We have another solution in the OWASP Security Shepherd challenges and we enjoyed completing this one. You can find out about Session Management from OWASP here. So let’s get on with the challenge!!
Below is the screen we are presented with and if we click on the Administrators Only Button we are told we are not admin. Simple enough, we need to escalate our privileges to admin to complete the challenge.

Apparently the dogs have been released. This challenge will require a proxy for us to intercept the packet before it hits the server to see what is going across the airwaves. We will use Burp Suite for this task which comes as a default tool in Kali Linux.
Hyperledger Fabric Fundamentals (LFD271) $299
You can find out how to configure your browser to work with Burp Suite here. So let’s hit the Admin button again and catch the packet in Burp. [ Click on images for a better view. ]
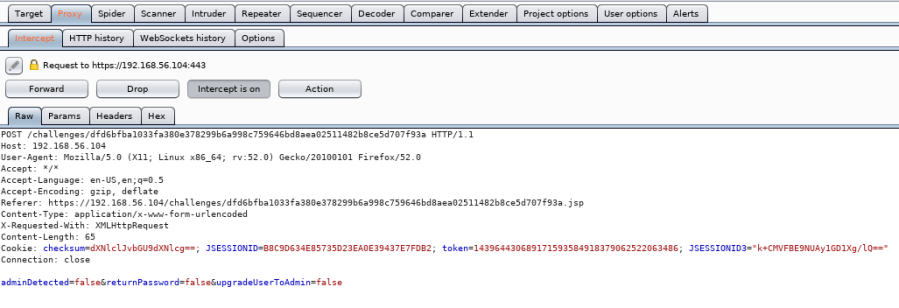
At the bottom of the data being sent over the wire we can see a few Boolean statements. AdminDetected=false, what can we do with that?
Let’s change it to true and forward the packet to the server?

Whoops!! That was detected on the server, probably best to not do that again. So what’s next? Let’s look at the packet again to see what other information we can extract from it. We will send the packet again, click the admin button, catch it in the proxy and inspect the packet.
Looking more carefully this time at the packet we should notice that there is a strange cookie in there and it’s called checksum. The checksum looks to be encoded with an MD5 hash. So let’s right click on the packet in Burp and send to our decoder tab to decode the hash.
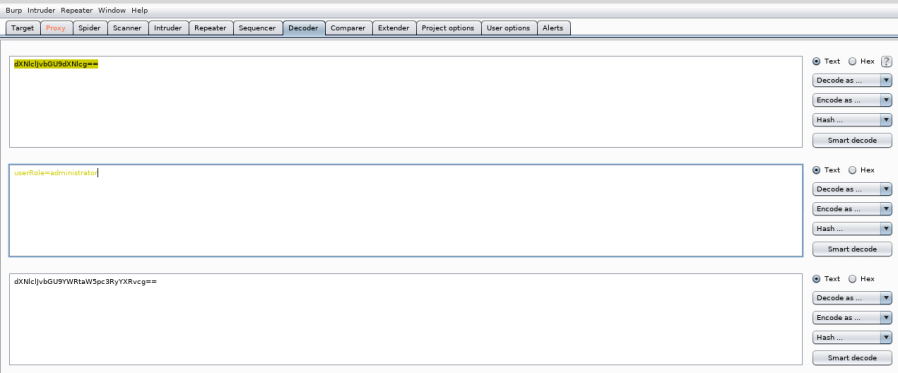
Bingo!! When we decode the hash we can see that it queries if userRole=admin. This cookie seems to be checking if the user is an admin and just encoded with the MD5 algorithm. We can’t just send that to the server, that is a normal request and we are just back to the start. So maybe we need to change it slightly and then send it to the server?
How about we lengthen the word admin to administrator?
Let’s quickly encode that back to MD5 with the tabs on the right hand side, replace the checksum in the sending packet with our new checksum and then forward that packet to the server.
Looks fine and dandy, will we gain privileges? Let’s Forward the packet and see what happens.

Perfecto!! To be honest, we didn’t get this first go and it was a bit of a challenge. But I managed to get there in the end. Hacking requires us to have attention to detail and knowing when cookies are sent in a HTTP request helps us to be able to manipulate those cookies. Having a basic understanding of encryption helps too as we were able to identify the hash used in the cookie. So another level of SecShep DEFEATED!!
Thanks for reading and I hope it helps you in some way.
QuBits 2018-10-10