Am I Vulnerable To ‘Failure to Restrict URL Access’?
The best way to find out if an application has failed to properly restrict URL access is to verify every page. Consider for each page, is the page supposed to be public or private. If a private page:
- Is authentication required to access that page?
- Is it supposed to be accessible to ANY authenticated user? If not, is an authorization check made to ensure the user has permission to access that page?
External security mechanisms frequently provide authentication and authorization checks for page access. Verify they are properly configured for every page. If code level protection is used, verify that code level protection is in place for every required page. Penetration testing can also verify whether proper protection is in place.
Hyperledger Fabric Fundamentals (LFD271) $299
With that in mind let’s tackle the next Security Shepherd challenge – Failure To Restrict Access.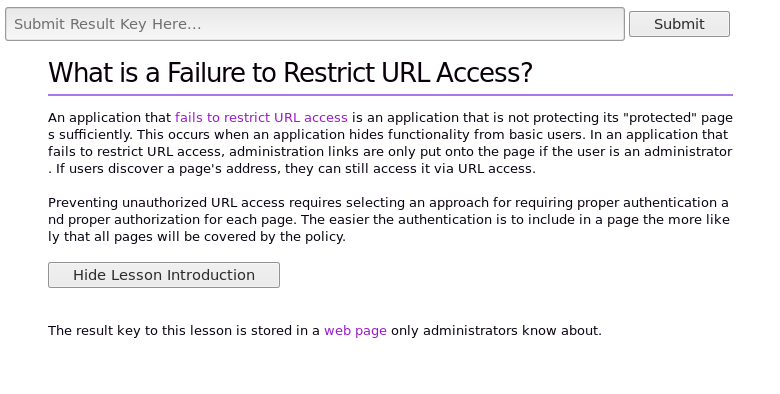
Above is the screen we are presented with on Security Shepherd. It’s all straight forward and what we notice straight away is that the words “web page” is highlighted. When we click on it the website does nothing but it still looks like a link. We will need the developer tools in Chrome to look at the code behind it. Right click on the highlighted words and choose Inspect. This will inspect that elements HTML.

Now we can see the code a bit clearer. Notice the div 2 lines under the web page text, the style=”display: none”. This is telling the web page not to display that element. Let’s change the text shall we?

Instead of style=”display: none” we change it to style=”display: text” this pops onto the screen what the developer did not want us to see. 
We have access to the Admin page now, this is where the key to the round resides. Click on the link and collect the key.
How Do I Prevent ‘Failure to Restrict URL Access’?
Preventing unauthorized URL access requires selecting an approach for requiring proper authentication and proper authorization for each page. Frequently, such protection is provided by one or more components external to the application code. Regardless of the mechanism(s), all of the following are recommended:
- The authentication and authorization policies be role based, to minimize the effort required to maintain these policies.
- The policies should be highly configurable, in order to minimize any hard coded aspects of the policy.
- The enforcement mechanism(s) should deny all access by default, requiring explicit grants to specific users and roles for access to every page.
- If the page is involved in a workflow, check to make sure the conditions are in the proper state to allow access.
Thanks for reading and don’t forget to return for further OWASP Security Shepherd solutions.
QuBits
