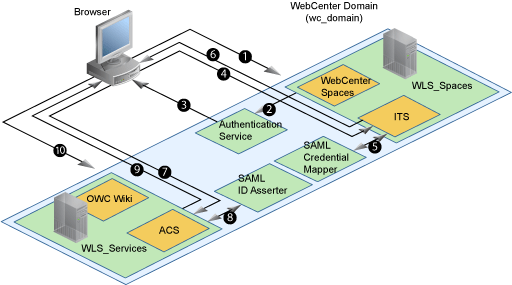
The steps in the flow are:
The user's browser accesses WebCenter Spaces (source site), hosted on a WebLogic managed server (WLS_Spaces) in the WebCenter domain (wc_domain), by supplying user credentials.
WebCenter Spaces passes the user credentials to the authentication service provider.
If authentication is successful, the authenticated session is established, and the WebCenter Spaces welcome page is displayed.
From the welcome page, the user then clicks on a link on the page to access a secured Web page of the Wiki service (destination site), hosted on a different WebLogic Server (WLS_Services) in the same domain. This triggers a call to the Inter-Site Transfer Service (ITS) servlet configured. In this case, the ITS servlet is hosted within the source site (that is, on the WebCenter Spaces application on the WLS_Spaces managed server) that will share the same JSESSIONID cookie as WebCenter Spaces.
The ITS servlet calls the SAML Credential Mapper configured in the WebCenter domain (wc_domain) to request a caller assertion. The SAML Credential Mapper returns the assertion. It also returns the URL of the destination site application Web page (a secured Web page of the Wiki service) and path to the appropriate POST form (if the source site is configured to use the POST profile).
The SAML ITS servlet generates a SAML response containing the generated assertion, signs it, base-64 encodes it, embeds it in the HTML form, and returns the form to the user's browser.
The user's browser POSTs the form to the destination site's Assertion Consumer Service (ACS). In this case, the ACS Servlet is hosted in destination site (the Wiki service) and shares its login cookie.
The assertion is validated.
If the assertion is successful, the user is redirected to the target (the secured Web page of the Wiki service).
The user is logged in on the destination site Wiki service without having to reauthenticate.
Configuring SAML-based SSO consists of the following six steps:
After installing WebCenter Spaces and the Wiki and Worklist services, you must test the single sign-on configuration.
To check the default WebCenter Spaces and Wiki service login:
Install WebCenter Spaces, and select the Wiki service and Discussions service, and any other service applications to be configured for SSO (RSS is automatically deployed when you install WebCenter Spaces). For information on installing WebCenter Spaces, see "Installing WebCenter Spaces, Portlet Producers, Discussions, and Wiki and Blogs" in the Oracle Fusion Middleware Installation Guide for Oracle WebCenter.
When the installation is complete, WebCenter Spaces is hosted on the WLS_Spaces managed server, and Wiki and Discussions services are hosted on the WLS_Services managed server. Record the host and port that the Wiki service is running on so, later on, you can construct the URL and test single sign-on.
Log into WebCenter Spaces and create a personal page with a link to the Wiki service as shown below:
Log in to WebCenter Spaces as a user with create page permissions.
Create a new page by clicking on the Create a page tab in a group space.
Title the page appropriately (for example, "Wiki") and choose the Web page template.
Click the Inspector button and click on the Web page.
Change the source to be the URL specified below:
http://host:port/owc_wiki/page/show.jz?inline=1&scope=#{communityContext.communityName}
Where host is the Wiki server host ID and port is the Wiki server port number.
Save the page.
When you click the link, note that you are challenged to log in by the Wiki service. Once you have completed the remainder of the steps, this is not required. You will be automatically logged into Wiki service.
For the Worklist service, install SOA (which includes the BPEL server). For information on installing SOA, see Oracle Fusion Middleware Installation Guide for Oracle SOA Suite.
Configure the BPEL connection for WebCenter Spaces as described in Section 11.5, "Setting Up Connections for the Worklist Service".
To test the BPEL connection:
Log into WebCenter Spaces, create a group space, and add your administrator account as a moderator.
Log into WebCenter Spaces with your administrator account.
You should see a new item in the Worklist task flow indicating that you have been added as a moderator for the group space.
Click the link.
Note that you are challenged to log in. After you have completed the rest of the steps you automatically log into the Worklist service on the SOA domain.
Although optional, to secure communication between the SAML source and destination sites, communication should be encrypted. Additionally, certificates should be used to verify the identity of the other party during SAML interaction. Follow the steps below to generate a key using the keytool utility (available as part of the JDK 6.0), and register it using the WLS Administration Console.
To create certificates using keytool
Navigate to the WEBLOGIC_HOME/server/lib directory.
Using keytool, generate the key with the following command:
keytool -genkey -keypass key_password -keystore keystore_name -storepass keystore_password -keyalg rsa -alias alias
Where:
key_password is the password to apply to the generated key
keystore_name is the name of the custom keystore
keystore_password is the password for the custom keystore
alias is the alias name (for example, testalias)
Run the keytool command with -export option to generate a key file calling it, for example, testalias.der.
keytool -export -keypass key_password -keystore keystore_name -storepass keystore_password -alias alias -file testalias.der
where:
key_password is the password for the generated key
keystore_name is the name of the custom keystore
keystore_password is the password for the custom keystore
alias is the alias name (for example, testalias)
To register the keystore using the WLS Administration Console
Log in to the WLS Administration Console.
For information on logging into the WLS Administration Console, see Section 1.12.2, "Oracle WebLogic Server Administration Console".
In the Domain Structure pane, expand Environment and click Servers.
The Summary of Servers pane displays (see Figure 14-85).
Click the WebCenter Spaces server (WLS_Spaces) to configure the identity and trust keystore.
The Settings pane for the WebCenter Spaces server displays (see Figure 14-86).
Figure 14-86 Settings Pane for WebCenter Spaces Server

Open the Configuration tab, and then the Keystores subtab.
The Keystores pane displays (see Figure 14-87).
For Keystores, select Custom Identity and Java Standard Trust.
In the Identity section, enter the path to the Custom Identity Keystore you created, choose JKS as the Type, and enter and confirm the Custom Identity Keystore Passphrase.
In the Trust section, enter the path to the trust keystore in Java Standard Trust Keystore, enter JKS as the Type, and enter and confirm the Java Standard Trust Keystore Passphrase.
Click Save.
This section describes how to create a SAML Credential Mapping Provider V2 instance. Note that the SAML Credential Mapping provider is not part of the default security realm and must be created.
Creating the SAML Credential Mapping Provider instance is the first of two steps required to configure the credential mapping provider:
Creating the SAML Credential Mapping Provider instance
Configuring a Relying Party for each of the participating service applications (which can include OWC Wiki, OWC Discussions, RSS, Worklist Community Detail, Worklist SDP, and Worklist Integration)
To create a SAML Credential Mapping Provider instance:
Log in to the WLS Administration Console.
For information on logging into the WLS Administration Console, see Section 1.12.2, "Oracle WebLogic Server Administration Console".
From the Domain Structure pane, click Security Realms.
The Summary of Security Realms pane displays (see Figure 14-88).
Figure 14-88 Summary of Security Realms Pane

Click your security realm.
The Settings page for the security realm displays (see Figure 14-89).
Figure 14-89 Security Realm Settings Page
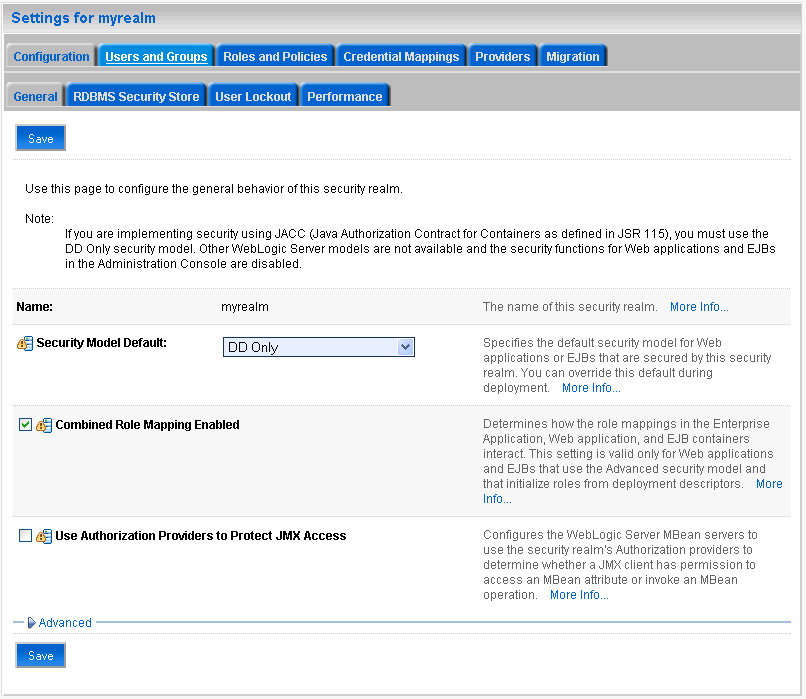
Open the Providers tab and select the Credential Mapping subtab.
The Credential Mapping pane displays (see Figure 14-90).
Click New.
The Create a New Credential Mapping Provider pane displays (see Figure 14-91).
Figure 14-91 Create a New Credential Provider Pane
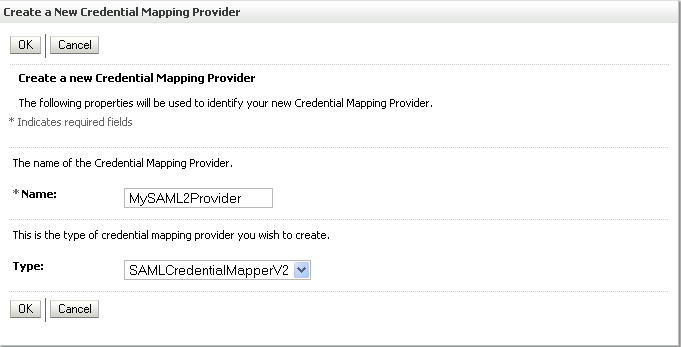
Enter a Name for the provider, select the Type as SAMLCredentialMapperV2, and click OK.
On the Security Realm Settings page, click the provider you just created.
The Settings page for the new provider displays (see Figure 14-92).
Open the Provider Specific tab.
The Provider Specific Settings Pane displays (see Figure 14-93).
Figure 14-93 Provider Specific Settings Pane
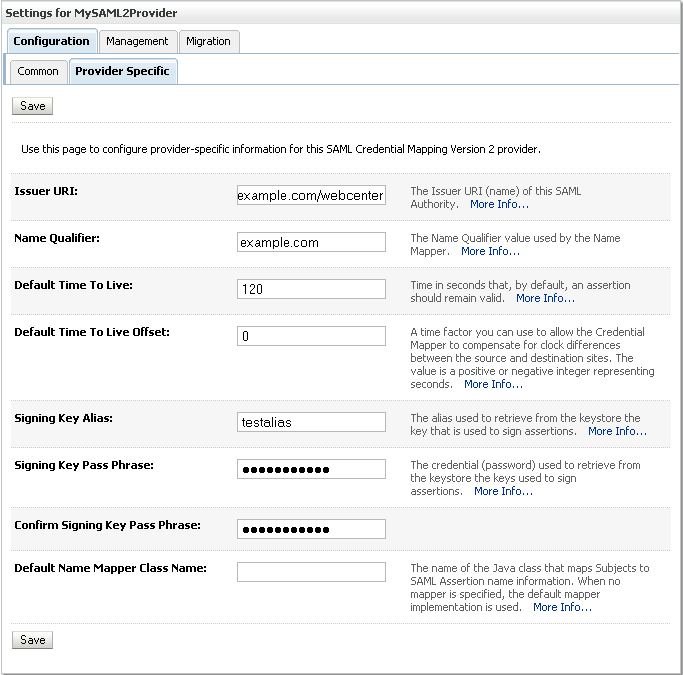
Configure the SAML Credential Mapping provider as a SAML authority, using the Issuer URI, Name Qualifier, and other attributes as shown below in Table 14-3. Leave the remaining parameters set to their default values.
Table 14-3 SAML Credential Mapping Provider Security Realm Settings
| Parameter | Value | Description |
|---|---|---|
|
Issuer URI |
|
The Issuer URI (name) of this SAML Authority. This unique URI tells the destination site (Wiki service) the origin of the SAML message and allows it to match with the key. Typically, the URI is used to guarantee uniqueness. |
|
Name Qualifier |
|
The Name Qualifier value used by the Name Mapper. The value of the Name Qualifier is the security or administrative domain that qualifies the name of the subject. This provides a means to federate names from disparate user stores while avoiding the possibility of subject name collision. |
|
Web Service Assertion Signing Key Alias |
The alias used to retrieve from the keystore the key that is used to sign assertions (for example, testalias). |
|
|
Web Service Assertion Signing Key Passphrase |
The credential (password) used to retrieve from the keystore the keys used to sign assertions (for example, testkeypass). |
|
|
Please type again To confirm |
Re-enter the credential password. |
Click Save to save your settings.
Restart the WebLogic Administration server.
Configuring a relying party is the second of two steps required to configure the credential mapping provider:
Creating the SAML Credential Mapping Provider instance
Configuring a relying party for each of the participating service applications (which can include OWC Wiki, OWC Discussions, RSS, Worklist Community Detail, Worklist SDP, and Worklist Integration)
To configure a relying party:
From the Domain Structure pane, click Security Realms.
The Summary of Security Realms pane displays (see Figure 14-94).
Figure 14-94 Summary of Security Realms Pane

Click your security realm and open the Providers tab and the Credential Mapping subtab.
The Credential Mapping Providers Settings pane displays (see Figure 14-95).
Figure 14-95 Credential Mapping Providers Settings Pane
Click the SAML Credential Mapping Provider you created.
Open the Management tab and the Relying Parties tab on the Settings page for the provider.
The Relying Parties Management Settings pane displays (see Figure 14-96).
Figure 14-96 Relying Parties Management Settings Pane
Click New.
The Create a New Relying Parties page displays (see Figure 14-97).
Figure 14-97 Create a New Relying Party Page
Select Browser/POST as the SAML Profile, and provide a Description (for example, Wiki).
Click OK to save your settings.
On the Relying Parties Management Settings pane, click the Partner ID of the Relying Party you just created (the Partner ID is automatically generated for you).
The Relying Party Settings page displays (see Figure 14-98).
On the Relying Parties page, use the settings shown in Table 14-1 to configure a relying party for the Wiki service. Leave the remaining parameters set to their default values. Click Save when finished.
Table 14-4 Relying Party Settings for Wiki Service
| Parameter | Value | Description |
|---|---|---|
|
Enabled |
Checked |
The state of this SAML Relying Party. |
|
Description |
OWC Wiki |
A short description of this Relying Party |
|
Target URL |
The destination site URL for which authentication is requested (for example: |
|
|
Assertion Consumer URL |
The URL at which an Assertion Consumer Service for this SAML Relying Party can be reached (for example, Indicates the URL to which an assertion or artifact should be POSTed or redirected. Note: If you have checked ACS requires SSL while configuring destination site federation services, then use HTTPS protocol and the SSL port for the |
|
|
Assertion Consumer Properties |
|
One or more optional query parameters, in the form name=value, that will be added to the ACS URL when redirecting to the destination site. In the case of POST profile, these parameters will be included as form variables when using the default POST form. In this case, |
|
Sign Assertions |
Checked |
Specifies whether generated assertions for this SAML Relying Party are signed. |
|
Include KeyInfo |
Checked |
Indicates whether a |
Repeat steps 1 - 8 to configure a relying party for the Worklist Community Detail service using the settings shown in Table 14-1. Leave the remaining parameters on the Relying Parties page set to their default values. Click Save when finished.
Table 14-5 Relying Party Settings for Worklist Community Detail
| Parameter | Value | Description |
|---|---|---|
|
Enabled |
Checked |
The state of this SAML Relying Party. |
|
Description |
Worklist Detail |
A short description of this Relying Party |
|
Target URL |
The destination site URL for which authentication is requested (for example: |
|
|
Assertion Consumer URL |
The URL at which an Assertion Consumer Service for this SAML Relying Party can be reached (for example, Indicates the URL to which an assertion or artifact should be POSTed or redirected. Note: If you have checked ACS requires SSL while configuring destination site federation services, then use https protocol and the SSL port for the SOA managed server. |
|
|
Assertion Consumer Properties |
|
One or more optional query parameters, in the form name=value, that will be added to the ACS URL when redirecting to the destination site. In the case of POST profile, these parameters will be included as form variables when using the default POST form. In this case |
|
Sign Assertions |
Checked |
Specifies whether generated assertions for this SAML Relying Party are signed. |
|
Include KeyInfo |
Checked |
Indicates whether a |
Repeat steps 1 - 8 to configure a relying party for the Worklist SDP service using the settings shown in Table 14-1. Leave the remaining parameters on the Relying Parties pages set to their default values. Click Save when finished.
Table 14-6 Relying Party Settings for Worklist SDP
| Parameter | Value | Description |
|---|---|---|
|
Enabled |
Checked |
The state of this SAML Relying Party. |
|
Description |
WebCenter SDP |
A short description of this Relying Party |
|
Target URL |
The destination site URL for which authentication is requested (for example: |
|
|
Assertion Consumer URL |
The URL at which an Assertion Consumer Service for this SAML Relying Party can be reached (for example, Indicates the URL to which an assertion or artifact should be POSTed or redirected. Note: If you have checked ACS requires SSL while configuring destination site federation services, then use https protocol and the SSL port for the SOA managed server. |
|
|
Assertion Consumer Properties |
|
One or more optional query parameters, in the form name=value, that will be added to the ACS URL when redirecting to the destination site. In the case of POST profile, these parameters will be included as form variables when using the default POST form. In this case |
|
Sign Assertions |
Checked |
Specifies whether generated assertions for this SAML Relying Party are signed. |
|
Include KeyInfo |
Checked |
Indicates whether a |
Repeat steps 1 - 8 to configure a relying party for the Worklist Integration service using the settings shown in Table 14-1. Leave the remaining parameters on the Relying Parties pages set to their default values. Click Save when finished.
Table 14-7 Relying Party Settings for Worklist Integration
| Parameter | Value | Description |
|---|---|---|
|
Enabled |
Checked |
The state of this SAML Relying Party. |
|
Description |
WebCenter SDP |
A short description of this Relying Party |
|
Target URL |
The destination site URL for which authentication is requested (for example: |
|
|
Assertion Consumer URL |
The URL at which an Assertion Consumer Service for this SAML Relying Party can be reached (for example, Indicates the URL to which an assertion or artifact should be POSTed or redirected. Note: If you have checked ACS requires SSL while configuring destination site federation services, then use https protocol and the SSL port for the SOA managed server. |
|
|
Assertion Consumer Properties |
|
One or more optional query parameters, in the form name=value, that will be added to the ACS URL when redirecting to the destination site. In the case of POST profile, these parameters will be included as form variables when using the default POST form. In this case |
|
Sign Assertions |
Checked |
Specifies whether generated assertions for this SAML Relying Party are signed. |
|
Include KeyInfo |
Checked |
Indicates whether a |
Repeat steps 1 - 8 to configure a relying party for the RSS application using the settings shown in Table 14-1. Leave the remaining parameters on the Relying Parties pages set to their default values. Click Save when finished.
Table 14-8 Relying Party Settings for RSS
| Parameter | Value | Description |
|---|---|---|
|
Enabled |
Checked |
The state of this SAML Relying Party. |
|
Description |
RSS |
A short description of this Relying Party |
|
Target URL |
The destination site URL for which authentication is requested (for example: |
|
|
Assertion Consumer URL |
The URL at which an Assertion Consumer Service for this SAML Relying Party can be reached (for example, Indicates the URL to which an assertion or artifact should be POSTed or redirected. Note: If you have checked ACS requires SSL while configuring destination site federation services, then use https protocol and the SSL port for the |
|
|
Assertion Consumer Properties |
|
One or more optional query parameters, in the form name=value, that will be added to the ACS URL when redirecting to the destination site. In the case of POST profile, these parameters will be included as form variables when using the default POST form. In this case |
|
Sign Assertions |
Checked |
Specifies whether generated assertions for this SAML Relying Party are signed. |
|
Include KeyInfo |
Checked |
Indicates whether a <ds:keyinfo> element containing the signing certificate should be included when signing assertions. The default value is |
Repeat steps 1 - 8 to configure a relying party for the Discussions application using the settings shown in Table 14-1. Leave the remaining parameters on the Relying Parties pages set to their default values. Click Save when finished.
Table 14-9 Relying Party Settings for Discussions
| Parameter | Value | Description |
|---|---|---|
|
Enabled |
Checked |
The state of this SAML Relying Party. |
|
Description |
Discussions |
A short description of this Relying Party |
|
Target URL |
The destination site URL for which authentication is requested (for example: |
|
|
Assertion Consumer URL |
The URL at which an Assertion Consumer Service for this SAML Relying Party can be reached (for example, Indicates the URL to which an assertion or artifact should be POSTed or redirected. Note: If you have checked ACS requires SSL while configuring destination site federation services, then use https protocol and the SSL port for the managed server. |
|
|
Assertion Consumer Properties |
|
One or more optional query parameters, in the form name=value, that will be added to the ACS URL when redirecting to the destination site. In the case of POST profile, these parameters will be included as form variables when using the default POST form. In this case |
|
Sign Assertions |
Checked |
Specifies whether generated assertions for this SAML Relying Party are signed. |
|
Include KeyInfo |
Checked |
Indicates whether a <ds:keyinfo> element containing the signing certificate should be included when signing assertions. The default value is |
This section describes how to create and configure source site Federation services.
To configure Source Site Federation Services:
Log in to the WLS Administration Console.
For information on logging into the WLS Administration Console, see Section 1.12.2, "Oracle WebLogic Server Administration Console".
On the Domain Structure pane, expand the Environment node and click Servers.
The Summary of Servers page displays (see Figure 14-99).
Click WLS_Spaces and open the Configuration tab.
Open the Federation Services subtab and the SAML 1.1 Source Site subtab.
The Federation Services Configuration SAML 1.1 Source Site Settings page for the WLS_Spaces server displays (see Figure 14-100).
Figure 14-100 Federation Services Configuration SAML 1.1 Source Site Settings Page
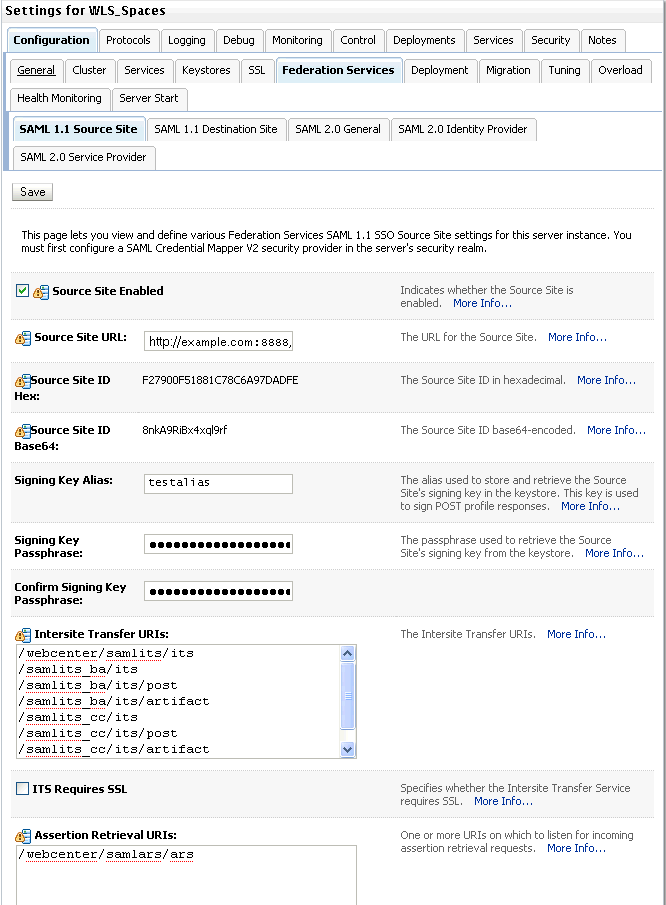
Configure the SAML source site attributes as shown in Figure 14-100. Leave the remaining parameters set to their default values.
Table 14-10 Source Site Federation Services Parameters
| Parameter | Value | Description |
|---|---|---|
|
Source Site Enabled |
Checked |
Allow the WebLogic server instance to serve as a SAML source site by setting Source Site Enabled to true. |
|
Source Site URL |
Set the URL for the SAML source site (for example, |
|
|
Signing Key Alias |
The SAML source site requires a trusted certificate with which to sign assertions. Add this certificate to the keystore and enter the alias (for example, |
|
|
Signing Key Passphrase |
The SAML source site requires a trusted certificate with which to sign assertions. Add this certificate to the keystore and enter the passphrase (for example, |
|
|
Intersite Transfer URIs |
|
Specify the URIs for the Intersite Transfer Service. These URIs are also specified in the configuration of an Asserting Party. |
|
Assertion Retrieval URIs |
|
N/A - URI for Assertion Retrieval Service used when artifact profile is used. |
|
ITS Requires SSL |
Unchecked |
Note: If you check this, then you need to change the Source Site ITS URL specified in the SAML Asserting Party configuration in the SAML Identity provider as HTTPS and the server's SSL port. |
|
ARS Requires SSL |
Unchecked |
Applicable only when Artifact profile is used |
Click Save to save your settings when done.
Restart the WLS_Spaces managed server.
This section describes how to create and configure a SAML Identity Assertion Provider V2 instance (the SAML Identity Assertion provider is not part of the default security realm). This section also describes how to establish trust by registering the source site's SSL certificate in the certificate registry maintained by the SAML Identity Assertion provider.
To create a SAML Identity Assertion Provider
Log in to the WLS Administration Console.
For information on logging into the WLS Administration Console, see Section 1.12.2, "Oracle WebLogic Server Administration Console".
From the Domain Structure pane, click Security Realms.
The Summary of Security Realms pane displays (see Figure 14-101).
Figure 14-101 Summary of Security Realms Pane

Click your security realm.
The Settings page for the security realm displays (see Figure 14-102).
Figure 14-102 Security Realm Settings Page

Open the Providers tab and select the Authentication subtab.
The Authentication Settings pane displays (see Figure 14-103).
Figure 14-103 Authentication Settings Pane
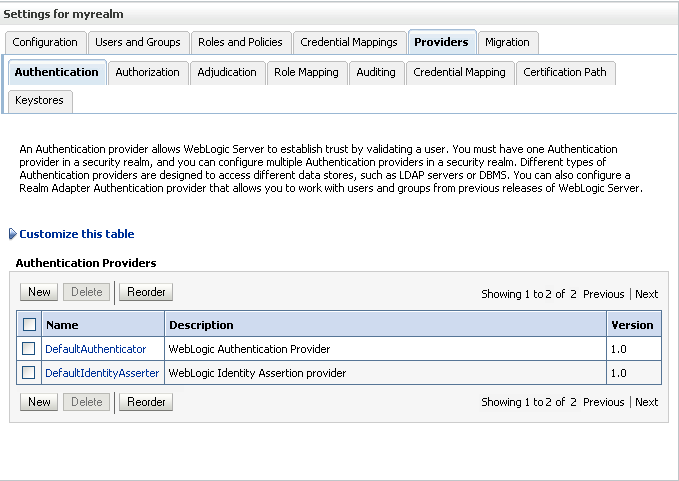
Click New.
The Create a New Authentication Provider page displays (see Figure 14-104).
Figure 14-104 Create a New Authentication Provider Page
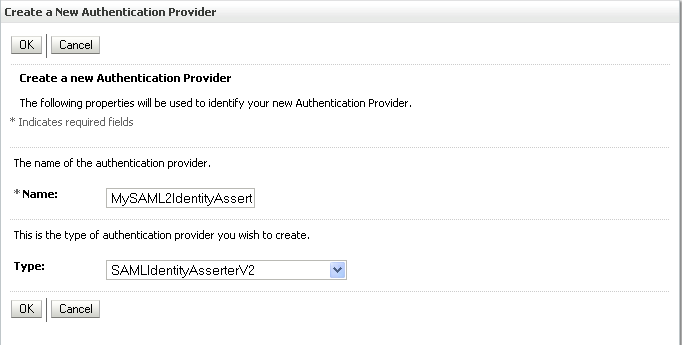
Enter a Name for the new SAML Identity Asserter, and select the Type as SAMLIdentityAsserterV2.
Click OK to save your settings.
Restart the WebLogic Administration server if indicated in the Messages area.
Go to the SOA domain and create a SAML Identity Asserter provider there as well using the steps above.
To configure a certificate for the SAML ID Asserter
Log in to the WLS Administration Console.
For information on logging into the WLS Administration Console, see Section 1.12.2, "Oracle WebLogic Server Administration Console".
From the Domain Structure pane, click Security Realms.
The Summary of Security Realms pane displays (see Figure 14-105).
Figure 14-105 Summary of Security Realms Pane

Click your security realm.
The Settings page for the security realm displays (see Figure 14-106).
Figure 14-106 Security Realm Settings Page

Open the Providers tab and select the Authentication subtab.
The Authentication Settings pane displays (see Figure 14-107).
Figure 14-107 Authentication Settings Pane

Click the SAML Identity Asserter you created and open the Management tab and the Certificates subtab.
The Certificate Settings pane displays (see Figure 14-108).
Click New.
The Create a New Identity Asserter Certificate page displays (see Figure 14-109).
Figure 14-109 Create a New Identity Asserter Certificate Page
Configure the certificate as shown in Table 14-11.
Table 14-11 Certificates Page Parameters
| Parameter | Value | Description |
|---|---|---|
|
alias |
The name to assign to your new Certificate This is the alias of the keystore you created in Section 14.7.3.2.2, "Generating and Registering Certificates". |
|
|
Path |
Specify the path name of the .der file containing the X509 certificate you wish to import. This is the file you created in Section 14.7.3.2.2, "Generating and Registering Certificates". |
Click OK to save your settings.
Repeat the previous step for the SAML ID Asserter created in the SOA domain. Be sure to copy over testalias.der (assuming that this was the name given to your .DER file) from your WebLogic Home to the machine hosting the SOA domain.
To Configure an Asserting Party
Log in to the WLS Administration Console.
For information on logging into the WLS Administration Console, see Section 1.12.2, "Oracle WebLogic Server Administration Console".
From the Domain Structure pane, click Security Realms.
The Summary of Security Realms pane displays (see Figure 14-110).
Figure 14-110 Summary of Security Realms Pane

Click your security realm.
The Settings page for the security realm displays (see Figure 14-111).
Figure 14-111 Security Realm Settings Page

Open the Providers tab and select the Authentication subtab.
The Authentication Settings pane displays (see Figure 14-112).
Figure 14-112 Authentication Settings Pane

Click the SAML Identity Asserter you created and open the Management tab and the Asserting Parties subtab.
The Asserting Parties Settings pane displays (see Figure 14-113).
Figure 14-113 Asserting Parties Settings Pane
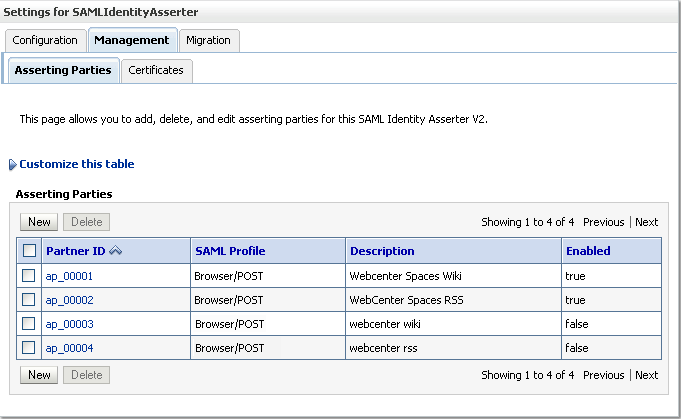
Click New.
The Create a New Asserting Party page displays (see Figure 14-114).
Figure 14-114 Create a New Asserting Party Page
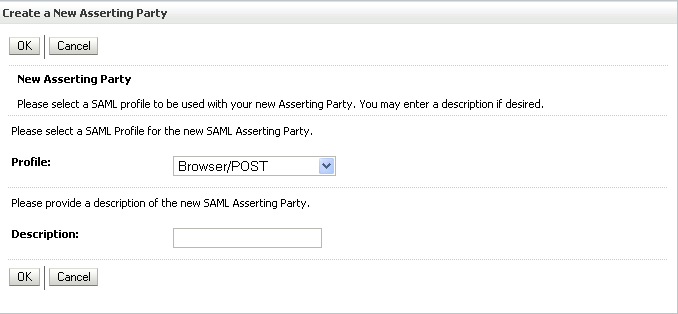
Select the Profile and provide a Description for the Asserting Party.
Use the same SAML profile you chose for the corresponding relying party (for example, Browser/POST).
Click OK to save your settings.
From the Asserting Parties Settings pane, click the Partner ID of the Asserting Party you just created (the Partner ID is assigned automatically).
The Settings page for the new Asserting Party displays (see Figure 14-115).
Figure 14-115 Asserting Party Settings Page
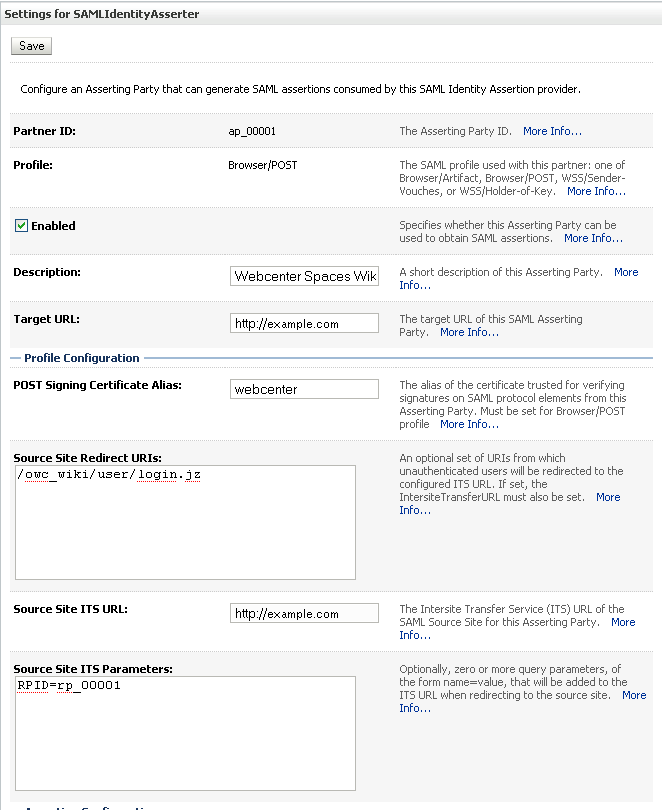
Configure the Asserting Party for the WC domain Wiki service as shown in Table 14-12. For more information, see Table 14-4, "Relying Party Settings for Wiki Service".
Table 14-12 WC Domain - Asserting Party for Wiki
| Parameter | Value | Description |
|---|---|---|
|
Enabled |
Checked |
Specifies whether this Asserting Party can be used to obtain SAML assertions |
|
Description |
A short description of this Asserting Party (for example, |
|
|
Target URL |
The target URL of this SAML Asserting Party (for example, |
|
|
POST Signing Certificate alias |
The alias of the certificate trusted for verifying signatures on SAML protocol elements from this Asserting Party (for example, |
|
|
Source Site Redirect URIs |
|
An optional set of URIs from which unauthenticated users will be redirected to the configured ITS URL. If set, the IntersiteTransferURL must also be set. Note: Based on this setting, when you first access the destination site, you are redirected to the configured ITS URL (which in this case is within the source application), your session is established with the source application and then redirected to the destination site. |
|
Source Site ITS URL |
The Intersite Transfer Service (ITS) URL of the SAML Source Site for this Asserting Party (for example, Used with SSO profiles only, to support the destination site first scenario, whereby a user tries to access a destination site URL prior to being authenticated and is redirected to the source site to be authenticated and obtain a SAML assertion. The Redirect URIs attribute must also be configured for source-site redirection to work. Note: If you check ITS requires SSL in Source Site Federation Services, you must also change the Source Site ITS URL to use HTTPS and the server's SSL port. |
|
|
Source Site ITS parameters |
|
Optionally, zero or more query parameters, of the form name=value, that will be added to the ITS URL when redirecting to the source site. In this case, |
|
Issuer URI |
The issuer URI of the SAML Authority issuing assertions for this SAML Asserting Party (for example, |
|
|
Signature Required |
Checked |
If true, assertions must be signed. If false, signature elements are not required, but will be verified if present. |
|
Assertion Signing Certificate alias |
The alias of the certificate trusted for verifying signatures on assertions from this Asserting Party (for example, testalias). This must be set if Signature Required is checked. The certificate must also be registered in the SAML Identity Asserter's certificate registry. |
Click Save to save your settings.
Repeat steps 1 - 11 using the settings shown in Table 14-13 to configure the Asserting party for the WC domain RSS application.
Table 14-13 WC Domain - Asserting Party for RSS
| Parameter | Value | Description |
|---|---|---|
|
Enabled |
Checked |
Specifies whether this Asserting Party can be used to obtain SAML assertions. |
|
Description |
A short description of this Asserting Party (for example, |
|
|
Target URL |
The target URL of this SAML Asserting Party (for example, |
|
|
POST Signing Certificate alias |
The alias of the certificate trusted for verifying signatures on SAML protocol elements from this Asserting Party (for example, |
|
|
Source Site Redirect URIs |
|
An optional set of URIs from which unauthenticated users will be redirected to the configured ITS URL. If set, the IntersiteTransferURL must also be set. Note: Based on this setting, when you first access the destination site, you are redirected to the configured ITS URL (which in this case is within the source application), your session is established with the source application and then redirected to the destination site. |
|
Source Site ITS URL |
The Intersite Transfer Service (ITS) URL of the SAML Source Site for this Asserting Party (for example, Used with SSO profiles only, to support the destination site first scenario, whereby a user tries to access a destination site URL prior to being authenticated and is redirected to the source site to be authenticated and obtain a SAML assertion. The Redirect URIs attribute must also be configured for source-site redirection to work. Note: If you check ITS requires SSL in Source Site Federation Services, you must also change the Source Site ITS URL to use HTTPS and the server's SSL port. |
|
|
Source Site ITS parameters |
|
Optionally, zero or more query parameters, of the form name=value, that will be added to the ITS URL when redirecting to the source site. In this case |
|
Issuer URI |
The issuer URI of the SAML Authority issuing assertions for this SAML Asserting Party (for example, |
|
|
Signature Required |
Checked |
If true, assertions must be signed. If false, signature elements are not required, but will be verified if present. |
|
Assertion Signing Certificate alias |
The alias of the certificate trusted for verifying signatures on assertions from this Asserting Party (for example, |
Repeat steps 1 - 11 using the settings shown in Table 14-14 to configure the Asserting party for the WC domain Discussions application.
Table 14-14 WC Domain - Asserting Party for RSS
| Parameter | Value | Description |
|---|---|---|
|
Enabled |
Checked |
Specifies whether this Asserting Party can be used to obtain SAML assertions. |
|
Description |
A short description of this Asserting Party (for example, |
|
|
Target URL |
The target URL of this SAML Asserting Party (for example, |
|
|
POST Signing Certificate alias |
The alias of the certificate trusted for verifying signatures on SAML protocol elements from this Asserting Party (for example, |
|
|
Source Site Redirect URIs |
|
An optional set of URIs from which unauthenticated users will be redirected to the configured ITS URL. If set, the IntersiteTransferURL must also be set. Note: Based on this setting, when you first access the destination site, you are redirected to the configured ITS URL (which in this case is within the source application), your session is established with the source application and then redirected to the destination site. |
|
Source Site ITS URL |
The Intersite Transfer Service (ITS) URL of the SAML Source Site for this Asserting Party (for example, Used with SSO profiles only, to support the destination site first scenario, whereby a user tries to access a destination site URL prior to being authenticated and is redirected to the source site to be authenticated and obtain a SAML assertion. The Redirect URIs attribute must also be configured for source-site redirection to work. Note: If you check ITS requires SSL in Source Site Federation Services, you must also change the Source Site ITS URL to use HTTPS and the server's SSL port. |
|
|
Source Site ITS parameters |
|
Optionally, zero or more query parameters, of the form name=value, that will be added to the ITS URL when redirecting to the source site. In this case |
|
Issuer URI |
The issuer URI of the SAML Authority issuing assertions for this SAML Asserting Party (for example, |
|
|
Signature Required |
Checked |
If true, assertions must be signed. If false, signature elements are not required, but will be verified if present. |
|
Assertion Signing Certificate alias |
The alias of the certificate trusted for verifying signatures on assertions from this Asserting Party (for example, |
Change domains to the SOA domain and repeat steps 1 - 11 using the settings shown in Table 14-15 to configure the Asserting Party for the SOA domain Worklist Community Detail service.
Table 14-15 SOA Domain - Asserting Party for Worklist Community Detail
| Parameter | Value | Description |
|---|---|---|
|
Enabled |
Checked |
Specifies whether this Asserting Party can be used to obtain SAML assertions |
|
Description |
A short description of this Asserting Party (for example, |
|
|
Target URL |
The target URL of this SAML Asserting Party (for example, |
|
|
POST Signing Certificate alias |
The alias of the certificate trusted for verifying signatures on SAML protocol elements from this Asserting Party (for example, |
|
|
Source Site Redirect URIs |
|
An optional set of URIs from which unauthenticated users will be redirected to the configured ITS URL. If set, the IntersiteTransferURL must also be set. Note: Based on this setting, when you first access the destination site, you are redirected to the configured ITS URL (which in this case is within the source application), your session is established with the source application and then redirected to the destination site. |
|
Source Site ITS URL |
The Intersite Transfer Service (ITS) URL of the SAML Source Site for this Asserting Party (for example, Used with SSO profiles only, to support the destination site first scenario, whereby a user tries to access a destination site URL prior to being authenticated and is redirected to the source site to be authenticated and obtain a SAML assertion. The Redirect URIs attribute must also be configured for source-site redirection to work. Note: If you check ITS requires SSL in Source Site Federation Services, you must also change the Source Site ITS URL to use HTTPS and the server's SSL port. |
|
|
Source Site ITS parameters |
|
Optionally, zero or more query parameters, of the form name=value, that will be added to the ITS URL when redirecting to the source site. In this case |
|
Issuer URI |
The issuer URI of the SAML Authority issuing assertions for this SAML Asserting Party (for example, |
|
|
Signature Required |
Checked |
If checked, assertions must be signed. If unchecked, signature elements are not required, but will be verified if present. |
|
Assertion Signing Certificate alias |
The alias of the certificate trusted for verifying signatures on assertions from this Asserting Party (for example, |
Change domains to the SOA domain and repeat steps 1 - 11 using the settings shown in Table 14-16 to configure the Asserting Party for the SOA domain Worklist SDP service. For more information see Table 14-6, "Relying Party Settings for Worklist SDP" and Table 14-7, "Relying Party Settings for Worklist Integration".
Table 14-16 SOA Domain - Asserting Party for Worklist SDP
| Parameter | Value | Description |
|---|---|---|
|
Enabled |
Checked |
Specifies whether this Asserting Party can be used to obtain SAML assertions. |
|
Description |
A short description of this Asserting Party (for example, |
|
|
Target URL |
The target URL of this SAML Asserting Party (for example, |
|
|
POST Signing Certificate alias |
The alias of the certificate trusted for verifying signatures on SAML protocol elements from this Asserting Party (for example, |
|
|
Source Site Redirect URIs |
|
An optional set of URIs from which unauthenticated users will be redirected to the configured ITS URL. If set, the IntersiteTransferURL must also be set. Note: Based on this setting, when you first access the destination site, you are redirected to the configured ITS URL (which in this case is within the source application), your session is established with the source application and then redirected to the destination site. |
|
Source Site ITS URL |
The Intersite Transfer Service (ITS) URL of the SAML Source Site for this Asserting Party (for example, Used with SSO profiles only, to support the destination site first scenario, whereby a user tries to access a destination site URL prior to being authenticated and is redirected to the source site to be authenticated and obtain a SAML assertion. The Redirect URIs attribute must also be configured for source-site redirection to work. Note: If you check ITS requires SSL in Source Site Federation Services, you must also change the Source Site ITS URL to use HTTPS and the server's SSL port. |
|
|
Source Site ITS parameters |
|
Optionally, zero or more query parameters, of the form name=value, that will be added to the ITS URL when redirecting to the source site. In this case For more information, see Table 14-6, "Relying Party Settings for Worklist SDP". |
|
Issuer URI |
The issuer URI of the SAML Authority issuing assertions for this SAML Asserting Party (for example, |
|
|
Signature Required |
Checked |
If true, assertions must be signed. If false, signature elements are not required, but will be verified if present. |
|
Assertion Signing Certificate alias |
The alias of the certificate trusted for verifying signatures on assertions from this Asserting Party (for example, |
Change domains to the SOA domain and repeat steps 1 - 11 using the settings shown in Table 14-17 to configure the Asserting Party for the SOA domain Worklist Community Integration service.
Table 14-17 In SOA Domain, Asserting party For Worklist Integration
| Parameter | Value | Description |
|---|---|---|
|
Enabled |
Checked |
Specifies whether this Asserting Party can be used to obtain SAML assertions |
|
Description |
WebCenter Spaces for Worklist SDP |
A short description of this Asserting Party (for example, |
|
Target URL |
The target URL of this SAML Asserting Party (for example, |
|
|
POST Signing Certificate alias |
The alias of the certificate trusted for verifying signatures on SAML protocol elements from this Asserting Party (for example, |
|
|
Source Site Redirect URIs |
|
An optional set of URIs from which unauthenticated users will be redirected to the configured ITS URL. If set, the IntersiteTransferURL must also be set. Note: Based on this setting, when you first access the destination site, you are redirected to the configured ITS URL (which in this case is within the source application), your session is established with the source application and then redirected to the destination site. |
|
Source Site ITS URL |
The Intersite Transfer Service (ITS) URL of the SAML Source Site for this Asserting Party (for example, Used with SSO profiles only, to support the destination site first scenario, whereby a user tries to access a destination site URL prior to being authenticated and is redirected to the source site to be authenticated and obtain a SAML assertion. The Redirect URIs attribute must also be configured for source-site redirection to work. Note: If you check ITS requires SSL in Source Site Federation Services, you must also change the Source Site ITS URL to use HTTPS and the server's SSL port. |
|
|
Source Site ITS parameters |
|
Optionally, zero or more query parameters, of the form name=value, that will be added to the ITS URL when redirecting to the source site. In this case For more information, see Table 14-7, "Relying Party Settings for Worklist Integration". |
|
Issuer URI |
The issuer URI of the SAML Authority issuing assertions for this SAML Asserting Party (for example, |
|
|
Signature Required |
Checked |
If true, assertions must be signed. If false, signature elements are not required, but will be verified if present. |
|
Assertion Signing Certificate alias |
The alias of the certificate trusted for verifying signatures on assertions from this Asserting Party (for example, |
This section describes how to configure the Destination Site Federation Services for the Wiki service, RSS, and the Worklist service on the SOA domain.
To configure the Destination Site Federation Services:
Log in to the WLS Administration Console.
For information on logging into the WLS Administration Console, see Section 1.12.2, "Oracle WebLogic Server Administration Console".
On the Domain Structure pane, expand the Environment node and click Servers.
The Summary of Servers page displays (see Figure 14-116).
Click WLS_Services (the managed server where the Wiki service and Discussions service are deployed) and open the Configuration tab.
Open the Federation Services tab and the SAML 1.1 Destination Site subtab.
The SAML 1.1 Destination Site Settings pane displays (see Figure 14-117).
Figure 14-117 SAML 1.1 Destination Site Settings Pane (Wiki and Discussions)
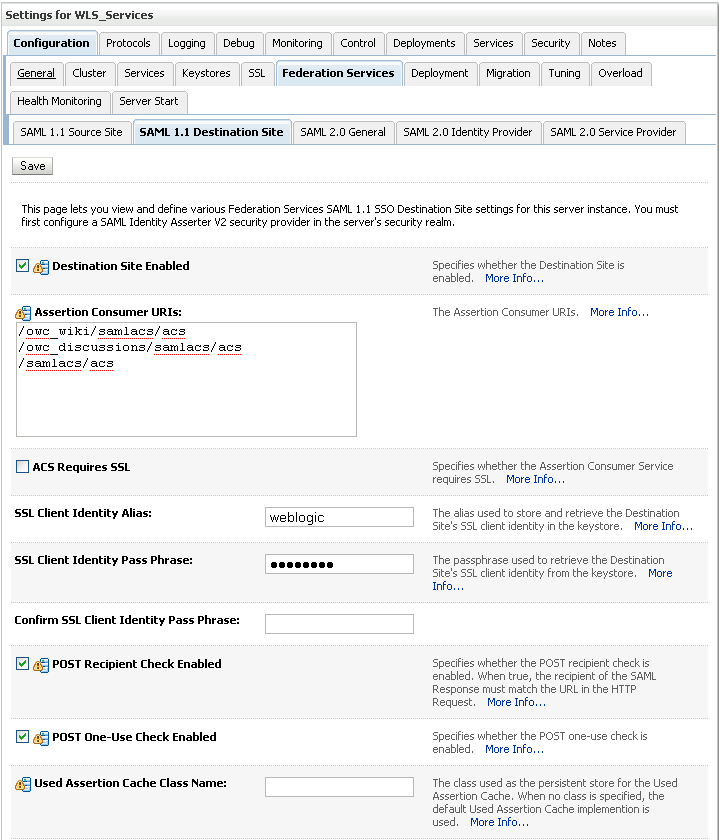
Configure the SAML destination site attributes for the Wiki and Discussions applications as shown in Table 14-18.
Table 14-18 SAML Destination Site Attributes (Wiki and Discussions)
| Parameter | Value | Description |
|---|---|---|
|
Destination Site Enabled |
Checked |
Specifies whether the Destination Site is enabled. |
|
ACS Requires SSL |
Unchecked |
Specifies whether the Assertion Consumer Service requires SSL. If checked, then ensure that the ACS URL specified in the Credential Mapper's relying party uses HTTPS and target server's SSL port. |
|
Assertion Consumer URIs |
|
The Assertion Consumer URIs. In this case, we have chosen for the ACS to reside within the target app so that it uses the same login cookie. |
|
POST Recipient Check Enabled |
Checked |
Specifies whether the POST recipient check is enabled. When checked, the recipient of the SAML Response must match the URL in the HTTP Request. |
|
POST One use Check Enabled |
Checked |
Specifies whether the POST one-use check is enabled. |
Click Save to save your settings, and restart the WLS_Services server so that they take effect.
From the Domain Structure pane, expand the Environment node and click Servers.
Click WLS_Spaces (the managed server where RSS is deployed) and open the Configuration tab.
Open the Federation Services tab and the SAML 1.1 Destination Site subtab.
The SAML 1.1 Destination Site Settings pane displays (see Figure 14-118).
Figure 14-118 SAML 1.1 Destination Site Settings Pane (RSS)
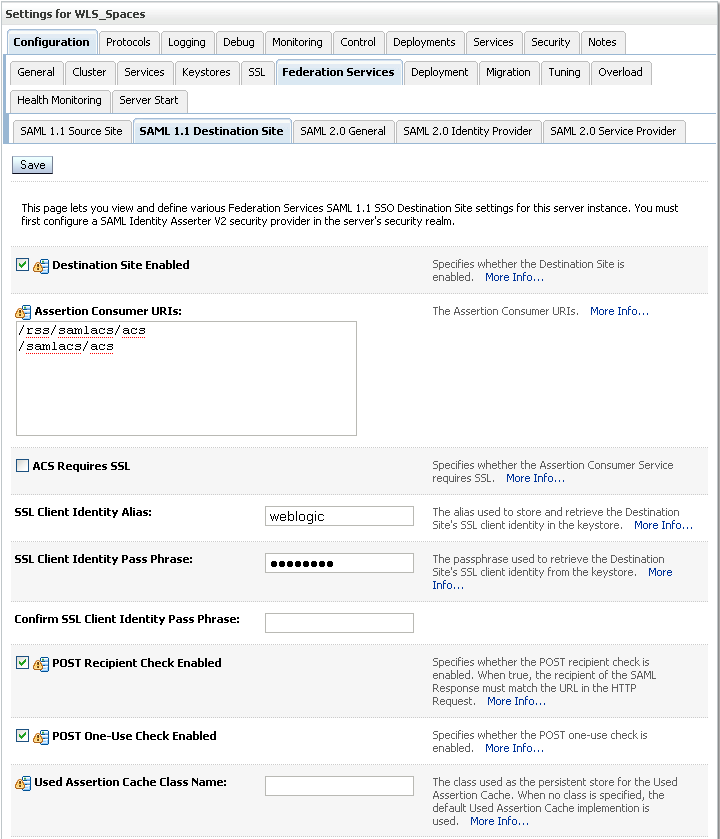
Configure the SAML destination site attributes for RSS as shown in Table 14-19.
Table 14-19 SAML Destination Site Attributes (RSS)
| Parameter | Value | Description |
|---|---|---|
|
Destination Site Enabled |
Checked |
Specifies whether the Destination Site is enabled. |
|
ACS Requires SSL |
Unchecked |
Specifies whether the Assertion Consumer Service requires SSL. If checked, then ensure that ACS URL specified in Credential Mapper's relying party uses https and target server's SSL port. |
|
Assertion Consumer URIs |
(add on top, leave rest as is) |
The Assertion Consumer URIs. In this case, we have chosen for the ACS to reside within the target app so that it uses the same login cookie. |
|
POST Recipient Check Enabled |
Checked |
Specifies whether the POST recipient check is enabled. When true, the recipient of the SAML Response must match the URL in the HTTP Request. |
|
POST One use Check Enabled |
Checked |
Specifies whether the POST one-use check is enabled. |
Click Save to save your settings, and restart the WSL_Spaces server so that they take effect.
Navigate to the SOA domain and then to soa_server1, or the managed server where the Worklist applications are deployed.
Follow the same steps as above to open the SAML 1.1 Destination Site subtab.
The SAML 1.1 Destination Site Settings pane displays (see Figure 14-119).
Figure 14-119 SAML 1.1 Destination Site Settings Pane (Worklist Detail and SDP)
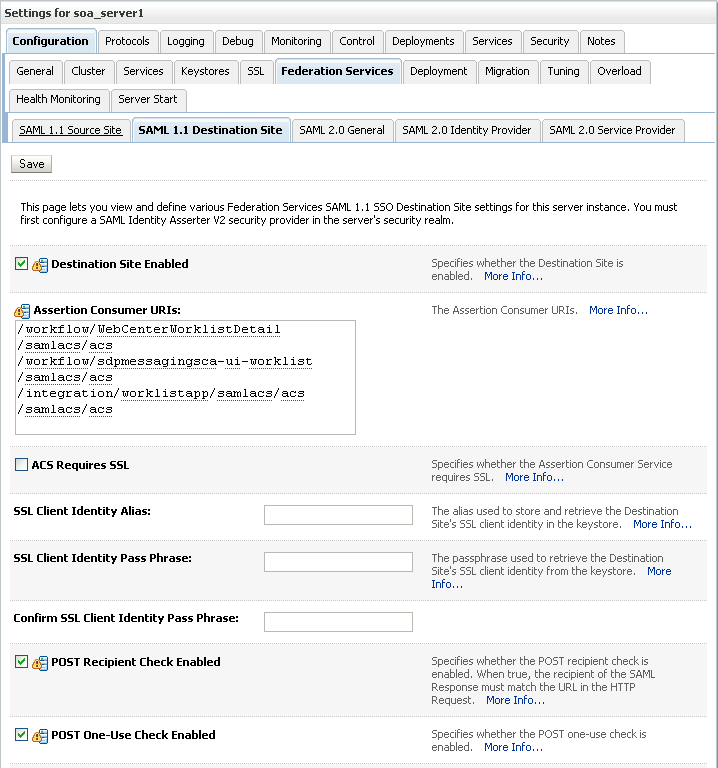
Configure the SAML 1.1 Destination Site attributes for Worklist Detail and SDP as shown in Table 14-20.
Table 14-20 SOA Domain - SAML Destination Site Attributes (Worklist Detail and SDP)
| Parameter | Value | Description |
|---|---|---|
|
Destination Site Enabled |
Checked |
Specifies whether the Destination Site is enabled. |
|
ACS Requires SSL |
Unchecked |
Specifies whether the Assertion Consumer Service requires SSL. If checked, then ensure that ACS URL specified in Credential Mapper's relying party uses HTTPS and the target server's SSL port. |
|
Assertion Consumer URIs |
(add on top, leave rest as is) |
The Assertion Consumer URIs. In this case, we have chosen for the ACS to reside within the target app so that it uses the same login cookie. |
|
POST Recipient Check Enabled |
Checked |
Specifies whether the POST recipient check is enabled. When checked, the recipient of the SAML Response must match the URL in the HTTP Request. |
|
POST One use Check Enabled |
Checked |
Specifies whether the POST one-use check is enabled. |
Click Save to save your settings.
Restart the SOA managed server.
The last step in the process is to check that your single sign-on configuration is working. To do that:
Check that when you try to access the Wiki and RSS applications independently, you are taken to the WebCenter Spaces login page (source site) and then directed to the URL you were trying to access.
Now log into WebCenter Spaces and check that you're not challenged for credentials when:
You access the Wiki from a group space
You access RSS from a list task flow
You click Forum Administration from Group Space Settings > Services > Discussions (assuming this service is provisioned for the group space)
You click a Forum from Group Space Settings from Discussions
To configure the discussions server for SAML single sign-on, be sure to perform these steps:
Deploy the SSO-enabled discussions server as described in Section 14.7.1.7.2, "Deploying the Discussions Server"
Configure a relying party for the Discussions application as described in Section 14.7.3.2.4, "Configuring a Relying Party"
Configure an asserting party for the Discussions application as described in Section 14.7.3.2.6, "Configuring the SAML Identity Assertion Provider".
Configure the Discussions application in the destination site federation services as described in Section 14.7.3.2.7, "Configuring Destination Site Federation Services"
This section describes how to set up single sign-on (SSO) with Microsoft clients, using Windows authentication based on the Simple and Protected Negotiate (SPNEGO) mechanism and the Kerberos protocol, together with the WebLogic Negotiate Identity Assertion provider for the WebCenter Spaces application. This SSO approach enables Microsoft clients (such as browsers), authenticated in a Windows domain using Kerberos, to be transparently authenticated to web applications (such as WebCenter Spaces) in a WebLogic domain based on the same credentials, and without the need to type in their password again.
Cross-platform authentication is achieved by emulating the negotiate behavior of native Windows-to-Windows authentication services that use the Kerberos protocol. In order for cross-platform authentication to work, non-Windows servers (in this case, WebLogic Server) need to parse SPNEGO tokens in order to extract Kerberos tokens, which are then used for authentication.
Understanding Kerberos
Kerberos is a secure method for authenticating a request for a service in a network. The Kerberos protocol comprises three parties: a client, a server and a trusted third party to mediate between them, known as the KDC (Key Distribution Center). Under Kerberos, a server allows a user to access its service if the user can provide the server a Kerberos ticket that proves its identity. Both the user and the service are required to have keys registered with the KDC.
The diagram below describes the basic exchanges that must take place before a client connects to a server.
Figure 14-120 Connecting to a Server Through a Key Distribution Center
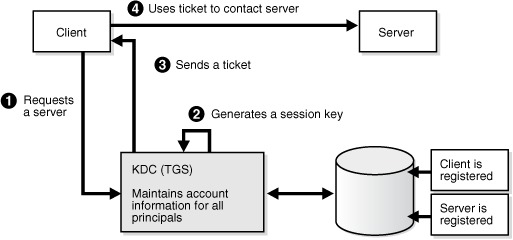
Understanding SPNEGO
SPNEGO (Simple and Protected GSSAPI Negotiation Mechanism) is a GSSAPI "pseudo mechanism" that is used to negotiate one of a number of possible real mechanisms. SPNEGO is used when a client application wants to authenticate to a remote server, but neither end is sure what authentication protocols the other supports. The pseudo-mechanism uses a protocol to determine what common GSSAPI mechanisms are available, selects one, and then dispatches all further security operations to it. This can help organizations deploy new security mechanisms in a phased manner.
SPNEGO's most visible use is in Microsoft's HTTP Negotiate authentication extension. The negotiable sub-mechanisms include NTLM and Kerberos, both used in Active Directory.
This feature enables a client browser to access a protected resource on WLS, and to transparently provide the WLS server with authentication information from the Kerberos database using a SPNEGO ticket. The WLS server is able to recognize the ticket and extract the information from it. WLS then uses the information for authentication and grants access to the resource if the authenticated user is authorized to access it. (Kerberos is responsible for authentication only; authorization is still handled by WLS).
Figure 14-121 SPNEGO-based Authentication
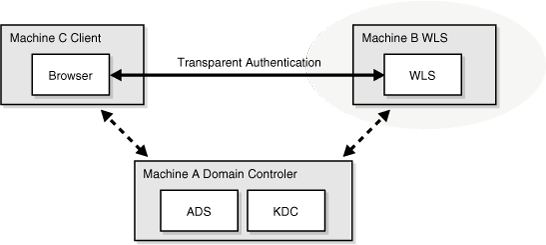
To use SSO with Microsoft clients you need:
A host computer with:
Windows 2000 or later installed
Fully-configured Active Directory authentication service. Specific Active Directory requirements include:
User accounts for mapping Kerberos services
Service Principal Names (SPNs) for those accounts
Key tab files created and copied to the start-up directory in the WebLogic Server domain
WebLogic Server installed and configured properly to authenticate through Kerberos, as described in this section
Client systems with:
Windows 2000 Professional SP2 or later installed
One of the following types of clients:
A properly configured Internet Explorer browser. Internet Explorer 6.01 or later is supported.
.NET Framework 1.1 and a properly configured Web Service client.
Note:
Clients must be logged on to a Windows 2000 domain and have Kerberos credentials acquired from the Active Directory server in the domain. Local logons will not work.Configuring SSO with Microsoft clients requires configuring the Microsoft Active Directory, the client, and the WebLogic Server domain shown in Figure 14-122. For detailed configuration steps and troubleshooting, see "Configuring Single Sign-On with Microsoft Clients" in Oracle Fusion Middleware Securing Oracle WebLogic Server.
Figure 14-122 Configuring SSO with Microsoft Clients
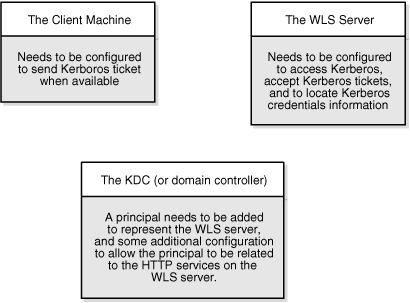
To configure Microsoft clients for SSO:
Configure your network domain to use Kerberos.
Create a Kerberos identification for WebLogic Server.
Create a user account in the Active Directory for the host on which WebLogic Server is running.
Create a Service Principal Name for this account.
Create a user mapping and keytab file for this account.
Choose a Microsoft client (in this case Internet Explorer) and configure it to use Windows Integrated authentication.
Set up the WebLogic Server domain (wc_domain in this case) to use Kerberos authentication.
Create a JAAS login file that points to the Active Directory server in the Microsoft domain and the keytab file created in Step 2.
Configure a Negotiate Identity Assertion provider in the WebLogic Server security realm (see Section 14.7.4.3.1, "Configuring the Negotiate Identity Assertion Provider")
Configure the WLS domain to use the Active Directory Authenticator so that the WebLogic domain uses the same Active Directory of the domain as the identity store. You could also use a different identity store and match the users in this store with the Active Directory users of your domain, but using the Active Directory authenticator is recommended as maintaining two different identity stores risks them getting out of sync. See Section 14.7.4.3.2, "Configuring an Active Directory Authentication Provider")
Caution:
Ensure that only the identity store is configured for Active Directory. The policy and credential stores are not certified for Active Directory.Start the WebLogic Servers (Administration Server and managed servers) using specific start-up arguments. Repeat steps 4 and 5 for the SOA Domain to enable single sign-on for SOA applications.
Configure WebCenter Spaces (see Section 14.7.4.3.3, "Configuring WebCenter Spaces").
This section provides instructions for creating and configuring a Negotiate Identity Assertion provider. The Negotiate Identity Assertion provider enables single sign-on (SSO) with Microsoft clients. The identity assertion provider decodes Simple and Protected Negotiate (SPNEGO) tokens to obtain Kerberos tokens, validates the Kerberos tokens, and maps them to WebLogic users. The Negotiate Identity Assertion provider uses the Java Generic Security Service (GSS) Application Programming Interface (API) to accept the GSS security context via Kerberos.
To configure the Negotiate Identity Assertion provider:
Log in to the WLS Administration Console.
For information on logging into the WLS Administration Console, see Section 1.12.2, "Oracle WebLogic Server Administration Console".
From the Domain Structure pane, click Security Realms.
The Summary of Security Realms pane displays (see Figure 14-123).
Figure 14-123 Summary of Security Realms Pane

Click your security realm.
The Settings page for the security realm displays (see Figure 14-124).
Figure 14-124 Security Realm Settings Page

Open the Providers tab and select the Authentication subtab.
The Authentication Settings pane displays (see Figure 14-125).
Figure 14-125 Authentication Settings Pane

Click New.
The Create a New Authentication Provider pane displays (see Figure 14-126).
Figure 14-126 Create a New Authentication Provider Pane
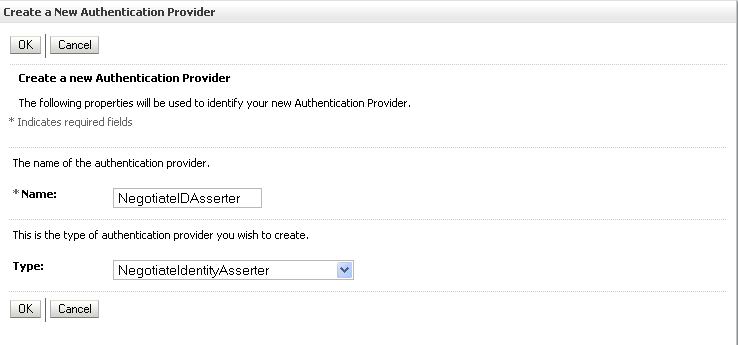
Enter a Name for the identity asserter, and select NegotiateIdentityAsserter as the Type.
Click OK.
Follow the steps below to configure an Active Directory authentication provider using the WebLogic Administration Console.
To configure an Active Directory Authentication provider:
Log in to the WLS Administration Console.
For information on logging into the WLS Administration Console, see Section 1.12.2, "Oracle WebLogic Server Administration Console".
From the Domain Structure pane, click Security Realms.
The Summary of Security Realms pane displays (see Figure 14-127).
Figure 14-127 Summary of Security Realms Pane

Click your security realm.
The Settings page for the security realm displays (see Figure 14-128).
Figure 14-128 Security Realm Settings Page

Open the Providers tab and select the Authentication subtab.
The Authentication Settings pane displays (see Figure 14-129).
Figure 14-129 Authentication Settings Pane

Click New.
The Create a New Authentication Provider pane displays (see Figure 14-130).
Figure 14-130 Create a New Authentication Provider Pane
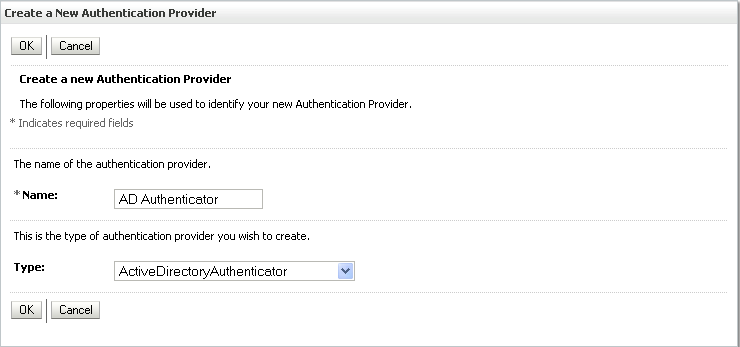
Enter a Name for the authentication provider, and select ActiveDirectoryAuthenticator as the Type.
Click OK.
Click on the authentication provider you just created in the list of providers.
The Settings page for the provider displays (see Figure 14-131).
Open the Configuration tab and the Common subtab.
Set the Control Flag to SUFFICIENT and click Save.
Note:
The Control Flag settings of any other authenticators must also be changed toSUFFICIENT. If there is a pre-existing Default Authenticator that has its Control Flag set to REQUIRED, it must be changed to SUFFICIENT.Open the Provider Specific subtab.
The Provider Specific Settings pane displays (see Figure 14-132).
Figure 14-132 Provider Specific Settings Pane
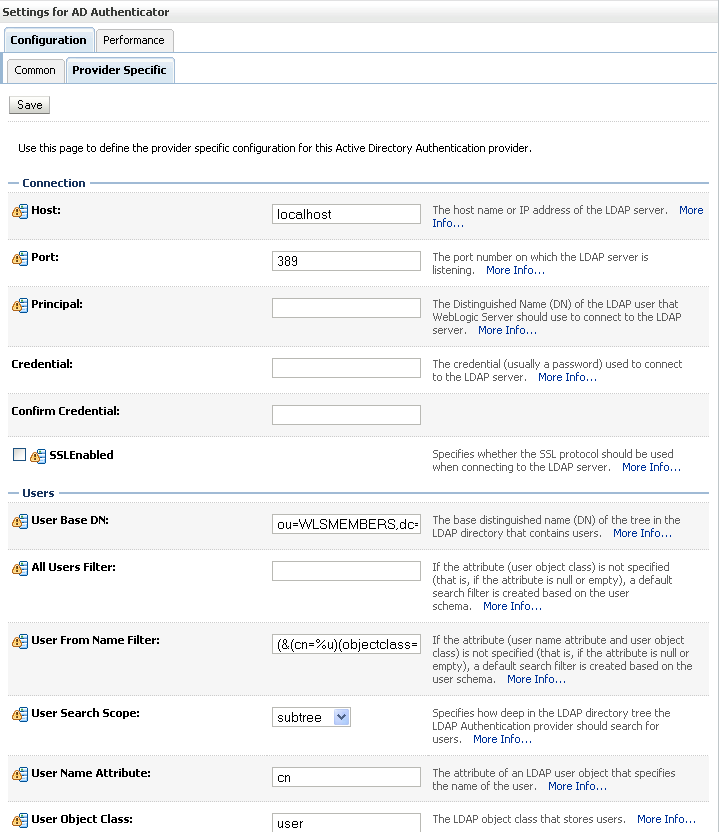
Complete the fields as shown in the table below. Leave the rest of the fields set to their default values.
Table 14-21 Active Directory Authenticator Settings
| Parameter | Value | Description |
|---|---|---|
|
Host: |
The host ID of the LDAP server |
|
|
Port: |
The port number of the LDAP server |
|
|
Principal: |
The LDAP administrator principal |
|
|
Credential: |
||
|
User Base DN: |
The user search base (for example, OU=spnego unit,DC=admin,DC=oracle,DC=com) |
|
|
User From Name Filter: |
(&(cn=%u)(objectclass=user)) |
|
|
User Search Scope: |
subtree |
|
|
User Name Attribute: |
cn |
|
|
User Search Scope: |
user |
|
|
Group Base DN: |
The group search base (same as User Base DN) |
|
|
Group From Name Filter: |
(&(cn=%g)(objectclass=group)) |
|
|
Group Search Scope: |
subtree |
|
|
Static Group Name Attribute: |
cn |
|
|
Static Group Object Class: |
group |
|
|
Static Member DN Attribute: |
member |
|
|
Static Group DNs from Member DN Filter: |
(&(member=%M)(objectclass=group)) |
Click Save.
On the Provider Summary page, reorder the providers in the following order, making sure that their Control Flags are set to SUFFICIENT where applicable:
Negotiate Identity Asserter
ActiveDirectoryAuthenticator (SUFFICIENT)
DefaultAuthenticator (SUFFICIENT)
Other authenticators...
Once you have completed the steps for configuring the Negotiate Identity Assertion Provider and Active Directory Authenticator, and all applications on your WebLogic domain are configured for single sign-on with Microsoft clients in the required domain, a final step is required to provide a seamless single-sign-on experience for your users when accessing WebCenter Spaces. There are two options for doing this:
Turn off public access, by logging into WebCenter Spaces as an administrator and removing view access from the Public role. Once public access has been turned off, accessing the URL http://host:port/webcenter will directly take the user to the authenticated view rather than the default public page which has a login section. This is recommended when users will be accessing WebCenter Spaces only using Internet Explorer, and will be confined to the domain where WNA is set up.
If you need to retain public access to WebCenter Spaces, then the recommendation is to use the oracle.webcenter.osso.enabled flag when starting the WLS_Spaces server. This flag tells WebCenter Spaces that SSO is being used and no login form should be displayed on the default landing page. A login link is displayed instead that the user can click to invoke the SSO authentication where the user will be automatically logged in. If Firefox is used to access WebCenter Spaces within the Windows network configured for WNA, or any browser is used to access WebCenter Spaces from outside the Windows network domain, the user will see the login page after clicking the Login link.
This section describes setting up WS-Security for WebCenter Spaces and related components and includes the following subsections:
Securing Oracle WebLogic Communication Services (OWLCS) with WS-Security
Securing WebCenter Spaces for Applications Consuming Spaces Client APIs with WS-Security
WebCenter Spaces workflows deployed on a SOA instance invoke the WebCenter client APIs that are deployed on a WebCenter Spaces instance. To enable secure Web services calls between these two instances, the administrator must set up WS-Security as described in this section.
This section includes the following subsections:
Note that if the SOA server and WebCenter Spaces share the same domain the steps for generating the keystores are different. If the SOA server and WebCenter Spaces are on different domains follow the instructions in Section 14.8.1.1, "Generating the Keystores"; if the SOA server and WebCenter Spaces share the same domain follow the instructions in Section 14.8.1.2, "Generating the Keystores When the SOA Server and WebCenter Share the Same Domain." The remaining steps for Registering the Keystores and Updating the Credential Stores are the same in both cases.
This section describes how to generate the keystores, and import the trusted certificates of the WebCenter keystore to the Oracle SOA instance using webcenter_spaces_ws as the alias.
This section includes the following subsections:
Importing the Trusted Certificate of the WebCenter Spaces Keystore to the SOA Keystore
Importing the Trusted Certificate of the SOA Instance in the WebCenter Instance
For information on how to generate keystores, see Section 14.8.4.3, "Setting Up the Keystores". In this case, WebCenter is the producer, and BPEL is the consumer.
After you have created keystores in the WebCenter Spaces instance, import the trusted certificate of the alias webcenter_spaces_ws to the SOA instance.
Note:
The alias parameter must always be set towebcenter_spaces_ws. If you change the alias, the security setup will not work correctly.To import the trusted certificate in the SOA keystore:
Go to JAVA_HOME/bin/.
Run the following command:
keytool -importcert -alias webcenter_spaces_ws -file certificate_file -keystore keystore_name -storepass keystore_password
Where:
certificate_file is the file name or path for the WebCenter's certificate file (for example, webcenter.cer)
keystore_name is the keystore name in the SOA instance (for example, bpel.jks)
keystore_password is the keystore password for the SOA instance's keystore.
This section describes how to generate a key pair in the SOA instance.
To generate the key pair:
Go to JAVA_HOME/bin/.
Run the following command:
keytool -genkeypair -keyalg RSA -dname "bpel_dname" -alias bpel_alias-keypass key_password -keystore keystore -storepass keystore_password-validity days_valid
Where:
bpel_dname is dname of the SOA instance (for example, cn=bpel,dc=example,dc=com).
bpel_alias is the alias in keystore for the SOA instance (for example, bpel).
key_password is the keystore password for the new public key.
keystore is the keystore name for the SOA instance (for example, bpel.jks).
keystore_password is the keystore password of the SOA instance's keystore.
days_valid is the number of days for which the key password is valid (for example, 1024).
This section describes how to export public key of the SOA instance.
To export the public key:
Go to JAVA_HOME/bin/.
Run the following command:
keytool -exportcert -v -alias bpel_alias -keystore keystore -storepass keystore_password -rfc -file certificate_file
Where:
bpel_alias is the alias in the keystore of the SOA instance (for example, bpel).
keystore is the keystore name of the SOA instance (for example, bpel.jks).
keystore_password is the keystore password for the keystore in the SOA instance.
certificate_file is the file name for the certificate in which the key is to be exported. For example, bpel.cer.
To import the trusted certificate of the SOA instance in the WebCenter instance:
Go to JAVA_HOME/bin/.
Run the following command:
keytool -importcert -alias bpel_alias -file certificate_file -keystore keystore_name -storepass keystore_password
Where:
certificate_file is the exported certificate file from the SOA instance (for example, bepl.cer).
bpel_alias is the alias in keystore of the SOA instance (for example, bpel).
keystore_name is the keystore name of the WebCenter instance (for example, webcenter.jks).
keystore_password is the keystore password for keystore in the SOA instance.
This section describes how to generate the keystores and import the trusted certificate of the WebCenter keystore to the Oracle SOA instance using webcenter_spaces_ws as the alias when both share the same domain. After generating the producer keystore pair, continue by registering the keystores as shown in Section 14.8.1.3, "Registering the Keystores," and updating the Credential Store as shown in Section 14.8.1.4, "Updating the Credential Stores."
To create the Java keystores for the producer:
Go to JDEV_HOME/jdk/bin and open a command prompt.
Using keytool, generate a key pair:
keytool -genkeypair -keyalg RSA -dname "producer_dname" -alias producer_alias -keypass key_password -keystore keystore -storepass keystore_password -validity days_valid
Where:
producer_dname is the name of the producer (for example, cn=producer,dc=example,dc=com)
producer_alias is the alias of the producer (for example, producer)
key_password is the password for the new public key, (for example, welcome1)
keystore is the keystore name, (for example, producer.jks)
keystore_password is the keystore password, (for example, welcome1)
days_valid is the number of days for which the key password is valid (for example, 365)
Note:
You must use the-keyalg parameter and specify RSA as its value as shown above as the default algorithm (DSA) used by keytool for generating the key is incompatible with Oracle WebServices Security Manager requirements.Export the certificate of the producer:
keytool -exportcert -v -alias producer_alias -keystore keystore -storepass keystore_password -rfc -file certificate_file
Where:
producer_alias is the alias of the producer (for example, producer)
keystore is the keystore name (for example, producer.jks)
keystore_password is the keystore password (for example, welcome1)
certificate_file is the file name for the certificate to export the key to (for example, producer.cer)
Import the certificate to the same keystore using the alias webcenter_spaces_ws. You must use this alias or the end-to-end integration with workflows will fail.
keytool -importcert -alias webcenter_spaces_ws -file certificate_file -keystore keystore -storepass keystore_password
Where:
certificate_file is the file name or path for the producer's certificate file (for example, ../producer/producer.cer)
keystore is the keystore name (for example, producer.jks)
keystore_password is the keystore password (for example, welcome1)
This section describes how to register keystores in the SOA and WebCenter Spaces instances. This section includes the following subsections:
Before they can be used, the keystores must also be registered. Follow the steps below to register the keystores in the WebCenter Spaces instance.
To register the keystores in the WebCenter Spaces instance:
Change directories to WEBCENTER_HOME/user_projects/domains/<domain_name>/config/fmwconfig where the WebCenter instance is installed.
Copy the WebCenter keystore that you created earlier, for example, webcenter.jks, by running the following command:
cp webcenter.jks .
In the jps-config.xml file, set the keystore location to the name of the keystore (for example, webcenter.jks).
<serviceInstance name="keystore" provider="keystore.provider"
location="./webcenter.jks">
<description>Default JPS Keystore Service</description>
<property name="keystore.type" value="JKS"/>
<property name="keystore.csf.map" value="oracle.wsm.security"/>
<property name="keystore.pass.csf.key" value="keystore-csf-key"/>
<property name="keystore.sig.csf.key" value="enc-csf-key"/>
<property name="keystore.enc.csf.key" value="enc-csf-key"/>
Keystores must be registered before they can be used. You can register keystores using command line, as described in this section or through Fusion Middleware Control, as described in Section 14.8.4.3.2, "Configuring the Keystores". If you choose to register keystores using Fusion Middleware Control, make sure that property names are identical to those described in this section.
To register keystores using the command line tool:
cd SOA_HOME/user_projects/domains/<domain_name>/config/fmwconfig where the SOA instance is installed.
Copy the SOA keystore that you created earlier, for example, bpel.jks, by running the following command:
cp bpel.jks .
In the jps-config.xml file, set the keystore location to the name of the keystore, for example, webcenter.jks.
<serviceInstance name="keystore" provider="keystore.provider" location="./bpel.jks">
<description>Default JPS Keystore Service</description>
<property name="keystore.type" value="JKS"/>
<property name="keystore.csf.map" value="oracle.wsm.security"/>
<property name="keystore.pass.csf.key" value="keystore-csf-key"/>
<property name="keystore.sig.csf.key" value="enc-csf-key"/>
<property name="keystore.enc.csf.key" value="enc-csf-key"/>
After registering the keystores for the SOA and WebCenter instances, you must update the credential store of these instances to add the keystores, signing, encryption keys, and passwords. You can update the credential stores using the createCred WLST command or Fusion Middleware Control.
This section includes the following sub sections:
Updating the Credential Store in the WebCenter Spaces Instance Using WLST
Updating the Credential Store in the WebCenter Spaces Instance Using Fusion Middleware Control
Updating the Credential Store in the SOA Instance Using WLST
Updating the Credential Store in the SOA Instance Using Fusion Middleware Control
To update the credential store using WLST, see the section "createCred" in Oracle Fusion Middleware WebLogic Scripting Tool Command Reference. Use the following example values to add keystore-csf-key, enc-csf-key, and sign-csf-key encryption keys. Before running the command, be sure to back up the cwallet.sso file.
Example 14-8 keystore-csf-key
createCred(map="oracle.wsm.security",key="keystore-csf-key",user="keystore-csf-key",password="password",desc="Enc Password")
This section describes how to update credential store of the WebCenter Spaces instance using Fusion Middleware Control. Before running the command, be sure to back up the cwallet.sso file located in the SOA_HOME/user_projects/domains/<user_domain>/config/fmwconfig directory.
To update the credential store using Fusion Middleware Control:
Open Fusion Middleware Control and log into the target domain.
For information on logging into Fusion Middleware Control, see Section 6, "Starting Enterprise Manager Fusion Middleware Control".
From the WebLogic Domain menu, select Security and then Credentials.
On the Credentials page, click Create Map.
In the Create Map dialog, enter oracle.wsm.security as the map name. Click OK.
On the Credentials page, click Create Key, to create keystore-csf-key.
In the Create Key dialog, from the Select Map field, select oracle.wsm.security.
In the Key field, enter keystore-csf-key.
From the Type field, select Password, if it is not already selected.
In the User Name field, enter keystore-csf-key.
In the Password field, enter password of the keystore used for the WebCenter instance.
Optionally, enter a description and click OK.
On the Credentials page, click Create Key, to create sign-csf-key.
In the Create Key dialog, in the Key field, enter sign-csf-key.
In the User Name field, enter the public key alias of the keystore used in WebCenter instance. For example, webcenter.
In the Password field, enter password of the public key used in the WebCenter instance.
Optionally, enter a description and click OK.
On the Credentials page, click Create Key, to create enc-csf-key.
In the Create Key dialog, in the Key field, enter enc-csf-key.
In the User Name field, enter the public key alias of the keystore used in the WebCenter Spaces instance. For example, webcenter.
In the Password field, enter the password of the public key used in the WebCenter instance.
Optionally, enter a description and click OK.
Restart both Administration server and managed servers as described in Section 8.2, "Starting and Stopping Managed Servers for WebCenter Application Deployments".
Update the credential store using the WLST createCred command. Use the following example values to add keystore-csf-key, enc-csf-key, and sign-csf-key encryption keys.
Example 14-11 keystore-csf-key
createCred(map="oracle.wsm.security",key="keystore-csf-key",user="keystore-csf-key",password="password",desc="Enc Password")
This section describes how to update the credential store in the SOA instance using Fusion Middleware Control.
To update the credential store using Fusion Middleware Control:
Open Fusion Middleware Control and log into the target domain.
For information on logging into Fusion Middleware Control, see Section 6, "Starting Enterprise Manager Fusion Middleware Control".
From the WebLogic Domain menu, select Security and then Credentials.
On the Credentials page, click Create Map.
In the Create Map dialog, enter oracle.wsm.security as the map name. Click OK.
On the Credentials page, click Create Key, to create keystore-csf-key.
In the Create Key dialog, from the Select Map field, select oracle.wsm.security.
In the Key field, enter keystore-csf-key.
From the Type field, select Password, if it is not already selected.
In the User Name field, enter keystore-csf-key.
In the Password field, enter password of the keystore used for the SOA instance.
Optionally, enter a description and click OK.
On the Credentials page, click Create Key, to create sign-csf-key.
In the Create Key dialog, in the Key field, enter sign-csf-key.
In the User Name field, enter the public key alias of the keystore used in SOA instance. For example, bpel.
In the Password field, enter password of the public key used in the SOA instance.
Optionally, enter a description and click OK.
On the Credentials page, click Create Key, to create enc-csf-key.
In the Create Key dialog, in the Key field, enter enc-csf-key.
In the User Name field, enter the public key alias of the keystore used in SOA instance. For example, bpel.
In the Password field, enter password of the public key used in the SOA instance.
Optionally, enter a description and click OK.
By default, the Oracle WebCenter Discussions allows unsecured Web service calls. You can optionally configure Oracle WebCenter Discussions to enable the Web Services Security (WS-Security) trusted authentication. WS-Security establishes a trust relationship between your WebCenter application and Oracle WebCenter Discussions so that your WebCenter application can pass the user identity information to the server without knowing the user's credentials.
To configure WS-Security on the Discussions server side, you must create a keystore certificate properties file, specify it for the ClassLoader, modify the system property webservices.soap.custom.crypto.fileName, and delete the webservices.soap.permissionHandler.className system property.
To enable the WS-Security trusted authentication for Oracle WebCenter Discussions, you must:
Obtain a valid client and server certificate as described in Section 14.8.4.3, "Setting Up the Keystores".
Configure WS-Security-related properties on the Discussions server.
Add the WS-Security-related properties in your Oracle WebCenter Discussions connection created for integrating Discussions and Announcements services into your WebCenter applications.
These configuration steps are described in the following sub-sections:
The server-side keystore certificate configuration must be stored in a properties file (keystore.properties) and specified as a system property on the Discussions server. The properties file then must be loaded in the ClassLoader for the WS-Secure Handler to pick it up.
To create the properties file
Create a properties file with the following entries:
org.apache.ws.security.crypto.provider= <Specify your crypto provider (typically org.apache.ws.security.components.crypto.Merlin)> org.apache.ws.security.crypto.merlin.keystore.type=<Specify the keystore type (either jks or pks)> org.apache.ws.security.crypto.merlin.keystore.password=<Specify the keystore password of your server certificate> org.apache.ws.security.crypto.merlin.keystore.alias=<Specify the keystore alias of your server certificate> org.apache.ws.security.crypto.merlin.file=<Specify the absolute path of your server certificate file. For example, C:\Programs\Discussions\server_public_certs.keystore>
Save the file as keystore.properties.
There are two ways you can choose either way to specify your keystore.properties file based on your setup. This is recommended way when using Clustered Discussions Server installation in Linux to use a same file mounted across different servers.
To specify the properties file for ClassLoader, do one of the following:
Specify the properties file as the CLASSPATH in setDomainEnv.sh.
For Linux:
Place the keystore.properties file in a directory (for example, . /home/user/keystore/)
Open MW_HOME/user_projects/domains/wc_domain/bin/setDomainEnv.sh.
Towards the end of the file, add the following lines to specify this directory as the CLASSPATH.
if [ "${CLASSPATH}" != "" ] ; then
CLASSPATH="${ CLASSPATH}${CLASSPATHSEP}/home/user/keystore/"
export CLASSPATH
else
CLASSPATH="/home/user/keystore/"
export CLASSPATH
fi
Note that the CLASSPATH directory name must end with "/".
For Windows:
Place the keystore.properties file in a directory (for example, c:\keystore\).
Open MW_HOME\user_projects\domains\wc_domain\bin\setDomainEnv.cmd.
Towards the end of the file, add the following lines to specify this directory in CLASSPATH.
if NOT "%CLASSPATH%"=="" (
set CLASSPATH=%CLASSPATH%;c:\keystore\
) else (
set CLASSPATH=c:\keystore\
)
Note that the CLASSPATH directory name must end with "\".
Or add the keystore.properties file to a .JAR file and place the .JAR file in your MW_HOME/user_projects/domains/wc_domain/lib directory.
To update your system properties:
Log in to the Oracle WebCenter Discussions Admin Console at the following URL:
http://host:port/owc_discussions/admin
Where host and port are the address and the port number of the server where you deployed Oracle WebCenter Discussions (for example, http://localhost:7001/owc_discussions).
Click System Properties under Forum System. This displays the Jive Properties page.
Modify the system property webservices.soap.custom.crypto.fileName and specify the properties file that you created (i.e., keystore.properties).
Be sure to specify the name of file, and not the directory or .JAR name.
Under All Properties, click the delete icon next to the webservices.soap.permissionHandler.className system property.
Click OK.
Extract the owc_discussions.war file from MW_HOME/Oracle_WC1/discussionserver/owc_discussions.ear/or owc_discussions_sso.ear, then extract WEB-INF/classes/jive_extra_startup_content.xml.
Open WEB-INF/classes/jive_extra_startup_content.xml and delete or comment out the following entries:
<entry name="webservices.soap.permissionHandler.className" overwrite="false" readonly="false">com.jivesoftware.webcenter.webservices.OraclePermissionHandler</entry> <entry name="webservices.soap.custom.crypto.fileName" overwrite="false" readonly="false">crypto.properties</entry>
Save the file.
Repackage the .WAR file with the updated WEB-INF/classes/jive_extra_startup_content.xml file, and then repackage the .EAR file with the updated .WAR file.
Delete the existing installation and install the newly generated.EAR file.
Restart the WLS_Services managed server.
After setting the system properties, your WebCenter application also needs to supply the WS-Security client certificate through the connection settings for Discussion Forum and Announcement Server as described in Section 11.1, "Setting Up Connections for the Discussions and Announcements Services".
Follow the steps below to configure WS-Security for Oracle WebLogic Communication Services (OWLCS):
Provide the policyURI when creating the Instant Messaging and Presence (IMP) connection.
When you create the connection to the WS-Security enabled OWLCS server, you must provide the policyURI. The value of policyURI should be set to oracle/wss11_saml_token_with_message_protection_client_policy. If no policyURI is supplied, the application will use a non-secure connection. See also Section 11.2.3, "Registering Instant Messaging and Presence Servers".
Supply an alias name for the private key to the IMP connection.
Provide an additional property in the WebCenter IMP connection named recipient.alias. Set the value of this property to the alias under which to import the OWLCS certificate. Ensure that this value is unique and is not used already by some other service. If no alias name is supplied, the application uses the default value webcenter_owlcs. See also Section 11.2.3.1, "Additional IMP Connection Properties".
Determine the private key in the OWLCS keystore (located on the OWLCS instance at DOMAIN_HOME/config/fmwconfig).
Use the following command to list the keystore contents:
keytool -list -v -keystore Serversidekeystore.jks -storepass password
Find the entry with the Entry type set to keyEntry. The alias name of this entry is the private key (orakey by default).
Export the private key from the OWLCS server keystore.
Use the following command to export orakey to a certificate file (for example, orakey.cer).
keytool -exportcert -v -alias orakey -keystore Serversidekeystore.jks
-storepass welcome -rfc -file orakey.cer
Determine the private key in the WebCenter keystore (on the WebCenter instance at DOMAIN_HOME/config/fmwconfig).
If no keystore is found, proceed to step 6. Otherwise, use the following command to list the keystore contents:
keytool -list -v -keystore default-keystore.jks -storepass welcome
Find the entry with Entry type set to keyEntry or PrivateKeyEntry. The alias name of this entry is the private key.
If no such entry is found, proceed to step 6. Otherwise, continue at step 7.
Generate a private key on WebCenter.
Go to DOMAIN_HOME/config/fmwconfig in your WebCenter installation and run the following command to add a key pair to the keystore. The command creates a keystore named default-keystore.jks if it doesn't already exist, and adds a new private key entry with alias orasig and the password set to welcome1. You can optionally change the alias, password and domain name command when you run the command.
keytool -genkeypair -keyalg RSA -dname "cn=consumer,dc=example,dc=com" -alias orasig -keypass welcome1 -keystore default-keystore.jks -storepass welcome1 -validity 360
Configure OWLCS on your WebCenter instance to use the private key.
Run the WLST createCred command substituting the user and password keys in the first two commands with your private key alias and password.
createCred(map='oracle.wsm.security', key='enc-csf-key', user='orasig', password='welcome1', desc='EncryptionKey') createCred(map='oracle.wsm.security', key='sign-csf-key', user='orasig', password='welcome1', desc='SigningKey') createCred(map='oracle.wsm.security', key='keystore-csf-key', user='owsm', password='welcome1', desc='KeystoreKey')
Export the private key pair to a certificate.
Export the private key found in step 5 or created in step 6 to a certificate file using the following command:
keytool -exportcert -v -alias orasig -keystore default-keystore.jks -storepass welcome1 -rfc -file orasig.cer
Import the certificate generated on the OWLCS Server to the WebCenter keystore.
Copy the certificate generated in step 4 to a temporary location on the WebCenter instance. Import the certificate in the WebCenter instance using the alias name from step 2.
Use the following command to import the certificate in the WebCenter keystore:
keytool -importcert -alias webcenter_owlcs -file orakey.cer -keystore default-keystore.jks -storepass welcome1
Import the WebCenter certificate on the OWLCS instance.
Copy the certificate created in step 8 to a temporary location on the OWLCS instance. Go to DOMAIN_HOME/config/fmwconfig and import the certificate in the keystore under a meaningful alias (for example, webcenter_key) using the following command:
keytool -importcert -alias webcenter_key -file orasig.cer -keystore Serversidekeystore.jks -storepass welcome
The following sections describe how to secure access to JSR-168 standards-based WSRP portlets from WebCenter applications:
For a conceptual overview of securing WSRP producers, see "Securing Identity Propagation Through WSRP Producers with WS-Security" in the Oracle Fusion Middleware Developer's Guide for Oracle WebCenter.
Before you configure the producer for WS-Security, you must first deploy your standards-compliant portlet producer to an Oracle WebLogic managed server by performing the steps described in Section 12.8, "Deploying Portlet Producer Applications".
This section describes how to attach a security policy to a WSRP producer endpoint. The following policies are supported for WSRP producers:
Username token with password
wss10_username_token_with_message_protection_service_policy
This policy enforces message-level protection (message integrity and confidentiality) and authentication for inbound SOAP requests in accordance with the WS-Security 1.0 standard. It uses WS-Security's Basic 128 suite of asymmetric key technologies (specifically, RSA key mechanism for message confidentiality, SHA-1 hashing algorithm for message integrity, and AES-128 bit encryption). The keystore is configured through the security configuration. Authentication is enforced using credentials in the WS-Security UsernameToken SOAP header. The Subject is established against the currently configured identity store.
Username token without password
wss10_username_id_propagation_with_msg_protection_service_policy
This policy enforces message level protection (message integrity and confidentiality) and identity propagation for inbound SOAP requests using mechanisms described by the WS-Security 1.0 standard. Message protection is provided using WS-Security's Basic 128 suite of asymmetric key technologies (specifically, RSA key mechanisms for confidentiality, SHA-1 hashing algorithm for integrity, and AES-128 bit encryption). Identity is set using the user name provided by the UsernameToken WS-Security SOAP header. The Subject is established against the currently configured identity store.
SAML token
There are two SAML token policies:
SAML token with message integrity:
wss10_saml_token_with_message_integrity_service_policy
This policy provides message-level integrity protection and SAML-based authentication for inbound SOAP requests in accordance with the WS-Security 1.0 standard. It uses WS-Security's Basic 128 suite of asymmetric key technologies, specifically RSA key mechanisms for message confidentiality, and SHA-1 hashing algorithm for message integrity.
SAML token with message protection:
wss10_saml_token_with_message_protection_service_policy
This policy enforces message-level protection and SAML-based authentication for inbound SOAP requests in accordance with the WS-Security 1.0 standard. It uses WS-Security's Basic 128 suite of asymmetric key technologies, specifically RSA key mechanisms for message confidentiality, SHA-1 hashing algorithm for message integrity, and AES-128 bit encryption.
The keystore is configured through the security configuration. It extracts the SAML token from the WS-Security binary security token, and uses those credentials to validate users against the configured identity store.
To attach a policy to a producer endpoint
Open Fusion Middleware Control and log into the target domain.
For information on logging into Fusion Middleware Control, see Section 6, "Starting Enterprise Manager Fusion Middleware Control".
In the Navigation pane, expand the Application Deployments node, and click the producer to attach a policy to.
From the Application Deployment menu, select Web Services.
The Web Services Summary page for the producer displays (see Figure 14-133).
Open the Web Service Endpoint tab and click the endpoint to which to attach a policy.
Note:
Only the markup service ports should be secured (WSRP_V2_Markup_Service and WSRP_V1_Markup_Service).The Web Service Endpoints page for the producer displays (see Figure 14-134).
Open the Policies tab to display the currently attached policies for the producer (see Figure 14-135).
Figure 14-135 Web Services Endpoint Policies Page
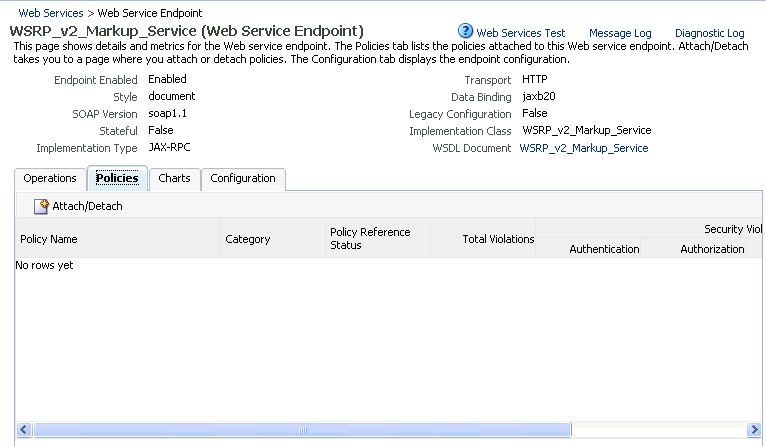
Click Attach/Detach to add or remove a policy.
The Attach/Detach Policies page is shown listing the available policies and their descriptions (see Figure 14-136).
Figure 14-136 Attach/Detach Policies Page
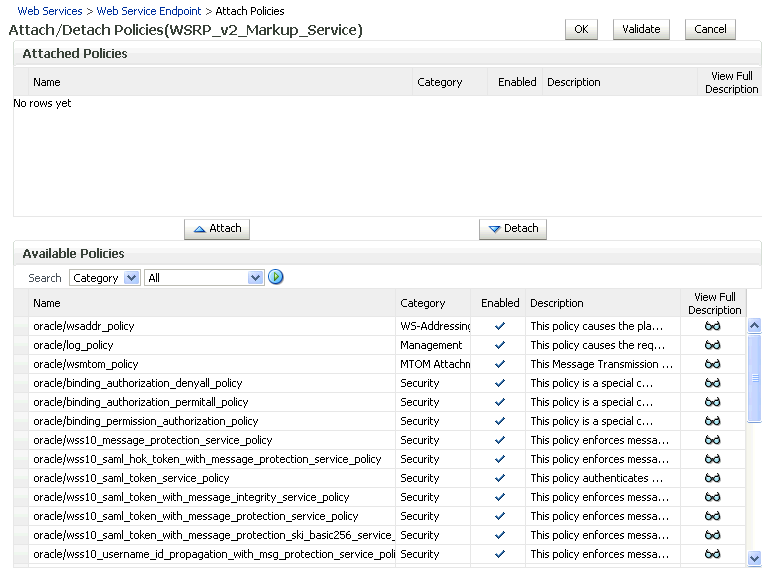
Under Available Policies, select Category and Security as the policy category to search, and click the Search icon to list the security policies.
Select the policies to attach and click Attach. Use the Ctrl key to select multiple policies.
The policies appear in the list under Attached Policies (see Figure 14-137).
Figure 14-137 Attach Detach Policy Page with Policy Attached
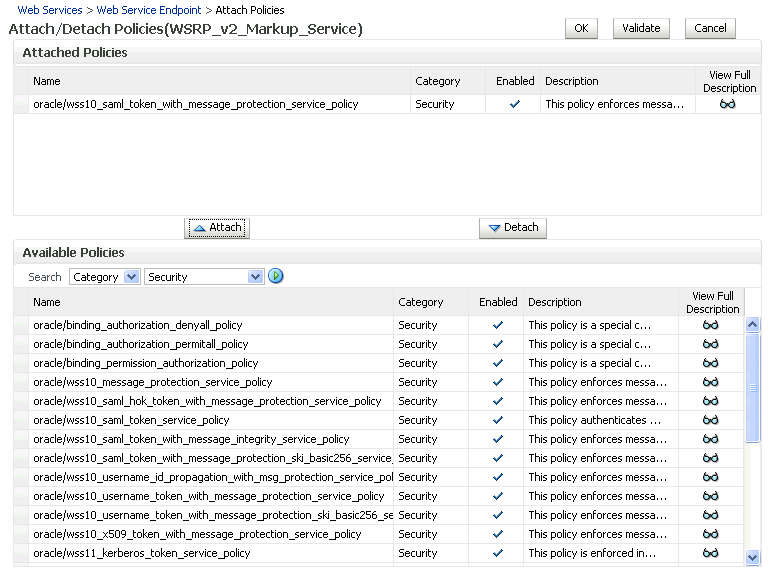
When finished adding polices to attach to the producer endpoint, click OK.
The security credentials of the WSRP producer and WebCenter application can be retrieved and managed using a Java Keystore (JKS). A keystore is a file that provides information about available public and private keys. Keys are used for a variety of purposes, including authentication and data integrity. User certificates and the trust points needed to validate the certificates of peers are also stored securely in the wallet or keystore. See the Oracle Fusion Middleware Security and Administrator's Guide for Web Services for information about JKS.
The consumer in the step-by-step procedures below is the WebCenter application, which consumes portlets generated by the remote portlet producer over WSRP. The producer uses the public key of the consumer to verify the authenticity of the security tokens received from the consumer in the WS-Security headers of the requests it receives over its getMarkup interface. To do this, the producer needs a Java keystore that contains the certificate of the consumer and the root certificate used to sign it. These certificates are added to the Java keystore as trusted certificates.
This section describes the following tasks:
This section describes how to create keystores and keys using a Java Keystore (JKS). JKS is the proprietary keystore format defined by Sun Microsystems. To create and manage the keys and certificates in the JKS, use the keytool utility that is distributed with the Java JDK 6.
To create Java keystores for the consumer and producer:
Go to JDEV_HOME/jdk/bin and open a command prompt.
Using keytool, generate a key pair:
keytool -genkeypair -keyalg RSA -dname "consumer_dname" -alias consumer_alias -keypass key_password -keystore keystore -storepass keystore_password -validity days_valid
Where:
consumer_dname is the name of the consumer (for example, cn=consumer,dc=example,dc=com)
consumer_alias is the alias of the consumer (for example, consumer)
key_password is the password for the new public key, (for example, welcome1)
keystore is the keystore name, (for example, consumer.jks)
keystore_password is the keystore password, (for example, welcome1)
days_valid is the number of days for which the key password is valid (for example, 360).
Note:
You must use the-keyalg parameter and specify RSA as its value as shown above as the default algorithm (DSA) used by keytool for generating the key is incompatible with Oracle WebServices Security Manager requirements.Export the public key of the consumer:
keytool -exportcert -v -alias consumer_alias -keystore keystore -storepass keystore_password -rfc -file certificate_file
Where:
consumer_alias is the alias of the consumer (for example, consumer)
keystore is the keystore name, (for example, consumer.jks)
keystore_password is the keystore password, (for example, welcome1)
certificate_file is the file name for the certificate to export the key to (for example, consumer.cer)
Generate the producer keystore by importing the trusted certificate of consumer:
keytool -importcert -alias consumer_alias -file certificate_file -keystore keystore -storepass keystore_password
Where:
consumer_alias is the alias of the consumer
certificate_file is the certificate file name
keystore is the keystore name
keystore_password is the keystore password
Generate the key pair for the producer:
keytool -genkeypair -keyalg RSA -dname "producer_dname" -alias producer_alias -keypass key_password -keystore keystore -storepass keystore_password -validity days_valid
Where:
producer_dname is the name of the producer (for example, cn=producer,dc=example,dc=com)
producer_alias is the alias of the producer (for example, producer)
key_password is the password for the new public key, (for example, welcome1)
keystore is the keystore name, (for example, producer.jks)
keystore_password is the keystore password, (for example, welcome1)
days_valid is the number of days for which the key password is valid (for example, 1024)
Note:
You must use the-keyalg parameter and specify RSA as its value as shown above as the default algorithm (DSA) used by keytool for generating the key will not work.List the contents of the keystore:
keytool -list -v -keystore keystore_name -storepass password
Where:
keystore_name is the name of the consumer keystore file (for example, portal.jks)
password is the keystore password.
The keystore should now have two key entries.
Export the public key of the producer:
keytool -exportcert -v -alias producer_alias -keystore keystore -storepass keystore_password -rfc -file certificate_file
Where:
producer_alias is the alias of the producer (for example, producer)
keystore is the keystore name (for example, producer.jks)
keystore_password is the keystore password, (for example,welcome1
certificate_file is the certificate file name (for example, producer.cer)
Import the trusted certificate of the producer:
keytool -importcert -alias producer_alias -file certificate_file -keystore keystore_name -storepass keystore_password
Where:
producer_alias is the alias of the producer (for example, producer)
certificate_file is the file name or path for the producer's certificate file (for example,../producer/producer.cer
keystore_name is the keystore name (for example, consumer.jks)
keystore_password is the keystore password, (for example, welcome1)
To enable Web Services Security (WS-Security) trusted authentication for the WSRP producer and WebCenter application, you must first configure keystores for both the consumer and producer, and then import the keystore information to the consumer system as described below.
If a keystore provider is already configured, you will first need to unconfigure the existing keystore provider as described in Section 14.8.4.3.3, "Unconfiguring a Keystore Provider".
To configure the keystore provider:
Copy the corresponding keystores to corresponding servers.
Open Fusion Middleware Control and log into the target domain.
For information on logging into Fusion Middleware Control, see Section 6, "Starting Enterprise Manager Fusion Middleware Control".
In the Navigation pane, expand the WebLogic Domain node and click on the domain (for example, webcenter).
From the WebLogic Domain menu, select Security -> Security Provider Configuration.
The Security Provider Configuration page displays (see Figure 14-138).
Figure 14-138 Security Provider Configuration Page
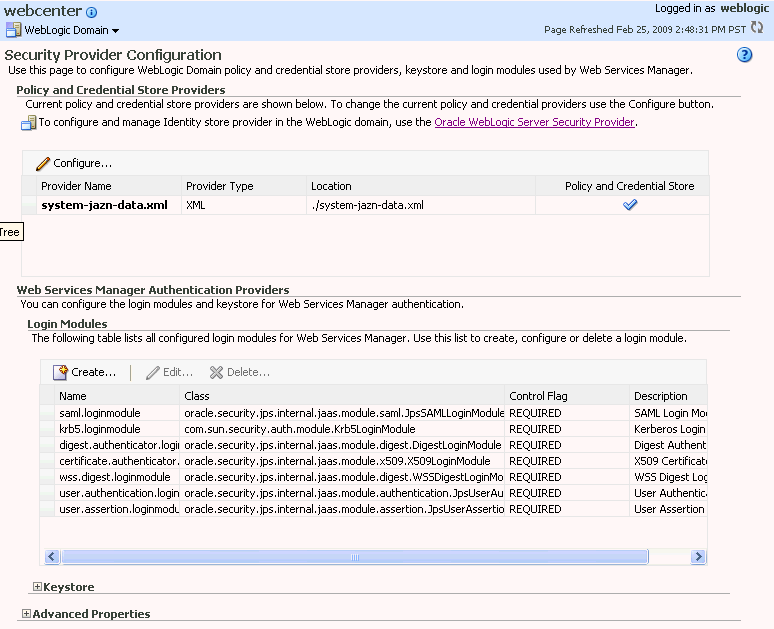
Expand the Keystore section on the Security Provider Configuration page.
Click Configure.
The Keystore Configuration page displays (see Figure 14-139).
Figure 14-139 Keystore Configuration Page
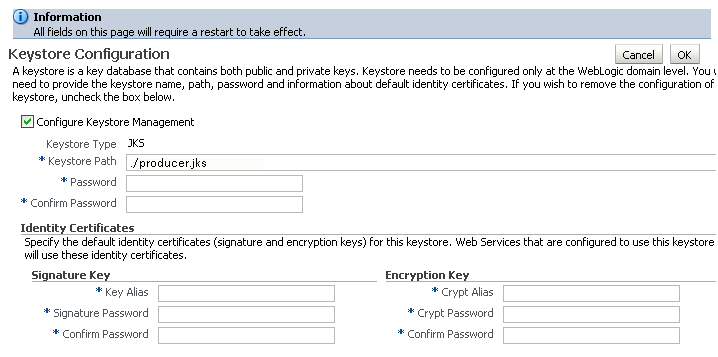
Use the Keystore section to specify the location of the keystore that contains the certificate and private key that is used for signing some parts (security token and SOAP message body) of the SOAP message, setting the signature key and encryption key parameters, and to set the keystore user name and password.
For detailed parameter information, see Section 14.8.1.4.2, "Updating the Credential Store in the WebCenter Spaces Instance Using Fusion Middleware Control".
Click OK to save your settings.
Restart the Administration server for the domain.
If a keystore provider is already configured, you will first need to unconfigure the existing keystore provider before configuring a new provider. To unconfigure, follow the steps below. Otherwise, continue with the steps to configure the producer.
To unconfigure a keystore provider using Fusion Middleware Control:
Open Fusion Middleware Control and log into the target domain.
For information on logging into Fusion Middleware Control, see Section 6, "Starting Enterprise Manager Fusion Middleware Control".
From the WebLogic Domain menu, select Security -> Security Provider Configuration.
The Security Provider Configuration page displays (see Figure 14-138).
Figure 14-140 Security Provider Configuration Page

Expand the Keystore section on the Security Provider Configuration page.
Click Configure.
The Keystore Configuration page displays (see Figure 14-139).
Figure 14-141 Keystore Configuration Page

Uncheck Configure Keystore Management.
Click OK.
This section describes how to configure WS-Security for WebCenter Spaces to support custom WebCenter applications that consume WebCenter Spaces client APIs.
This section includes the following subsections:
Follow the steps below to generate Java keystores for the consumer (the custom WebCenter application) and producer (WebCenter Spaces).
To generate keystores for the consumer and producer:
Go to JDEV_HOME/jdk/bin and open a command prompt.
Using keytool, generate a key pair:
keytool -genkeypair -keyalg RSA -dname "consumer_dname" -alias consumer_alias -keypass key_password -keystore keystore -storepass keystore_password -validity days_valid
Where:
consumer_dname is the name of the consumer (for example, cn=consumer,dc=example,dc=com)
consumer_alias is the alias of the consumer (for example, consumer)
key_password is the password for the new public key, (for example, welcome1)
keystore is the keystore name, (for example, consumer.jks)
keystore_password is the keystore password, (for example, welcome1)
days_valid is the number of days for which the key password is valid (for example, 360).
Note:
You must use the-keyalg parameter and specify RSA as its value as shown above as the default algorithm (DSA) used by keytool for generating the key is incompatible with Oracle WebServices Security Manager requirements.Export the public key for the consumer:
keytool -exportcert -v -alias consumer_alias -keystore keystore -storepass keystore_password -rfc -file certificate_file
Where:
consumer_alias is the alias of the consumer (for example, consumer)
keystore is the keystore name, (for example, consumer.jks)
keystore_password is the keystore password, (for example, welcome1)
certificate_file is the file name for the certificate to export the key to (for example, consumer.cer)
Generate the producer keystore by importing the trusted certificate of the consumer:
keytool -importcert -alias consumer_alias -file certificate_file -keystore keystore -storepass keystore_password
Where:
consumer_alias is the alias of the consumer
certificate_file is the certificate file name
keystore is the keystore name
keystore_password is the keystore password
Generate the key pair for the producer:
keytool -genkeypair -keyalg RSA -dname "producer_dname" -alias producer_alias -keypass key_password -keystore keystore-storepass keystore_password -validity days_valid
Where:
producer_dname is the name of the producer (for example, cn=producer,dc=example,dc=com)
producer_alias is the alias of the producer (for example, producer)
key_password is the password for the new public key, (for example, welcome1)
keystore is the keystore name, (for example, producer.jks)
keystore_password is the keystore password, (for example, welcome1)
days_valid is the number of days for which the key password is valid (for example, 1024)
Note:
You must use the-keyalg parameter and specify RSA as its value as shown above as the default algorithm (DSA) used by keytool for generating the key will not work.List the contents of the keystore:
keytool -list -v -keystore keystore_name -storepass password
Where:
keystore_name is the name of the consumer keystore file (for example, portal.jks)
password is the keystore password.
The keystore should now have two key entries.
Export the public key of the producer:
keytool -exportcert -v -alias producer_alias -keystore keystore -storepass keystore_password -rfc -file certificate_file
Where:
producer_alias is the alias of the producer (for example, producer)
keystore is the keystore name (for example, producer.jks)
keystore_password is the keystore password, (for example,welcome1
certificate_file is the certificate file name (for example, producer.cer)
Import the trusted certificate of the producer:
keytool -importcert -alias producer_alias -file certificate_file -keystore keystore_name -storepass keystore_password
Where:
producer_alias is the alias of the producer (for example, producer)
certificate_file is the file name or path for the producer's certificate file (for example,../producer/producer.cer)
keystore_name is the keystore name (for example, consumer.jks)
keystore_password is the keystore password, (for example, welcome1)
Before registering the keystores, make sure that you have provided the following to the developer creating the application that will be consuming the WebCenter Spaces APIs.
The consumer keystore to be used to secure the connection. This is a .jks file (for example, consumer.jks).
The consumer public alias key stored in the keystore (for example, consumer).
The password of the consumer public alias key (for example, welcome1).
The producer public alias key stored in the consumer keystore (for example, producer). This is the alias used when importing the trusted certificate of the producer, and created in step 8 of Section 14.8.5.1, "Generating the Keystores".
The consumer keystore password (for example, welcome1).
After you have created the keystores, configure the keystore for WS-Security by performing the following steps. If a keystore provider is already configured, unconfigure the existing keystore provider before proceeding as described in Section 14.8.4.3.3, "Unconfiguring a Keystore Provider".
To register the keystore provider:
Copy the producer.jks file to the file system where your producer application is running (for example, domain_home/config/fmwconfig).
Log into Fusion Middleware Control.
For information on logging into Fusion Middleware Control, see Section 6, "Starting Enterprise Manager Fusion Middleware Control".
In the Navigation pane, expand the WebLogic Domain node and click on the domain (for example, webcenter).
From the WebLogic Domain menu, select Security -> Security Provider Configuration.
The Security Provider Configuration page displays (see Figure 14-142).
Figure 14-142 Security Provider Configuration Page

Expand the Keystore section on the Security Provider Configuration page.
Click Configure.
The Keystore Configuration page displays (see Figure 14-143).
Figure 14-143 Keystore Configuration Page

In the Keystore Path field, specify the location of the keystore that contains the certificate and private key that is used for signing some parts (security token and SOAP message body) of the SOAP message, and enter and confirm the keystore Password.
In the Signature Key section, enter sign-csf-key as the Key Alias, and enter and confirm the signature key Password (the value used for <key_password> above) for the new public key, (for example, welcome1).
In the Encryption Key section, enter enc-csf-key in the Crypt Key field, and enter and confirm the encryption key Password (the value used for <key_password> above) for the new public key, (for example, welcome1).
Click OK to save your settings.
Restart the WLS Administration server for the domain.
Follow the steps below to update the credential stores using Fusion Middleware Control, or from the command line using WLST.
To update the Credential Store using WLST
Update the credential store using the WLST createCred command. Use the following example values to add the keystore-csf-key, enc-csf-key, and sign-csf-key encryption keys. Before running the command, be sure to back up the cwallet.sso file.
Example 14-14 keystore-csf-key
createCred(map="oracle.wsm.security",key="keystore-csf-key",user="keystore-csf-key",password="welcome1",desc="Keystore Password")
Example 14-15 enc-csf-key
createCred(map="oracle.wsm.security",key="enc-csf-key",user="producer",password="welcome1",desc="Enc Password")
Example 14-16 sign-csf-key
createCred(map="oracle.wsm.security",key="sign-csf-key",user="producer",password="welcome1",desc="Enc Password")
To update the Credential Store using Fusion Middleware Control
Log into Fusion Middleware Control.
For information on logging into Fusion Middleware Control, see Section 6, "Starting Enterprise Manager Fusion Middleware Control".
In the Navigation pane, expand the WebLogic Domain node and click on the domain (for example, webcenter).
From the WebLogic Domain menu, select Security -> Credentials.
The Credentials page displays (see Figure 14-144).
Click Create Map.
On the Create Map pop-up, enter oracle.wsm.security as the map name and click OK.
Click Create Key.
On the Create Key pop-up, select oracle.wsm.security as the map, enter keystore-csf-key as the Key, select Password as the Type, enter keystore-csf-key as the User Name, supply the Password (in this case, the keystore password of producer.jks) from when you created the keystores (for example, welcome1), enter an optional description, and click OK.
Click Create Key.
On the Create Key pop-up, select oracle.wsm.security as the map, enter sign-csf-key as the Key, select Password as the Type, enter the public key alias of the keystore used in the custom WebCenter application as the User Name, enter the password of the public key used in the custom WebCenter application as the Password, enter an optional description, and click OK.
Click Create Key.
On the Create Key pop-up, select oracle.wsm.security as the map, enter enc-csf-key as the Key, select Password as the Type, enter the public key alias of the keystore used in the WebCenter instance (for example, webcenter) as the User Name, enter the password of the public key used in the custom WebCenter application as the Password, enter an optional description, and click OK.
Restart the Administration server and WLS_Custom or managed server on which the custom WebCenter application is hosted.
A shared key can be defined for message integrity protection and should be used with SSL. The steps to store a shared key as a password credential are:
Define a shared key as a password credential in the credential store of the administration server instance. This can be done using either Fusion Middleware Control or WLST.
Grant the appropriate PDK-Java code access to the credential store (for example, oracle.portlet-producer.jpdk).
Restart the web producer and access the test page. Confirm that the shared key has been picked up correctly by checking the application logs.
Note:
Using a shared key provides only message integrity protection. For complete message protection SSL is required. For more information on securing PDK-Java portlets using SSL, see Section 14.6.5, "Securing the WebCenter Spaces Connection to Portlet Producers with SSL".You can define a shared key as a password credential in the credential store of the administration server instance using either Fusion Middleware Control or WLST commands.
To define a shared key using Fusion Middleware Control:
Log into Fusion Middleware Control.
For information on logging into Fusion Middleware Control, see Section 6, "Starting Enterprise Manager Fusion Middleware Control".
In the Navigation pane, expand the WebLogic Domain node and click the target domain (for example, wc_domain).
From the WebLogic Domain menu, select Security > Credentials.
The Credentials pane displays (see Figure 14-145).
Click Create Map and enter a unique Map Name and click OK.
Click Create Key and select the map name of the map you just created.
Enter a User Name (this value is not used so it could be anything), a Key in the form pdk.<service_id>.<user_name> (where <service_id> is the name of the producer and <user_name> is the value you entered for the User Name), and a 10 to 20 hexadecimal digit Password and click OK.
The new key is displayed in the Credential pane (see Figure 14-146).
Figure 14-146 Credentials Pane with New Shared Key
You can also define a shared key using WLST:
Start WLST as described in Section 1.12.3.1, "Running Oracle WebLogic Scripting Tool (WLST) Commands", and connect to the Administration Server instance for the target domain.
Connect to the Administration Server for the target domain with the following command:
connect('user_name','password, 'host_id:port')
Where:
user_name is the name of the user account with which to access the Administration Server (for example, weblogic)
password is the password with which to access the Administration Server
host_id is the host ID of the Administration Server
port is the port number of the Administration Server (for example, 7001).
Add a shared key credential for a producer to the credential store using the WLST createCred command:
createCred(map='MAP', key='MAP.service_id.sharedKey.user_name', user='user_name', password='password')
Where:
service_id is the name of the producer to create the key for (for example, omniPortlet)
user_name is the name of the user. This value is not used so it could be anything.
password is a 10 to 20 hexadecimal digit value.
For example:
createCred(map='MAP', key='MAP.omniPortlet.sharedKey', user='sharedKey', password='1234567890abc')
Note:
After creating a credential, you can use the WLSTupdateCred command with the same parameters as above to update it.Restart the producer.
Web producers pick up properties the first time they handle a request (for example, a browser test page request or when they are first registered), so producers should be restarted once a shared key credential has been set up.
After defining the shared key, the next step is to give the Web producer code (a shared library) read access to the credential store (defined as a permission class). The codebase URL for the shared library used for most Web producers will look like:
file:${domain.home}/servers/WLS_Portlet/tmp/_WL_user/oracle.portlet-producer.jpdk/-
which grants access to any file under the shared library directory. There are exceptions to this where the Web producer doesn't use the usual shared library. The Tools Web producer, for example, packages its code differently due to classloading considerations. The URL in this case would look like this:
file:${domain.home}/servers/WLS_Portlet/tmp/_WL_user/portalTools_11.1.1.1.0/-
The permission class is:
oracle.security.jps.service.credstore.CredentialAccessPermission
There are two ways to give a shared library access to the credentials:
Follow the steps below to add a grant where the Web producer code is granted access to the credential store, an existing grant is copied, and the codebase URL is changed to a Web producer code base URL.
To add a grant using Fusion Middleware Control:
Log into Fusion Middleware Control.
For information on logging into Fusion Middleware Control, see Section 6, "Starting Enterprise Manager Fusion Middleware Control".
In the Navigation pane, expand the WebLogic Domain node and click the target domain (for example, wc_domain).
From the WebLogic Domain menu, select Security > System Policies.
The System Policies pane displays (see Figure 14-147).
Click Create.
The Create System Grant pane displays (see Figure 14-148).
In the Grant To combo box, select Codebase.
In the Codebase field, enter the URL of the PDK shared library that accesses the credential store.
Under Permissions, click Add.
The Add Permissions pane displays (see Figure 14-149).
Do a search for all codebases, select one that has the needed permission class and click OK.
Now update it with the required details.
Display the test page in a browser (thereby making a request to the Web producer which will pick up the shared key). Then check the log.
To define a shared key using WLST:
Start WLST as described in Section 1.12.3.1, "Running Oracle WebLogic Scripting Tool (WLST) Commands".
Connect to the Administration Server for the target domain with the following command:
connect('user_name','password, 'host_id:port')
Where:
user_name is the name of the user account with which to access the Administration Server (for example, weblogic)
password is the password with which to access the Administration Server
host_id is the host ID of the Administration Server
port is the port number of the Administration Server (for example, 7001).
Define a shared key using the grantPermission command:
grantPermission(appStripe=None,principalClass=None,principalName=None, codeBaseURL='Codebase', permClass='Class',permTarget='context=SYSTEM, mapName=PDK,keyName=*',permActions='read')
Where:
Codebase is the codebase URL
Class is the permissions class (oracle.security.jps.service.credstore.CredentialAccessPermission)
For example:
grantPermission(appStripe=None,principalClass=None,principalName=None,codeBaseURL='file:${domain.home}/servers/WLS_Portlet/tmp/_WL_user/-',
permClass='oracle.security.jps.service.credstore.CredentialAccessPermission',
permTarget='context=SYSTEM,mapName=PDK,keyName=*',permActions='read')